Design Scheme of Library Card Management System
[ad_1]
1 System design ideas and principles
The design idea of the library’s IC card management system is to gradually replace the bar code management with a library’s IC card management, using the IC card as the identity certificate of all library staff and readers (including teachers and students), and passing the IC card Reading and writing equipment, collecting the use of library resources by all personnel, making full use of computer network technology and database technology to realize the integration of library information, improve the overall management level of the library, realize scientific and standardized management, and serve the library Development decision-making provides a scientific basis. The system is designed based on the following principles:
(1) Advancement: The system adopts advanced Client/Server database management and supports various hardware platforms. Both in terms of system function and system practicability, the system is at the leading level in the same industry. At the same time, the system is guaranteed to be advanced in the next few years.
(2) The system is designed to be flexible, with strong openness, shrinkage, and expandability. According to the actual application requirements of the library, the overall design is implemented in stages to realize the principle of “urgent use” and at the same time provide a good interface for future expansion , Flexible and changeable in hardware selection.
(3) Standardized management, which is convenient to improve the efficiency of system management. According to the specifications of the all-in-one card information management system, a complete set of IC card computer management methods are developed. The software adopts a modular structure, which can easily construct customized management modules according to different management requirements.
(4) Simple and friendly user interface, easy to learn and operate, strong practicability The software is partly designed based on WINDOWS, with all the advantages of graphical operation, which is convenient for beginners to master the operation of the entire system in a short time while taking into account the practicality of the system The design adopts various shortcuts that are easy to operate.
(5) Provide a wealth of decision-making and management information data to facilitate the improvement of the library’s scientific management system. It is necessary not only to support the daily management of the library, but also to consider providing leaders with corresponding decision-making data on this basis in order to improve the library’s scientific management system. Management level and competitiveness.
(6) High-performance safety and reliability to ensure the normal operation of the library
The library all-in-one card management system is a long-running system and involves the issue of money. Therefore, the reliability and safety of the system are particularly important. The system should have strict security and confidentiality functions, and at the same time provide functions such as authority control, password protection, and system data security backup.
2 Technical route of the system
The key to realizing one card with multiple functions lies in the design of the card, the data sharing of each system, and the security of the system.
(1) Card design: It mainly includes the card selection (cost and security) and the design of the data structure in the card.
① Data protection: logical encryption, with password verification function, improve the security of the card;
② Storage capacity: more than 256 bytes of capacity, realizing one card for multiple purposes.
(2) To satisfy one card with multiple functions. The data structure in the card is divided into: ① the card header design of the library card issuing system; ② the book management record area; ⑧ the transaction record area of the library charge management.
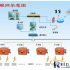
(3) In order to ensure the security of the card, you can choose a CPU card. This card is often called a smart card (SMART CARD). This card not only has EEPROM and other memory, but also has a CPU and its operating system and encryption algorithms (DEs or RSA). It has two major functions: processing and storage, and high security performance. Figure 1 shows the module structure diagram of the smart card-related system.

Figure 1 Cross-block structure diagram of smart card related system
3 System structure and main functional modules
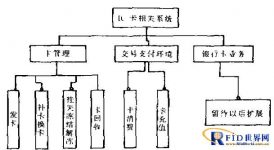
This system mainly includes central database, access control management system, electronic reading room management system, charging system and other parts. The IC card read-write device is directly connected to the terminal host, and then the terminal host will be connected to the system server through the library’s existing network system.
The main management tasks of the entire IC card all-in-one card system are completed by application software. The IC card mainly stores identity information and some cached information (such as the latest consumer information, etc.) used to ensure the reliability of the system. The main information and data will be directly stored in In the system server database, the unified management of the system is effectively realized. The main task of the local host is to read the user identity information from the IC card reader, and then according to the actual requirements of the specific subsystem, the user identity information and other related information are stored in the background database. The structure of the entire system is shown in Figure 2. .
3.1 Management module of card issuance center
Complete the user’s information storage, initialize the card, accept the user’s personal information inquiries, complete the user’s deposit process on the card, modify the user’s personal information, and have the functions of reporting loss, unlocking and re-applying for the card. Can log off users, allow the establishment of blacklists, system settings, and system maintenance.

Figure 2 System structure diagram
3.2 Access control management module
“The access control subsystem is the library’s security barrier. Users entering the library must first swipe their cards to register, and the access control management subsystem performs a legality check. When the check is legal, the system stores the user’s swipe card information in the database and sends The access control device sends a control signal to open the security door to allow the legal person to pass; and when the check is illegal, the security door is closed to deny the illegal person to pass. The library access control system mainly determines whether it has access through the identity verification of readers and staff The authority of the library. At the same time, the relevant information of the personnel entering the library will be transmitted to the server through the network to be recorded and stored in the library, so as to facilitate the staff attendance and flow statistics.
3.3 Electronic reading room and reader consumption management module
The main task of the electronic reading room management system is to monitor the user’s computer in the electronic reading room, realize the IC card verification and information recording of the readers who enter the reading room, and implement the billing of the user’s computer on the computer, and pass the corresponding consumption information to the background database. In case of special circumstances, it should also be able to retrieve the reader’s detailed information from the main computer’s database to facilitate the handling of on-site situations and realize the “blacklist” restriction function. By charging the electronic wallet in the IC card, the electronic reading room is implemented. Paid services for unmanned photocopiers and other equipment. The charging method can be pre-set as:
(1) Machine-time billing method: accumulatively charged by time}
(2) Traffic accounting method: accumulatively charged according to the amount;
(3) Fixed deduction method: a fixed deduction for a certain amount of money once on the computer.
After the IC card is inserted into the toll collection machine and charged, the amount in the Ic card electronic wallet is deducted. Through the IC card computer charging management system, library materials can be inquired and browsed online.
3.4 Book management module
3.4.1 Book borrowing management: Write the number of the book borrowed by the borrower and the time of borrowing into the Ic card at the same time, and cancel it when returning the book. If the book is overdue or if the book is damaged or lost, the compensation will be deducted from the IC card and the compensation information will be written into the IC card.
3.4.2 Reading room management: readers insert the library card into the reader before entering the reading room, and can enter after obtaining the right to enter the reading room. The reader automatically records the information and time of the personnel entering the reading room, prompts the management staff when the reading room is full, and performs statistics on the reading situation.
3.5 Attendance management module
The computer reads the employee’s identification code through the read-write device to determine when the employee goes to work and when he leaves work, and sends the data to the database.
3.6 Communication management module
Adopt RS-485 communication conforming to international industry standards to realize data collection by the system management server and implement hierarchical control management
3.7 Shared database management
The database system is the core of complex data processing. It determines the data manipulation capability in terms of operating time, space and complexity. The Oracle database is a coordination server and an open DBMS (database management system) used to support task-determining applications. It can be completely transplanted to more than 80 different hardware and operating system platforms. This portability allows free choice of database server platform to meet current and future needs without affecting existing applications. In addition, Oracle also provides scalable high performance for a large number of users on all hardware structures. As the representative of large-scale databases in the world, Oracle database has great data management capabilities. It will provide a solid foundation for the safety and reliability of information, reduce the burden of many daily database maintenance tasks, and support the use of c, C++, Delphi, etc. Language development.
[ad_2]