RFID important document dynamic supervision system
[ad_1]
1. Program overview
File management has always been an important part of the internal management of the government and enterprises. Traditional file management is still used by many organizations to this day, including manual extraction and bar code management developed later. Although it requires a lot of manual work, there are still chances of errors or accidental leaks. Therefore, in today’s fast-developing society of RFID, making full use of the superiority of RFID to supervise document files can reduce manual operations in the management process, and can greatly reduce errors caused by manual proofreading or negligence, and realize important The real-time monitoring of document files is also suitable for the internal management of the government or unit in the future, and at the same time, it can improve work efficiency. The government’s strong support is needed for us to work together to create RFID technology applications.
2. Overview of core technology
RFID is the abbreviation of “Radio Frequency Identification” in English. In Chinese, it is called radio frequency identification, inductive electronic chip or proximity card, proximity card, non-contact card… etc. It is a kind of non-contact automatic identification technology. The microwave RFID technology developed based on the principle of backscattering (Back ScaTtering) communication is a wireless, non-contact automatic identification technology, and is a cutting-edge technology project developed in recent years. This technology is mainly compatible with today’s digital building mobile commerce, which can realize automatic identification and remote real-time monitoring and management. Its communication distance can range from a few centimeters to tens of meters, and depending on the reading and writing methods, thousands of bytes of digital information can be input, which has extremely high confidentiality. It adapts to the social needs of contemporary digital mobile commerce and is one of the hottest technologies in information technology. Its main advantages are strong environmental adaptability, not affected by rain, snow, hail, dust, etc., can complete automatic identification, tracking and management all-weather, non-contact, and can penetrate non-metallic objects for identification, and have strong anti-interference ability. Therefore, RFID technology has been widely used all over the world. The application research of RFID technology in developed countries led by the United States, Japan and Europe has reached a very high level, while my country is in its infancy and mostly adopts imported technological achievements. . Therefore, research on this technology has become an inevitable trend in the development of today’s society.
3. Technical solution
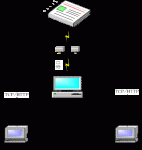
1. Model system structure diagram
The system uses RFID technology to realize file outflow supervision and alarm, and improve the level of security. The system structure is shown in (Figure 1). The controller monitors files with RFID in real time; once important files flow out, the system automatically collects file tag data; RFID intermediate data transmission equipment, point-to-point sending information to a remote computer or mobile phone; such as unverified or permitted files If it is taken out, the system can carry out the alarm function.

2. Processing flow
When the device with the RFID card reader passes the door, the controller regularly controls the reader to read the tag data, the controller obtains the file tag data, and sends the tag data to the “RFID Middleware Data Transmission Device” (sending end) The other (receiving end) reads the data of the receiving end through a computer, analyzes and processes the data, saves the data in the database, and realizes file supervision. The system processing flowchart is shown in the figure below.
3. System advantages
(1) The concealed installation of this equipment is not easy to be found;
(2) Through the customized remote transmission module, data can be obtained in time;
(3) All products are independently developed by the company to ensure data security;
(4) Multiple clients collect data, receive and process data in real time;
(5) Can dynamically monitor the flow of unauthorized files.
[ad_2]



