Application and case analysis of access control system in office building
[ad_1]
An ordinary office building may have dozens or even hundreds of companies stationed in the office, and there are many and mixed people, which brings severe challenges to the traditional safety management of personnel entering and exiting. A common traditional method is to register and release the staff in the communication room. This method is time-consuming, labor-intensive and easy to cause errors.
The electronic access control system brings a convenient and concise means to this series of tasks. The electronic access control system works in the form of a personal identification card, and each person or visitor who has the right to enter is issued a personal identification card, which is equivalent to a key. The system judges whether the card holder can enter according to the card number of the card, the number of times the card is available and the current time information, etc., if so, the door will be opened automatically, otherwise the door will not be opened. For places requiring attendance, the access control system can also record whether each employee goes to and from get off work on time. Another advantage of the access control system is that you can add or delete a card at any time, without worrying about what loss a card will cause.
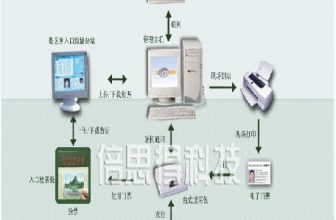
The basic composition of the access control system
The access control system is composed of card reader, controller, electromagnetic lock, identification card and computer.
Identification card
It can be divided into two types: contact type and non-contact type. Among them, there are EM cards, HID cards, MIFARE cards, LEGIC cards, TEMIC cards, and many other types of non-contact cards. Nowadays, EM is mostly used in domestic office buildings. Cards, HID cards, and MIFARE, TEMIC cards are also used.
Card reader
According to the different types of cards, there are many types of card readers. At some advanced and confidential entrances and exits, the use of fingerprint readers and palm readers as terminal identification devices is the future development trend.
Door lock
According to different applications, electromagnetic locks can be divided into electric bolt locks, magnetic locks, and cathode locks.
Controller
The core of the controller access control system, which consists of a microprocessor and corresponding peripheral circuits. If the card reader is compared to the eyes of the system and the electromagnetic lock is compared to the hands of the system, then the controller is the brain of the system. It determines whether a certain card is a valid card registered in the system and whether the card conforms to it. The limited period of time thus controls whether the electromagnetic lock is opened.
Engineering application case analysis
Product selection
In the access control system project of an office building, we chose the D.one access control system as the brain of the access control system. D.one’s DW series controller fully takes into account the safety, stability, convenience and availability of the controller itself. Scalability, the controller itself has a variety of protection measures such as lightning protection, high-voltage impact protection, and surge absorption. The photoelectric isolation technology is used in communication to prevent interference and intrusion from the transmission line to the greatest extent. It has multiple input and output ports. It can be conveniently matched with other systems in the building, can be connected to multiple types of card readers, supports multiple different access methods and multiple time periods, multiple authorization groups, and supports RS232, RS485, TCP/IP, etc. in communication. Suitable for large and small applications.
Support online real-time monitoring and offline operation, equipped with a backup battery, power-down operation and data protection. In the software, the classic WIDOWS operation interface is simple and easy to use and has different browsing rights. It can be applied on WIDOWS 98, WIDOWS 2000, NT and other operating systems, integrating access control and attendance; you just need to move your mouse easily You can complete the management mode you want. The software has three versions of stand-alone, WEB and server management modes, suitable for various user needs. The office building engineering architecture has a total of 256 access control points in the office building. Three different management modes of the D.one access control system are adopted in the specific engineering design:
Stand-alone management mode
Each access control point is independent of each other and does not need to have any connection relationship. At this time, we adopted the stand-alone mode. This mode does not mean that each computer can only control one controller, but only that each connected to the controller Each computer has an independent database and independent management mode. In fact, each computer can be connected to at least 64 controllers and can manage 512 one-way access doors. D.ONE’s DW series products have 1 door and 2 doors. There are multiple models such as 4 doors, 8 doors, and all models can share a set of software. In other words, in the same system, according to the number of access points, you can use 1 door, 2 doors, 4 doors, 8 doors Mixed mode to achieve the best equipment.
In the access mode, we have set different access methods. For example, in the computer room, warehouse and other confidential places, you can set the password + card or dual card access mode, and set the two-way access mode in the place where the number of people needs to be counted. , And it can be set to one-way access mode in general places. For any access control point, we set different access control time periods and attendance time periods according to the needs of different companies, and the computer automatically completes your access control management and attendance statistics. All access control points can be linked to equipment such as fire alarms, surveillance, etc., and can also be linked to image recognition systems.
Server management mode
The biggest difference between the server management mode and the stand-alone management mode is that it uses a server for centralized management. All controllers are connected to the server. The setting of all access points and the download of data are completed by the administrator in a unified manner. Each sub-station They can be operated through the WEB, and their permissions are also assigned by the administrator. For example, the general access control points can only browse the card status of the staff in the department and complete the attendance statistics of the staff in the department and upload them to the server, but some departments are different. For example, the security department can not only browse and complete the department’s attendance, but also arm and disarm, and issue temporary cards.
Server + stand-alone management mode
The office building has an intranet, but the controller needs to be connected to a different computer. At this time, we adopt the third management mode: server + stand-alone version. Specifically, the server has server version software and database, which can realize most of the access control and attendance functions such as card authorization, distribution, time period setting, etc., and each substation also has its own software and database, which has certain management Permissions, such as the entry and exit time of the personnel in the department, the setting of entry and exit groups, and the setting of alarms, etc., complete the attendance of the department and have certain modification rights as needed. Each substation downloads the controller connected to its own PC. Data, and generate various reports to the server, and the server conducts comprehensive evaluation based on the reports from each sub-site.
Problems in installation and commissioning
No matter how perfect the system is, it still needs people to complete it. Therefore, in order to maximize the functions of the access control system and reduce human errors, we should pay attention to the following aspects during the installation and commissioning process:
Anti-electromagnetic interference
For card readers and door opening buttons, special attention should be paid to preventing electromagnetic interference, especially interference problems such as lighting switches, electric typewriters, and computers. When conditions permit, the card reader should be installed at a distance of more than 30cm from the power source.
Prevent attenuation of the transmitted signal
The installation of the controller should take into account the distance between the controller and the card reader. The ideal transmission distance is within 50m. For signal transmission cables, cable shielding and signal attenuation due to long-distance transmission must be considered. In the pipeline construction process, steel pipes and cable trays should be used, and reliable grounding should be done.
Controller and system software debugging
System debugging is a key link to ensure the quality of the access control system. The focus is on the debugging of the controller and the operation of the system software. The debugging process of these two parts must be carried out by the manufacturer at the same time. The function of the controller is that besides the card reader input, the relay linkage output function should be set according to the needs, the time and place of alarm generation and activation such as camera, alarm horn, etc.
[ad_2]