Case of unmanned computer room access control system of communication company
[ad_1]
1. Market demand
With the continuous improvement of science and technology and the continuous emergence of new technology products, the modern management awareness of domestic enterprises and institutions has also been continuously enhanced; management requirements and levels have also been continuously improved. When the current telecom operators invest in the construction of the computer room, they not only consider the investment in network construction, but also consider the modern management mechanism. Abandon the outdated management concepts in the past, and implement safer and more convenient modern management methods.
2. Project overview
XX Communication Company currently has 30 unmanned edge computer rooms. Each computer room only monitors the status of one door (computer room entry). The central computer room must monitor the status of each computer room door in real time and remotely switch each computer room door. .
Three, the solution
In response to the above-mentioned needs of customers, we chose the SSET-ID05 editable multi-door access control system. This system adopts practical, advanced and economical design principles to design a new generation of access control system. In the SSET-ID05 editable multi-door access control system, computer technology, network communication technology, digital control technology, automatic identification technology, etc., are advanced technical systems at home and abroad. This system can help all enterprises and institutions to realize the seamless integration of network-based data exchange, information sharing, and computer digital control of building automation, security automation, fire automation and property management intelligence. The system is widely used in telecommunications, finance, public security, transportation, chemical and other enterprises and institutions, and is well received by users.
4. System composition and network structure
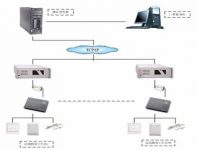
SSET-ID05 type editable multi-door access control system is composed of: access control management machine, communication server, remote client, RS232~RS485 converter, SSET-ID05 type editable single door integrated card reader (including controller function ), door lock, electric control switch, AC~DC power supply, card and other main parts.
The SSET-ID05 editable multi-door access control system is a real-time network system. The system can be divided into two layers from the network structure: the first layer is the network center, and the central equipment includes the access control management machine, communication server and RS232~RS485 The converter and central equipment are placed in the network management center of the central computer room. Users can intuitively monitor the access control status of each unattended computer room on the access control management machine of the network management center. The second layer is the remote communication unit. The remote communication unit includes a remote client, an integrated access card reader, door lock, exit button, and AC-DC power supply.

It can be seen from the network structure that the most critical device in the access control system is the controller, which acts as a hub tool in the network. Whether the controller’s function is powerful determines whether the access control system can meet the user’s management needs, and the stability, maintainability and scalability of the controller’s performance determine the use value of the access control system. The user should consider the above factors when investing in the establishment of an access control system to determine the finalization of the controller equipment in the system.
Five, system workflow
The SSET-ID05 editable multi-door access control system adopts a non-contact card reading method. The cardholder only needs to shake the card near the card reader (5-15cm) quickly, and the card reader can read the card in the card. The internal code is read out and temporarily stored in the card reader. At this time, the controller will automatically retrieve the card internal code temporarily stored in the card reader, and compare the card internal code with the permissions in the FLASH through the CPU in the controller , That is, to check the validity of the card. The comparison result is returned to the CPU, and the CPU then makes corresponding output actions based on the comparison result, that is, opening the door, alarming or other controllable transmission equipment. As long as the entire process of the system is within the effective card reading range, various management functions in the access control system can be realized. At the same time, various event logs that occur in the system can be recorded by the controller device. The system can also monitor the status of all equipment through the access control management machine, and at the same time back up the data. The user can query, count and process the data through the PC, and can also print various data reports through the print function in the system , Leave it as a written backup.
[ad_2]