ICBC Fund Office Building Access Control System Application Case
[ad_1]
1. Project Overview
The ICBC Fund Office Building Access Control System includes a total of 24 access control points, 2 of which are set for two-way card access and 22 for one-way card access, so a total of 26 card readers are required. Among them, 2 doors of the computer room are set to enter and exit two-way card swiping, 17 offices are to enter one-way card swiping; 5 are fire exit doors to enter one-way card swiping. The office wooden doors use electronically controlled cathode locks, two double-leaf glass doors are equipped with electric bolt locks, and five fire access doors use electromagnetic locks.
2. Design principles and needs analysis
Use integrated access control equipment to avoid the paralysis of the entire access control system caused by a single point of failure.
Adopt smart IC card, support the integration of all-in-one card, and ensure the security of the card.
Integrated anti-theft alarm function, providing real-time alarm report.
Provide attendance function.
Support the linkage with the fire protection system, and centrally control the fire access door.
3. Scheme design
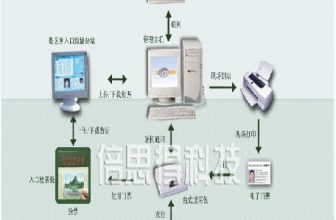
The design includes an access control management system, an anti-theft alarm system, and an attendance management system. The control terminal is composed of a computer, control software, attendance software, and communicator.
A single access control point is composed of card readers, locks, door sensors, door opening buttons, controllers and other equipment.
The access control/alarm control system uses NSTAR from Honeywell Security of the United States. It incorporates the most advanced security technology, the communication method supports RS232/485 and TCP/IP, and can provide users with a full range of products from single door controllers to large-scale integrated access control and security integrated systems. It integrates multiple functions such as access control, alarm processing, CCTV control, online patrol and card production. At the same time, the system can also provide a variety of input/output ports, which can realize seamless integration with building control, security, fire protection and other product systems.
3.1 Configuration of the card reader
The card reader uses a non-contact inductive card reader to avoid physical damage to the card caused by multiple card insertions during long-term use, and it can also avoid the common contact card readers from filling the slot with foreign objects in the card reader. Man-made acts such as mischievous destruction of the card reader. It adopts the international mainstream MIFARE IC card reader, the effective reading distance is 10cm, and supports all-in-one card. The system includes a total of 24 access control points, of which 2 are set for two-way card access, and 22 are for one-way card access, so a total of 26 card readers are required.
3.2 Configuration of electric lock
According to the door material:
Glass door or wooden door can choose standard single lock or cathode lock with a suction force of 300 pounds.
A 600-pound standard single lock can be used for aluminum alloy glass doors or wooden doors.
The fire exit door or its own heavier door can choose a standard single lock of 1200 pounds.
According to the opening angle:
When the door opening angle is 90°, electromagnetic locks, electric bolt locks and cathode locks can be selected.
When the opening angle is 180°, an electric bolt lock can be selected.
According to the way of working:
If the working mode of the electric lock is that the door is closed when the power is on, and the door is opened when the power is off, an electromagnetic lock or an electric bolt lock can be selected.
If the working mode of the electric lock is that the door is opened when the power is on, and the door is closed when the power is off, a cathode lock can be selected.
Of the 7 fire access doors in this system, 3 are double doors, so a total of 10 electromagnetic locks are configured. The remaining access points are glass doors and one-way wooden doors, using electric bolt locks and cathode locks. The specific configuration situation will be different due to the different door conditions and use functions of each security zone. Therefore, the configuration should allow adjustment. The final configuration should be based on the construction drawings.
The power supply of the electronically controlled door lock is provided by the security system itself. According to the system instructions, the functions of unlocking and locking can be realized. The fire alarm system in the office building can release the door lock in an emergency.
3.3 Door status monitor
The door status monitor is a sealed electromagnetic switch, and the switch part and the electromagnetic part are cylindrical, which can be fixed in the frame and the 25mm hole on the door. Provide alarm information to the control software when the door is opened overtime or opened illegally without authentication.
3.4 Access Controller
The access controller is a double-door controller. One controller is connected to two nearby card readers and controls its corresponding electric locks, exit buttons and door sensors. The 18 controllers are networked through the RS485 bus to communicate with the control software.
3.5 Intrusion detector
Mainly for the windows on the second floor of the office building on the 3rd facing street. Taking into account the safety and reliability of prevention, it can prevent employees from forgetting to close the windows after get off work and criminals illegally sneaking in. Because glass break detectors have strict requirements on indoor environment and glass specifications, and are prone to false alarms, infrared dual-check detectors are used to immediately report an alarm when someone intrudes. A total of 15 infrared dual-detection detectors are configured. The magnetic detector of each door can also provide real-time monitoring of the status of each door.
4. Realize the function
Access control
Control the opening/closing of electric locks at all access control points, implement authorized safety management, and report the status of each door to the control center in real time.
Through the pre-programmed settings of the management computer, the system can authorize the cardholder’s pass card validity (in/out level setting), and set the effective use time and range of the card (the area allowed to enter), which is convenient for internal unified management.
The system automatically recognizes the identity of entering and exiting personnel to prevent intrusion by outsiders.
All use non-contact card reading identification methods, and system users can enter and exit within the authorized scope only with a valid card.
Set up to enter and exit two-way monitoring management at important passages (cards are required for both entry and exit). The anti-reverse transmission function can enhance the security of the access control system.
The system can detect abnormal door opening and has an alarm function. If someone opens the door illegally (destroyed), or “applies” a low-level card to try to sneak into an important place, the access controller will immediately transmit the alarm to the control center computer and prompt the location of the crime, and record it at the same time.
Programming management
Managers with programming authority can set limits, cancel and reset the issued proximity card through the monitoring terminal and the management host, and can set the door lock method. In the event of an accident, the central control room can control the opening and closing of some or all of the door locks.
Card and cardholder management
The central control center issues cards uniformly, which can be made into work permits, access permits, VIP cards, temporary cards, etc., and can grant different authorizations to different cards. If the work permit can be used for a long time, the temporary card will automatically become invalid after several or several days of use. If the card is lost, it can be deleted in the database; the used card can also be re-authorized to other people.
You can set the effective and expiration date of the card
With batch add and batch delete cards, as well as card query functions
The authorized IC card issued by the central control center serves as an electronic key. Before the card approaches the reader, the indicator light in the reader turns from red to green, and the door lock is automatically opened. At the same time, the controller records the date and time of opening the door and the name of the cardholder.
Online monitoring and alarm function
All personnel can individually set their access control levels to control the area and time that can be accessed. When someone enters and exits, you can see the cardholder’s photo and the card reader’s image on the monitoring computer, and the security personnel can verify whether they have their own card based on this.
Door status detection and alarm input have the ability to prevent damage (such as: cutting, short circuit, parallel connection, series connection and other means to destroy the normal status indication)
Online tracking statistics, showing the entry records of cardholders in any area, and providing accurate on-site personnel information in an emergency.
Data and event record query and report generation
The system can record in detail the time and date of each door opening, the card number, name, subordinate department, position and other information of the personnel entering and exiting, and assist the management staff to inquire about their work. The management department can query the detailed records of the employees of each department on the query system at any time as needed. And can be printed out at any time. Each department can also inquire about the entry and exit status of its personnel at any time as needed.
Each access controller can work offline. In the offline state, it has the ability to store no less than 5000 events. When the communication with the host is restored, these events will be transmitted to the host for storage and query.
Management workstation: In addition to the real-time monitoring function of each channel port and equipment, the access control software provides various data reports, such as equipment settings, schedule programming, cardholder information, access records, etc., and can specify the required data Type or region, time, sorting method.
[ad_2]