Zhihui RFID smart prison security management system
[ad_1]
Part One Introduction to RFID
1. Introduction to RFID technology
RFID (Radio Frequency Identification Technology) is a non-contact automatic identification technology that uses radio frequency signals to automatically identify target objects and obtain related data. Conceptually, RFID is similar to barcode scanning. The barcode scanning technology attaches the encoded barcode to the target and uses a dedicated scanning reader to use photoelectric signals to transmit information from the bar magnet to the scanning reader; and RFID Use a dedicated RFID reader and a dedicated RFID unit that can be attached to the target, and use RF signals to transmit information from the RFID unit to the RFID reader.
2. Features and advantages of RFID technology
RFID is a flexible application technology that is easy to control, simple and practical, and especially suitable for automatic control. The identification work does not require manual intervention. It can support both read-only working mode and read-write working mode without contact or aiming; Can work freely in a variety of harsh environments: short-distance radio frequency products are not afraid of oil stains, dust pollution and other harsh environments, and can replace bar codes, such as tracking objects on the assembly line of a factory; long-distance radio frequency products are mostly used in traffic, and the identification distance can be Up to tens of meters, such as automatic toll collection or vehicle identification. Its unique advantages are beyond the reach of other identification technologies, mainly in the following aspects:
Convenient and fast reading: Data reading does not require a light source, and can even be carried out through the outer packaging. The effective recognition distance is larger, and the effective recognition distance can reach more than 30 meters;
Fast recognition speed: As soon as the terminal enters the magnetic field, the reader can read the information in it instantly, and it can process multiple terminals at the same time to realize batch recognition;
Large data capacity: The two-dimensional barcode (PDF417) with the largest data capacity can only store up to 2725 numbers; if it contains letters, the storage capacity will be less; RFID terminals can be expanded to dozens of K according to user needs;
Long service life and wide range of applications: Its radio communication method enables workers to work without being in dust, oil and other highly polluted environments and radioactive environments. The closed packaging of the terminal makes the service life much longer than the printed bar code;
The label data can be changed dynamically: The data can be written using the programmer, which gives the RFID label interactive portable data file function, and the writing time is less than that of printing a bar code;
Better security: Not only can it be embedded or attached to products of different shapes and types, but also password protection can be set for the reading and writing of terminal data, thus having higher security;
Dynamic real-time communication: The terminal communicates with the reader at a frequency of 50 to 100 times per second, so as long as the object attached to the RFID terminal appears within the effective recognition range of the reader, its position can be dynamically tracked and monitored.
Part II Introduction and development prospects of RFID smart prison management system
The RFID intelligent prison management system is a safe and reliable way of distinguishing and identifying detainees, and a one-to-one intelligent prison administration management system that matches each person’s information in the management system with each person in reality, realizing prison management in a true sense Informatization has entered the path of “requiring police power from science and technology”.
The RFID smart prison management system adopts the most advanced Active (active/active) radio frequency identification technology at present. It is a set of software and hardware combined application system specially designed and developed for the needs of prison personnel situation management and monitoring. The RFID prison intelligent management system has been proved to be very efficient in the use of Virginia prison, Michigan prison, California prison, Illinois prison and Ohio prison, Dutch prison, Singapore prison, and Kajang prison in Malaysia. Reliable management system, which enables managers to grasp the detailed information and number of detainees in each controlled area of the prison in real time, effectively prevent detainees from escaping, reduce the chance of criminals forming parties and making troubles, secretly monitor high-risk detainees, and track down Follow up on the occurrence of violent incidents and protect the personal safety of managers and detainees to the utmost extent. In addition, the system can also automatically count the number of people in the designated area and the information of the police officers on duty in the surrounding area, which greatly reduces the work intensity of the prison management staff, and can quickly locate the police officers on duty in the event of an emergency.
The RFID prison management system can also be used in combination with a face recognition system, an intelligent access control system, and a video capture system, which can provide convenient and efficient modern methods for prisons to carry out various management tasks for criminals.
Part III Function Description of RFID Intelligent Prison Management System
1. Hardware introduction of RFID smart prison management system
The RFID smart prison management system uses active RFID hardware devices. The equipment mainly includes: Receiver, Activator and Active Tag.
Receiver: A device that reads (and sometimes writes in) tag information. It can be designed as a handheld or fixed type.
receiver
Frequency band: 433 MHz
Communication interface: RJ-45->10 Mbps, RS232->19200 bps, RS485->19200 bps
Data line communication distance: RJ-45->100M, RS232->15M, RS485->1000M
Applicable voltage: 220VAC 50HZ / 24 VDC
Power consumption: <1W
Ambient temperature: -30 ℃-+100 ℃
Storage temperature: -60 ℃-90 ℃
Anti-collision: 200 tags (bracelets) can be identified at the same time
Communication speed: 19200bps
Activator: activates the tag device, and can also write the ID number to the tag
Frequency: 125 K Hz
Communication interface: RS232->19200 bps, RS485->19200 bps
Applicable voltage: 220VAC 50HZ / 24 VDC
Power consumption: <24W
Ambient temperature: -40 ℃-+85 ℃
Storage temperature: -60 ℃-90 ℃
Transmitting power: 37 dbm
Tag: Generally, electronic data in an agreed format is stored in an electronic tag. In practical applications, the electronic tag is attached to the surface of the object to be identified. The reader can read and identify the electronic data stored in the electronic tag without contact, so as to achieve the purpose of automatic identification. There are two types of tags: Passive tags and Active tags. Active tags are powered by batteries and have a longer reading/writing distance. They are also called active tags and generally have a longer reading distance. After receiving the microwave signal from the reader (reading device), the passive electronic tag converts part of the microwave energy into direct current for its own work. Generally, it can be maintenance-free, has a low cost and a long service life. Active tags are small and light, and have a shorter reading and writing distance. They are also called passive tags.
Active (active/active) technology and Passive (passive/passive) technology comparison
|
Active (Active/active) technology |
Passive (Passive/passive) technology |
|
Remote automatic detection |
Prisoner swiping card at close range |
|
Automatically send |
Prisoner swiping card at close range |
|
Self-check damage alarm |
Can not self-check damage alarm |
|
Prison Guard Help Device |
No Prison Guard Help Device |
|
Set up a cordon and call the police when the prisoner crosses the line |
No cross-border alarm |
|
Penetrate the human body and accurately identify multiple people at the same time |
No penetration |
According to whether the stored information is rewritten, the terminal is also divided into a read-only terminal (read only) and a read-write terminal (read and write). The RFID prison management system adopts a read-write terminal. The information in the read-only terminal is about to be written during the production of the integrated circuit, and cannot be modified later, and can only be read by special equipment; the read-write terminal writes the saved information into its internal storage area, and also when it needs to be rewritten You can use special programming or writing equipment to erase and write. Generally, it takes much longer to write information into an electronic terminal than it takes to read information from an electronic terminal. The time spent writing is on the order of seconds, and the time spent reading is on the order of milliseconds. The tags are composed of coupling elements and chips. Each tag has a unique electronic code and is attached to the object to identify the target object; each terminal has a globally unique ID number-UID, which is placed in the ROM when the chip is made , Cannot be modified. The user data area (DATA) is for users to store data, which can be read, written, overwritten, and operated.
Prisoner label
Frequency band: 433 MHz
Wireless data rate: 256k ps
Service life: more than 3 years
Ambient temperature: -40 ℃-+80 ℃
Storage temperature: -60 ℃-90 ℃
Built-in antenna: omnidirectional
Receiving sensitivity: ≮ -90dBm
Transmitting power: 0 dbm
2. Advanced features of hardware products
1. The electronic chip has a long service life and can work in harsh environments;
2. The reading range is larger, and it can be read and written within the range of 40-50m from the terminal to the reader;
3. It can realize real-time tracking and positioning, and automatic monitoring;
4. Outdoor hardware is equipped with high-quality lightning protection, and the equipment has a 10-minute power outage backup power supply
5. The terminal equipment can be designed with different appearances such as wrist type or ankle type as required, and one-time design or recycling type can be selected.
6. Waterproof and replaceable batteries make the label longer life and have damage alarm function;
7. A variety of different colors can be provided on the software to facilitate classification of personnel
3. Basic functions of the system
1. Basic data management The basic data management function is the foundation of the RFID monitoring and management system. The RFID monitoring system needs some basic data to provide information for other functions of the system. These basic data include: basic personnel information, basic terminal information, personnel and electronic tag correspondence, personnel classification and grouping, etc. as the picture shows:
The operation interface is mainly used to set the basic personnel information, the correspondence between the electronic tags and the corresponding personnel, and the setting of personnel access permissions.
2. Basic system settings:
The upper part is the corresponding display of the equipment on-site, and the lower part is the equipment information. In the device information, only “Activator ID” and “Receiver IP Address” can be filled in or modified. “Area No.”, “Room Description” and “Entry Description” should be selected from the upper site plan when adding. This interface provides a search function, which can be queried by “activator ID” or “receiver IP address” respectively.
3. Monitoring alarm function
3.1 Illegal Entry Alarm: Each monitoring point has a certain access authority, and only authorized personnel can enter. If an unauthorized person enters the monitoring point (restricted area), an illegal entry alarm will be triggered, the detailed information of the intruder will be rebounded, and the video will be activated to capture the alarm area.
3.2 Terminal damage alarm: When the prisoner’s terminal is damaged, the system will immediately issue an alarm and highlight the location.
3.3 Alarm for the policeman for help: When the policeman presses the button of the terminal he wears, the system will immediately issue an alarm and highlight the location.
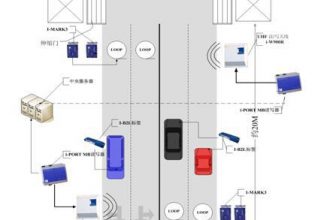
Five, network connection diagram
The network connection diagram of the system is shown in the following figure (the RFID intelligent prison management system version software does not limit the number of receivers used. When the system uses multiple receivers, the following figure can be used as a reference):
The receiver transmits the received data to the application server through the network. After the application server analyzes and processes the data, it stores the record in the data server and provides the required data to each work terminal.
Part IV Instructions for Use of RFID Smart Prison Management System
1. Use of RFID Smart Prison Management System
1. Personnel data input: Enter the prisoner’s data in the corresponding terminal number database, such as the crime, the sentence, the photo, etc.The function of personnel information management should be divided into multiple levels of personnel categories based on the special needs of prisons: police officers, prisoners (category one, two, three…) prisoner information, photos, crimes committed, sentence period, gang (gang), attendance , Performance records, personal restricted areas, schedule review, cell allocation, transfer records
2. Monitoring of the number of felons in the area: Focus on monitoring the actions of prisoners in the felon area, such as counting the number of people at a fixed time, restricted movement areas, area gates or fence lines.
3. District population monitoring and access control: medical (hospital) district population monitoring, meeting area control, production area control, main import and export control
4. In-prison consumer electronic management: Combine electronic consumer cards and electronic tags for detainees to wear. This will allow detainees to consciously protect the electronic tags they wear and reduce disputes between detainees due to money. .
5. Emergency call for help from the police officer: The police officer presses the button on the terminal to trigger an alarm. And highlight personnel information and location.
6. Historical playback: You can query historical access records in two ways, by personnel or by monitoring points. Fill in the query conditions and click the “Query” button to get a list of historical records. Use the “playback” function to dynamically display the personnel’s activities on the floor plan.
7. Emergency response procedures: The prison staff pre-designed and entered the emergency response program table. When an alarm occurs, the system will pop up the response program to the monitor terminal display. The operator must take action according to the preset program, and after completing each program Confirm with the system, and the system will automatically register the operator’s identity and operating time, and confirm the responsibility.
Example: Monitoring staff number 1347869
1 .Notify the guard to close all entrances and exits. Confirm
2 .Notify frontline officers of the location of the accident
3.Report the accident Confirm
4.Report to the top leadership
8. System self-checking and anti-breaking: The system regularly checks the status of each reader and activator to ensure the normal operation of the system. If an instrument fails, the system will automatically issue an alarm and display the location of the faulty instrument
9. System upgrade and expansion: Connect video surveillance, simple procedures to add monitoring points to comprehensive coverage of prisons, biometrics, electronic wallets, operator terminals, corresponding passwords to confirm identity, and remote access
10. Software list and permissions
a. Main database: Only the system administrator can operate the main database, such as data backup, but cannot modify the stored data.
b. Monitoring center: Responsible for daily monitoring operation is a pure operation mode. When an accident occurs, operate according to the system pop-up response procedure, and the system automatically registers the identity of the supervisor and the operating time.
c. Data Center: Responsible for inputting basic personnel information and updating prisoners’ information according to prescribed procedures and cycles. Such as labor performance, prison term, health, rewards and punishments, merits and demerits, funds, etc., the system automatically registers the operator’s identity and operating time.
d. Prison Administration Distribution/Recycling Center: The user terminal provided by the prisoner must be allocated, recycled, activated, and dormant monitoring functions by the prison administration office. The system automatically registers the operator’s identity and operating time.
e. Client software: The client can log in to the system at any time to view the real-time monitoring status, and to inquire about all operation records and playback data of various departments belongs to the cadre-level authority.
Part 5 Application Case
1. European and American prisons have applied RFID Active Active (active/active) technology
Alanco Technology is the developer of the TSI PRISM RFID prison tracking system. The Virginia Department of Prisons (VDOC) recently announced that it has selected the company’s T RSI RRISM system to be installed in the prison rehabilitation and treatment center. The project contract is worth 600,000 U.S. dollars. The terms of the contract are under negotiation, and an agreement is expected to be reached before the end of the year, and then construction will begin soon.
In April 2005, after the Virginia Department of Prisons announced a request for an RFID tracking system solution, Alanco quickly responded. This system will be used in the Marion Center, a psychiatric treatment facility for male inmates with 230 beds. One of the main purposes of the bureau’s pilot project is to evaluate the performance and benefits of RFID tracking for future use in the bureau’s large prisons. The contract obtained through the solicitation plan lasts for 8 years and is re-signed once a year. It will promote the adoption of fast-tracking systems in other prisons of the bureau. There are 42 rehabilitation facilities for prisoners under the bureau, and a total of 34,000 prisoners are held.
This system can track the location and movement of prisoners and police officers, greatly reduce prison management costs, and improve the safety of police officers and facilities. Using RFID technology, related software, and patented hardware, the system can identify, locate and track prisoners and police officers in real time indoors and outdoors. The system has been applied in Michigan, California, Illinois and Ohio.
2. Shandong Lunan Prison uses (RFID Active) technology
In order to improve safety, Shandong Lunan Prison uses an intelligent management system in the management of prisoners and wears RFID electronic tag bracelets to prisoners. After the prisoner enters the controlled area, the system activator activates the RFID electronic tag worn by the prisoner or prison guard, the tag transmits a signal, and the micro signal sent by the RFID electronic tag is received by the system receiver. The system receiver transmits the signal to the central server through optical fiber, and the server loads the time stamp. The system software uses these data to calculate the position and status of each RFID electronic tag. At the same time, it is judged whether there is an abnormal condition, and an abnormal alarm is automatically issued after it occurs, and a system emergency mechanism is adopted. Transmit all information to the terminal client. The terminal client displays this information in different ways, and allows the manager to operate it through the man-machine interface of the graphical interface, and saves the names and operation records of all operators.
Guangzhou Zhihui Technology Co., Ltd. is an RFID system integrator. You can get in touch with our company in the following ways and serve your company enthusiastically!
Phone 020-87511987
Q: 243313899
Intelligent recognition, gathering the best of hundreds of families!
Author: Zhihui Technology
Source: Zhihui RFID Technology Network
All rights reserved, welcome to repost, please indicate the author and source!
[ad_2]