The application of iris recognition in prison security management
[ad_1]
I. Introduction
Prisons are places where prisoners are held, and preventing prisoners from escaping is a particularly important task for prison management. In recent years, the walls and buildings in prisons across the country have undergone standardized renovations. Several cases of escaping from the prison gate in 2009 have drawn everyone’s attention to the prison gate access control system. In this paper, the characteristics of the access control system are summarized. Taking the transformation of a prison access control system as an example, the structure of the access control system is discussed, and the application of the iris recognition technology in the entry and exit passages of the prison access control system is described.
2. Overview of access control system
The access control system, also known as the access management control system, is a new modern security management system. In recent years, with the development of proximity card technology and biometric identification technology, the access control system has developed by leaps and bounds, and has entered a mature period. Various technical systems, such as out-of-order keyboard access control systems, have their own advantages in terms of security, convenience, and ease of management, and the application fields of access control systems are becoming more and more extensive.
The iris is the annular tissue between the pupil and the white of the human eye. It is the visible part of the human eye. The application of iris recognition technology in access control systems is a type of biometric recognition technology. It has four characteristics in identity recognition: collectability, uniqueness, stability, and anti-spoofing.
3. Access control management of prison personnel’s access channels
The gate of the prison is one of the key parts of the prison to prevent prisoners from escaping. Especially in 2009, there were two cases of prisoners escaping through the prison gate, which caused prison management leaders and security companies to think deeply about the prison access control system.
1. Special requirements for prison access control systems
As a high-security special area, the control and management of the door is very important. In line with the concept of “wide entry and strict exit”, all access control uses the card to enter the door without the need to verify the password, and the door must be opened by swiping the card (or fingerprint, face recognition, iris, etc.) and passing the verification; at the same time, due to all There are production and business activities in prisons. Personnel from external units often enter and leave the prison. The access control system itself must manage and record the entry and exit of personnel from external units. After the access control system is powered off, all door locks must be manually closed and opened by police officers; anti-trailing function , that is, when the police go out in a normal way, if there is a trailing prisoner, the access control can prevent the prisoner from escaping from the access control in some way.
2. Implementation of the prison gate access control system scheme
It can be seen from the previous description of this article that the iris scanning method is the most reliable method in the current access control system. In this article, an example of access control in a prison is used to introduce the structure and function of the prison access control system.
3. Design of access control structure
(1) Single door A/B door access control system
Usually regulatory agencies (prisons, detention centers, etc.) adopt a single AB door management model as shown in Figure 1. The system realizes the combination of double-door linkage interlocking function, radio frequency identification technology, fingerprint identification, and face identification to control the entry and exit functions of personnel, and creates a buffer area on the outside of door B. The implementation of the access control system is as follows: when entering the supervision area, swipe the card to open door A and enter the access control area. When door A is closed, the access control personnel will open door B and enter the internal area. When leaving the supervision area, swipe the card from door B to enter the access control area, and then the access control center will verify it, that is, the personnel on duty behind the explosion-proof glass or the control center will check whether the personnel in the surveillance video meet the exit permission, and if there is permission, turn on A Door, this is the whole process of entering and exiting.
The advantages of the single access control system are: simple structure and convenient construction; the disadvantage is that it is not very convenient when a large number of people enter and exit at the same time, which may cause time delays and the possibility of wrong release. For example, when an illegal person illegally obtains an access card from Figure 1 and enters the access control area from door B, if someone happens to enter from door A and opens door A, the illegal person is very likely to escape through door A. .
(2) Dual-channel access control system
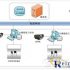
In order to make up for the shortcomings of the single A/B door access control system, combined with the needs of the actual application of the prison, a dual-channel access control system is designed, as shown in Figure 2. The entrance passage is mainly composed of doors A1 and B1; the exit passage is composed of doors B2, C1, A2, and C2. The entrance/exit passages are separated by high-strength metal railings, which not only achieves the effect of perspective, but also prevents people from crossing. In daily work, not only prison staff, but also outsiders who temporarily work for the prison go in and out of the prison. In terms of safety and convenience, the two types of people use different entry and exit modes. Prison officials’ identity information, photo information, and iris information are pre-recorded in the computer host of the access control system, and personal information can be compared when entering and leaving. Temporary registration of identity information for outsiders before entering the door, and prison officials lead in and out. The following describes the workflow of the dual-channel access control system in detail.
There are four cameras in the access control system and its function is to record 24 hours a day. When an unexpected situation occurs, you can view the recording to confirm the process when the unexpected situation occurred. In the entrance passage, door A1 and door B1 are interlocked, and only one of them can be opened at the same time. A radio frequency card reader and a snapshot camera are installed at door A1. Prison officials can enter the entrance channel by swiping their card. Outsiders must first follow the prison’s workflow, register their identity information, and receive a radio frequency card. Swipe the card before entering the door A1, the camera will take a picture, and the photo and card information will be recorded into the access control system. At the same time, the information of the police officers leading the outsiders should also be registered in the outsider information. To ensure safety, the opening of the B1 door is manually controlled by the control room. Persons entering the prison must also swipe their card at gate B1 to confirm the person registered to enter the prison in the access control system.
The card reader of the buffer door registers all the access cards of the prison, including the access cards of the prison staff and the access cards used by the personnel temporarily entering and leaving the prison. The cardholder swipes the card to open the door, and the door is automatically locked after passing through. It is not networked with the dual-channel access control system, and mainly serves as a simple buffer. But its shutdown can be controlled by the control room. When an emergency occurs, the access control must be closed or the buffer door must be closed during the entire access control period. At this time, no card can open the door.
Doors B2, C1, A2, and C2 form an exit passage. The cardholder enters the door by swiping the card at gate B2, and waits for the identity check at gate C1. In Figure 2, the identification room is a space that allows only one person to pause. Gate A2 and gate C1 are the logical relationship of opening first and then opening. That is, when someone is in the identification room, both doors are closed. If the identity confirmation is legal, the door A2 is opened, the person passes through the door A2, and after the rear door A2 is automatically locked, the door C1 is opened, waiting for the person to enter the identity confirmation room. Once someone opens the door C1 to enter, the door C1 is automatically locked. There is an iris recognition camera and a capture camera in front of the explosion-proof glass window of the identity confirmation room. When the prison officials confirm their identity, they swipe their cards first, and the computer host of the access control system automatically calls out their identity information and iris information, and then the prison officials look directly at the iris camera. If the comparison is successful, the identity is correct, otherwise, the identity is wrong. When the identity is correct, the access control personnel manually open the door A2 and allow the personnel to pass through the door A2; otherwise, the emergency plan of the prison shall be implemented. When outsiders confirm their identity, first swipe their cards, and the computer host of the access control system automatically calls out the pictures they took at door A1 when they entered the door and the information of the prison staff who led them in, and then the outsiders look at the capture cameras to carry out Take a photo. After the photo is taken successfully, the access control personnel will compare the two photos, and at the same time ask the prison officials who have led him. If the information is correct, it is allowed to pass, otherwise it will be handled according to the emergency plan. After the foreigners pass through, the information at the time of passing will be kept in the computer for a period of time for information inquiry. The last door C2 of the exit passage is also controlled and opened by the access control personnel. It is used as a safety door for door A2. Once an illegal person passes through gate A2 without passing the identity verification, there is gate C2 as a block to delay their passing time. At the same time, A2 and C2 also have an interlock function to ensure that only one of the doors can be opened at the same time.
(3) Power configuration of access control system
Prisons are generally dual power systems, and there is usually no power outage. However, in order to ensure 24-hour uninterrupted power supply and the occurrence of unexpected situations, the access control system must use UPS uninterruptible power supply and emergency power generation system. The newly installed UPS power supply system needs to ensure that the power supply of the access control system can be guaranteed within 24 hours after the power failure, so as to ensure that the battery can be replaced for several years.
(4) Access control system lock configuration
At present, the electronically controlled locks are mainly composed of electric control locks, electric mortise locks and electromagnetic locks. Changes in temperature will affect the deformation of the metal door, thus affecting the positioning of the female lock and the male lock. Since the electromagnetic lock has a certain movement margin, a small amount of deformation of the door will not affect its normal use. At the same time, the electromagnetic lock has fewer accessories, so there are fewer faults. The installation of the lock should take into account the anti-pick, and also the force of the door to prevent the deformation of long-term use. Therefore, the electromagnetic lock should be installed concealed, and the installation position should be about 1.4 meters away from the ground. The position here is the position where ordinary people push the door, so the lock is just laborious and will not cause deformation of the door.
Prisons are generally closed from 22:00 in the evening to 6:00 in the morning. At this time, the management of the access control can rest. In order to prevent accidental power failure, etc., doors A1, B1, B2, and C2 in Figure 2 are equipped with anti-theft locks, which must be manually locked with a key. At the same time, the four doors should not have keyholes on the side facing the prison gate.
4. Vehicle access control management
The gate of the prison is divided into two channels, namely the personnel access channel and the vehicle access channel. The structure and management of the vehicle access channel are described below. The general structure of the vehicle access channel of the prison is shown in Figure 3. The tire breaker is to defend the yard, that is, to prevent the prisoners from hijacking the vehicle and forcibly hitting the gate to escape. Usually the tire breaker should be in the open state. When a normal vehicle needs to pass through the electric gate A, close the tire breaker and open the electric gate A; when the vehicle passes, close the gate A and open the tire breaker at the same time. The two electric gates must have an interlock function, that is, the two gates cannot be opened at the same time. At the same time, the door must have a locking device, that is, when the door is not powered on to open the door, the door cannot slide freely, to the extent that manpower cannot push the door. When the vehicle passes through the gate, it must pass the inspection of full-time personnel, and no prohibited items can be brought into the prison. More importantly, no prisoner can escape from the prison by hiding in the car. Therefore, there are usually underground cameras to assist the inspection. In order to make the vehicle chassis pass the camera just before the inspection, the vehicle should be instructed to move or be required to drive and stop according to the road signs.
V. Conclusion
The structure, function setting and management of the prison gate together affect its security. This paper mainly introduces the relevant concepts and technologies of access control, and introduces the structure and general workflow of the personnel passage and vehicle passage of the prison gate with examples. In the national prison system, the construction of personnel passages is affected by the specific prison leadership ideas, as well as by the product plan recommended by the security integration unit. Therefore, the structure of the personnel passage and the access control products used are different. The access control structure and management process of the personnel passage introduced in this article is the real form of the transformation of a prison access control system in 2009. Before and during the reformation, various relevant units and personnel conducted in-depth discussions and inspected several prisons. After the completion of the access control system renovation, it has been officially nearly a year. Its security and the smoothness of personnel passage are very good, and the leaders of the prison and labor reform bureau have expressed their affirmation.
[ad_2]