HID Access Control System Engineering Case of the First Affiliated Hospital of Jinan University
[ad_1]
At present, traditional doorman management can no longer meet the safety needs of modern hospital employees and property. Only by establishing an information-based safety management system can we better defend against various hidden safety hazards. The access control solution for the First Affiliated Hospital of Guangzhou Jinan University strengthens the hospital’s ability to respond to emergencies, ensure the safety of medical staff, patients, and property, and improve patient satisfaction and management efficiency of medical institutions.
As an open place, medical institutions carry the important responsibility of the public to see a doctor. Hospitals at all levels circulate a very large flow of people every day, and their commuters include patients, family members, and medical staff. The huge flow of people and the special crowd structure have brought great difficulty to the safety management of the hospital. It is easy for intruders to enter and leave the hospital, and enter areas where only authorized employees should be able to enter at will, thus posing safety hazards. For example, the recent malignant injury case at Harbin Medical University is the biggest warning to the hidden dangers of hospital safety.
Contactlesssmart cardThe application of technology in the medical industry helps the medical industry solve some long-standing thorny problems. Control personnel entering and exiting relevant areas of the hospital through hierarchical authority to protect the safety of medical staff and provide better access control management.At present, the contactless smart card technology in hospitals includesAccess controlThe system controls the entry and exit of hospital personnel, the secure login of computers and IT systems, and the management of patient medical information. HID Global recently designed an access control solution for the Affiliated Hospital of Jinan University in Guangzhou to meet the needs of safety management.
Project Background
The First Affiliated Hospital of Jinan University, formerly known as Guangzhou Overseas Chinese Hospital, was approved by the State Council and established in 1978 to serve the health of the general public and overseas Chinese and cultivate medical talents for the society. The hospital is the clinical medicine teaching base of Jinan University, with more than 1,100 professional and technical personnel, 43 specialties and 850 beds. It is a comprehensive hospital integrating medical treatment, teaching, scientific research, prevention, health care and rehabilitation. The hospital is about to build a new inpatient building of 72,000 square meters, implement digital and networked hospital construction, and step up investment in high-level medical equipment and safety management systems to improve the overall medical level and hospital safety in Guangdong Province.
The first affiliated hospital of Jinan University includes patients, visiting relatives and accompanying staff. The huge flow of people and the special crowd structure have brought great difficulty to the safety management of the hospital. It is easy for intruders to enter and exit the hospital, and enter areas where only authorized employees should be able to enter at will, thereby posing safety hazards (such as stealing babies from pediatric wards). Therefore, in terms of the safety management of the entrance and exit of the hospital, it is necessary to meet the dual requirements of opening to the outside world and protecting the rescue site at the same time.
In addition, the safety management of key areas such as the hospital’s drug room, operating room, and intensive care unit is the top priority. Any hidden safety hazard and accidental intrusion may cause major safety accidents. Therefore, the access control system of the First Affiliated Hospital of Jinan University should meet the following requirements:
Graded authorization, limited time entry and exit: Key areas such as drug rooms and operating rooms need to be managed by grades, times and locations to prevent unauthorized personnel from entering.
Future scalability: The hospital will renovate the old building and construct a new building at the same time. Therefore, the access control system must be able to expand in the future in addition to meeting the application needs of the current stage, eliminating the need to reinstall the system in the future.
Hospital access control system composition
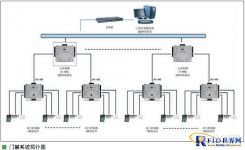
The hospital access control system is the first line of defense to protect the working area of the hospital and the safety of medical staff. It is mainly composed of on-site access control equipment and the management center. The controlled area is divided by the distribution and functions of the hospital floors, so as to be effective, reasonable and cost-saving. . Combining the application functions of the hospital to choose the controller and access card of the access control system can also facilitate the expansion and addition of applications in the future. (See the topological diagram of the access control system)

Access control field equipment: Field equipment includes field controllers, card readers, electric locks, door magnetic switches, door opening buttons and emergency glass breaking buttons. Mainly set at the door end of the hospital’s access control points, including operating rooms, baby rooms, medicine rooms and important computer room areas, office areas, and equipment areas. By setting different passage periods and permissions for personnel entering these areas, safety is improved.
Management Center: The management center includes system servers, authorized management workstations, management workstations (with database, report, query and other functions), main controller, printer, communication interface equipment and system software. The hospital sets the access authority, area, and time of access card through the management center.
The access control solution for the Affiliated Hospital of Guangzhou Jinan University. The system adopts a networked structure of centralized management and decentralized control. Through the TCP/IP network of the hospital, the access control points of the hospital management area are connected to the central management platform, and the main access points, such as the drug room , Operating room, important ward and other areas. HID iCLASS card readers are installed at each access control point. When an employee wants to enter the controlled area, the card needs to be authenticated. Each card has set permissions to restrict the access time and area of medical staff and other employees. For example, the intensive care unit and operating room are restricted to doctors and related medical staff. The management of the drug room is based on the schedule of on-duty hours, and the permissions are set for the cards held by the staff in the drug room to ensure that authorized personnel enter during the permitted period to prevent accidental and malicious intrusion.
The function and characteristics of hospital access control system
Multiple ways to open the door
The system sets up a variety of door opening methods to meet the different security needs of each area of the hospital, such as card opening methods, such as card opening, card or password, fingerprint, card + password, card + fingerprint, card + password + fingerprint, password + fingerprint and other door opening methods. For example, installing a fingerprint reader in the operating room can double-identify the surgeon by swiping card + fingerprint, which can accurately confirm the identity of the surgeon and prevent surgeons from switching operations.
HID iCLASS contactless smart card technology provides three security levels: single-factor authentication, two-factor authentication, and three-factor authentication. In the case of single-factor authentication, you can log in to the system or enter the building as long as you use a smart card. Two-factor authentication is the most common smart card authentication method in hospitals, and both personal identification numbers (PIN) and smart cards are used to increase security. Three-factor authentication goes a step further, not only using PIN codes, but also using other security measures such as biometrics to provide stronger security guarantees for the management of important areas.
Hierarchical authority management
All hospital employees enter the management area by swiping their credential cards. According to the functions of the management area, the functions of the employees are classified, and the access rights are managed by time periods, and the relevant personnel are restricted from entering at will. For example, key areas such as medicine rooms and operating rooms need to be managed by levels, time and location to prevent unauthorized personnel from entering and improve regional security.
The iCLASS card reader is connected to the network access controller HID VertX V1000 through the field controller HID VertX 100, and is connected to the central management station through the hospital’s TCP/IP. The administrator can use the system software to set different levels and permissions to implement permission setting, data browsing and query, and data backup for each access control point. When the computer in the management center fails, the entrances and exits can still work offline, and the card reading and access control switches will not be affected in any way.
Upload event records in real time
The access control system can record event records in real time and upload them to the computer, which can immediately display: cardholder (name, photo, etc.), event time, door address, event type (door swiping record, exit swiping record, button to open the door, invalid card reading Card, door opening timeout, forced door opening, etc.), and record truthfully. The records cannot be changed, which is convenient for the hospital to manage various reports.
The HID VertX access control system can automatically record the card information of the personnel, including: employee number, name, department, position and other information, as well as the time and location of entry, through the analysis and screening of the card reading data, and processing statistics of late arrivals, early departures, absenteeism, and abnormal situations , Overtime and vacation. Managers can even generate various reports from the data for attendance and shift management.
Multi-system linkage
Fire-fighting linkage: When a fire occurs, the access control system automatically receives the fire-fighting signal, and opens the electric lock of the corresponding door according to the set plan, so that people can evacuate in time.
Video linkage: For the received abnormal alarm signal, the access control system can linkage switch the camera screen, and video monitoring, recording or snapping the parts that need to be monitored.
HID VertX controller through the modular, networked flexible design, through the built-in alarm/fire interface, and the hospital’s closed-circuit monitoring, anti-theft and fire-fighting and other systems coordinated linkage, when the access control system receives a fire alarm signal, it can Automatically open all the gates in the control area, which is conducive to the escape of people in the control area; cameras are installed in important parts to monitor and record the parts that need to be monitored.
Scalable
With the development of the hospital and the needs of adding new applications, the access control system can easily and quickly expand the system to meet new requirements. The HID Global access control system has good scalability and can be upgraded with the company’s existing access control to meet the actual needs of the expansion and reconstruction of the hospital and increase future applications, and save the cost of the hospital. At the same time, HID iCLASS cards can not only be used in access control management, but also other applications can be added, such as computing/network security authentication, health record management, attendance, parking lot management, and realizing hospital all-in-one cards.
The role of contactless smart cards
The application of smart card technology to hospital computers and IT login systems and medication dispensing systems can help hospitals better establish patient information files, protect patient privacy, improve hospital management efficiency, and control doctors’ medication use. It can improve the hospital’s information management level, improve efficiency, and prevent medication and medical accidents.
Prevent sensitive patient information from leaking
Doctors log in to the personal computer and IT system through the equipped access card, and can store and manage patient information in a safe and secure manner, preventing the disclosure of sensitive patient personal information. Doctors only need a smart card to log in to the IT system, avoiding wasting time by recalling and entering user names and passwords, and quickly accessing sensitive patient information through the Internet to save time to take care of patients.
HID on the Desktop is a brand-new security authentication solution. Its most notable feature is “one card with multiple uses”. A credential card is not only an identification card with a photo, a key to open the door, or a personal computer and IT Security authentication of the system. Medical staff can directly access Windows and the network through the equipped access card, which is easy to use, safe and reliable, and effectively prevents the leakage of sensitive patient information.
In addition, HID on the Desktop’s unique two-factor authentication (card + personal authentication password (PIN)) eliminates the risk of IT systems being attacked by hackers and improves the risk management of IT systems.
Improve the efficiency of medical staff
At present, many foreign hospitals are the first to adopt smart card technology for patient information management. For example, Germany has just issued a health care smart card to more than 80 million people across the country to establish an “electronic case book” for patients. Through this project, the hospital will improve Manage patients well. When the patient first visits, the hospital establishes an electronic file for the patient, records the patient’s health information including name, gender, ID number, medical history and other information, and encrypts it and stores it on the smart card. The patient can use the self-service terminal in the hospital Or the hospital network system for appointment registration. At the time of consultation, the patient’s medical card is connected to the doctor’s computer system through the identity verification terminal equipped in each department. After the verification is successful, the doctor can quickly retrieve the patient’s electronic medical record and prescribe for the consultation.
Provide support for the hospital’s dispensing system
Non-contact smart card technology provides safer management measures for the hospital’s dispensing system to ensure the safety of patients’ medication. By setting the authority of the smart card of medical staff, the medical staff responsible for dispensing medicines are allowed to use the smart card to log in to the computer system to view the patient’s electronic medical record, recheck the relevant medicines and dosages, and reduce medication errors. This benefit also lies in the fact that the medical center can track the user and the time of use of the medicine, helping practitioners to better abide by the hospital’s medication rules and protecting the rights of patients.
Reduce the probability of nosocomial infection
Contactless smart card technology has a great impact on hospital infection control. We have all noticed that antibacterial hand sanitizers are now placed at the entrances of all wards in the hospital, and everyone has seen the bird flu prevention posters distributed by the government to every household. Imagine that a doctor inspected 20 patients in 5 wards during a few hours of rounds. During this period, she arrived in different areas of the hospital and logged in to different computer systems. It is easy for us to understand how infection spreads through these contacts. Contactless smart cards only need to be swiped in front of the reader, which plays a key role in limiting infection.
With the increasing level of security technology, the hospital’s security system is also developing in a multi-functional direction. Security technology is inevitably a necessary management hardware for modern hospitals. It will improve the management level of the hospital and ensure the safety of hospital personnel and property.
Concluding remarks
The HID access control solution adopts a networked structure of centralized management and decentralized control. Through the TCP/IP network of the hospital, the access points of each district are connected to the central management platform to monitor important areas, such as drug rooms, operating rooms, and important wards and administrative areas. And implement authority management to restrict personnel’s access authority and time period.
ICLASS R10 card readers are installed at the access control points in each area. When employees want to enter the controlled area, they need to authenticate the card. Each card has set permissions to restrict the access time and area of medical staff and other employees. For example, the intensive care unit and operating room are restricted to doctors and related medical staff. The management of the drug room is based on the schedule of on-duty hours, and the permissions are set for the cards held by the staff in the drug room to ensure that authorized personnel enter during the permitted period to prevent accidental and malicious intrusion.
The iCLASS R10 card reader of each access control point is connected to the network access control controller VertX V1000 through the field controller VertX 100, and then connected to the central management station via TCP/IP. The administrator can use the system software to set different levels and permissions to implement permission setting, data browsing and query, and data backup for each access control point. When the computer in the management center fails, the entrances and exits can still work offline, and the card reading and access control switches will not be affected in any way.
At the same time, the system can automatically record the personnel’s card information, including: employee number, name, department, position and other information, as well as entry time and location, through the analysis and screening of card reading data and processing statistics of lateness, early leaving, absenteeism, abnormal situations, Overtime and vacation. Managers can even generate various reports from the data for attendance and shift management.
Zhao Gong of the Infrastructure Construction Department of the Jida Affiliated Hospital said that after comparing many domestic and foreign brands, he chose HID Global’s products in consideration of its leading technology, perfect market support and lifetime maintenance. HID Global products comply with multiple international security technology standards. Data encryption and dual identity verification are used between iCLASS cards and iCLASS card readers to ensure the need for security management in key areas.
In addition, HID Global’s access control solution has good openness, can easily and conveniently realize expansion requirements and hardware interchange, and flexibly configure various scales and grades of systems to meet the needs of future hospital expansion. If the hospital needs to further improve the security level in the future, it can add functions such as biometrics, two-door interlocking, and anti-returning to the system, and it can also be linked with various fire/alarm systems to ensure the safety of the hospital in all aspects. HID Global’s access control solutions can be developed into all-in-one cards for computer desktop login, consumer systems and parking lot management.
[ad_2]



