Application of RFID gun off-position alarm system
[ad_1]
project description:
In order to strengthen the security work of the troops, prevent firearms and ammunition on duty being robbed, sentries being attacked, and sentries fleeing the troops with guns and ammunition, intensify the supervision and management of on-duty (mobile) ammunition, effectively prevent the loss of bullets, and eliminate gun involvement. Major and malignant cases of ammunition occurred. Based on the actual situation of the army, we developed the “firearms anti-lost and anti-looting, anti-theft wireless alarm system”, and “guns and bullets combined, gun and ammunition wireless alarm system.”
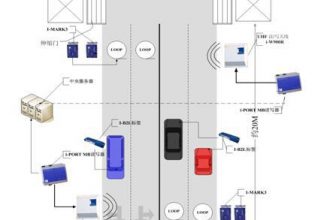
Firearms out of position alarm system
Miniature signal transmitters are installed in the buttstock of automatic rifles such as Type 81, Type 81-1, Type 95, Type 03, etc., which are installed on the butt. System monitoring and control are defined according to the actual situation of the sentry post. The range is the warning line. The signal collected by the receiver is analyzed by the single-chip microcomputer. When the sentinel is out of position 4-5 meters, the receiver loses the signal, and the voice prompts the gun to be out of position. If it comes back within the specified time, the system returns to normal. ; Otherwise, the alarm system will regard it as a warning that the gun has been stolen, and the alarm will sound an alarm after comparison is confirmed. (If you encounter an emergency, you can also call the alarm button.) After the alarm host in the duty room receives the alarm signal, it will display the sentinel number with sound and light, and send out voice messages and alarm sounds. The personnel on duty can arrange emergency teams for disposal. In order to understand the whole process of the sentinel’s duty situation and provide reference materials after an emergency occurs, the alarm host sets up a storage unit to comprehensively record the situation of the firearms.
2. System composition
1 RFID electronic label
electronic labelAs the most advanced identification code at present, it is not easy to be damaged, has reliable data, and is used as the only identification of the target for tracking and positioning. At work, managers use networked wireless identification base stations to track and locate the characteristics of long period, effective communication distance, etc., which is the best choice to replace bar codes and infrared identification. Install it on the controlled target.
2 RFID reader
The RFID read-write controller is composed of a microprocessor, a security module, a microwave communication controller, and RS232, 485, TCP/IP and other communication interfaces. It uses short-range communication protocols and microwave wireless transmission methods to achieve security with RFID For the purpose of reliable information exchange, RWU connects to the host computer through RS232, 485, WIFI, GPRS, TCP/IP, etc., receives control commands and data from the host computer and returns data.
3 Low frequency activator
4 or 6 channels of activation antennas, adjacent 4 or 6 rooms can share a low-frequency activator. In our positioning system, the positioning base station is the smallest base point, which is the closest base point of the positioning point. The distance to activate the tags is 3-3.5 meters, that is, each tag is activated within the range of 3-3.5 meters from the activator, and its positioning accuracy can be described as 3-3.5 meters. Activators in different areas have their own unique address codes. When a person enters the positioning base station with a semi-active low-frequency activation tag and is activated, the tag works normally. It sends the ID number of the tag to the outside world and also sends out the activation tag’s ID number. The address code of the activator, in this way, through the address code of the activator, we can locate the location of the label. When the tag is taken from one activator to another location, the uploaded activator address code will also change accordingly, thus forming a complete positioning system. The data uploaded by the tag is received by a large-scale positioning base station gateway, and the information is uploaded to the management center for processing, completing the entire positioning system. For the sentry off-position system, only the low-frequency activator needs to be reasonably arranged or by means of a coil around the city, which can effectively control the sentry off-site by about 5 meters.

Three, system characteristics
1. It has real-time automatic alarm function for robbery guns: the device has advanced detection functions, and under the 24-hour real-time operation monitoring control, it automatically alarms and informs the staff on duty when the gun is robbed or the gun is out of position.
2. Automatic alarm function for unauthorized departure from the sentry post: The system can automatically warn or notify the staff on duty when the sentry leaves the post without authorization according to the actual situation of the sentry on duty by the troops.
3. Anti-demolition and anti-demolition: It has the function of anti-demolition and anti-demolition alarm. The electronic tag in the gun has an anti-removal function. When the electronic tag set in the butt accessory box is illegally removed, it can automatically alarm. The equipment is small in size, good in concealment, and not easy to be destroyed by people.
4. Multiple alarm functions: firearms in position display, off-position warning or alarm, power failure reminder, emergency alarm, multi-level alarm, disconnection alarm.
5. With event real-time recording function: the system can detect on duty sentry in real time, and record the occurrence of events in real time, which is convenient for related personnel to review afterwards.
6. Arming and disarming: the time of arming and disarming can be set according to the time period of changing defense.
7. Strong anti-interference ability: adopts wireless frequency triple frequency hopping technology, adaptive space radio wave.
8. Full wireless mode, low power consumption: energy saving, low power consumption. The testing equipment in the field is low-power equipment;
9. The design idea is novel. The project comprehensively analyzed the key and difficult issues of the army’s duty work, and did systematic research on alarm review, alarm linkage, etc., and creatively proposed the design idea of combining civil air defense and technical defense, and combining external defense and internal defense. It has fundamentally solved the problem of uncontrollable guns on duty that has long plagued the army. At the same time, it has a wide range of application value in military equipment supervision, personnel monitoring and other related work, filling the gap in this field.
10. Wide adaptability: The system function adopts a modular structure, which can flexibly combine the functions of gun out of position, sentry out of position, emergency alarm and other functions according to actual needs, and has a wide range of adaptability.
11. Tracking and positioning: In case of special circumstances, the tracker can monitor the sound around the gun through the mobile phone or learn the geographic location of the off-site gun through the mobile phone text message. At the same time, the real-time geographic location of the gun can be found through the “location online” electronic map of the mobile phone or computer online platform.
12. Gun and ammunition separation and combination: As long as the sentry gun and the magazine are separated or the gun and the magazine are combined, the system will immediately issue an alarm, which greatly improves the rapid response ability of the troops to deal with the emergency situation of the sentry, and improves the security management of the sentry. level.
Applications:
A military battalion-level unit uses RFID to manage guns
All units of the army are equipped with “electronic inspections” or “electronic inspections” or “RFID“Automatic identification” system, and realize the network connection in the system, so that it has multiple functions such as automatic identification of passage, real-time recording of entry and exit, authorized passage, illegal entry and exit alarm, information query, data analysis, etc., for strengthening confidentiality, security, and security. Ensure the safety of weapons, ammunition, equipment, and key departments; it will play a positive role in real-time, accurate, and complete control of the personnel, vehicles, and objects of the troops, improving the effectiveness of scientific management of the troops, and enhancing the deterrence of the troops.
[ad_2]