NFC smart consumer solutions
[ad_1]
1. The status quo of NFC smart consumption
In fact, smart consumption has entered our lives. Public transportation and subways provide credit card services, and campus canteens provide credit card consumption. However, smart consumption is still not applied in large areas and multiple fields. Let’s take a look.NFCThe status quo of smart consumption.
1. Inconveniences encountered in life
(1) When I bought a bottle of water, chewing gum, and snacks in the supermarket, I found out when I took out my wallet that there was only one piece of 100 yuan without the scattered money. The supermarket waiter spent a lot of effort to find the scattered money, and the result was a lot of waste. time.
(2) When eating lunch at KFC or McDonald’s, the super value lunch costs 15.6 yuan. There is already some distance in the line behind, and at this time, it is found that you have no money to spend, so you get 100 yuan to find a break. It’s inconvenient to hold a lot of change and find a seat with a fast food plate.
2. The Mifare card has been cracked
(1) Hacker attack: Henryk Plotz, a German scholar, and Karsten Nohl, a Ph.D. student at the University of Virginia, demonstrated how to crack Mifare cards. They claim to be able to crack the Mifare Classic key within a few minutes using an ordinary computer.
(2) Domestic government response: In early 2009, some domestic agencies and units issued a red-headed document-“Notice on Doing a Good Job in Dealing with Serious Security Vulnerabilities in Certain IC Cards”, requesting risk assessment of access control systems using M1 cards, and Carry out rectification. In the future, the new IC card system should adopt my country’s independent innovation of IC card technology in principle, and the password scheme of the IC card system must be approved by the national password authority.
3. The bank card flash payment is not friendly
Payment security and portability are always mutually reinforcing. The more portable the product is, there are often greater security risks. The safer the system is, the more troublesome it is to use.
Similar to all daily non-cash consumption and payment, the services that integrate bank cards, bus cards, and shopping cards will indeed make our daily lives more convenient and faster. Bank’s systems and products have high security performance for users. Will it affect the portability of people’s use? Imagine buying a bottle of water, chewing gum, small snacks, in order to facilitate the removal of the bank card from the wallet and swipe the card Quick pass to complete the payment. But what if the card is lost? Will people get used to putting their bank cards in their wallets? So the flash payment function is not enough in this kind of intimacy.
2. Introduction of NFC Consumer System
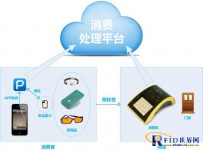
1. Work flow chart

2. NFC consumer system workflow
(1) CPU label: Under the premise of ensuring safety by the principle of CPU encryption, the label should be made as small and thin as possible. The item can be 20mm×11mm×0.78mm. The purpose is to make the CPU label an accessory carried by consumers, which can be made in Wristbands, mobile phone cases, glasses and other products that are convenient for consumers to carry;
(2) APP software: install a simple and convenient APP software in the consumer’s mobile phone, and its APP account is bound to the CPU tag, and it is connected to the consumer processing platform through the GPRS function of the mobile phone;
(3) Consumer machine: The merchant uses a consumer machine that can read and write CPU tags, and the consumer machine is connected to the consumer processing platform;
(4) Access control: The original access control system swipe card to open the door, without changing the system, the CPU tag can replace the original access control card, so that the user does not need to bring multiple cards;
(5) Consumption processing platform: All data processing is realized through the processing platform, which fully guarantees the safety of consumption.
3. System advantages
1. Security
The core of the CPU card is the Card Operating System (COS), which controls the exchange of information between the CPU card and the outside world, manages the memory in the CPU card, and completes various command processing internally. Therefore, it is not the password that participates in the communication exchange, but the encrypted data. The CPU card mainly realizes the operation of different types of application files in the card through COS. Each application is independent of each other and controlled by its own key management system, so that each application of each card has its own independent key. , And the key of each application is 128 bits. Therefore, the security of the CPU card is the highest so far. At the same time, due to the hardware coordinator and COS management, the data information exchange process is very stable, there is no critical state loss of data, and the reliability is very high.
CPU label like a computer
2. Portability
At present, the minimum label size of Zhongzhi Internet of Things projects is 20mm×11mm×0.78mm, which is convenient for “transplantation” in most products.
3. Kindness
If the tag is lost or stolen, such as the wristband, phone case, or glasses, the user only needs to open the APP on the phone and cancel the link between the account and the tag through the APP, which is very convenient.
[ad_2]




