Application and Development of Access Control System in Nanning Power Supply Bureau
[ad_1]
1.Overview
Today’s society is an information age in which science and technology are changing rapidly and developing rapidly. People are feeling the great convenience and benefits brought by high technology, and at the same time, people have higher and higher requirements for high technology to serve life. But with the development of science and technology, it also brings many unsafe aspects. For example, the use of high-tech means to commit crimes such as theft, robbery and espionage is increasing day by day. How can people’s safety precautions keep up with the development of science and technology and prevent these criminal acts more effectively? It is not enough to rely only on ordinary door locks, anti-theft doors or monitoring and alarm systems. Therefore, the intelligent access control system came into being in the long-awaited.
2.access control systemOverview
Nanning Power Supply Bureau is a large-scale power supply enterprise with power supply areas spanning three regions, and is responsible for the power supply tasks of 26 counties (cities) including Nanning City. In the 1990s, information systems such as finance, electricity management, and distribution geographic information were successively established and networked. In order to monitor and manage the important places in the production plant area of the Power Supply Bureau and ensure the safety of the power grid operation, the construction of the access control system began in 2002. The access control system belongs to a security system in the intelligent weak current system.
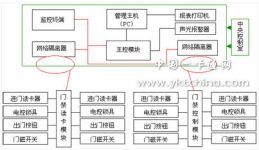
2.1 The composition of the access control system: the access control system consists ofcard reader, controller, electromagnetic lock, identification card and computer. For identification cards and card readers, they can be divided into two categories, namely contact and contactless.

2.2 System scale: It basically covers the management of the main floors of the bureau. The network laying has been extended to the five office buildings of the bureau and its main production plant area. In the early stage of construction of the access control system, the main office building of the production compound was monitored and managed. Inductive access control system is used.
2.3 Hardware platform server: The server adopts Lenovo 733 and the memory is 256M.
2.4 Server operating system: PC server: Windows2000 Chinese version.
2.5 Operating system: The network operating system adopts Windows2000 Chinese version, TCP/IP protocol; the workstation operating system is mainly Windows 2000, as well as Windows 98, Windows 3.11, Windows NT Workstation 4.0.
3 Access control system functions and functions
With the advancement and development of science and technology, the access control system has a variety of functions and can manage the monitoring of various important places.
3.1 Functions of the access control system
3.1.1 —-Security management function, you can set the user’s authority and entry and exit time, you can enter the user’s name, age, job title, photo and other data into the computer, which is convenient for query statistics and verification identity;
3.1.2 —Attendance function, which can group and classify personnel according to the actual situation, and record attendance for various holidays and working days;
3.1.3 —- Patrol function, which can record the patrol route, time and events of patrol points such as door damage, elevator failure, etc.;
3.1.4 —-A combination of various access control methods, you can set the door lock as only in and out, long open, time switch and other functions and various combinations;
3.1.5 —-Emergency and statistical functions, the system can display the physical location of the designated cardholder on the computer, which is convenient for timely contact. In the event of fire and other emergencies, the fire door will be automatically opened to facilitate escape, and the entrance and exit can also be opened automatically; when illegal entry and exit occurs, the system will automatically alarm; the system can also print out various statistical reports according to the needs of customers.
3.2 The computer management function of the access control system
3.2.1 System management: The function of this part of the software is to manage all the equipment and data of the system, including the following items:
3.2.1.1 Device registration: For example, when adding a controller or card, it needs to be re-registered to make it effective; when reducing the loss of the controller or card, or the change of personnel, it will be invalid.
3.2.1.2 Level setting: in the registered cards, which gates can pass through and which cannot pass through. Which cards are allowed and which are not allowed by a controller. For the operation of the computer, set a password to control who can operate.
3.2.2 Time management: You can set what time certain controllers can or cannot allow cardholders to pass through; which cards can or cannot pass through which doors at what time.
3.2.3 Database management: The recorded data is processed such as dumping, backup, archiving and reading. Event record: When the system is running normally, it records various access events, abnormal events and their processing methods, and saves them in the database for future query.
3.2.4 Report generation: can generate various reports regularly or randomly according to requirements. For example, it is possible to find out the entry and exit of a certain person within a certain period of time, who has entered and exited a certain door within a certain period of time, etc., and generate a report, which can be printed out by a printer. And then combine “attendance management”, “patrol management”, “meeting room management” and so on.
3.2.5 Inter-network communication: The system does not exist as a single system, it transmits information to other systems. For example, when there is illegal intrusion, it is necessary to send information to the TV monitoring system, so that the camera can monitor the situation there and record it. Therefore, there must be support for communication between systems.
In addition to completing the required functions, the management system should also have a beautiful and intuitive human-machine interface, which makes it easy for personnel to operate.
3.3 Access control function
Access control systems belong to the category of public safety management systems. In the main management areas, entrances and exits, elevator halls, main equipment control center machine rooms, warehouses of valuables and other important parts of the passageway in the building, install control devices such as door magnetic switches, electric locks or card readers, controlled by the center The system adopts computer multi-task processing, which can control or set program control in real time for the location, passing objects and passing time of each channel, which is suitable for the public safety management of some banks, financial trade buildings and comprehensive office buildings.
The role of the access control system is to manage the entry and exit of the crowd into and out of the control area, restrict the entry and exit of unauthorized personnel, and make it easier for authorized people to enter and exit. The system can use proximity cards, fingerprints, passwords, etc., as authorized identification, through the control machine programming, record the time and date of the personnel entering and leaving, and can cooperate with the alarm and CCTV system to achieve the best management. Applicable to various types of offices, computer rooms, databases, parking lots and warehouses.
4 Principles of Access Control System
4.1proximity cardFeatures
Because of the appearance of the proximity card, the user no longer needs to carry the key, and the trouble of duplicating the key is eliminated, and there is no need to worry about the possible loss of property. There are many package forms of inductive signal transmitters, including card type, key ring type, pen type, glass tube type, microphone pen…… and so on. In direct proportion, generally speaking, when the user is in the access control and parking lot control, for the convenience of carrying, it is usually made into a card type, so it is commonly known as a proximity card.
4.2 Action principle
Promixity cards are generally called contact cards, and magnetic cards must be swiped to achieve control purposes. Usually, an induction card contains IC chips, induction coils and capacitor elements. The inductive card is the transmitting and answering end, and the inductive card reader is the receiving end, similar to a generator, which continuously transmits the frequency. When the card is close to the range of the transmission frequency of the card reader, the coil in the card will accept this frequency and generate energy, which is stored in the capacitor. After the password is sent to the card reader for identification, the door can be opened. The frequencies emitted by the card readers of different brands are different, so the cards will not communicate with each other and can be used.
4.3 Settingsaccess controlThe main purpose of the system
It is to ensure the safety of important areas and equipment in the area, facilitate the reasonable flow of personnel, and implement various methods of access permission management for personnel entering these important areas, so as to restrict personnel from entering and leaving at will. When employees want to enter the restricted area, they must swipe their card in the card reader next to the door before the door can be opened. The card reader at each door is controlled by the monitoring terminal through the on-site control interface unit and the system centralized controller. According to the system settings, each card can only open the door within the specified range within the specified time. At the same time, to prevent outsiders from breaking in at will, if someone forcibly breaks the door or does not close the door after get off work, the access control device will send an alarm signal, and the monitoring terminal will immediately display the alarm door number. The purpose of the design of the access control system is to realize the access control and access information recording of personnel.
4.4 Principle of access control system
1. For the entrances and exits to be controlled, install electric control doors controlled by electric lock devices and sensors (such as electronic password keyboards, card readers, fingerprint readers, etc.);
2. Authorized personnel can open the electric control door with a valid card, or password and their own fingerprints;
3. All access data are recorded by the background computer; the access rights of authorized personnel can be modified at any time through the background computer;
4. The system can also join the attendance system function;
5 Apply the effect
During the construction period of the access control system, the needs of employees’ attendance, canteen consumption, and vehicle access were taken into consideration, and ID cards were used to do so.a cartoon.Since it was put into operation, it has been realizedAttendance, access control, meals, vehicle entry and exit functions, which greatly facilitates the needs of employees to enter and exit and consume, and provide managers with a variety of monitoring and management functions. In 2003, the comprehensive building of the fleet of Nanning Power Supply Bureau was completed, and access control management was constructed in the parking lot on the first and second floors of the comprehensive building, which further strengthened the management of vehicle parking, entry and exit. Put an end to the phenomenon of employees driving buses without permission.
6 Status and Development of Access Control Technology
6.1 Current Situation of Power Supply Bureau
The access control system has been put into operation in the power supply bureau for a long time. In the process of use, it is found that there is still room for improvement. The increase in the number of employees and the limitation of the capacity of the equipment to read data, the single mode of querying data, easy to demagnetize, due to The canteen consumption system is upgraded, and the ID card is not compatible with access control systems using different technologies; the access control system is restricted to play a greater role. In the future, the access control system will use a simpler and more compatible IC card as a card. The access control system is also used for the security management of the residential area.
6.2 Current Status of Access Control Technology
At present, the access control system produced abroad is relatively safe, but expensive. The price of the inductive access control system and fingerprint access control system produced in China is lower than that of similar foreign products, but the reliability of the system is slightly worse. The advanced intelligent access control system is an important development direction of the current access control system. The advanced intelligent access control system is a networked access control system with relatively complete functions.
Most people think that access control is only a device for access control. The most typical one is the traditional keyboard controller or magnetic card reader installed by the door. In order to obtain the right to enter, the person must swipe the card first. However, now access control has more advanced technologies and new application markets. The technologies currently used in access control systems include: barcode, graphic ID, magnetic barcode, Wiegand, induction, smart code, biometric identification, etc. Among them, inductive access control and biometric access control will become the two major trends in the development of access control.
The emergence of compatible cards allows one card to be used in a variety of access control systems with different technologies, allowing users to use one card for multiple purposes, because this card can be used for various card readers: graphic ID, induction, bar code, magnetic card type Accepted, so the cardholder can use one card to enter and exit different buildings or perform various functions. IC cards can integrate complex key authentication and identity authentication logic, and will definitely replace the previous magnetic cards and ID cards. The formation of the one-card system is the inevitable outcome of the development of smart cards.
These access control systems vary in technology and the level of security they can achieve. Optical technology is used in barcode and graphic ID systems to identify the information stored in barcodes and graphic IDs; electromagnetic technology is used in magnetic card access control systems. When the cardholder swipes the magnetic card, the system will read the magnetic properties that are allowed to enter; The root technology is extremely ingenious and still belongs to the category of electromagnetics; the frequency of induction technology is generally 110~125KHz. The stronger the frequency, the farther the reading distance of the induction access control system. The reading distance of the MHz inductive access control system can reach nearly 1 meter. This access control system has many other application fields, such as: parking lots, various toll systems and so on. Of course, the safest access control system should be a system that can identify human biometrics, not the characteristics of objects held by people. For example, a biometrics system that uses the unique biometrics of the human body can identify fingerprints and pupil structure, which will be the most important feature of the access control system. The highest level, but the price is extremely expensive, it is difficult for the majority of users to accept.
In contrast, the inductive access control system is still the one with more mature technology and reasonable price. Many experts predict that the inductive access control system will replace other access control (such as electromagnetic access control system, etc.) to become the dominant access control market. There are several reasons why the induction type access control system can be quickly accepted by the market: it is easy to use; because the system does not have any mechanical wear, the long-term maintenance cost is low; the service life of the card is long. More reliable security performance.
6.3 Global current level and development direction of access control system
(1) The level and development direction of front-end input devices. In terms of card readers and cards, due to the high requirements for the operating environment of magnetic cards and contact IC cards, the work of magnetic cards and IC cards themselves have a certain lifespan. In addition, the operator’s actions and the time required in the identification process are significantly more than Contactless cards, therefore, although magnetic cards, contact IC cards, and card readers still have a part of the market in the application of access control systems, from the perspective of development trends, in addition to hotel locks, magnetic card IC card readers have gradually Quickly exit the access control system market.
(2) It is bound to replace the magnetic card and IC card market in an all-round way with the current development momentum of non-contact D-card and IC card. The non-contact IC card not only inherits the advantages of large capacity and high security of the contact IC card, but also has the advantages of small size, high integration and high reliability, and its performance is much higher than that of the familiar contact card. type IC card.
7 Conclusion
Although the construction of the access control system of Nanning Power Supply Bureau has achieved initial results, information sharing has basically been achieved. But from the overall management point of view, it has just started, and the software needs to be further improved and perfected. It is necessary to continuously improve the system with reference to higher standards, so that the system can better serve production and management, and improve the overall work efficiency and management level.
About the Author: Lin Fei was born in December 1974, Gender: Female Title: Assistant Engineer
The main work of Nanning Branch of Guangxi Bolian Information and Communication Technology Co., Ltd.: maintenance of information application system and management of broadband network.
[ad_2]


