Dalian West Pacific factory all-in-one card system project case
[ad_1]
Large-scale enterprise one-card system
1.1 Company profile
Dalian West Pacific Petrochemical Co., Ltd. (WEPEC for short) is currently my country’s largest Sino-foreign joint venture petrochemical enterprise approved by the State Council and jointly invested by seven Chinese and French shareholders. The total investment is 1.013 billion U.S. dollars. It is located in Haiqingdao, Dalian Economic and Technological Development Zone with beautiful scenery and surrounded by the sea on three sides. It covers an area of 2.07 square kilometers and is adjacent to deep water ports such as Dalian Bay and Dayao Bay, as well as Dalian New Port, Daliang Bay Container Terminal and Beiliang Terminal. It has unique advantages in port transportation.
WEPEC is designed as a fully hydrogenated fuel chemical refinery with Middle East high-sulfur crude oil (commonly known as “coarse grains”) as raw materials. It has 12 sets of production equipment and public engineering systems, with reasonable equipment layout, advanced technology and high level of automation control. 5 million tons/year atmospheric and vacuum distillation, 2 million tons/year heavy oil catalytic cracking, 2 million tons/year heavy oil hydrogenation, 100,000 tons/year sulfur recovery, etc. are the largest single units in China at present, with good scale benefits. Construction started in May 1991, and it was fully completed in 1996 and put into production one after another. It can process 10 million tons of original high-grade unleaded gasoline, diesel, aviation kerosene, liquefied petroleum gas, polypropylene, sulfur and more than 10 varieties and more than 20 annually. A brand of product.
WEPEC currently has 1114 employees, with an average age of 31 years old, of which 521 employees have a college degree or above.There are 447 professional and technical cadres, 66 of whom have senior professional titles
WEPEC is working hard to give full play to its advantages of “new model, new system, and new mechanism”, in accordance with the requirements of “doing first-class work, creating a first-class level, and running a first-class enterprise”, the goal is to become a modern large-scale petrochemical enterprise in the 21st century.
1.2 Project background
a. Many items in the factory are stored in the open air and are easy to be stolen. It is very necessary to strengthen the effective identification of personnel entering the factory.
b. Dalian West Pacific Petrochemical Co., Ltd. is currently my country’s largest Sino-foreign joint venture petrochemical enterprise. It has extremely high requirements for fire prevention and vandalism in the plant area. Currently, an external security company is employed to be responsible for guards and gate guards in the plant area, but for personnel entering the plant ( Including the employees of the unit) did not conduct identity verification, forming a certain security loophole. Once saboteurs enter the factory with forged identity documents and destroy them, the consequences will be disastrous.
c. Most of WEPEC’s products are flammable and explosive. Once an accident occurs, it should be possible to know who is in the factory area immediately, so that it is easy to deal with afterwards.
d. Although the company has established a closed-circuit monitoring system and factory perimeter wall, to a certain extent, the phenomenon of criminals entering the factory area has been reduced. However, part of the theft is caused by criminals entering the factory area with fake work permits or colluding with security personnel to enter the factory area. , So it is impossible to fundamentally put an end to theft phenomenon. It is necessary to adopt more scientific methods for auxiliary management to fundamentally prevent such things from happening.
e. Manual registration of the identity of the personnel entering the factory is inefficient, error-prone, and incomplete, causing problems and incomplete information after an incident.
f. Attendance management still relies on manual processing. Each workshop and office has an attendant responsible for daily attendance, and automatic attendance is performed by using the employee’s card swiping data in and out of the factory, which will improve the efficiency of attendance.
g. The dining management in the canteen still adopts manual methods, and the accounting with contractors also adopts manual methods, which is inefficient. The use of IC card consumption management system will improve work efficiency and management level.
1.3 Project requirements
There are currently 6 doors for personnel and vehicles to enter the factory area: Door 2, Door 1, Door 4, Tank Farm Door, Office Building Door 1, Office Building Door 2, and Door 2 has approximately 600 people entering and exiting. Day; the in and out flow of gate 1 is roughly 400 people/day; the in and out flow of gate 4 is roughly 400 people/day; the in and out flow of tank gate is roughly 400 people/day; the in and out flow of office building gate is roughly 200 people/day Days; the entrance and exit flow of office building No. 2 is roughly 200 person-times/day; most employees go to work by company shuttle bus.
There are two canteens, which are located in the No. 1 office building area and the No. 2 office building area. Each canteen has two floors. The management and ordinary employees share meals. The management is on the second floor and ordinary employees are on the first floor. Each floor has three dining windows. It is planned to contract to two catering companies to compete with each other. The consumption system should be able to meet the daily tasks of daily card issuance, recharge, card consumption, data collection, query, and statistics. At the same time, the system should be able to distinguish the monthly consumption statistics of the two catering companies and facilitate settlement.
Attendance management is the responsibility of the Labor and Management Department. Each office and workshop has a dedicated person who also manages the attendance records of the department. At the beginning of the month, the labor and management results are reported to the Labor and Management Department.
1.4 Project goals
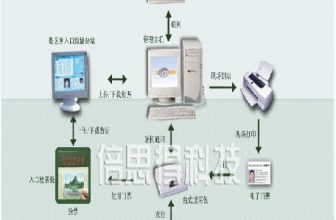
The ultimate goal of the All-in-One Card System of Dalian West Pacific Company is to realize the identification of personnel entering the factory,Access control,Attendance, Consumer card use. It is divided into four subsystems, “Personnel Entering Factory Identity Identification System”, “Important Area Access Control System”, “Employee Attendance Management System”, and “Canteen Consumption Management System”.
The system uses an inductive IC card as an employee ID. The employee ID is printed on the surface of the employee’s color head portrait, which requires high definition. It also prints the employee’s name, number, and department. The system confirms the identity of the cardholder, swipes the card to go out after get off work; enters the important area of the factory, swipes the card to open the electric lock and enters; the labor department uses the card data for commuting to realize automatic attendance; swipe the card in the canteen to deduct the card for meals. The commissioning of the system realizes the effective identification of the identity of the personnel entering the factory, realizes the authorized access control management in important areas, improves the work efficiency of the attendance management, and improves the efficiency of the canteen consumption management.
The system consists of inductive IC portrait card, inductive IC card reading and writing equipment, controller, sound and light alarm device, IC card consumer machine, network communication equipment, PC, server, database, etc.
Except for regular employees, temporary staff from outside should fill in complete personal information and reason for entering the factory before entering the factory. The security department will enter the computer and then issue a temporary IC card. In this way, the information of the outside staff will be completely entered into the database. Access areas and time periods are also strictly restricted.
“Personnel Entering the Factory Identity Recognition System” is a PC at the gate of the factory, identification equipment (composed of a controller, a card reader, a warning light, and a voice alarm device) and a database server. It is prompted by a warning light and a voice alarm device. Is the identity of the card reader legal?
“Important Area Access Control System” is composed of a controller, a card reader (a password keyboard can be attached), and an electric lock. The door of the critical area is equipped with an electric lock, and only after authorization can you swipe the card to open the electric lock and pass. The entry and exit records are stored in the database server of a card system.
“Staff Time Attendance Management System” is to generate the attendance results by using the employee’s card swiping data when entering the factory and the data from the factory swiping card.
“Canteen consumption system” is to write the amount of each person into the electronic wallet in the proximity card, and the consumer machine will deduct the payment from the electronic wallet in the card during consumption, and at the same time, the consumption details will be generated and stored in the consumer machine and uploaded to the background at any time In the database.
System Features:
1. High system security
At present, large-scale enterprises generally use paper work permits that can be 100% forged. When guards check paper work permits, they cannot confirm with the personnel department, causing criminals to enter and leave the factory with fake permits. However, the inductive IC card portrait card work permit has a built-in inductive chip. The chip number is unique in the world and cannot be copied. If a criminal purchases an inductive IC card from a card factory to forge an IC portrait card work permit, the IC card number is not stored in the background database. When you swipe your card to enter the factory or when you are asked to swipe your card in the factory by a patrol guard, the green indicator light that confirms your identity does not light up, and the criminals will immediately reveal their identity.
As everyone enters the factory to swipe their card, the swiping data (card number, entry time, door number) are stored in the back-end database for future reference at any time. At the same time, it is a forged IC portrait card work permit. The system will immediately issue a voice prompt to inform which channel has illegal entry. In addition, surveillance video records the entry of employees and guards on duty at all times, even if the guards deliberately release those Entrants who have not swiped their card or the green light does not turn on will also be found in the future video review. Once there is a problem, the public security agency will provide the staff with the specific time, door number and on-site video when the employee enters the factory area to provide a favorable guarantee for the rapid detection of the case This greatly reduces the phenomenon of guards’ deliberate release and collusion between guards and criminals.
The system has been successfully applied to Anshan Iron and Steel, Taiyuan Iron and Steel, Shagang, and fundamentally reversed the order in the factory area. The original chaos of theft, residents walking through the factory area indiscriminately, car accidents, and miscellaneous people roaming the factory area has been fundamentally reversed, greatly purifying the production environment of the factory area. . This has greatly reduced the incidence of theft, so that various large steel companies have established projects to plan for the system.
The electronic wallet in the proximity card is stored in a fixed sector, with different key protections for reading and writing. The proximity card and the consumer must go through three mutual authentications, and all data is encrypted during the communication process. At the same time, the consumption details and balance data will be uploaded to the back-end database, and the remaining amount expressed in the back-end database is equivalent to the balance in the card, so the security of the electronic wallet is guaranteed from all aspects.
2. Able to achieve true access control management
The system is set up to set the gates that each person is allowed to pass through. The doors of important parts can be equipped with electric locks or gates. The persons who enter and exit these doors and the specific time period can be set according to the situation.
3. The management method of temporary personnel entering the factory has been changed to achieve real and effective control
4. It can meet the identification of large-volume personnel entering the factory during the peak period
5. Significantly improve the efficiency of canteen consumption management
Computerized dining management in the canteen is realized, and the accounting with the contractor is also very fast and accurate, which will improve the efficiency of the canteen’s accounting work and improve the management level.
System implementation
The ultimate goal of the Dalian West Pacific Company’s factory card system is to realize the identification of personnel entering the factory, access control, attendance, and consumption card. The system is divided into four subsystems, “Personnel Identity Recognition System”, “Key Area Access Control System”, “Employee Attendance Management System”, “Canteen Consumption Management System”.
According to the requirements of Dalian West Pacific Petrochemical Co., Ltd., combined with our understanding, after detailed investigation and demonstration, a complete system solution is proposed, which is summarized as follows:
Section 1 System structure
As shown in the following figure 2-1-1:

The one-card system adopts C/S system structure. The four subsystems of this system: “Personnel Entering Factory Identity Recognition System”, “Important Area Access Control System”, “Employee Attendance Management System”, and “Canteen Consumption Management System” have the same database server. The four subsystems are used by different departments. “Personnel Entering Factory Identity Recognition System” and “Key Area Access Control System” are used by the Security Department, and “Employee Attendance Management System” is used by the labor management office and attendance administrators of various departments. The “Canteen Consumption Management System” is used by the General Affairs Office, the Canteen, and the Finance Office (recharge for employees).
Section 2 System Composition
The following is the composition of the four subsystems:
1. “Personnel Entering the Factory Identity Recognition System”
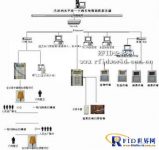
The working principle of the system is shown in Figure 2-2-1:

The gate post is generally composed of the following equipment:
a. PC computer (mainstream PC is fine)
It is the operating platform of the real-time monitoring program for personnel entering the factory in the “Personnel Entering the Factory Identity Recognition System”.
b. UPS uninterruptible power supply
c. The real-time monitoring program for personnel entering the factory in the “Personnel Entering Factory Identity Recognition System”
It is used to drive the TCP/IP controller, extract the card data in real time, and confirm the identity of the card reader through the background database, and display the card reader’s photo, name, department and other information on the display. When the identity of the card reader is legal, a confirmation instruction is sent to the controller, and the green light of the warning light is driven by the controller to flash. When the identity is illegal, the power amplifier and loudspeaker are driven to play the sound file “invalid card in certain channel” to prompt the guard, in the database Save a credit card record in the.
d. Control cabinet
Place TCP/IP controller, optical fiber access equipment, HUB, UPS uninterruptible power supply, etc.
e. 10M HUB
Used to connect controllers, PC computers, and optical fiber access equipment.
f. TCP/IP controller
It is used to store the swiping data of the IC card reader, and is responsible for communicating with the PC, sending the swiping data to the PC, accepting the confirmation instruction from the PC, and driving the warning light connected to the controller to flash green
g. IC card reader (485 communication protocol)
The card reading distance is 5-6 cm, which is a MF one card reader.
h. Four high-bright warning lights (one pair of red and green)
It is installed in four directions in the loading shell, and each direction is equipped with a high-brightness warning light. The guards and cardholders can see the warning light in each direction.
i. The loading shell and stainless steel column of the card reader and high-bright warning light
The loading shell is used for loading IC card readers and high-bright warning lights, and the stainless steel column is used to support the loading shell.
j. Loudspeaker, power amplifier
Play the sound of “Invalid Card for XX Channel” to remind the guard.
The reason why the optical fiber is laid in the gate guard room is to install surveillance video equipment on the spot. The surveillance picture can be transmitted to the security monitoring center through the optical fiber in real time. At the same time, the card data on the spot can also be transmitted to the all-in-one card database in real time. Obtain the confirmation result of the database.
Several characteristics of the system:
a. The controller is specially developed for the large-flow access control system of large companies. It can realize that each channel can verify up to 3 persons per second. At the same time, the drive of the warning device is a unit of 150 milliseconds, which guarantees the requirement of large-flow. At the same time, it technically solves the problem that individual card swiping records are ignored in real-time swiping.
b. In order to meet the needs of mobile identification, a large-capacity handheld card reader with a Chinese character library has been specially developed, which can download the card numbers of tens of thousands of employees (as continuous as possible, with a high degree of continuity, and fast query speed) for commuting to work Car personnel do not get off the car to verify and compare (the guards go to the commuter car with a handheld card reader to swipe the card to verify the valid identity of the cardholder).
c. The stainless steel column and loading shell of the card reader are specially designed and manufactured for the access control system. Reasonable structure and convenient connection.
d. The subsystem has been applied to Anshan Iron and Steel, Taiyuan Iron and Steel, and Shagang, with complete and mature system functions, optimized system structure, and high data processing efficiency.
2. “Key Area Access Control System”
a. TCP/IP controller
This controller can control four doors and has a built-in TCP/IP module. As long as there is a standard network cable to connect it to the network, any PC on the LAN can access this controller.
b. Electric lock and electric lock power supply
Choose electric mortise lock or magnetic lock according to actual situation.
c. IC card reader head and exit button.
The card reader can choose one of the keyboard with password and the keyboard without password.
d. PC for access control management (mainstream PC is fine)
e. “Key Area Access Control System” software
The system can perform many functions such as authorization, see section 4 of this chapter for details.
3. “Employee Attendance Management System”
Each department provides a PC to run the “Employee Attendance Management System” software.
4. “Canteen Consumption Management System”
a. RF card TCP/IP consumer machine (on-hook)
b. Communication management workstation (mainstream PC can be used) and TCP/IP communication platform (communication software)
c. General affairs office card issuing management workstation (mainstream PC can be used) and radio frequency card reader (for card issuing, 232 serial communication)
d. “Canteen consumption management system”
e. UPS uninterruptible power supply
f. HUB
Section 3 System Implementation
The four subsystems of the one-card system originally had the function of inputting personnel information (all the four subsystems can run independently as a complete system, or can be combined into a database to run as a subsystem), but the databases of the four subsystems are merged into After a database, personnel information entry, modification, and deletion are performed by the consumer system. Card issuance, card recovery, card loss reporting, and cancellation of loss reporting are also uniformly completed by the consumer system. The same functions in the other three subsystems will not be allowed to be used.
1. Implementation of “Personnel Entering the Factory Identity Recognition System”
WEPEC has six doors: Gate 2, Gate 1, Gate 4, Tank Farm Gate, Office Building Gate 1, and Office Building Gate 2 that require personnel to enter the factory for identification, including Gate 2, Gate 1, and Gate 4. The gates of the doors and tank farm doors are being remodeled, and there are fixed guard rooms, and the network optical fiber needs to be laid in the guard room rooms.The four gatekeepers will install a complete set of equipment, namely: a PC, a UPS uninterruptible power supply, a set of real-time monitoring procedures for personnel entering the factory of the “Personnel Entry Identification System”, a control cabinet, a 10M HUB, and a
TCP/IP controller, two sets of loading shells and stainless steel columns, one set of loudspeaker amplifiers, each set of loading shells contains an IC card reader and four high-brightness warning lights, two sets of loading shells and stainless steel The uprights are placed on both sides of the entrance passage near the guardhouse. The above four gates are being renovated. During the renovation, a 50mm diameter galvanized pipe and a 30mm diameter PVC pipe should be buried below 35cm underground between the stainless steel column and the guardhouse. The PVC pipe is sleeved in the galvanized pipe and the PVC pipe is buried. Two 8-core shielded wires (one spare) and two two-core power cords (one spare), the card reader in the loading shell is connected to the controller in the guard room through two-core shielded wires, the card reader and the warning light The 12V power cord is connected to the 12V power supply of the guard room through a two-core power cord.
No. 1 office building door and No. 2 office building door have no guards or guard rooms. These two doors are different from the other four door guards in terms of personnel identification. Only a set of loading shells and stainless steel columns are placed in front of the door, PC The computer, UPS, control cabinet, 10M HUB, TCP/IP controller are all placed in the computer room upstairs. The card reader, the communication line and the power line for the warning light in the loading shell can be directly routed out of the computer room upstairs, requiring prior construction. The wireless communication method can also be considered, that is, the controller and the card reader communicate through a wireless module, and there is no need to wire between the two devices. The card reader and the wireless communication module loaded with the shell are powered by a 14AH lead-acid battery. Since the warning light must be connected to the controller via a wired connection, the warning light is taken out of the loading housing and placed on the wall of the entrance. The 14AH lead-acid battery in the loading housing needs to be charged once a week, which is a disadvantage of wireless communication.
Some gates that cannot be constructed are recommended to use the wireless controller method. The disadvantage is that the 14AH lead-acid battery in the loading housing needs to be charged once a week, and the warning light used to indicate whether the identity is legal is placed on the wall near the loading housing Instead of loading on the shell.
See the first part of the fourth section of this chapter for system functions.
2. Implementation of “Key Area Access Control System”
The main tasks of this subsystem are: the installation of the communication line between the controller and the electric lock and the exit button; the installation of the electric lock and the power supply of the electric lock, other workloads are relatively small.
See the second part of the fourth section of this chapter for system functions.
3. Implementation of “Employee Attendance Management System”
The system can realize the management and attendance of a variety of shifts, especially in the case of three shifts in the workshop. The system uses the data of employees entering get off work and leaving work as the basis for daily attendance, and generates daily attendance records for each person based on the results of prior scheduling. Since each department and workshop has attendance staff, the daily schedule, leave, and shift management of this department are completed by the attendance staff through this system.
See the third part of the fourth section of this chapter for system functions.
4. Implementation of “Canteen Consumption Management System”
Since the electronic wallet file that can be used independently is directly established in the proximity card, the cardholder can still swipe the card for consumption when the consumer machine is not connected to the back-end database server (this method is called “offline consumption”). The system can be consumed online or offline.
The communication management workstation (mainstream PC can be used) and the TCP/IP communication platform (communication software) in the system are the platforms responsible for communication with consumer computers, and are responsible for consumption data collection and various data distribution. Because the consumer machine (on-hook) has a built-in TCP/IP module, it is easy to install.
See the fourth part of the fourth section of this chapter for system functions.
Section 4 System Function
1. “Personnel Entering the Factory Identity Recognition System”
1) Basic information management
a. In-service personnel information entry
b. Temporary personnel information entry
c. M1 card initialization
d. Official card issuance
e. Temporary card issuance
f. Formal card verification
g. Temporary card verification
h. Temporary card renewal
2) Information query
a. Inquiry of incumbents
b. Temporary personnel inquiries
c. All kinds of code query (department, gate, etc.)
d. Inquiry about card application
e. Blacklist query
3) Code management
a. Department management
b. Gatekeeper management
4) Real-time swipe card monitoring display
5) Statistical report
a. Credit card statistics of all gates and posts of the whole factory
b. Statistics of the number of personnel entering the factory
c. Statistics of card application
6) System management
a. Operator management
b. User authorization
c. Blacklist management
d. Authorized management of entry and exit areas
e. Data upload and download, import and export
f. Regular database backup
g. Swiping and running water cleaning
For detailed function introduction, please refer to the file “Zhijia All-in-One Card-Personnel Entry Identification System Operation Manual.doc”.
2. “Access Control System for Important Areas”
1) Real-time monitoring
a. Graphical monitoring
b. Event record monitoring
2) System design
a. Design of electronic map
b. Process control
3) Entry of department and job data
4) Enter a valid card number
a. Use the controller to connect the card reader to read the inner code of the proximity card
b. Directly enter the inner code of the proximity card
c. Import of external files
5) Time control setting
a. Set the time zone
b. Set holidays
c. Set schedule
6) Staff profile setting
a. The staff group controls the copy of the data
b. APB control
c. Password control
7) Set door parameters
8) Inquiry/Report
a. Card data query report
b. Staff data report (in and out data query report, time zone data report, timetable data report)
c. Staff group data report
d. Holiday data report
e. Door data report
f. Departmental data report
g. Job data report
h. Operator data report
9) Database processing
a. Database backup
b. Database recovery
c. Clear the database
10) System management
a. Permission settings
b. Operator settings
c. Modify the operator password
For detailed function introduction, please refer to the file “Zhijia Card-Access Control Management System Operation Manual.doc”.
3. “Employee Attendance Management System”
1) Shift setting
a. Time attendance shift setting
b. Unified department scheduling
c. Individual employee schedule setting
d. Attendance parameter setting
2) Shift handling
3) Process attendance data
4) Modify attendance results and attendance explanation
5) Query
6) Report
4. “Canteen Consumption Management System”
1) Network management
a. System startup
b. Sales monitoring
c. System shutdown
d. Communication recovery
e. Automatic removal
2) Meal card management
a. Account opening
b. Pin card
c. Replace card
d. Repair card
e. Card verification
f. Recycling
g. Key card
3) Account management
a. Account freeze
b. Account recovery
c. Host increase
d. Subsidies
e. File modification
f. Personal withdrawal
g. Refund due to error
4) Detailed accounts
a. Sales revenue
b. Access browser
c. Meal card statistics
d. Terminal details
e. Refund list
f. Subsidy record
5) Analysis and summary
a. Structural analysis
b. Consumption curve
c. Administrative data
d. Data per capita
6) Data security
a. Backup
b. Backup and recovery
c. Import
d. Export
e. Synchronization
f. Clear
7) System maintenance
a. System settings
b. Data dictionary
c. Terminal management
d. Communication detection
e. Network control
f. Schedule Memo
g. System permissions
h. Operation log
For details, please contact: Shanghai Ningzhi Information Technology Co., Ltd.
Phone: 021-50273310 021-50277118
Development Department: Extension 16, 19
Sales Department: Ext. 15, 17 and 18
Technical support: 22 extension
Fax: 021-50273310-26
Address: 67, Lane 377, Chenhui Road, Zhangjiang Hi-Tech Park, Pudong, Shanghai
[ad_2]