Bank treasury management and financial cash box circulation security authentication system technology application solution
[ad_1]
One project overview
With the rapid development of my country’s economy, crimes in the economic field, especially against the financial industry, have occurred from time to time. Bank vaults involve a large amount of cash in and out of the warehouse every day, and the scope of work of the money-carrying truck covers treasuries, savings houses, merchants, etc. Units, therefore, can easily become targets of financial crimes. In May 2001, the case of a counterfeit banknote truck in Wenzhou Bank of China that took away a huge amount of cash revealed the security loopholes in the transfer of cash boxes in the bank’s financial management center, which aroused widespread concern in the society; In recent years, crimes against payment transfers have increased unabated. In early 2006, a bank transfer officer in Shenyang took advantage of his power and management loopholes to transfer a total of more than 3 million yuan in two transfers and fled. He has been wanted by the public security organs. . These facts show that more scientific and safe management methods are needed for bank transfer of cash boxes, door-to-door collection and delivery, and treasury management.
With the rapid development of science and technology, the electronic, networked, automated, and intensive level of banking business has been greatly improved. Modern high-tech is used to realize the electronic safe handover of the cash box, collection and delivery of the financial management center, and prevent financial risks. It is completely feasible to incorporate electronic handover services into the bank’s management network to implement intensive management.
At present, the business specifications of each bank’s cashier system have put forward certain business requirements for the entire process of treasury cash box, cash bag storage, allocation, escort, and circulation. There are three aspects involved in the deposit and receipt of the entire cash box: warehouse (manager), escort or transfer clerk, cash box administrator (for door-to-door collection and delivery business, it is the financial staff of the merchant), but Regardless of whether it is a transaction of “cash box receiving, handing in, and appointment” or “cash box, purse bag in and out of the warehouse” transaction, all business systems only regulate and record warehouses and outlets, but the whole process of transfer transfer is not There are no related electronic records and specifications, only manual operations. In addition, for the management of temporary transfer payments at savings outlets, some banks currently use phone authorization transfers, which is prone to fake transfer staff transfers. This is a “blind spot” in business process management, which is for safety. A hidden danger was buried. Objectively, a supplementary system is needed here to perfect it.
In this context, the RFID cashier business wireless terminal electronic verification handover system solution was proposed. This system is a set of systems designed to address the security loopholes in the transfer of cash boxes in the treasury and the bank’s door-to-door collection and delivery business in recent years. The system uses electronic means to control and record the entire transfer. process.
Every bankkeeper, escort, cash box administrator, merchant financial staff, etc. receive and send money with the electronic tag ID card as the identity authentication certificate for the transfer of money and tickets, as the transfer of money box, package transfer, and certificate transfer , Foreign currency handover, on-site collection and delivery of money handover certification and many other tasks. Business outlets (or paying customers) recognize the card and not recognize the person, thereby verifying the identity and preventing fraudulent collection; at the same time, use this label card to forcibly track and record the collection business data, thereby preventing “collection” The occurrence of criminal acts such as “detainees, escorts, and embezzlement of deposits”.
An electronic label is installed on each box or bag as the unique identification of the box. Not only does the transfer person need to be authenticated during the handover, but the box must be confirmed to ensure that “the person is in the right box and the correct circulation”.
Whether it’s the transfer of money box or door-to-door receipt and delivery, the wireless handheld terminal is used for handover certification. The handheld terminal not only has a unique hardware number, but also has a safety certification module. The handover, query, background data upload and download all need to pass the safety certification module The certification ensures the safety of the system. The RFID wireless handheld terminal can store the original electronic information of the transfer register in the terminal, and can send it to the database of the branch or financial management center at any time as the data of the bank’s cashier business system. The data can be grasped by the branch or the financial management center at the first time, and the improvement of the timeliness of the data can create conditions for real-time monitoring of the transfer of cash boxes. Through the analysis of the handover data, abnormal alarms were detected, and fraudulent collection and embezzlement in the process of cash box handover and door-to-door collection were found in time. This creates conditions for timely action to prevent crime.
The RFID wireless handheld terminal can also be used as the initiating terminal for temporary payment transfers, instead of telephone transfers or paper bill transfers. Because of its uniqueness, passwords and operating permissions can be set, it can completely prevent savings houses from unauthorized transfers or counterfeiting. The occurrence of transfers. In addition, the data of temporary transfers can also be uploaded to the servers of branches or financial management centers in real time to strengthen data acquisition and monitoring.
The system is based on RFID radio frequency technology and wireless technology to supplement the existing bank teller business integrated management system. It will realize the real-time collection and reading of the handover business chain information, provide safe identity authentication, dynamic monitoring of the currency transport process, Audit and supervise management, realize the modernization and automation of management, ensure the safe and scientific conduct of business, and prevent unauthorized operations.
Two needs analysis
1 Current situation
At present, the handover of cashier business generally adopts manual handover. The identification is mainly based on whether the bank’s money car and the person knows or not. However, the handover register and even the transfer vouchers are not included in the important voucher management in some banks. This method has serious problems. Security vulnerabilities are mainly reflected in the following aspects:
○The identity authentication method is simple and extremely unreliable. The identity of the handover person is only used as the certificate of the handover person by the face of the handover person or a simple certificate. This is extremely dangerous and provides a convenient door for criminals.
○Handover information is recorded on paper, which is easy to tamper with and difficult to enter information management.
○Daily statistical information is calculated manually, which is easy to make mistakes and has a large workload. Moreover, due to the lag of manual entry, it is impossible to monitor the payment status of subordinate branches in real time, and it is impossible to detect and investigate the abnormal payment in real time. stop.
○If the registration book and transfer voucher information is not strictly supervised, other personnel can easily obtain and imitate it, and it is also difficult to manage in this respect.
○Temporary transfer payment by telephone has potential safety hazards that are difficult to identify and counterfeit transfer payment.
○It is difficult to count and manage the workload and working conditions of the staff.
○The division of labor can be exchanged at will. For example, security personnel and handover personnel can change roles during the handover process, which is likely to cause hidden dangers.
2 Business needs
Based on the above situation, the bank cash teller project team put forward the requirements for the wireless terminal application of the cashier integrated business management system, aiming to solve the identification and control problems in the treasury management, cash box handover, and door-to-door collection and delivery. The specific measures are as follows to ensure Security of cashier business:
○Safe production of personnel and box identification and identity tag cards
○Safety control and line inquiry safety mechanism for receiving and returning the handheld terminal
○Safe identification and transfer control of cash box transfer in the banking system
○Handover control of door-to-door collection
○Handover control of home delivery
3 The system achieves its goals
The goal achieved by the system is mainly to use advanced RFID electronic label technology and handheld terminal wireless network technology to achieve the security control of the cash box transfer in the banking system, and the security control of the merchant’s door-to-door paymentremittance transfer, specifically:
○Using electronic label card to realize safe and efficient handover
Give full play to the characteristics of large storage capacity and good security of electronic label cards, so that staff use IC cards as the main identification method for the transfer of cash boxes, and electronic tags are also used as unique identification and identification methods for the transfer of various tags. The card and a wireless handheld terminal with a security module with a unique number are used for personal identification, which overcomes the security loopholes in the past that only rely on face or simple documents to hand over, and realize safe and fast handover.
○The escort tag card strictly authorizes working hours and working lines every day, and can store work records
Using the authorized operation and password protection of the work line of the escort during the handover, the information of the handover of personal work is recorded in the tag card at the same time, which can also be used as a basis for the workload or assessment of bank employees.
○Electronic vouchers replace paper vouchers and registration books, and the handover data cannot be tampered with, and is transmitted to the central database in real time to avoid lag and tampering of manual entry
All handover work is based on electronic data, and the register or payment voucher is only used as a necessary supplementary means, even if it is tampered with or imitated, it is meaningless.
Handover records are stored in encrypted electronic data, which cannot be tampered with, and avoids the cumbersome manual entry, and can be easily uploaded to the branch or the financial management center database in real time. The data of the transfer and payment transfer of the cash box can be monitored in real time, so that the bank can further achieve early warning and realize the intervention of abnormal payment transfer. Put an end to crimes that are taking place.
○Temporary transfers can be initiated using wireless handsets for identity authentication
A dedicated wireless POS device can be used to initiate a payment transfer request. The uniqueness of the hardware code of each bank’s equipment and secure authority management can eliminate insecure factors in telephone transfers.
○The wireless handover equipment is durable, reliable and easy to carry
The handover environment is more complicated, and the equipment is required to be durable and reliable; it can be used outdoors, it needs to be easy to carry, and the information can be reliably stored and uploaded.
○Using database encryption technology to realize data security management
The collected data enters the database through the system, and cooperates with the data of warehouse management to realize the information management of the business data of the treasury center. Special algorithms are applied to encrypt the database, which can only be accessed through the management system, so that the data entering the database is prevented from illegal tampering.
○Output customized reports to achieve management purposes
Data management is based on the database, and various reports can be customized and output according to business needs, making data statistics a simple task, making management targeted and evidence-based
○Provide real-time query of various information
○Stable and friendly docking with the banking system
Three system overall design
1 Design principles
System construction should unify data standards, unify software, and unify hardware, adopt mature and reliable technologies, focus on integrity and practicality, and take into account advancement and scalability. At the same time, the system has a good performance-price ratio.
2 The overall structure of the system
This system involves branch management centers, branch central treasury warehouses, as well as various savings outlets and various door-to-door merchants. When handing over, it is necessary to use the RFID wireless handheld terminal to confirm the personnel and the cash box, and upload the confirmation result to the database backstage for confirmation via GPRS/CDMA in real time. The RFID wireless handheld terminal can download real-time information such as the escort line and the payable box from the background of the monitoring center.
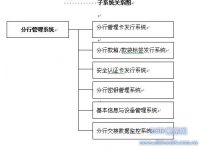
3 The overall structure and composition of the application software system
This system integrates bank door-to-door collection management; cash box handover management; bill package handover management; foreign currency handover management; it is composed of the following modules:
○Branch Management Card Issuance and Maintenance System
○Branch box/bag label issuance and maintenance system
○Safety certification card issuance and maintenance system
○Basic information and equipment management system
○Branch Key Management System
○Branch handover data monitoring system
○System administrator tag card authorization and maintenance system
○Treasury Center Handover Management System
○Handheld POS search query system
○Handheld POS receipt and return management
○Handheld POS handover system for outlets
○Handheld POS transfer management system in warehouse
○Wireless communication management system


Branch Management System
Branch Management Card Issuing System
Branch box/bag label issuance system
Security authentication card issuing system
Branch key management system
Basic information and equipment management system
Branch handover data monitoring system
System Administrator Tag Card Authorization System
Treasury Center Handover Management System
Treasury Center Management System
Handheld POS search query system
Handheld POS receipt and return management
Handheld POS handover system for outlets
Warehouse Handheld POS Handover Management System
Wireless communication management system
4 Main business operation process
Four hardware system design

System hardware deployment
It is recommended to establish a data center, branch management system and treasury management system data for centralized management, warehouse and various outlets handover control, through the lease of GPRS or CDMA network, and through the bank’s private network for encryption. All data uploaded to the background must pass the TAC verification of the encryption machine to ensure its integrity, correctness and reliability.
Five application software system function design
1 Branch Management Center
○Branch Key Management System
○Branch Management Card Issuance and Maintenance System
○Branch box/bag label issuance and maintenance system
○Safety certification card issuance and maintenance system
○Basic information and equipment management system
○Branch handover data monitoring system
2 Treasury Center Management System
○System administrator tag card authorization and maintenance system
○Treasury Center Handover Management System
○Handheld POS search query system
Route query:
Box query:
Identity verification:.
Enter the transfer record and upload:
Temporary payment application:
Management function:
Identity verification:
Enter the transfer record and upload:
Management function
○Wireless communication management system
Six system security
The security requirements of this system are very high, and the key considerations are as follows:
○Security of the application tag card
The world’s only code, multiple data encryption system, such as the storage of digital signatures to identify authenticity and prevent counterfeiting.
When someone illegally reads the tag card (such as using a card reader other than this system, etc.) three times, the card will self-destruct; when the password is entered incorrectly three times, the card will be automatically locked. Once logged off, the card cannot be used in this system.
In addition to the security key, the operator’s name and ID number are also stored in the tag card, which can be used as an auxiliary means to confirm the legitimacy of the identities of both parties.
○Security of transaction authentication
When the tag card and the handheld POS are authenticated, not only a password is required, but also MAC verification is performed through the security module to ensure transaction security.
The system can realize real-time strict control of each handover: including the effective time and the specific handover object. Only after the system authorization, the handover can be carried out within the specified time and within the specified range.
In the authorization of each transaction, the cashier’s identity must be authenticated by the system before it can be realized.
When collecting money, the cashier must use the tag card he holds as an authentication tool to verify the password with the paying customer. Payment customers only recognize the card but not the person. Any counterfeit card, unauthorized card (unauthorized payment card), or a card with an authorized type that also matches but the password is incorrect will be prompted by the alarm and the operation will be refused.
The cashier must use the card with the correct password to receive the payment. During this process, the system will automatically record the data, thus accomplishing the purpose of “tracking record”. And no one except the center administrator can change this data. When the cashier sends the money into the warehouse, his label card has already recorded in detail every payment received on that day, even including every error record.
○Safety of machine data storage
The security authentication module is embedded in the machine, which not only guarantees the safety of the transaction, but also performs TAC verification with the encryption machine on the data uploaded to the background.
POS can realize self-protection. When an external force tries to open the POS case, it will automatically clear the POS program and POS storage area data;
○Application system security
The management of the system software is a three-level management mode. The operation authority of management personnel at all levels is gradually reduced.
The database is encrypted in a special way, and general decryption software cannot open and modify it.
Data is stored and transmitted in an encrypted manner.
○Key system
The security core of the system is the key library of the collection system, from which the security keys of the operator cards at all levels are generated. The keystore stored in the system is unreadable.
The user roles of the key management system are divided into system operators and code sheet input personnel.
Processing sensitive data in the key management system includes code sheets and related data in key transmission. The key management system does not save the code sheet, and the sensitive data in the key transmission process is encrypted by the key entities of the transmitting parties, so there is no security problem.
Key access is not allowed to be read directly, and the key cannot be directly accessed by the outside world, and must be updated under the control of the master key
The communication content between any two key entities is encrypted and transmitted, so the security of the data transmission process can be guaranteed.
The generation, decentralization, transmission, maintenance, preservation and custody of the key are the guarantee of application security. In order to prevent the possibility of leakage of secrets by insiders who hold secrets, a set of efficient and safe key distribution, storage and custody centralized measures, as well as a set of safe storage and custody methods should be established.
The whole process is similar to the issuance process of a bank card. The key encryption algorithm at each level is different.
○Other safety measures
The system will also consider data security and backup, and the security of the interface with existing application subsystems.
○Abnormal event handling
The system has a complete abnormal event handling function and blacklist function. If the label card is lost, the card can be cancelled in the system, and the card cannot be used in the system. When the POS device is damaged, the system provides manual entry function after authorization to ensure the integrity of the transaction information.
Since the system adopts an encryption verification mechanism, the system implements identity trust verification for both parties to the handover. Only when both parties to the transfer have swiped their own tag cards and entered their correct passwords respectively, the transaction can be continued after the identity authentication of both parties, ensuring the functions of identity verification and double verification for both parties. When the data is accidentally entered incorrectly and a correction transaction needs to be carried out on the POS, the supervisor must enter the POS password and perform label card verification and authorization before execution.
Six system performance characteristics
○High system safety factor
Relying on the safety management technology and measures described above, this system minimizes the risk of customers with comprehensive and professional safety management.
○Simple data information management
All collection records can be directly read into the database system through RFID electronic tag cards and wireless communication, without manual entry. And can print various reports as needed.
○Detailed data records
Each record includes: payment customer number, payment customer name, name of the person who handles the payment, payment amount, time, cashier’s name, certificate number, seal number, voucher number, change, etc., and can be added as needed information.
Cashiers can view their own historical collection records at any time, and the query results can be accurate to the specific time and amount of each item.
○Business processing complies with handover specifications
The door-to-door payment collection system has functions such as “receiving”, “inquiry”, “correction”, “receiving package”, “multiple orders”, “uploading data”, “report printing”, “change” and other functions. Two-person handover is required to ensure the supervision of business processing.
○POS operation is convenient and time-saving
Convenience and time-saving are particularly important for operators, which is more prominent in the treasury banknote transportation management system. Because only by doing this can the handover process be completed in a relatively short period of time. Otherwise, it will easily affect the business of various outlets and give criminals an opportunity to take advantage of it. In the system, in addition to the manual input of the password and amount, other things such as the time, the number of both parties, the name, etc. are automatically completed by the POS. And every step of the operation of the system has prompts, and the operation is very concise.
○Maintain the integrity of transactions
Every transaction must be complete, otherwise an alarm will be issued and the operation will be refused, and the failed transaction will be recorded at the same time
The system has been successfully applied to bank treasury management and financial box transfer applications and third-party logistics escort applications.
If you have any questions, please contact
Document production: Ren Gong
Email: [email protected]
QQ: 479017087
Mobile: 13911533725
http://company.rfidworld.com.cn/rfidworld_company_27961.html
[ad_2]