Application case of non-contact CPU card technology in China Science and Technology Museum
[ad_1]
technical background
Since the Mifare 1 card algorithm cracking incident was widely concerned by social media in February 2009, the security of non-contact IC cards has become one of the hottest topics in various media in the smart card industry; the security algorithm of the cracked Mifare 1 card chip, It is currently the most widely used non-contact IC card security algorithm in the world! It is conceivable that if this scientific research result is maliciously used by people, then most access control systems will lose the meaning of existence, and other IC cards using this technology, such as campus all-in-one cards and enterprise all-in-one cards used by college students, will also be used. Faced with huge security risks.
The Ministry of Industry and Information Technology of the People’s Republic of China also issued relevant documents across the country in response to this incident, requesting all localities to carry out investigations and responses to the use of the Mifare 1 card. The schematic diagram of M1 card cracking is shown in Figure 1. The CPU card and CPU card all-in-one card system with domestic independent intellectual property rights can effectively solve the serious security risks of the current traditional all-in-one card system based on the Mifare 1 logic encryption card. as shown in picture 2.
.jpg)
User situation
The China Science and Technology Museum is the only national comprehensive science and technology museum in my country. It is a large-scale science popularization infrastructure that implements the strategy of rejuvenating the country through science and education and the strategy of strengthening the country through talents, and improves the scientific quality of the people. The first phase of the project was completed and opened on September 22, 1988, the second phase of the project was completed and opened on April 29, 2000, and the new building was completed and opened on September 16, 2009.

Users require that all-in-one card systems be built throughout the museum, including applications such as security access control systems, consumer systems, attendance systems, conference sign-in systems, personnel visitor management, parking lot management, and self-service systems. Provide intelligent all-in-one card services for the employees and visitors of the Science and Technology Museum. Considering that the M1 card has serious security risks, users require the construction of an enterprise all-in-one card system based on the non-contact CPU card technology, and the non-contact CPU card is used as the identity The carrier of identification, transaction and payment.
System goals
The Tongfang Enterprise Card System is built with the current world’s advanced non-contact CPU card technology as its core, based on the enterprise local area network, and adopting popular network structures, communication modes and development tools. Realize the functions of “one card for multiple use” and “one card use” in the enterprise.
Enterprise employees in the new China Science and Technology Museum use an authorized CPU card to realize consumption, access control, attendance, comprehensive inquiry, personnel access and other “one card” services through the software functions and hardware supporting equipment of the one card system; foreign visitors can Through a CPU card, all kinds of consumption within the enterprise can be realized. The system can also be extended to conference sign-in, medical treatment, book borrowing and other systems; it can also be connected and interacted with enterprise HR systems, OA systems, finance, building automation systems and other systems. And sharing data information, providing enterprise managers with various types of comprehensive query and comprehensive analysis of basic data.
System composition
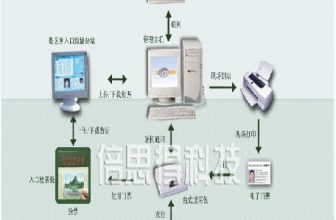
The system includes a card center platform, transaction applications, identity applications, and self-service applications. Among them are key management module, card initialization module, central management module, card management module, consumption management module, consumer POS module, transaction clearing, access control management module, attendance management system, conference sign-in system, Web comprehensive query module, Self-service machine module and other components.
.jpg)
All-in-one card center platform system: It is the core layer of all-in-one card, which is composed of all kinds of modules such as all-in-one card center database, identity management, transaction settlement management, system management, etc. It mainly comprehensively manages all kinds of application subsystems and hardware terminals of all-in-one card, and manages business flow And data flow.
All-in-one card application subsystem: It is the application service layer of all-in-one card, which provides all kinds of application function management of all-in-one card, including card management, comprehensive inquiry, consumption, access control, attendance, conference sign-in, visitor management, vehicle access monitoring, elevator control and other subsystems . Through various POS machines, card reader equipment, collecting and reading card information of cardholders, and managing various cardholder information through computer terminals, providing cardholders with various card-related services.
Third-party application interface: the one-card system provides standardized interfaces and open communication protocols, which facilitates third-party application subsystems (such as personnel management systems, OA office systems, building automation systems, etc.) to access the one-card center platform through a unified application interface. Data sharing and data exchange.
Main functions of the system
1. All-in-one card center platform
It is the data center, security control center, card management center, and clearing accounting center of the entire system.
Settlement management: storage and processing of all transaction and management data; system security control includes application authorization and
Equipment authorization management; blacklist management; clearing account management; account management, etc.
Card management: Provide management functions such as unified issuance of CPU cards, loss reporting, card replacement, card replacement, card cancellation and account cancellation.
2. Application subsystem
Security access control management
The access control management system is composed of a safe, reliable and easy-to-use smart card door lock, CPU card access control card reader, controller and management software, and can be used online or non-networked. The smart card door lock system can set the employee’s access authority according to the department, administrative level and actual needs of each employee. Unauthorized personnel cannot open the door lock or pass. The door opening record is processed and analyzed to obtain personnel entry and exit information; the system will send out real-time alarm information when situations such as illegal entry and door locks are broken. Fire linkage can be realized, and real-time monitoring of linkage can be realized.
The access control management system adopts the CPU card security access control card reader, adopts the safety certification of SAM and CPU card, and establishes a complete and rigorous key management system, making full use of the CPU card security features. After the key is injected into the SAM card, it cannot be read externally. Insert the SAM card into the card reader device, and perform two-way verification through the SAM card and the CPU card. The verification message is calculated by a random factor. The same card is swiped on a device, and each time it is different, the appearance of “fake cards” is completely eliminated.
Personnel visitor management system
The guest system client is deployed at the doorman management window entering and exiting the office building. The system is composed of management software, card issuers, first- and second-generation ID card reading devices, digital cameras, etc., and performs data communication with the identity authentication server of the All-in-One Card Center. After the visitor obtains the temporary access card, he can pass within the permitted range.
According to the actual needs of the company, visitor management can be connected with the existing access control system and elevator control system to realize that the respondent can swipe the card to confirm at the guard (safer and more reliable), and at the same time, the visitor card issued by the guest can automatically authorize the activity area (up to It is the permission of the interviewee). After the visit, swipe the card at the doorman to automatically complete the cancellation of the card.
Attendance Management System
The attendance management system is based on the employee’s use of CPU card to swipe the card data at the access control or attendance machine, and is processed by the background attendance management module to fully realize the automation of employee attendance management. The system can flexibly set up and down time, shifts, and formulate different attendance systems. According to the employee’s card swiping record, it can quickly and accurately calculate the employee’s on-duty and off-duty time, and generate the attendance report required by the user. The summary results are processed. The wages of employees can be directly calculated.
Parking lot management system
The parking lot management system is similar to the general access control management system. Employees enter and exit the parking lot automatically with a valid card, and visitors get a temporary entry card at the ticket gate before entering the parking lot. The system collects data of incoming and outgoing vehicles in real time, can query the parking status of the parking lot at any time, and generate various reports at any time. The parking lot management system can be divided into two types: free parking and paid parking.
Consumption Management System
The CPU card consumption management system can realize consumption management such as internal employee dining, enterprise or shopping in the park. The system can authorize and set consumption functions and operators such as canteens, commissaries, etc., establish consumption items and accounts, employees consume with cards, and the system authenticates the card security and encrypts the consumption information. The consumption information is real-time or timed. Send to the back-end center system as the basis for unified clearing and accounting management.
Online Patrol Management System
The system can set the security guard’s patrol route and time according to management requirements, and the security guard on duty must trigger the designated patrol point within the specified time. A series of induction cards representing different points are installed on the patrol line. When patrolling to each point, the patrol personnel use a handheld patrol machine to read the card, and record the card number and time representing the point at the same time. After the inspection is completed, the patrol machine transmits the data to the background system for processing through the communication line, and can record and assess the inspection situation (personnel, location, time, event, etc.).
Self-service query system
Provides inquiries about all transaction and management information (such as account information, transaction information, card service information, etc.) of the enterprise all-in-one card system. The inquiry content can be set according to the position, and people in different positions can inquire different information.
3. Third-party interface
The enterprise/park card system will provide interfaces with existing information systems such as financial statistical information, personnel and wage systems, library management, medical management and other systems, as well as intelligent building automation systems, to achieve integration with existing information resources and protect existing investments.
System advantages
Compared with the traditional enterprise card based on Mifare 1 logic encryption card, the Tongfang CPU card enterprise card has the following advantages:
1. Security access control system based on CPU card technology
The access control management system adopts the CPU card secure access control reader with state-owned independent intellectual property rights. The CPU card secure access control reader has a built-in PSAM card slot and SAM module. It can store various application secrets by issuing PSAM cards or using SAM authentication modules. The key, through internal/external authentication, mutually authenticates the transaction card and terminal equipment to ensure the legality of the transaction medium.

Adopt the safety certification of SAM and CPU card, establish a complete and strict key management system, make full use of the safety features of the CPU card, and completely solve the security vulnerabilities of the Mifare 1 logic encryption card. Ensure the safety of the entire access control security system.
2. Key management and initialization are led by the user
In the information system with CPU card as the application carrier, the management of the key is the basis for the safe operation of the entire system. The main task of the key management system is to generate, issue and update keys, which is directly related to the security of the entire system. Customers can generate and manage various application keys by themselves through the key management module of the Tongfang CPU Card Enterprise Card, and complete the initialization of the card by themselves, ensuring that customers have the initiative in key management and card issuance.
3. The terminal equipment supports SAM card slot and authentication
The terminal equipment in the Tongfang CPU Card Enterprise Card can be divided into several categories, one is consumer, the other is recharge, and the third is identity authentication. The PSAM card embedded in the consumer terminal only reduces the key for the money, and the recharge terminal needs to be online. Go to the hardware encryption machine to obtain the recharge key. The identity type can be done according to the actual situation. The identity type PSAM card can be issued. For example, the card content can be read correctly after the card reader is placed in the access control card reader to ensure the CPU card High security of information reading and writing.
4. Strictly follow the transaction standard specifications of the CPU card
The Tongfang CPU Card Enterprise Card will adopt the People’s Bank of China Financial CPU Card Transaction Standards and regulations, and authenticate with the financial encryption machine in the background during the financial transaction process of the CPU card. The key and algorithm for calculating the transaction authentication code will be stored in the financial encryption machine. When the end-of-day transaction flow is cleared and cleared, it needs to be connected to the hardware encryption machine in real time to verify the TAC code of the transaction flow to ensure the accuracy of transaction records And security.
5. The stability and scalability of the software platform architecture
The Tongfang CPU Card Enterprise Card System adopts J2EE to simplify the architecture of complex problems related to the development, deployment and management of enterprise solutions, and provides the application requirements of high availability, high reliability and scalability of the middle-tier integration framework.
The one-card system integrates the most popular three-tier system architecture, and divides the entire business application into: presentation layer (UI), business logic layer (BLL), and data access layer (DAL). Facilitate system expansion and distributed applications.
The platform development uses JAVA language, adopts Struts + Spring + Hibernate framework structure, the database adopts oracle 10g large-scale database. Fully meet the needs of large and medium-sized enterprises with more than ten thousand people for stability and scalability.
[ad_2]