Chuangyi joins hands with CNOOC to develop offshore personnel positioning system
[ad_1]
1. System introduction
1.1 Project background
Marine operations are complicated in most cases. If blowouts are out of control, fires and explosions, platform distress, plane or helicopter crashes, ship damages, oil (gas) production facilities and pipeline damage/leakage, leakage of toxic and hazardous materials, radioactivity Material loss; serious injuries, deaths, missing persons, and outbreaks of infectious diseases and poisoning; special circumstances such as oil spills, natural disasters, and other emergencies, which not only cause huge property losses, but also seriously threaten the safety of marine operators. Personal safety.
When an accident occurs, how to know the location information of the operator in the first time so as to make a timely judgment and take corresponding measures becomes particularly important.
1.2 Purpose of implementation
From the perspective of customers, China Chuangyi Technology, with its own advanced technology and excellent development team, has developed a maritime operator positioning management system based on the current social conditions. The management system realizes the regional positioning of the working environment of marine personnel, and can know the regional location of the personnel at any time.
China·Chuangyi’s offshore operator positioning management system adopts the most advanced ZIGBEE technology, and specifically designed and developed a set of software and hardware combined application system for the needs of offshore staff management and monitoring. It is a safe and reliable intelligent management system , In a real sense, realize the information management of offshore operators, and provide reliable guarantee for the personal safety of offshore operators.
2. System function

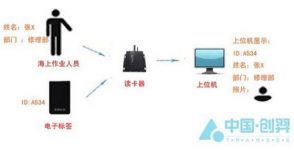
Configure an active tag (wristband or card type) for each offshore operator. Each active tag has its own unique ID number. The information in the tag can be set to basic information such as name, age, gender, department, etc. , Because the electronic tag is active, so the working mode is active, and the ID number information can be sent out continuously.
Install several card readers at the main positions of stairs, passages, working areas and living areas (the number and location of the installation are determined according to the site conditions, so that the area that needs to be monitored does not appear in the blind area where the label information cannot be read)
When an operator wearing a tag enters the recognition range of a card reader, the reader receives the tag information, and transmits the signal to the system terminal through wireless transmission or other intermediate devices, and can be compared with the ID number database See the detailed information of the person.
The fixed card reader in each monitoring area can be monitored at a fixed time interval through software settings, for example, set to automatically refresh once every 30 seconds, that is, realize automatic execution once.
2.1 Real-time monitoring of personnel
The position of all operators is displayed in real-time on the position diagram of the upper computer of the system, and the monitoring personnel can dynamically grasp the number of personnel and real-time distribution. Move the mouse to the personnel icon to view the detailed information of the personnel.
2.2 Personnel search and location
Enter the person’s name or number to quickly locate the area where the person you want to find is located.
2.3 Remote monitoring and inspection
After the card reader reads the information, it can transmit the information to the data center through WIFI, GPRS, etc., and the system can be operated through the Internet, which can realize remote management and monitoring of the platform site in the monitoring center.
3. Principle of operation
According to the size of the operating table, arrange several locators to cover the entire operating table. When there is an unauthorized person on the console or the staff leaves the console without authorization, that is, when the tag signal of the staff is read abnormally or the signal cannot be read, the system will alarm in time.

Configure an active tag (wristband or card type) for each operator, install several card readers at the main positions of the stairs, the main roads of the passage, the working area and the living area (the installation location depends on the site conditions) ), can receive the information data sent by the active tags worn by the personnel in the entire work area in real time, and realize the real-time positioning of the personnel.
Divide the positioning area inside the console, and each locator can set a small coverage radius as needed to cover the entire console. The locator performs polling and card reading according to the time set in the background, and locates the activity block of each worker in the workshop. According to the positioning interval, the real-time trajectory of each worker is depicted.
4. System Features
4.1 Technical features
The system uses ZigBee technology. ZigBee is a wireless connection that can work at 2.14GHz (globally popular) wireless communication technology. It has the following characteristics:
Low power consumption: Due to the low transmission rate of ZigBee, the transmission power is only 1mW, and the sleep mode is adopted, and the power consumption is low, so ZigBee devices are very power-saving. Short delay: The communication delay and the delay of activation from the dormant state are both very short. The typical search device delay is 30ms, the dormant activation delay is 15ms, and the active device channel access delay is 15ms. Therefore, ZigBee technology is suitable for wireless control (such as industrial control occasions, etc.) applications with demanding delay requirements.
Large network capacity: A star-shaped Zigbee network can accommodate up to 254 slave devices and one master device. There can be up to 100 ZigBee networks in an area at the same time, and the network composition is flexible.
Reliability: A collision avoidance strategy is adopted, and a dedicated time slot is reserved for communication services that require a fixed bandwidth to avoid competition and conflicts in sending data. The MAC layer adopts a fully confirmed data transmission mode, and each data packet sent must wait for the receiver’s confirmation information. If there is a problem in the transmission process, it can be retransmitted.
[ad_2]



