Jiangsu Tangan: Passive UHF RFID"Pig cow sheep"Safety Traceability Management System
[ad_1]
I. Overview:
Project Background
Some kind of livestock improvement center, in order to realize the unified management of all breeding farms under its jurisdiction. Through the use of RFID radio frequency identification technology, all pigs, cattle and sheep in each farm are identified by electronic ear tags, and an “electronic identity” is established for each physical pig, cattle and sheep, so as to realize the feeding, breeding, epidemic prevention, and delivery of all farmed pigs, cattle and sheep. All information of key links such as slaughter is automatically collected, and collected to the management center software through computer network technology to form electronic file information of all breeding pigs, cattle and sheep.
Project summary
The pig, cattle and sheep safety traceability management system is mainly conducive to the Internet of Things RFID technology, using RFID electronic pig, cattle and sheep ear tags as the information carrier, and relying on technologies such as network communication, system integration and database application to realize the feed and breeding of pigs, cattle and sheep. , Tracking records and timely trace management of each link of epidemic prevention and slaughter at the factory to ensure the safety and reliability of the quality of pig, cattle and sheep products, so that consumers can truly eat safe and safe pig, cattle and sheep food. In this technical scheme, “sheep” is taken as an example to describe the scheme of the pig, cattle and sheep safety traceability management system.
Significance of project construction
1. The establishment of the pig, cattle and sheep safety traceability management system will improve the production modernization level of the livestock improvement center, promote the healthy and sustainable development of pig, cattle and sheep breeding, and enhance the core competitiveness of the enterprise
2. Promote the informatization process of the breeding farms under the Animal Improvement Center, improve the efficiency of breeding, and reduce the cost of breeding
3. Information transparency, reduce public doubts, and reduce losses caused by unexpected markets to enterprises
4. The full traceability of pig, cattle and sheep information provides strong support for the market development and brand establishment of pigs, cattle and sheep
5. The pig, cattle and sheep safety traceability system allows consumers to supervise the behavior of enterprises, and encourages breeding enterprises to improve the quality of meat products
6. Let consumers eat reliable, high-quality, delicious and healthy pork, beef and mutton
2. System construction content
Breeding link
Raw sheep breeding is divided into different stages such as breeding, pregnancy, young sheep, and finished sheep
One is that rams and ewes can be dynamically managed by wearing RFID electronic ear tags, including information on breeding, pregnancy, and baby-bearing information, etc.
Secondly, when the lambs are born 30 days later, they will receive the first vaccine and health care. At the same time, they will wear colored RFID electronic ear tags that distinguish males and females, and associate the lamb’s ewe and their parents with the electronic ear tags. In the process, the breeder uniformly writes the feed feeding information, epidemic prevention information, medication information, and environmental information of the young sheep and the finished sheep into the RFID electronic ear tags of the pigs, cattle and sheep through the information platform or PDA, and uploads the data to the enterprise cloud through the network Platform data center, and establish complete individual sheep breeding files in the data center
Third, when the lambs are 50 days old, they will come out of the ewe pen, and the lambs selected as breeding lambs will be raised permanently (self-retained and cultivated), and other lambs will be transferred to the breeding shed to continue feeding into finished mutton lambs.
Factory link
When the finished mutton is loaded into the car, the UHF reader installed above the entrance of the breeding factory can automatically read and count the RFID electronic ear tag information of the finished mutton, and automatically record the time of delivery and other information. (And the factory flow information is entered in the PDA or background input when loading the car, and the illegal or under-factory conditions will automatically alarm when the sheep passes the gate) and upload the data to the enterprise cloud platform data center through the network, and the system will automatically save the factory information In the corresponding finished sheep file database for follow-up traceability and to provide the initial basis for the financial accounts of the breeding stock improvement center.
Mobile handheld terminal PDA office
Develop application modules for breeding, feeding, quarantine, quarantine, and data query on the mobile handheld terminal PDA; feeders or quarantine personnel can directly use the handheld terminal to operate when they raise sheep every day or perform quarantine and quarantine, and the data can be wirelessly operated. The network connection is automatically synchronized and imported to the security traceability database center.
3. Project construction plan
Design Principles
In order to ensure the feasibility and stability of the scheme, and to adapt to the continuous development of the application, the following principles should be followed in the design of the system scheme:
(1) Practicality: The system planning should provide guidance for implementation and provide a basis for further implementation; the function of the entire system should be completely based on the customer’s operation and management needs; the selection of the plan should pursue practicability and must comply with the management of the breeding stock improvement center Practical needs, technically must have a certain height, the means emphasize practicality;
(2) Advancement: The system design should adopt advanced concepts, technologies, methods, and equipment, which are reliable and mature, reflect the advanced level of the world today, and have development potential;
(3) Openness: The entire system should follow the overall development specifications and interface standards, and at the same time, consider the interface with some existing application systems to ensure the integrity of the system structure and the consistency of information. It should be able to support the interconnection of heterogeneous systems and different network protocols, provide open network interfaces and data interfaces, and different systems can work together to exchange data and share information;
(4) Economy and redundancy: The system strives to be designed to closely meet the needs of users, while leaving room for possible value-added services, and generally has a good price-performance ratio;
(5) Scalability: The system must have good compatibility, portability and upgrade prospects. It has scalability and business reorganization capabilities in terms of system capacity, communication capabilities, and processing capabilities. In the design, it is necessary to ensure that the system structure is modular, and the function modules can be smoothly expanded;
(6) Ease of use: A user-friendly cross-section must be provided, and standardized industry language must be adopted. Friendly, clear, simple, convenient and fault-tolerant;
(7) Maintainability: For application systems, maintainability is reflected in easy analysis, easy modification, easy testability, and stable business process reorganization. Use a modular structure; for network systems, it is reflected in the system monitoring, testing, and diagnosis tools that can provide effective network management to ensure that the system maintenance and management are concise, convenient and effective;
(8) Reliability: Comprehensive consideration should be given to the system structure, design scheme, equipment selection, technical service, etc., to ensure that the system can continue (7X24 hours) operation without failure. At the same time, the system should have error handling, fault tolerance, and redundant backup capabilities;
(9) Security: The system should have a high degree of security and confidentiality. It can prevent various forms of system damage through the hierarchical protection of the system, the control of data storage permissions, the setting of firewalls in the internal and external networks, and virtual routing isolation. Trespass;
Data collection based on RFID
RFID radio frequency technology is a non-contact automatic identification technology, which automatically recognizes the target object and obtains related data through radio frequency signals. The identification work does not require manual intervention and can work in various harsh environments. Compared with barcode technology, RFID can save more time, manpower and material resources, reduce production costs, and improve work efficiency. The advantage is that it is not limited to the line of sight, the recognition distance is farther than the optical system, the radio frequency identification card has the ability to read and write, can store a large amount of data, and has a certain degree of intelligence, which is difficult to forge.
This system manages the birth, breeding, and delivery of pigs, cattle, and sheep through the use of UHF pig, cattle and sheep ear tags containing RFID chips. In each process, various information about the sheep is recorded through ear tags, and through the use of handheld or non-mobile devices. The card reader collects data, and finally realizes the information traceability of pigs, cattle and sheep.
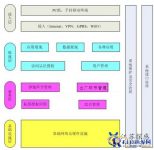
Overall architecture
System construction framework
 620)this.style.width=620;”>
620)this.style.width=620;”>
Figure 1 System construction framework
As shown in Figure 1, the system adopts a multi-layer structure, which is divided into four layers: the access layer, the presentation layer, the service layer, and the infrastructure layer.
(1) Access layer
Users use PCs and handheld mobile terminals to access the pig, cattle and sheep safety traceability management system through different access methods (Internet, VPN, GPRS, WIFI).
(2) Presentation layer
Provide a unified representation and display portal for internal information interaction and all business systems. Realize three types of services: application display, authentication and authorization, and system management. The display layer will realize the display mode of the PC browser and the display mode of the handheld device client.
(3) Business layer
As the implementation of the specific application of the pig, cattle and sheep safety traceability management system, it includes the business realization of the entire process of breeding, the business realization of the factory link, the realization of the pig, cattle and sheep ear tag authorization business, and the integrated management of related businesses.
(4) Infrastructure
Including basic network and hardware facilities, etc., to ensure the normal operation and access of the system.
In addition, the system also includes systems and safety management and interface management that run through all levels.
System Technical Framework
The development of the “Pig, Cow and Sheep” safety traceability management system will achieve componentization, modularization and platformization to ensure the various functions of the systems and subsystems and meet the needs of sustainable development. Each application program will be highly advanced. Modularization in order to support cross-platform transplantation capabilities, and at the same time have an expandable technical framework and standard external interfaces, and reserve interfaces for application systems and secondary development outside the system.
Take the “pig, cattle and sheep” safety traceability management system as an example, the technical framework diagram is shown in the figure below:

Figure 2 System technical framework
System composition
This system is composed of two parts: hardware and software.
The hardware includes the central WEB server for software deployment, the cloud platform data center server for providing data services, and the handheld UHFReader, Fixed UHF readers, HD cameras, UHF RFID ear tags and network equipment, etc.
The software part includes the “Pig, Niu and Sheep” safety traceability management system deployed on the central WEB server, and the handheld client of the “Pig, Niu and Sheep” safety traceability management system deployed on the handheld UHF.
Operating environment requirements
In order to ensure satisfactory performance, the pig, cattle and sheep safety traceability management system has the following minimum and recommended client and server application system requirements.
The following platforms support the installation and operation of the system.
|
plan
|
operating system
|
|
Client
|
Microsoft Windows 2000 Professional
Microsoft Windows 2000 Server/Advanced Server
Microsoft Windows 7
Microsoft Windows XP Home Edition
Microsoft Windows XP Professional and above.
Note: On all these systems, Microsoft Internet Explorer 6.0 or higher is also required.
|
|
server
|
Microsoft Windows 2000 Professional with Service Pack 2.0
Microsoft Windows 2000 Server with Service Pack 2.0
Microsoft Windows 2000 Advanced Server with Service Pack 2.0
Microsoft Windows Server 2003
Microsoft Windows Server 2008
Linux
|
The pig, cattle and sheep safety traceability management system is a database application software system based on J2EE technology. To enable the system to run correctly, the following additional components are required (Note: These additional components have been integrated in Windows XP, Windows Server 2003 and later superior).
|
plan
|
Features
|
Required software
|
|
Client
|
IE browser
|
IE browser
|
|
server
|
System operating environment
|
JDK1.6
|
|
|
SQL Server
|
Mysql5.1/Microsoft SQL Server 2005/2008
|
|
|
Tomcat
|
Tomcat6.0
|
|
plan
|
Required processor
|
Recommended processor
|
RAM required
|
Recommended RAM
|
|
Client
|
Pentium IV 500MHz
|
Pentium IV series or faster
|
512 MB
|
1G or higher
|
|
server
|
Pentium IV 1GHz
|
Pentium IV series or faster
|
1G
|
2G or higher
|
Note: In order to make the system display information complete and beautiful, it is recommended to use a monitor with a resolution of 1024*768 or above.
System function design plan
System function framework
According to the business needs of Zhuniuyang, the software system we designed will include the following functional modules, as shown in the figure below:
 620)this.style.width=620;”>
620)this.style.width=620;”>
Figure 4 PC terminal system function module diagram
 620)this.style.width=620;”>
620)this.style.width=620;”>Figure 5 Mobile handheld PDA client system
Basic data management
Basic data management refers to the initialization of some basic data used in the business management process. These data run through the entire business process. After initialization, the data needs to be used in the business module to directly select it. Basic data management includes sheep house management, employee management, ear tag management, camera management, feed information management, drug information management, etc.
Sheep shed management
Sheep shed management is used to manage the shed information of all the breeding farms under the breeding stock improvement center. The parent of the shed is the building number. The breeding stock improvement center needs to create a building number for all the sheep sheds, as well as for each sheep building. All sheep sheds are compiled with a shed number. After editing, write the number on the wall of each sheep shed, and then enter the information in this module of the system. The administrator can add new information to the data. Modify, delete and other operations. The card of the building number is an ultra-high frequency hard card that prints the LOGO information of the breeding stock improvement center. The card stores the related information of the shed and sheep breeding in the sheep house of the building. It can also be used to manage the breeding and fighting of the entire sheep Vaccines and other tasks are also convenient for the leaders of the Breeding Animal Improvement Center to bring hand-held equipment for inspections from time to time.
Staff management
Employee management is used to manage the information of all employees in the breeding stock improvement center. The system administrator can add, modify, and delete member information.
Ear tag management
Ear tag management is used to manage the information of all ear tags purchased by the breeding stock improvement center. When ear tags are purchased, they are marked with numbers. The system operator needs to manually enter these numbers into the system through this module. Of course, the process of entering ear tags can be carried out at the same time as the process of using ear tags. When ear tags are used, only the ear tags to be used are entered, and the data is written into the ear tags through the tag reader. Once the ear tag is used, it is bound to a specific sheep. As long as the number on the ear tag (of course the number is also stored in the RFID chip in the ear tag), all information related to the sheep can be queried.
Feed information management
Enter the feeding information of various feeds into the system for management, and directly select the type of drink to be fed in the feeding management. System operators can add, modify, and delete member information.
Drug Information Management
Enter the information of various drugs that may be used in the growth process of the black sheep into the system for management, and directly select the type of drugs used in the epidemic prevention management. System operators can add, modify, and delete member information.
Breeding management
Breeding management is the most important functional module in the system. This module will manage all the affairs of sheep in the entire breeding process.
Ewe Management
Ewe management is to manage those ewes that are used to conceive and give birth to lambs. The system needs to record the corresponding ear tag numbers of these sheep, the number of the sheep house where they live, the food information fed during the breeding process, the medication information, and so on. The system operator can add, modify, delete and other operations on this information.
Breeding (ram) management
Sheep management is the management of high-quality rams used for breeding. Just like ewe management, the system needs to record the corresponding ear tag numbers of these sheep, the number of the sheep shed where they live, the food information used during the breeding process, the medication information, etc. .
Breeding management
Breeding management includes two parts: breeding plan management and breeding management.
Breeding plan management is a plan drawn by the laboratory through scientific calculation of which ram and which ewe mate best. The plan information is entered into the system and the staff will implement it according to the plan when it is to be bred.
Breeding management is to manage the actual breeding situation, the information includes ram number, ewe number, mating date, etc. The actual operation is that the staff read the ear tags of the rams and ewes through the handheld when the sheep are mated, and then confirm them through the client software interface of the handheld. After confirmation, the data will be sent wirelessly to the server, and the management can use Visit the web to query this information.
Sheep management
Lamb management refers to the lambs that have not been assigned to the shed not long after they were born, and these sheep are still in the mother’s shed. The source of this information is that the lamb of the mother sheep’s birth will be recorded here by the staff. By entering the number of the ewe and the total number of sheep born, the system will generate a string of new numbers for each lamb by default. . After 30 days, the lambs should be treated for the first epidemic prevention, and the sheep should be earmarked and classified by gender. At this time, the information of these lambs needs to be updated, such as the gender of the sheep, the ear tag number, and the epidemic prevention information. Wait.
Growing sheep management
Breeding sheep management is used to manage sheep that have been allocated sheep sheds. In this module, you can query all the sheep’s information, including parent number, sheep shed number, date of birth, weaning date, feeding status, epidemic prevention, etc. Wait. You can search based on the mother’s ID number, sheep house number, ear tag number, etc.
Feeding management
Record the feeding situation after each feeding of the sheep. When recording this information, you can operate in batches according to the building number. The operation can be operated through the computer or the handheld client.
Epidemic prevention management
Record the epidemic prevention situation after every epidemic prevention of sheep. When recording this information, you can operate in batches according to the building number. The operation can be performed through the computer or the handheld client. If the sheep in a sheep shed are not quarantined in one go, select the building number first and then check all the sheds downstairs that have been quarantined.
System Management
System management includes functional modules for system maintenance, and the main function is to complete the task of system maintenance at the bottom. Included functions are: user management, authority management, data management, system log, role management, data dictionary items.
System management plays a very important role in software development. Whether the software can run normally or not is decided here. If this part is not done, the software will not run normally; at the same time, this is the first pass for software security. Without this part of the software, there is no security to talk about. Due to the importance of status, this part has always been the focus of software development, and it is also the most stable and mature part of software development. The reason for saying this is that every set of software has this part from the beginning of software development. Some of the functions are basically the same and the maturity is basically the same.
User Management
The ultimate purpose of any software is to provide people to use, so the personnel organization is the foundation of any software. We are here to extract personnel and institutions separately as a system to maintain. A variety of personnel are involved in this module, each of which belongs to a different system. As the data of the system is open to the outside world, the browsing right is not open to the maintenance right, so certain permissions and terminals are required to maintain the data. In this plan, the Breeding Animal Improvement Center has the right to modify the collected data and all the farms under its jurisdiction have no right to modify, and only have the right to query and browse, to ensure the completeness and accuracy of the data.
Role management
Based on RABC’s three-level authority management, the most important link is role management. The establishment of different roles and the assignment of permissions based on the roles greatly improves the flexibility and work intensity of authority assignment, and also meets the three-level permissions of the system. manage.
authority management
Resource management is responsible for maintaining the various resources of the system that require authorization processing, including various operations such as addition, modification, deletion, and viewing, as well as the data filtering function based on row level and the data filtering function based on page components.
Module management
Dynamic management of all modules in the system.
Data Dictionary
Setting of some constant data used in the system
Operation log
Check the operation log in the system, and the system will record all operation logs after each user logs in to the system for tracking and querying and guaranteeing the operation safety of system data.
data backup
Data backup is a protection method adopted to ensure data security. It is a process of retaining data in a certain way so that it can be reused in the event of system damage or other specific circumstances.
Data backup is an important part of the storage field, and its status and role in the storage system cannot be ignored. For a complete IT system, backup work is an essential part of it. Its significance is not only to prevent the destruction of accidents, but also the best way to preserve and archive historical data. In other words, even if the system works normally without any data loss or damage, the backup work is still of great significance-it provides us with the possibility of historical data query, statistics and analysis, and important information archiving and preservation.
Mobile handheld PDA client system
Breeding module
When the staff is doing breeding work, they use the handheld PDA to scan the ear tags of the rams and ewes. The breeding confirmation message pops up in the client system. After the staff clicks on the confirmation, the breeding information is uploaded to the data center.
Feeding module
After feeding a sheep house each time, the staff scans the building label at the door of the sheep house through the handheld PDA, or directly selects the number of the sheep house on the interface, and clicks confirm after selecting the food information to be fed.
Epidemic prevention module
After every time the staff has done epidemic prevention on the sheep in a sheep shed, they scan the floor label at the entrance of the sheep shed through the handheld PDA, or directly manually select the number of the sheep shed on the interface, select the drug information used for epidemic prevention and click Confirm That’s it. If a complete sheep shed is not done for one epidemic prevention, then the user can check the number of the sheep stall that has been quarantined downstairs in the system interface.
Quarantine module
Pigs, cattle, and sheep need to be quarantined before processing, and the quarantine personnel will complete the quarantine process after scanning with the handheld device and clicking the confirm button.
Data query module
This module is used to query various information, by scanning ear tags or manually entering the number to query various information related to sheep, such as breeding information, feeding information, epidemic prevention information, and so on.
4. List of main RFID equipment

1. Product name:
902~928MHz UHF RFID ear tags for pigs, cattle and sheep
2. Product model:
ETAG-T45
3. Product features:
1. The farthest reading distance can reach 5m
2. Waterproof, sun-proof, anti-soaking, in line with IP67 standard
Four, technical indicators
|
working frequency
|
915MHz
|
|
Protocol
|
ISO18000-6C
|
|
Chip type
|
H3
|
|
Reading and writing category
|
Read and write (512bit)
|
|
effective distance
|
1-5m
|
|
Packaging materials
|
TPU
|
|
Data preservation
|
10 years
|
|
Number of erasing and writing
|
100,000 times
|
|
Size
|
59.8mm*59mm
|
|
Operating temperature
|
-40~+85℃
|
|
stored temperature
|
-30~+50℃
|
|
Working humidity
|
≤90%
|

1. Product name:
902~928MHz UHF Rugged Handheld RFID Reader
2. Product model:
ETAG-R47
3. Product features:
1. Support one-dimensional, two-dimensional barcode, camera, Bluetooth, WIFI, GPS, etc.
2. Support multiple data interfaces of USB and RS232
3. Provide dynamic link library (DLL) and demo software source code, support secondary development
Four, technical indicators
|
working frequency
|
902~928MHz
|
|
processor
|
SAMSUNG Cortex-A8(1GHz)
|
|
Memory Capacity
|
ROM: 512MB RAM: 512MB (maximum expansion 32GB)
|
|
operating system
|
WIN CE6.0
|
|
The standard configuration
|
GPRS, WIFI, Bluetooth 2.1, one-dimensional code
|
|
Optional function
|
GPS, 5 million camera, QR code
|
|
Display screen
|
3.4 inch color touch screen
|
|
size
|
190*75*30mm
|
|
weight
|
490g (including battery)
|
|
keyboard
|
Number & letter keys, navigation keys, scan keys, side keys, handwriting
|
|
Call function
|
Built-in speaker
|
|
Battery
|
3.7V 3400mAh lithium battery
|
|
Communication Interface
|
USB, RS232
|
|
Protocol
|
ISO18000-6B, ISO18000-6C
|
|
Industrial grade
|
IP65
|
|
Working distance
|
3~5m
|
|
Storage temperature
|
-20° C ~ 65° C
|
|
Operating temperature
|
-10° C ~ 50° C
|
|
Working humidity
|
5% ~ 95%
|

1. Product name:
902~928MHz UHF Split RFID Reader
2. Product model:
ETAG-R43
3. Product features:
1. Work in a wide-spectrum frequency hopping (FHSS) or fixed frequency transmission mode
2. Support multiple working modes such as active, response, trigger, etc.
3. Provide dynamic link library (DLL) and demo software source code, support secondary development
Four, technical indicators
|
working frequency
|
902~928MHz
|
|
Protocol
|
ISO18000-6B, ISO18000-6C
|
|
Operating Voltage
|
9V
|
|
Working current
|
600mA
|
|
effective distance
|
5~8m
|
|
Output Power
|
30dBm (software adjustable)
|
|
Antenna connection
|
4 external TNC interfaces
|
|
Antenna form
|
Circular polarization, linear polarization
|
|
Communication Interface
|
RS232, RJ45, GPIO; RS485 (optional)
|
|
shell material
|
aluminum
|
|
show
|
LED, buzzer
|
|
size
|
230*170*40mm
|
|
net weight
|
1300g
|
|
Operating temperature
|
-10~+60℃
|
|
stored temperature
|
-25~+80℃
|
|
Relative humidity
|
5%~95% (no condensation)
|

1. Product name:
902~928MHz UHF 8dbi Circular Polarization RFID Antenna
2. Product model:
ETAG-A02
3. Product features:
1. Polarization method: circular polarization
2. 8dBi high gain design
Four, technical indicators
|
working frequency
|
902~928MHz
|
|
Polarization mode
|
Circular polarization
|
|
Antenna gain
|
8 dBi
|
|
Voltage standing wave ratio
|
≤1.4
|
|
Front-to-back ratio
|
≥20 dB
|
|
Half power angle
|
Hor: 63°, Ver: 56°
|
|
power
|
10 W
|
|
impedance
|
50 Ω
|
|
Connector
|
N-female
|
|
Lightning protection
|
DC grounding
|
|
Effective wind area
|
≤0.2 m²
|
|
Maximum wind resistance
|
60m/s
|
|
Radiation material
|
aluminum
|
|
Radome material
|
ABS (white)
|
|
size
|
260mm * 260mm * 45mm
|
|
weight
|
1.2kg
|
|
Operating temperature
|
-30℃~ 70℃
|
|
storage temperature
|
-40℃~85℃
|
|
Relative humidity
|
5%~95% (no condensation)
|

1. Product name:
902~928MHz UHF USB Interface RFID Reader
2. Product model:
ETAG-R45
3. Product features:
1. Work in a wide-spectrum frequency hopping (FHSS) or fixed frequency transmission mode
2. Output power: maximum 10dBm (adjustable)
3. The USB1.1 interface takes power without an external power supply
4. Provide dynamic link library (DLL) and demo software source code, support secondary development
Four, technical indicators
|
working frequency
|
902~928MHz
|
|
Protocol
|
ISO18000-6B, ISO18000-6C
|
|
Operating Voltage
|
5V
|
|
Working current
|
90mA
|
|
effective distance
|
10~30cm
|
|
Output Power
|
10dBm (software adjustable)
|
|
show
|
LED, buzzer
|
|
Communication Interface
|
USB
|
|
shell material
|
ABS reinforced plastic
|
|
size
|
105*70*10mm
|
|
net weight
|
80g
|
|
Operating temperature
|
-10~+60℃
|
|
stored temperature
|
-25~+80℃
|
|
Relative humidity
|
5%~95% (no condensation)
|
[ad_2]



