RFID media tracking alarm system
[ad_1]
1. RFID concept and working principle
RFID radio frequency identification is a non-contact automatic identification technology, which automatically recognizes the target object and obtains relevant data through radio frequency signals. The identification work does not require manual intervention and can work in various harsh environments. In the actual application of RFID, the electronic tag is attached to the identified object (surface or internal). When the identified item with the electronic tag passes through its readable range, the reader automatically removes the electronic tag in a contactless manner. The agreed identification information in the file is read out, so as to realize the function of automatically identifying items or automatically collecting item mark information. RFID technology can identify high-speed moving objects and can identify multiple tags at the same time, and the operation is quick and convenient.
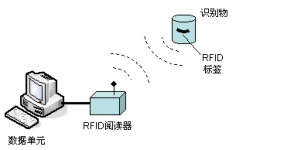
The most basic RFID system consists of three parts:
1) Electronic tag (Tag): Composed of coupling components and chips, each tag has a unique electronic code, attached to the object to identify the target object;
2) Reader: A device for reading (and sometimes writing) tag information, which can be designed as a handheld or fixed type;
3) Antenna: Transmit radio frequency signals between the tag and the reader.
After the tag enters the magnetic field, it receives the radio frequency signal from the reader, and uses the energy obtained by the induced current to send out the product information (Passive Tag, passive tag or passive tag) stored in the chip, or actively send a signal of a certain frequency ( Active Tag, RFID tag or active tag); after the reader reads and decodes the information, it is sent to the central information system for relevant data processing.

Typical RFID system composition
2. Secret-related carrier access management system and product introduction
1. Current status
At present, there are no records of personnel entering and exiting various office areas. The secret storage medium has been accidentally or deliberately taken out of the gate. The source of personnel loss or leakage cannot be traced, and the person cannot be held responsible. Unable to centrally manage personnel and confidential information in the region.
2. Introduction to the RFID hardware system implementation plan
First install the RFID antenna and the reading head in a hidden place at the entrance or exit of the office building (for example, the antenna can be completely embedded in the door frame or roof); at the same time, embed RFID electronic tags in each personnel card. When a person enters the office area, it will be identified by the reader’s antenna and reading head, and the time of the person’s entry will be recorded in real time. At the same time, it can be combined with the personnel access control management system to record the relevant information of the person leaving at the same time. Through the internal network, timely report the situation to the monitoring center (alarm, indicator light or SMS) or the relevant person in charge SMS)). In the event that items are lost or stolen, management personnel or unit leaders can lock relevant personnel by querying the access control records and find them in time.


Figure 1: System configuration diagram (side view)

Figure 2: System configuration diagram (front)
3. Hardware technical indicators and related technical parameters
The personnel access management and monitoring system adopts the most advanced and reliable RFID technology, which solves the two major problems of waterproof and metal shielding of electronic tags. Ensure that all personnel entering the management area are discovered in time.
(1) Anti-metallic material encapsulation for electronic label confidential media application
Description: The size of the label can be provided according to user needs, and can be packaged into a self-adhesive paper substrate
Features: It can print personalized LOGO, text and file filing number, etc.
Technical index:
Working mode: R/W (read and write)
Storage capacity: 96-bit EPC code, 64-bit unique ID, 224-bit user data area
Working frequency: 860~960MHz
Meet the standard: EPC C1G (ISO/IEC 18000-6C)
Features:
1. Thin label thickness
2. The Strap process has high packaging stability and high antenna sensitivity
3. It can be directly pasted on various confidential media electronic labels

(2) UHF four-channel reader

Introduction to the reader: RFID fixed reader JY-U8720
JY-U8720 is a multi-protocol compatibility, split design, can be connected to four antennas, fast reading rate, multi-tag reading, industrial design and other advantages, can be widely used in various RFID systems, typical Applications are:
Logistics and warehousing management: item flow and warehousing management, as well as the flow management of mail, parcels, luggage, etc.;
Supply chain application areas: application of goods supply process, etc.;
Product anti-counterfeiting detection: use the write protection function of the memory in the label to identify the authenticity of the product;
Other fields: in club management, library, student status, consumption management, attendance management, dining management, swimming pool management and other systems have been widely used.
Features of the reader:
Using a unique anti-collision algorithm to achieve a very high multi-tag recognition capability;
Four independent transmitting/receiving antennas increase the identification area of practical applications;
Comply with ISO18000-6B and ISO18000-6C (EPC-GEN2) protocol standards;
Ability to read and write tags: read more than 3 meters;
The reader provides functions such as multi-tag identification, single-tag reading, tag writing, tag lock, and kill.
4. Communication plan

1. Connect the RFID readers at the two exits of the building to the computer in the file management room through the TCP/IP local area network for data management.
2. Independent asset management system or seamless access to file management system.
3. Video surveillance and time-sharing record video.

3. Introduction to the confidential management system of confidential media
1. Business process
The “secret-related media monitoring system” with advanced radio frequency (RFID) technology as the core. This system attaches an RFID electronic tag to a mobile carrier. When the mobile carrier passes through the entrance and exit of the building or park, it will be The detector found that the system can alarm or record automatically, which provides an effective auxiliary management technique for the safety management of the mobile carriers of various large-scale units. flow chart:

2. System page structure diagram

[ad_2]