Smart Card System Project Case of East China Electric Power Building
[ad_1]
The smart card management system is a high-tech information management system that integrates core technologies such as electronic engineering technology, computer software engineering technology, and microcomputer technology with smart cards as electronic media. It integrates access control, attendance, patrol, canteen dining, and parking lot management into one, and realizes all-round “all-in-one card” intelligent integrated management. The system provides users with efficient, safe and convenient modern management methods.
In 2002, in accordance with the strategic goal of “best in the country, first-class in the world” put forward by the company’s leaders, the East China Power Building underwent a comprehensive renovation to improve the office environment of the entire company. At the same time, the construction of the all-in-one card system aimed at improving the modernization of the company’s daily management has also been put on the agenda accordingly. In May 2002, after bidding, the all-in-one card system of the East China Power Building was determined to be constructed by a company in Shanghai. After one year of design, installation and commissioning, the system has been successfully completed and has been in trial operation for several months in good condition.
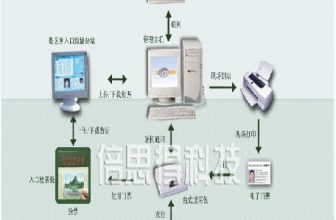
At present, the functions of the one-card system of the East China Power Building have been opened, including access control, attendance and canteen consumption. Among them, the access control system adopts the ××× series distributed access control system of an Israeli company. The attendance system uses the company’s professional attendance software based on the access control system, and the dining hall consumption system uses a Shenyang company’s catering system. Consumption management system. The front end of the all-in-one card system uses an inductive card reader and an inductive card from a company in the United States. We will introduce the entire system in more detail in the following sections.
1. Selection of the All-in-One Card System
According to the construction goal of our company’s one-card system, the first phase will build access control, attendance and canteen consumption systems, and then when appropriate, add books and audiovisual materials borrowing and reading systems, internal medical expenses management systems, and parking lot management systems. . Therefore, we emphasized the compatibility of the card’s magnetic card, card reader and the subsystems of the card in the initial stage of the model selection.
Judging from the technological development in recent years, the choice of inductive IC card is the general trend. Inductive IC card, also known as radio frequency card and non-contact IC card, is a new technology developed in recent years. It successfully combines radio frequency identification technology and IC card technology to solve the problem of passive (no power supply in the card). ) And the problem of contact-free is a major breakthrough in the field of electronic devices. Compared with the contact IC card, it has the advantages of high reliability, convenient operation, anti-collision, good encryption, and one card with multiple functions. The inductive IC card and corresponding card reader we chose is a product that is technically mature and highly compatible, and has a wide range of applications. It is one of the ideal products that meet our selection requirements.
Secondly, according to the original design, 145 gates will be installed in the entire building, a larger number. The East China Power Building is an important place for East China Power dispatch. The stability of its internal access control system will affect the normal operation of the entire building. Therefore, in the selection of the access control system, we focused on the stability index.
The access control system we choose can easily manage from one door to thousands of doors. Its product design is in accordance with industrial control standards, and the controller adopts a dual CPU design, and each point is a set of industrial control equipment to ensure the stability of the system. The mean time between failures of the main control board can be as high as 50,000 hours.
At the same time, all equipment of the system adopts relatively distributed control. In the event of a communication failure on the network, it can still continue to work in accordance with the preset working mode. Employees who have issued cards can use them as usual. During the failure period, employees’ card swiping records are temporarily stored in each lower computer. Inside, for reference. Once the communication failure is repaired, each network will automatically return the recorded data to the system management center to ensure the integrity of the system information, and its safety and reliability will be greatly improved.
For the selection of time and attendance software, considering that a company has its own professional time and attendance management software, the easiest way to implement the time and attendance system is to specify one or more access control card readers on the basis of the existing access control system For the attendance point, an additional set of attendance management software can be added, which also greatly guarantees the compatibility of the system.
The original canteen consumption system used in the building is a magnetic card consumption system provided by a Beijing company. Taking into account the continuity with the original consumer system, we originally planned to continue to use the company’s consumer system software. However, in the system implementation stage, the company proposed that its existing POS machines are incompatible with HID card readers, and were unwilling to change the POS machines and corresponding consumer software it provided. After the company’s recommendation, we adopted and read Card reader compatible catering consumption system.
Our all-in-one card management system (including access control, consumption, and attendance) adopts a modular design. Each subsystem is completely independent of each other and will never affect each other in the event of a failure, ensuring the high reliability of the system.
2. Access control system
The scope of the access control system includes the access doors and fire doors of the public parts of the building, the financial treasury, the financial office of the government, the archives and other important places, as well as the entry and exit management of some important offices.
1.Introduction to the main functions of the access control system
⑴ Computer-based programming: The operator makes various settings on the control host according to his own operating authority, such as authorizing door opening/closing, checking the status of a controlled area door, authorizing cards or deleting cards, etc.
⑵Access level control: The system (authorized person) can set the time and place of use of the proximity card at any time. Cardholders who do not belong to this level are forbidden to access, and the system will alarm for illegal entry behavior. There are a variety of timetables to choose from.
⑶ Real-time monitoring function: the status and behavior of the portal can be reflected in the computer of the control center in real time, such as door opening/closing, who, when, where, etc. When the door opening time exceeds the set value, the system will alarm.
⑷Record storage function: All card reading data have computer records, which is convenient for timely query after an accident.
⑸Multi-level operation authority password setting: The system assigns operation authority to operators of different levels, and only enter the correct password to perform corresponding operations.
⑹Remote monitoring: The system can realize remote control and automatic dialing to the pre-designated phone through the telephone MODEM.
⑺ Linkage control with various subsystems: The system can be connected through hardware contacts or through gateways and closed-circuit television monitoring, anti-theft alarm and fire alarm systems to implement coordinated linkage among various subsystems.
2.The specific configuration scheme of the access control system
The control unit of the access control system is composed of ××× series distributed controller (NSL-3/NSL-4), inductive card reader, exit button, emergency exit button, door sensor and magnetic lock. The access control system is also equipped with communication conversion (C-32), management computer, networking software Amadeus 3 and non-networking software QA8.
The whole system consists of five loops, each controlled by five communication converters. Among them, the first four loops belong to the online access control system, which respectively control all public passages, financial treasury, and financial office of the building on the 1st to 7th, 8th to 12th, 13th to 18th, and 19th to 24th floors of the building. For doors in important places such as archives, each loop controls about 18 doors. The fifth loop is an offline non-networked access control system, which controls 11 important offices on the 12th to 14th floors of the building. Considering a certain degree of privacy, the entry and exit records of these doors are not displayed in real time on the management computer, but when needed Download, you can use QA8 software to call out the stored records for inquiries. In addition, these 11 offices all use a visual intercom system to match the access control system, so that visitors at the door can communicate with the people in the house, and the people in the house can use the buttons under the desktop to easily open the access control. In addition, a card reader with a keyboard is also installed at the door of the dispatching room with a high level of security. In addition to using authorized proximity cards, those who want to enter must also enter the correct password to enter, which improves the security of the dispatching room. sex.
It is worth mentioning that the controllers used in the entire access control system are dual-door controllers, so the system has a faster response speed and higher security. In addition, the system uses a magnetic lock to control the opening and closing of the door. Compared with other control methods such as electric locks, the magnetic lock has the characteristics of strong suction, easy installation, low power consumption, no noise, anti-vandalism, anti-corrosion, and has a long life. Long, almost no maintenance, is a relatively ideal application mode.
The access control system can be linked with fire protection. When a fire alarm occurs, the access door of the floor will automatically open. This system is also linked with the alarm system, which can transmit the alarm signal to the building central control center to provide information about the time and place. Meet the real-time requirements of the alarm system.
3.Introduction to the main equipment used in the access control system
(1) Introduction to proximity card
●The reading range is not affected by body occlusion or environmental factors
●Tough texture, not easy to break or break
●More than 13.7 billion different passwords to ensure system security
●Can paste a variety of specially printed color patterns
(2) Introduction to the access controller
●Easy to install and use
●Each controller controls two card readers
●Can adapt to different card readers
●Can manage 2000 users
●Anti-reverse transmission as standard configuration
●Upgradable
(3) Card reader:
● Stand-alone, compact, easy to install and attractive appearance
●High working reliability, extremely stable reading range and performance, and low power consumption
●With buzzer and multi-color diodes, it is convenient to use or control.
●Compatible with all standard access control systems.
●The sealed design can withstand harsh environments, provide reliable operating conditions and a high degree of anti-destructive ability.
●Induction distance: 6-10cm.
(4) Access control management software Amadeus 3: It is an access control system management software based on Windows operating system. Its standard version includes all functions of access control management. The software is suitable for single user or multiple users at the same time, while QA8 is a non-networking Access control software.
4.Configuration table of main equipment of access control system
.jpg)
3. Attendance Management System
Attendance management system is based on the existing access control system, one or more access control card readers are designated as the attendance point, and a set of attendance management software is added to realize it.
Attendance management software can basically be divided into six functional modules: personnel management, daily processing, report management, attendance management, system maintenance and help. The software has the ability to process a large amount of data. It integrates employees’ commuting and attendance, automatic data collection, summary, accounting, query, and printing of reports. It eliminates a large amount of data redundancy and reduces the consumption of manpower and material resources.
[ad_2]