Men Geely: Introduction to the Application of the Access Control System in Chongqing Jiangbei Airport
[ad_1]
Chongqing Jiangbei International Airport is one of the three major aviation hubs in Southwest China and one of the five major hub airports planned by the state in the future. It is a 4E-class civil airport. The airport currently has three terminals, namely the T2A and T2B terminals for domestic flights and the T1 terminal for international flights. The domestic terminal has a construction area of 171,000 square meters and a designed annual passenger throughput of 20 million.
1.Project summary
The access control management system of Chongqing Jiangbei Airport (referred to as the access control system) refers to the comprehensive entrance and exit management system that controls the entry and exit of personnel according to the settings of the permissions for the entry and exit of personnel in each area of the T2A terminal and the international building of Jiangbei Airport at different times.
At the same time, the access control management system of this project requires that the access control system that has been put into operation in the T2B terminal building be brought into unified management, and its built access control system should be modified and upgraded according to the overall requirements. In this way, a unified access control IC card (employee card) and a unified database are used in the access control system of the T2A terminal, T2B terminal, and international building.
This project uses the internationally renowned brand Mengyili MeLucky®MACAS3000 large-scale access control and integrated security management system and equipment. The system has been used in dozens of large-scale domestic and foreign airports, such as Tianjin Airport, Xiamen Airport, Capital Airport, Taiyuan Airport, Urumqi Airport, and Angola Capital Airport. Successfully applied in airport projects.
2.Overall design principles
Safety and reliability
The products selected by this system fully comply with the requirements of current international, domestic and national standards and related regulations;
The system link must be stable and reliable, and fault detection and recovery must be quick;
Support dual-system hot backup technology;
Ensure that under any circumstances, without external interference, independent operation, operation and management and linkage control can be achieved.
Advanced
The system is simple, reliable, and convenient to manage, but it is also advanced.
Integration
The system can integrate third-party subsystems such as fire fighting system and CCTV system to achieve seamless integration.
Scalability
The system should be extensible in order to adapt to future development needs.
When the system is expanded, there is no need to change the system architecture and increase the main control equipment, just add the front-end equipment to realize the system expansion.
Economy
On the basis of meeting the application requirements, follow the principles of advanced technology, excellent equipment, reasonable economy and high quality to reduce the project cost.
3.Basic structure and configuration of the system
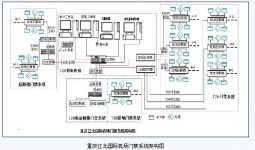
Chongqing Jiangbei International Airport adopts a networked access control system. The newly built T2A terminal access control system will be integrated with the new access control system of the international building and the original access control system of the T2B terminal through the internal local area network.
In order to reduce construction costs and management costs, improve management efficiency, and truly reflect the principle of “centralized management, decentralized control”, through the T2A terminal access control system management server and card issuing terminal equipment, the entire system The hardware equipment (the access control points under the jurisdiction of the International Building and T2B terminal) realizes parameter configuration, personnel authorization, real-time monitoring of access control events and alarm events, historical record query, remote control of the opening or closing of doors, etc.
Based on system security, the system is equipped with two management server hosts to realize one-master and one-backup dual-system backup.
In the international building and T2B terminal, computers are respectively configured as management workstations, which can independently realize personnel authorization, real-time monitoring, historical record query, and remote control of the opening or closing of doors in the area. At the same time, if the corresponding authority is granted, the device parameter configuration and personnel authorization can also be performed on the access control points in other areas.
The access control system is mainly composed of the control part of the management center (management server, card issuing terminal, area controller, etc.), data transmission part, and field part (entry and exit including card readers, field controllers, electric locks, etc.).
The area controller communicates with the management server through TCP/IP communication, and is connected to the front-end field controller through the RS485 bus.
Each access control point adopts two-way card swiping to strictly manage the entry/exit method (the identification of each card reader is through the dual identification of the proximity card and the personal password).
The system architecture is as follows:

4.Overall system function and performance
Safety management
Multi-level personal password login method to verify the authority and security of system administrators;
Improve access control event display and alarm management, prompt online prompts and alarms for unclosed doors and illegal openings, and notify the security department to deal with it;
Multiple approved door opening methods, including card only, password only, card plus password, card plus video double verification, etc.;
Supports three-level data/information storage and management of servers, area controllers, and field controllers. Once a certain level of equipment is paralyzed, it will not affect the normal access control management and the smooth passage of personnel. After the system is restored, all data will be automatically uploaded to achieve “centralized management,” The principle of decentralized control.
The access control controller supports ring dual bus. When a certain point of the bus is disconnected, the normal communication of all devices will not be affected.
Support dual-system hot backup to ensure data security.
Operator management
A variety of operator operation levels can be set, and the degree of operation can be defined. Each operator can only operate a limited module within the authorization range, and each step of operation will generate a record and store it in the event library.
Equipment management
The control center can set, monitor, and control various parameters and equipment status of each entrance and exit controller in the graphic mode.
Incident management
All operator events, access control events and various fault information are classified and processed and stored in the database.
Alarm management
In addition to faults and common alarms, the operator can also define some other event as an alarm event. When an alarm occurs, the corresponding auxiliary equipment can provide sound, light and voice prompts.
Personnel registration and issuance
Management functions such as local card issuance, authorization, loss reporting, visiting card registration, and blacklist.
Real-time monitoring of equipment status
Automatically detect the working status and failure conditions of communication channels, front-end controllers, card readers and other equipment, and have alarm prompts to remind staff on duty.
{$page$}
Automatic recovery
When the power supply is interrupted and the supply is restored, all equipment will restart automatically according to the set procedure in time; when the communication channel fails, the data is temporarily stored locally, once the communication channel returns to normal, the untransmitted data will be automatically transmitted.
Regional authorization settings
Set the activity area of the registered card through the software, that is, which doors or passages the cardholder can or cannot pass through; if the different areas are divided into levels, the cardholder’s entry area can be controlled by setting the card level Permissions.
Time period setting
According to the personnel authority, a certain person can be allowed to enter a certain area at a certain time.
256 holidays can be defined, and the minimum period of time can be defined in 1 minute, and 128 time zones can be freely defined for each person.
Record storage
The system will automatically store all modification operations, and store operation logs, event records, etc. within the time period set according to management requirements. Perfect alarm function.
Anti-turnback: After a certain access control card reader enters the management area, the access control card does not exit but the card read again;
Multiple alarms
Invalid access control card alarm, alarm for too long door opening time, alarm for equipment failure or offline, and alarm for forced intrusion when the door is opened abnormally.
Duress alarm: When a person holding an access card is threatened or kidnapped, he can send out a silent alarm when the door is opened normally by entering a special character or character combination, and immediately report it to the security monitoring center and related department control room or control center.
Electronic map display
The system software can display real-time equipment status in the system, door open/close status, personnel entry and exit, alarm status, etc. in 4W format (When, Where, Who, What) through a multi-level dynamic electronic map.
real time monitoring
A. Support dual display of electronic map and table
The system has the function of supporting user-defined color electronic map display capabilities, used to display the geographic location, door, and lock location of the event: and can receive alarm signals from other systems.
At the same time, the time and date of each door opening, the card number, name, subordinate department, position and other related information of each door opener are recorded in real time in a form, and the distribution of personnel can be selectively checked.
B. Dynamic icons
The electronic map allows users to add dynamic icons related to system components by themselves and can conveniently issue instructions to system components and complete related tasks by clicking on the icons.
Information query and report printing
The system records the abnormal event information in the database of the access control server, and the manager can check from the historical record and print the automatic classification report regularly.
Report function
It can keep a complete record of all access events, alarm events, fault events, etc., can be classified and inquired according to needs, and reports can be made.
System integration and linkage
The system has a variety of interface methods, such as hardware switch connection, RS232, Ethernet, ODB, TCP/IP, Winsock, etc.
Linked with the CCTV system, the camera automatically captures live images when the device is offline, the door is opened for too long, or when the door is forcibly broken in.
Linked with the FAS system, when the fire alarm occurs, the door lock of the corresponding area is automatically released to keep the door open.
5.Main hardware equipment functions and performance
5.1 Area Controller
Use well-known brand Mengyili MeLucky®MIC-4A regional controller
? Support time and regional anti-return control
?Automatic alarm arming/disarming mode
?Built-in storage function
? When the communication with the server is interrupted, it can automatically switch to independent working mode and still have access control management functions;
?System program and memory have power-off protection function
?The time set and time zone can be set flexibly, and there is no limit on the number
?With programmable auxiliary input and output interface, it is convenient to link with alarm system, CCTV and other systems
?Support dual network ports, support RS-232/RS-485/optical fiber, TCP/IP multiple communication methodssupport dual loop
? Storage capacity of 80GB, can store no less than 1,000,000 cardholders or 600,000 events
5.2 Field Controller
Use well-known brand door Geely MeLucky®ML300-4A access control field controller
With local storage, it can manage the opening of the door independently after being offline with the area controller
?Can connect 4 card readers and 4 exit buttons
?4 doors can be managed in one-way card scanning mode, and 2 doors can be managed in two-way card mode scanning mode
? With 4 auxiliary inputs (alarm) 4 auxiliary relay outputs
?Can receive Wiegeng input from card reader or keyboard
5.3 IC card reader
Choose well-known brand Mengyili MeLucky®ML4705-44 card reader
?Support multiple access modes such as swiping card, swiping card plus password, swiping card or password, and password only.
The shell is dust-proof, moisture-proof, rust-proof and shock-proof
?Small size, light weight, low energy consumption
? Fast response, anti-interference, stable performance
? Buzzer prompt and status display
The card reader supports Chinese and English color display
? LCD card reader can flexibly set the display content
? Induction distance: 0-100mm
6.Concluding remarks
The access control management system of Chongqing Jiangbei Airport was banned from entering the formal construction and implementation stage in May 2010. On New Year’s Day of 2011, it passed the inspection and acceptance by CAAC Airport Group Company, design company, supervision company and system general contractor, etc., and has been put into formal operation now. In good condition.
[ad_2]


