RFID technology for real-time supervision and management of computer room personnel
[ad_1]
With the rapid development of lT technology and communication technology, there are more and more computer room equipment in data centers, communication base stations, communication computer rooms, various mobile, telecommunications, radio and television, private networks, and enterprise networks. Computer room equipment and information security have become important for operations. Basic guarantee. There are many problems encountered in the monitoring and management of the computer room. Individualized requirements and diversified management require an increase in the number of equipment managed by the computer room, which promotes an increase in the maintenance workload of the equipment in the computer room. Computer room managers are facing new challenges in their daily management. How can they quickly and accurately understand the actual conditions of equipment in the computer room and personnel in the computer room? Many advantages of RFID technology have been gradually applied to the field of computer room monitoring and management. The personnel supervise and manage in real time.
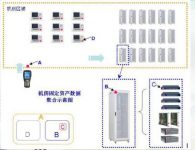
Due to the large amount of stored data, fast reading speed, and no need for human intervention in the process of reading data, RFID can perform rapid asset identification and inventory. Achieve accurate and rapid grasp of important fixed asset information.
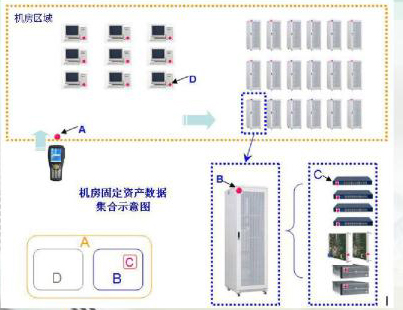
The management of computer room equipment generally faces the following problems:
The equipment in the computer room must be guaranteed to work 24 hours a day (if one of the equipment has a problem, there must be a spare equipment to ensure the normal operation of the network);
The equipment room has a large number and variety of equipment;
If there is a problem with the equipment in the computer room, it should be repaired and dealt with in time;
The equipment in the computer room needs regular maintenance to prevent malfunctions;
The maintenance of the equipment in the computer room needs to be undertaken by a professional company.
There are also other problems: For example, the maintenance methods and skills required for various equipment in the computer room are different, and the maintenance methods and required skills are also different; how to record, save maintenance records, repair records, and how to Query historical maintenance records, repair records, equipment failure statistics, and so on. The purpose of this program is to use RFID and information technology to manage network equipment inspections (maintenance), and solve the problem of low data recording efficiency and omissions of inspection items (many important inspection items are not inspected) during the network equipment inspection process. Know the patrol inspection methods and the difficulty of querying and counting historical patrol records.
Use RFID electronic tags to identify network equipment, establish network equipment database in the background (including inspection items, inspection methods, inspection cycles, etc.) and personnel information for each device. The inspector links to the mobile terminal of the inspection system, scans the equipment to be inspected through the RFID mobile device, inspects the network equipment item by item according to the inspection items maintained in the background, and records the inspection data, and finds the problems and hidden dangers in the computer room And deal with it in time to ensure the normal and stable operation of the computer room.
Core features of computer room monitoring system
Technical advantages:
The equipment adopts advanced data filtering technology and anti-cracking embedded encryption analysis algorithm to ensure data security in the communication process and ensure that the data judgment and recognition rate is close to 100% in complex situations; a highly encapsulated positioning system with hundreds of application cases; support A high-concurrency system with up to 2,000 devices and more than 10,000 location tags; rich peripheral interfaces compatible with mainstream video camera equipment.
Monitoring system construction structure and explanation:
It belongs to a perceptual positioning system, which utilizes the technical principles of long-distance recognition of equipment. Automatic identification and regional monitoring and management of tags entering certain areas. When a person wears a location tag and arrives at a certain area, the remote location system can detect the area where the person wearing the tag is currently located in real time and display it on the area map.
The computer room personnel monitoring and management system is mainly composed of four important parts: positioning tags, low-frequency locators, positioning base stations, and system software.
The location tag is an active electronic tag. Each tag has a unique ID number, and each tag number binds a person’s identity information. The RFID positioning tag actively sends out radio frequency signals at regular intervals, and carries the tag ID number, locator ID number, field strength value and other positioning information to the positioning base station, and then the base station uploads the detected tag signal and tag number to the The positioning server, because the physical location of each positioning base station is different, so the tag signal strength detected by the same tag with different positioning base stations is also different. The system database detects the different field strengths of the RFID electronic tags through each base station. Logic calculation to determine the current location of the label in the area.
RFID technology supervises and manages the personnel in the computer room in real time, and automatically collects data through RFID electronic tags through RFID reading and writing equipment, which can detect the location of personnel, the number of personnel, personnel information, dynamic changes of personnel, personnel seeking help in emergencies, and warning when entering dangerous areas Information and other information to be mastered. Efficiently deploy relevant personnel in the computer room to provide a basis for timely resolution of emergencies, reduce the workload of the computer room staff management, reduce labor costs, improve work efficiency, and ensure the normal operation of the computer room.
[ad_2]