Westinghouse access control 60,000 sets of system application flagship brand (picture)
[ad_1]

I. Overview
With the progress of the times, the access control system has become an extremely important part of the security system. In some developed countries, the access control system is developing rapidly at a much higher rate than other types of security products; the fundamental reason why the access control system can stand out among many security products is because it has changed the previous security products such as closed-circuit monitoring. , burglar alarm and other passive security methods, with active control instead of passive monitoring, through the control of the main channel, greatly prevent criminals from intrusion from the normal channel, and can pass the control of the channel door when a crime occurs Limit the scope of activities of criminals to stop crime or reduce losses. On the other hand, because a complete access control system has a powerful database structure, it often integrates the patrol management function; it can provide a large number of input and output interfaces, and at the same time, it can also complete simple attendance statistics through its report function. Purpose. That is, users don’t need to do any integration work, they can get seamless integration of anti-theft alarm system, relay output and attendance system.
2. System goals
With the radio frequency card technology as the core and the computer and communication technology as the means, the access control points in the building are connected into an organic whole.Through the same operation platform, users can complete various comprehensive security control and management functions of access control and alarm management
3. System requirements and demand analysis
The system requires the employees of the company to hold smart cards, which can be used to enter and exit the main passages of the building and the office space; enter and exit the parking lot; consume in the staff restaurant; staff attendance and other functions. The central management server records the data of all systems, and records the query through the “one card” system management software and automatically generates various reports.
demand analysis
The main control equipment and ancillary equipment of the “One Card” system are produced by professional manufacturers, with stable quality, reliable performance and scalability, and are widely used by domestic and foreign users.
It integrates multiple functions such as access control, attendance, consumption, patrolling, parking lot, etc. to realize comprehensive management and intelligent linkage.
The functions of opening, closing, fortifying, and disarming the access control system can be easily realized through the electronic effect diagram, the electronic structure plan, and the mouse click.
Each subsystem can work offline. When the communication between the subsystems and the central server fails, the inspection system will check whether the communication of each subsystem is normal. If the communication of each subsystem fails, the central server management system will prompt related The system needs to be repaired, etc.
The cables of each subsystem have the ability to resist lightning strike and signal noise interference.
Each system is equipped with a backup battery, in case of a sudden power failure, the system can work normally for more than 5 hours to ensure the safety of the system operation.
The access control system should be equipped with an “emergency backup card” (advanced authority), which can be used to open any door of the access control system.
The access control system can easily realize access control functions such as interlocking and anti-passback.
The functions of remote report, remote alarm, remote setting and remote query can be realized through modem, which is convenient for system management and maintenance.
Personnel entry and exit management and inquiry: The system records the attendance data, and the “one card” system software of the central server automatically generates a comprehensive attendance report and provides it to the personnel department.
Consumption management and inquiry: system canteen consumption, catering consumption, reservation consumption, etc., realize fixed consumption and non-fixed consumption according to needs, daily management of contactless IC consumption card issuance, recharge, loss reporting, etc., and realize data aggregation, query, and generation Consumption statement, provided to the financial department.
Employees can automatically enter and exit the parking lot with a valid ID card, and realize functions such as charging or free. At the same time, the parking lot management report is automatically generated and provided to the financial department.
Various linkage functions (such as CCTV, fire, alarm linkage).
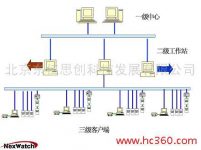
4. System structure
1. System composition
The access control system consists of two parts: software and hardware, including identification card, front-end equipment (card reader, electric door lock, door magnetic switch, control equipment, etc.), transmission equipment, communication server and related software.
The most important part of the hardware is the control device. All card readers, door locks, door sensors, door buttons and other front-end devices are connected to the corresponding control devices to complete various system functions (access control, anti-theft alarm, etc. )the goal of.
The software is installed on the computer specially used for monitoring and management in the management center. The management personnel use the access control software to set the system and issue card authorization management, check the passing objects and passing time of each channel; the completion of the patrol plan; the alarm situation of the defense area, etc. , and carry out relevant real-time control or set program control targets.
The system finally completes all management work by the system computer, which is determined by the management software in the computer. In the security access control system of the design center building, we adopted the access control software Pro-Watch from Westinghouse. The software has integrated anti-theft alarm function and elevator control function, and can manage the data of all equipment in the system.
2. Control principle
In daily applications, the user usually swipes the card on the entrance card reader. After the control device receives the card reading information from the card reader and recognizes it as a valid card through the control device, it triggers the relay that controls the electric lock. Open the corresponding entrance and exit to allow cardholders to pass. The control method of the two-way door is called “anti-reverse transmission”, and it is mandatory that all entry and exit must be swiped, and cannot follow others to enter and exit at will.
The controller stores these card swiping events, and after connecting with the management host, transmits the event records to the upper management host for long-term storage, query and statistics. After the control device is set up, it can run independently offline, control various front-end devices, and the management host or communication failure will not affect its operation.
On the computer of the monitoring center, managers can check the traffic conditions of each channel and the operation of front-end equipment in real time, and can control the switch of the channel and change the traffic mode in the control area. All data can form reports.
The access control system supports the access of alarm equipment, and provides the control output of the video surveillance system through the computer serial port, which can be set in the software to fully integrate the relevant security systems and equipment, so as to achieve the purpose of centralized management and decentralized monitoring of the security system.
3. System function
Control the opening/closing of electric locks at all access control points, implement authorized security management, and report the status of each door to the control center in real time.
Through the pre-programmed settings of the management computer, the system can authorize the cardholder’s access card (entry/exit level setting), and set the effective use time and scope of the card (the area allowed to enter), which is convenient for internal unified management.
The system automatically recognizes the identity of the personnel entering and leaving, preventing the intrusion of foreign personnel.
All use the non-contact card reading identification method, and the system user can only enter and exit within the authorized range with a valid card.
Set up two-way monitoring and management of entry and exit at important passages (both entry and exit need to be swiped). The anti-reverse transmission function enhances the security of the access control system.
The system can detect abnormal door opening and has an alarm function. If someone opens the door illegally (destroys), or “applies” a low-level card to try to sneak into an important location, the access control controller immediately transmits the alarm information to the control center computer and prompts the location of the crime, and records it at the same time.
Electric key – Issue an authorized radio frequency card, which can be used as an electronic key. Put the radio frequency card in front of the card reader, the indicator light of the card reader changes from red to green, and the door lock is automatically opened. At the same time, the controller records the date, time and the name of the cardholder when the door is opened.
Door opening authority – set by door: the door opening area (quantity) can be set according to the employee authority requirements. The radio frequency card with the highest authority can open all doors; set by time: each radio frequency card can set the time period for which the door is allowed to open.
Automatic alarm – when an illegal card is used or the door lock is forcibly opened, the system will automatically alarm to ensure security.
Recording information – When the card is read, the system will record the cardholder’s personal information, card reading time, card number and other information.
Inquiry – The management department can inquire the detailed records of employees of various departments on the inquiry system at any time as needed. and can be printed at any time. Each department can also inquire about the entry and exit status of its employees at any time as needed.
Emergency drive – such as stair doors can be set to automatically open in an emergency, so that people can evacuate in time and ensure personal safety.
The controller has an offline function, when it is offline with the computer, it can run independently and store data.
System linkage – can be linked with monitoring, alarm, fire protection and other security systems.
5. Equipment selection
The system adopts the stability of the access control management system and the high American Westinghouse access control system (NexWatch)
NexWatch is the inventor of the world’s first inductive access control system, with a history of more than 50 years. Westinghouse access control is world-renowned for its powerful system functions and unparalleled stability. Worldwide, Westinghouse has more than 300 agents and more than 800 support points in 76 countries. Westinghouse’s customers come from many fields around the world, including industrial and commercial enterprises, telecommunications companies, education sectors, government agencies, entertainment and military security sectors. There are currently 60,000 systems in use worldwide.
[ad_2]



