Analysis of Access Control Management System Based on RFID and Web Service
[ad_1]
The access control system, also known as the entrance and exit control system, is a system that manages and controls the entrance and exit of important areas or passages. With the development of society, it is no longer limited to simple management of door locks or keys, but a new modern safety management system integrating automatic identification technology and modern management technology, which has become an extremely important part of the safety protection system. It is widely used in intelligent buildings, offices, hotels and other occasions. At present, the main control methods of the access control system are: fingerprint recognition, face recognition, iris recognition and radio frequency card, etc. The first three methods are all biometrics, which use the characteristics of a certain part of the human body as the identification carrier and means. Their uniqueness and non-reproducibility determine that they are the safest authentication methods, but they are expensive and difficult to popularize. When it comes to personal privacy, it is only suitable for high-end and absolutely confidential places.
The radio frequency card is a product of the combination of radio frequency technology and smart card technology. It has the characteristics of simple use and convenient maintenance.
In order to improve the modern management and remote monitoring capabilities of the access control system, an access control system based on Web technology is introduced. The system adopts wireless radio frequency technology. When a non-contact IC card appears in the radio frequency range of the reader, the card is read and the information is transmitted to the server through serial communication for related data processing, and a management platform based on the C/S mode is constructed. , The administrator can query and control the access controller through the Web page, so as to effectively realize the real-time monitoring of information at any location on the Internet.
1 System architecture
The system uses a non-contact IC card, and uses radio frequency identification technology RFID (RadioFrequencyIdentificaTIon) to detect the IC card. When the IC card is close to the reader, the reader can accurately identify it and send its serial number to the main controller. Connect to the background database with the PC through the application to obtain the user information corresponding to the card number.
If the card has been registered, it will pass the verification and notify the controller to open the door, and record the card number and time of opening the door, otherwise, it will prohibit passage and inform the cardholder to leave.
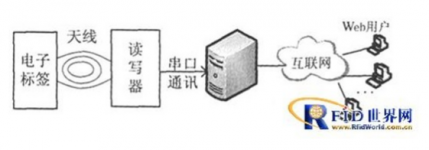
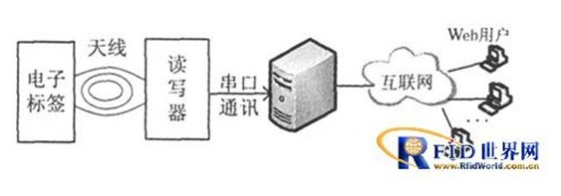
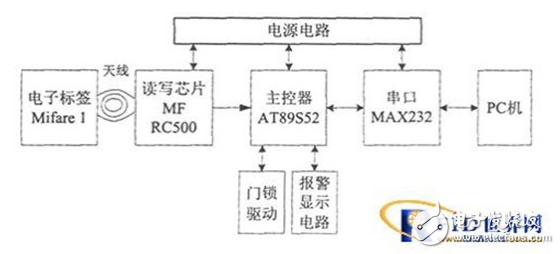
The system consists of five parts: electronic tag, reader, serial communication, server and user terminal. As shown in Figure 1. The reader is the core of the system. It communicates with the IC card (electronic tag) through radio frequency signals to complete the work of reading, storing and sending data. It can work independently or networked. In this article, RS232 serial communication is used to connect to the server. .
The C/S structure is adopted between the server and the user side. The connection between the application software and the database SQLSERVER2000 is realized through the ADO object, and the two are interconnected through the local area network. When the system administrator grants authority, users can query, count, and print all relevant records of the management system.
2 hardware design
2.1 Overall hardware design
The radio frequency reader is the core of the system. It is composed of the main control circuit, radio frequency read and write circuit, antenna coupling circuit and antenna. It is responsible for radio frequency signal processing and data transmission, and completes the task of reading the IC card serial number. as shown in picture 2.
The electronic tag, that is, the radio frequency card, is composed of an IC card and an induction antenna, and is encapsulated in a standard PVC card. The chip and its antenna have no exposed parts. The card does not need a power source. When the card is close to the reader within a certain range, the data is read and written through the transmission of the antenna. This article uses Philips’ Mifare1 card, which is based on the ISO14443TYPEA international standard. Each card has a unique serial number in the world and has an anti-collision function.
The function of the antenna is to generate magnetic flux, provide power to the card, and transmit information between the reader and the card. The effective electromagnetic field range of the antenna is the effective working area of the system.
The read-write chip selects the special chip MFR500 produced by Philips for reading and writing Mifare1 cards, and the working frequency is 13.56MHz.
The main controller is composed of AT89S52 single-chip microcomputer and its peripheral circuits, and is responsible for controlling the read-write module, serial communication with the PC and the control operation of the external equipment. The operation of the one-chip computer to the read-write module is to realize the operation of the Mifare1 card by controlling the MFRC500.
It is a bridge for data transmission between the single chip microcomputer and the IC card.
2.2 RF circuit design
The core of the radio frequency circuit is the read-write chip MFRC500, which is a bridge for data transmission between the single-chip microcomputer and the IC card. Its connection with the one-chip computer is shown as in Fig. 3.
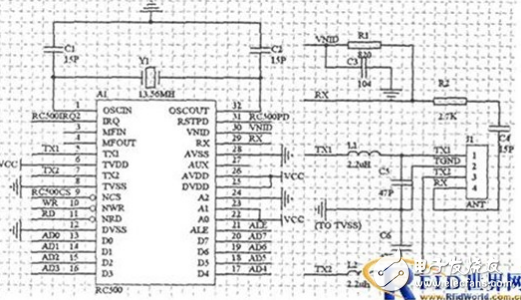
The one-chip computer adopts the interrupt control method to the read-write chip, and the interrupt control port INT0 is connected with the IRQ pin of the MFRC500. There are 64 registers inside the MFRC500. The single-chip microcomputer configures and operates them by writing control commands into the registers. The power-down detection pin RSTPD is connected to the single-chip P2.0 pin, the NCS pin is connected to the P2.7 pin, and NWR and NRD are respectively Connected to the read and write ports WR and RD pins of the single-chip microcomputer, the data ports D0~D7 are connected to the P0 port of the single-chip microcomputer quartz crystal oscillator to produce a working frequency of 13.56MHz. The low-pass filter composed of L1, L2, C5, and C6 is used to suppress the crystal oscillator circuit at the same time Generated high-order harmonics. The receiving circuit is composed of R1, R2, C3, and C4. The VNID potential generated inside the MFRC500 is used as the input potential of the RX pin. In order to reduce interference, a capacitor C3 is connected to the VND pin to ground, and a divider must be connected between RX and VNID. It is better to connect a capacitor (C4) in series between the antenna coil and the inverter (R1). In order to obtain better performance, these components should be close to the antenna pins RX, TX1, and TX2 of the MFRC500 chip when wiring the circuit board.
2.3 Antenna circuit design
In order to obtain a stable and reliable radio frequency signal, the performance of the antenna is very important, which directly affects the range and sensitivity of the reader. The performance of an antenna is related to its quality factor Q, which is related to the geometry, size, number of turns and other factors of the antenna.
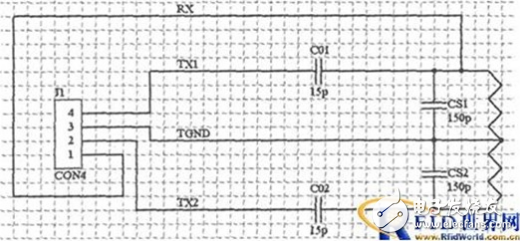
The system design is a close-coupled IC card, and the antenna is made of PCB antenna, that is, the antenna circuit board is directly made on the PCB board. This method has good stability.
When the antenna is connected to the read-write chip, an external matching circuit is required. As shown in Figure 4. The system estimates the antenna roughly and changes the capacitance of the matching circuit to achieve the best read and write distance.
3 software design
The system software includes two parts, the lower computer and the upper computer management system. Among them, the lower computer uses AT89S52 single-chip microcomputer as the core to realize the reading of the reader, access control and serial communication. The programming language used is C language, and the compiler is KeilC51. The upper computer management software runs on the server, and uses VisualC++6.0 and SQLSever2000 for system management and database development, including serial port communication, monitoring management and information release. Among them, the monitoring and management software is used to implement tasks such as user registration, record query, and deletion, and information release is used for administrators to view access control log records through web pages.
3.1 Software design of lower computer
The software runs on the single-chip microcomputer to complete the reading of the card number, the control of the door lock and auxiliary circuits, and the serial communication. Figure 5 shows the flow chart. The core of the software is to realize the communication between MFRC500 and Mifare1 card, and the communication needs to follow the ISO14443TYPEA standard transmission protocol. The card reading process must be carried out in strict accordance with a fixed sequence, that is, the response to reset anti-collision selection card authentication card reading and writing. Since the card is readable, only the serial number of the card needs to be read, and there is no need to write to the corresponding sector, so the authentication step can be ignored. The main code is as follows:

3.2 Host computer software design
In the VC++6.0 programming environment, use the CSerialPort class to realize serial communication, receive the sent IC card serial number, and then access the database through ADO technology to obtain the user information corresponding to the card for verification processing.
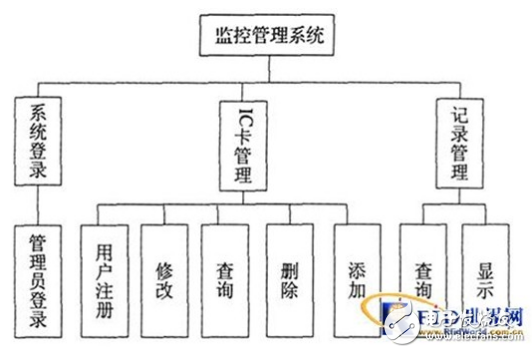
The system is based on SQLSERVER2000 for database development. Administrators must enter account numbers and passwords to prevent non-system administrators from illegally logging in to the system. After that, the administrator can complete the registration, query, modification, and deletion of the card number information, and record the visitor information (user and transit time) in the database for data statistics and query, etc. The functional modules of the monitoring management software are shown in Figure 6.
The information publishing module is implemented based on ASP.net. The implementation process is mainly to read the monitoring management information table of the SQL Server database through ado.net, make an information publishing website and deploy it to the IIS server, so that users can access webpages at any location. View system information and access control records.
4 Program operation
Taking the access control management of the laboratory of the School of Electronic Engineering of Guilin University of Electronic Technology as an example, the software and hardware design of the system is realized. After the administrator enters the account and password, he enters the main interface of the monitoring and management software as shown in Figure 7.

After testing, the effective working distance of the IC card is 6cm. When the IC card responds, the system automatically displays the card number, card user information, and access time, and automatically stores it in the background database. Since the Mifare1 card has a globally unique serial number, member information can be bundled with the IC card serial number and stored in the database during member registration. In this way, you can search accurately according to the time or directly according to the name when consulting the information.
5 Conclusion
The proposed access control management system based on RFID and Web services provides an intelligent control and remote management mechanism for the entry and exit of important departments. Using radio frequency technology RFID to achieve keyless access, not easy to lose, and reusable; using SQL database and Web services to achieve remote monitoring of access control, easy to operate, flexible and safe, and has a wide range of applications in smart homes, office access, logistics and other occasions Application prospects.
[ad_2]