Zhangjiagang Procuratorate Card Management System Project Case
[ad_1]
introduction
With the rapid development of my country’s economy and the rapid improvement of technological and cultural levels, intelligent equipment has been rapidly applied. The one-card as an intelligent must-have has also been greatly developed. So what is the all-in-one card? One card is to use information card technology as the core, computer and communication technology as means to connect various one card devices into an organic whole, and users can complete identity authentication, fund settlement, parking management, book borrowing, etc. through an IC card. Operations, such as using IC cards to open office doors, using IC cards for dining, shopping, entertainment, conferences, parking, office work, charging services and other activities. There is no need to carry multiple keys to open the door and go to various corresponding departments to pay for the complicated operations. It can be seen that a small card has penetrated into all aspects of unit management and property management, making various management tasks more efficient and scientific, and bringing convenience and safety to people’s daily work and life.
demand analysis
At present, the all-in-one card projects involved in the Zhangjiagang Procuratorate mainly include: all-in-one card management center, access control management system, parking management system, consumption management system, and data borrowing management system.
One Card Management Center: Responsible for the encryption and issuance of all cards in the unit. Combined with the actual situation, it can be combined with the consumer system without independent setting.
Access control management system: The main entrances and exits and some offices in the floors are equipped with access control systems, and the legal identity of the IC card held by the personnel is determined through the access control machine. The IC card information read by the access control machine is judged and analyzed by the controller: the electric lock can only be opened when the card swiping authority is legal, and the personnel can pass, otherwise the electric lock will not be released.
Access control points are mainly distributed: 6 points on the second floor, 24 points on the first floor, 31 points on the first floor, 15 points on the second floor, 29 points on the third floor, 21 points on the fourth floor, There are 16 points on the fifth floor, 16 points on the sixth floor, 20 points on the seventh floor, 18 points on the eighth floor, 19 points on the ninth floor, 18 points on the tenth floor, and 1 point on the eleventh floor. A total of 234 access control points.
Parking management system: The entrance and exit of the basement floor are equipped with a parking management system for internal employees.
Consumption management system: Set up consumption POS machines in the canteen for employees to swipe their cards for consumption. There are about 100 consumers in the unit at a time, and 3 consumer machines will be arranged.
Data borrowing management system: The data borrowing system is set up in the archives room on the first floor for the internal employees of the unit to use.
According to the actual situation of the project, combined with our all-in-one card technology and experience, our company recommends:
The all-in-one card (mainly the access control, parking, consumption, and borrowing system) is applied to the project, and the Mifare-one IC card technology of Philips of the Netherlands is used as the basis, and the MICROSOFT SQL Server 2000 database is used as the platform. Build an advanced, safe, efficient and convenient intelligent information system for the project.
System planning
Access control management system
1. Controller selection: Pingzhi company’s access controllers are divided into single door, double door and four door access controllers. The most suitable controller is selected according to the specific location of each access point on the site and the wiring position. The access point of each floor is selected. All are independently controlled by the access controllers on each floor. The access controllers on all floors have clear wiring in the weak current wells on each floor, which is convenient for on-site installation, commissioning and future maintenance. According to the above construction principles, there are 60 four-door access controllers and 4 two-door access controllers. At the same time, pay attention to the possible increase in the later period and leave the interface appropriately.
2. Communication method: Network communication must have the advantages of flexible scalability, reliability of data transmission, the lowest construction cost, and the ability to effectively diversify risks. Combined with the unit’s own network resources, all access controllers use TCP/IP communication. In addition to using existing network resources, the use of TCP/IP communication can realize the electronic map function of the system itself, which is not available in 485 communication.
3. Selection of access control card reader
Mode 1: One-way induction type (card reader + controller + exit button + electric lock): the employee presents an authorized proximity card outside the door, and after the card reader recognizes and confirms the legal identity, the controller drives the electric lock to release , And record the time of entry. Press the door button to open the electric lock and go out directly.
It is suitable for environments with general security levels and can effectively prevent illegal entry by outsiders. It is the most commonly used management mode.
Mode 2: Two-way induction type (card reader + controller + card reader + electric lock): The employee shows an authorized proximity card outside the door. After the card reader recognizes and confirms the identity, the controller drives the electric lock to release. And record the time of entry. When the user leaves the controlled room, he must also show the authorized proximity card inside the door. After the card reader recognizes and confirms his identity, the controller drives the electric lock to release, and records the time of going out.
It is suitable for environments with higher security levels. It can not only effectively prevent the illegal entry of outsiders, but also query the last person and time to leave, so as to facilitate the implementation of responsibility and provide evidence during a specific period (such as theft).
Mode 3: Card + Password: After swiping the card, you must enter the correct password to open the door. The password is a personalized password, that is, one password per person. The advantage of this is that it is used in higher security occasions, even if the card is picked up, it cannot be entered, and the correct password must be entered.
Mode 4: Biological reader (fingerprint card reader, face recognition card reader): Enter the fingerprint information or face information of the allowed passers-by, and set the door opening authority through the software. When passing through, you only need to input fingerprint information on the fingerprint reader or scan on the face recognition card reader, and the controller will judge its legitimacy. The use of fingerprint (face print) card readers not only improves the safety and tightness, but also reflects the grade of use occasions.
According to the security level of each access control point, the types of access control card readers in different modes are set. For example: the financial room, each storage room, confidential room, computer room, etc. are all set with a password keyboard reader, and the office of the section chief and above (including the section chief) is set with a fingerprint reader, each employee office, inquiry room, and interview room Wait to set the normal reader to swipe in and out, etc. According to the above selection principle, there are 28 fingerprint card readers, 8 face recognition card readers, 1 password keyboard reader, and 240 ordinary access control card readers.
4. Selection of locks: The locks produced by Pingzhi Company have been strictly tested to ensure normal use under severe conditions and high-frequency use. At present, the commonly used locks are divided into magnetic locks and electric mortise locks. Magnetic locks are suitable for wooden doors and single-open electric mortise locks are suitable for wooden doors, and glass doors can be double-opened. It is recommended that the company send professional and technical personnel to investigate the scene and discuss with the user to determine the type of lock. A total of 64 double-door magnetic locks 170 single-door magnetic locks.
5. Centralized control: All access controllers adopt unified control of the network center computer room connected to the tenth floor through the internal network of the unit.
Parking management system
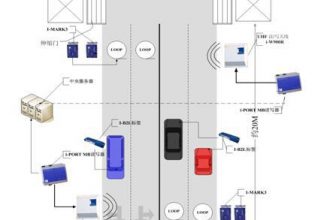
The construction of the parking system needs to design a parking management system that is most suitable for the Zhangjiagang Procuratorate based on the principles of ease of use, comprehensive functions, safety and reliability, and strict management, combined with the actual needs of the unit (for internal employees).
All vehicles in the unit are equipped with long-distance cards. When vehicles enter and exit the parking lot, there is no need to stop and swipe their cards. The long-distance card reader detects the incoming and outgoing vehicles in real time. After the controller receives the correct card reading signal, the barriers will automatically open, and the vehicles will automatically fall after passing by. .
In order to prevent accidental smashing by the barriers of the barriers, ground-sensing coils are buried under each barrier. At the same time, the barriers themselves also have anti-smashing functions. When the bar is dropped, it will automatically lift the bar when it encounters a certain resistance. Form two anti-smashing car protection.
The entrance and exit ticket box is equipped with an intercom function in case of emergency. When the vehicle enters and exits the card abnormally, press the intercom button in the ticket box to call the management center to remotely control the opening of the barrier through the software to ensure the correct passage of the vehicle.
Consumption Management System
The primary consideration of the consumer system is the security of consumer data, including the fast, accurate, and reliable data transmission. All consumer POS machines adopt TCP/IP communication to avoid such problems to the greatest extent. The second is to consider the power of the consumer system. The consumer machine has a powerful deduction function. In addition to the daily staff after swiping the card, the staff enters the corresponding deduction amount to deduct the deduction. For fixed consumption points (such as: the meal window), the machine comes with automatic card swiping. Function, after setting the number of deductions, there is no need for staff to intervene, and the card is directly placed in the induction area and the machine automatically deducts the money. It is convenient and quick. At the same time, the system supports the deduction function of working meal mode, and does not record the consumption amount but only the number of credit card consumption. In addition to the above-mentioned functions, the system also has a time-limited function that fully meets the needs of users.
Book Borrowing Management System
The book lending subsystem uses IC cards to identify readers, and books are identified by bar codes, and readers and bar code readers are used to identify readers and books, respectively. If some fees or fines are involved, they can be directly deducted from the IC card, and the records will be written into the card center database to form a complete data link.
Staffing
System administrator: Responsible for the overall security management of the system, including the physical security of data center equipment, data security, and access security management control
Network administrator: Responsible for providing a safe, reliable and fast network platform environment for the campus all-in-one card system. The network platform environment includes: transmission, exchange, access and other links of equipment and configuration.
Subsystem administrator: Responsible for the integrity of the managed application subsystem equipment, to ensure that it is not damaged or lost, and if there is a failure, contact the relevant technical support unit in time and make a record in time.
Highlight description
Electronic map function: On the access control management host of the monitoring center, the detailed information of the user’s card swiping (including the name of the person who swiped the card, department, entry and exit time, photo information, etc.), door entry and exit events, and door status changes can be reflected in real time through the electronic map Events, various system alarm events and various emergency events. Real-time display through the software is clear at a glance, which is convenient for users to understand the safety status of each unit door at the first time.
Abnormal alarm function: all alarms such as illegal intrusion alarm and door unclosed alarm for a long time will display red flashing records on the access control monitoring computer in real time, and drive the computer speakers to remind the administrator to pay attention.
Door sensor signal: The electric locks (magnetic lock, electric bolt lock) used in the access control system all have their own door sensor signal feedback function. There is no need to purchase a door sensor separately, which saves costs. Door sensor signal feedback function: to ensure that the door is closed normally. After the closing is successful, the electric lock transmits the signal to the controller, and uploads it to the access control software via the network to display the door status in real time.
Long-distance directional positioning card reader: The parking management system adopts a long-distance directional positioning card reader, which does not require ground sensing, which saves costs and improves the stability of the card reader itself. The card reading angle outside the car is 60° to 80°, the card reading angle inside the car is less than 60°, the card reading distance on the front is 4 to 6 meters, and the card reading is not on the back. Different from ordinary long-distance card reader 360° card reading and ground sensing trigger work. The directional positioning of the card reading ensures the accuracy of the card reading, does not require ground sensing to improve the real-time performance of the card reading, and ensures that the entire parking management system is more reliable, stable and fast.
ARM technology
All controllers adopt advanced 32-bit ARM7/9 microprocessor, which greatly enhances the functions of the controller and also improves the stability of the system.
System advantages
Advanced and practical
System intelligence: The communication capabilities of all front-end equipment and the system are reliable, with automatic fault detection and alarm functions.
Stupid operation: The system software has a good man-machine interface, and the operator can easily learn and operate the operating system to complete tasks. The system’s front-end products and system software have good learning and operability, especially operability. Under the condition of rough computer operation, you can master the operating essentials of the system through simple training, and achieve the operation that can complete the duty task.
Networking: In today’s highly developed and widely used computer network technology, all communication equipment adopts computer network communication to meet market requirements and stand the test of time.
System scalability: The system has good compatibility while fulfilling current functional requirements, reducing costs for future expansion requirements.
Reliable and stable
To ensure the stable operation of the system, we conduct serious reliability tests on all equipment from the configuration of the computer to the configuration of the system and the configuration of the front-end equipment. The hardware design of the split machine is highly integrated, with simpler structure, fewer failures, and lightning protection design. , Eliminate crashes (multi-level watchdog). At the same time, even if the failure rate is very low in actual operation, there will be problems due to various unexpected reasons. We fully consider the existence of the problem, and further consolidate the preservation and rapid recovery of data.
Upgrade maintenance: Even the most advanced system will fall behind due to the passage of time. The company promises to use the Pingzhi system software to provide free upgrade services.
Heiji’s advantages
1. Quality control and certification
1. Pingzhi products are designed and produced in strict accordance with the process regulated by the ISO9001:2008 quality system to ensure product consistency, stability and reliability;
2. Some products of Pingzhi obtained the “China National Compulsory Product Certification (3C) Certificate” issued by the “China Quality Certification Center”;
3. The non-contact IC card reading and writing machines all have the industrial product production license issued by the General Administration of Quality Supervision, Inspection and Quarantine;
4. All access control products have passed the inspection of “National Security Management System Product Quality Supervision and Inspection Center (Shanghai)”;
5. Our company was assessed as an AAA credit enterprise in September 2007.
6. Our company was appraised as “Advanced Enterprise of Social Responsibility” by Hangzhou Municipal People’s Government in March 2009.
2. Independent intellectual property rights
1. Pingzhi products are all independently developed and have complete intellectual property rights.
2. The Pingzhi All-in-One Card management software obtained the “Computer Software Copyright Registration Certificate” issued by the “National Copyright Administration of the People’s Republic of China”;
3. Core technology
1. The one-card controller adopts the international advanced 32-bit ARM9 microprocessor and embeds the latest industrial standard Linux operating system. The system control function and stability are greatly enhanced.
2. Data exchange through the TCP/IP (100MHZ) communication protocol to ensure the real-time performance and data processing capabilities of the system. It also has TCP/IP, RS-485, RS-422, RS-232, CAN, Wiegand, etc. Communication interface mode.
3. A variety of safety protection measures.
a. All input and output are equipped with dynamic voltage protection.
b. Instantaneous overvoltage and short circuit protection.
c. Advanced lightning protection technology can resist lightning impacts of tens of thousands of volts, including the system’s secondary lightning protection measures.
4. Provide various forms of interfaces such as OPC, ODBC, etc. to facilitate the integration with other intelligent systems and realize linkage control and management.
5. It can perform remote login query and control, and can download tool programs remotely, which is convenient for system maintenance and upgrade.
4. Rich product line and complete solutions
1. The Pingzhi product line currently covers access control, attendance, parking, consumption, elevators, channel control, patrols, library management, item debit, conference sign-in, temporary visitors, identity authentication, water control, hotel door locks, etc. , And they are all managed by the same IC card and the same database to achieve the true meaning of the card, which can meet the various supporting needs of our customers.
2. More than 10 years of engineering experience in R&D, manufacturing, and many large-scale cases involving various industries, which can provide systems, comprehensive solutions and technical guarantees for various applications.
5. Perfect service system
1. The company has spare parts for each completed project. Once faults are found, they will be replaced with spare parts to ensure uninterrupted use of the products.
2. A strong service team (currently there are 20 after-sales service personnel in Hangzhou). It can provide customers with fast and effective technical support and services. Hangzhou has a research and development base and service center, which can provide customers with more personalized service needs.
3. The company has hardware research and development department, software research and development department, product quality department and other departments to provide comprehensive services for product quality and upgrades.
Access control management system
The non-contact IC card access control management system integrates computer technology, electronic technology, magnetoelectric technology and non-contact IC card technology, enabling a complete “dialogue” function between the IC card and the lock, and the smart card is used to control the opening of the door lock , Thus creating a new concept of access control management. It provides managers with a safer, faster, and more automated management mode, and it also brings great convenience to users. There is a clock setting in the system, which can stipulate the time limit for entering the management area or implement automatic management of the public area. The management department can implement time management for internal personnel. It has multiple functions such as authorization, recording, query, statistics, anti-theft, and alarm for personnel entry and exit. It is convenient for internal personnel or users to enter and exit freely according to their authority, and at the same time, it prevents outsiders from entering and exiting at will, and improves security. ability.
System composition
The Pingzhi Card Access Control System consists of an access control controller, an access control card reader, a door opening button, a door forbidden electric lock (or personnel access equipment, such as three roller gates, swing gates, wing gates, etc.), and access control software. A centralized management access control network system is formed through the management of the host, the communication network layer and the controller. All the real-time data generated in the controllers are uploaded to the database server of the control center by each controller through the communication network, without manual collection. It is an access control system that truly gives full play to the advanced nature of embedded network technology. (Pictured)

For more information, please contact: Hangzhou Pingzhi Technology Co., Ltd.
Building 20, Xidoumen Road, Xihu District, Hangzhou
TEL:0571-89938886 FAX:0571-87906161
E-mial:[email protected]
[ad_2]