RFID city electric bicycle bicycle anti-theft and anti-lost intelligent management system
[ad_1]
1. System overview
1.1 Project background
While electric vehicles and bicycles bring convenience to people, they also cause major headaches for owners-frequent theft of vehicles. Electric vehicles and bicycles are parked in the parking lot or downstairs. The owners do not have the conditions to monitor them all the time, leaving a lot of room for criminals to commit crimes.
Electric vehicles and bicycles are the main means of transportation for many citizens, but their frequent theft not only brings trouble to themselves, but also puts pressure on police work. In order to solve this livelihood problem, relevant departments of the county public security bureau plan to build anti-theft systems for electric vehicles and bicycles. We have fully communicated with public security departments, vehicle owners and insurance companies, and made this plan based on the principles of advanced, reliable, durable, and economical.
With fast processing speed, accurate data, and strong automatic identification capabilitiesRFIDWith the increasing maturity of technology, combined with this technology, we can install “identity cards” on bicycles. In the past, the loss of community or school bicycles was mainly due to the unclear number of bicycles and the unclear identity of the owners. With the RFID bicycle anti-theft management system, the bicycle can be managed scientifically and effectively.
Hongyan bicycle anti-theft management system has significant advantages in at least the following two aspects:
⒈Improve manageability: dual-card association recognition, vehicle information system management, and real-name information system, greatly improving the manageability of bicycles.
⒉Reduce management costs: higher efficiency and more controllable bicycle anti-theft measures greatly reduce the probability of bicycle theft and improve the overall security level.
3. Combined with the fixed monitoring station, the key area of lost bicycles can be alarmed and found and tracked and located.
1.2 Business model:
The project includes the following relationships: Public Security Bureau, vehicle owners, enterprises and insurance companies.
Public Security Bureau: The traffic management department is compulsory to apply for license plates for all electric vehicles and other non-motor vehicles. Only vehicles with license plates and RFID identification cards are allowed to go on the road. At the same time, traffic police patrol handhelds at any time to check vehicle cards and vehicles without cards. detain;
Vehicle owner: The vehicle owner only needs the purchase invoice and relevant documents to go to the traffic police department of the Public Security Bureau to register and RFID identification card, and pay a certain fee as the license fee and insurance premium, and enjoy commercial insurance;
Enterprise: The company here is the manufacturer that provides this electric vehicle anti-theft intelligent management system. The company provides all positioning equipment, RFID identification cards and technical support for system operation, and maintains the normal operation of the system at any time;
Insurance company: Our system introduces a commercial insurance model, and is under the supervision of the traffic police department of the Public Security Bureau, allowing car owners to use a small amount of money to insure;
All owners of electric vehicles and other non-motor vehicles must be registered in the public security department and receive RFID identification cards. The owners need to pay less than 100 yuan in cost and commercial insurance; the system is established in the security network of the Public Security Bureau. Assist the public security department to investigate various illegal cases. At the same time, when the owner’s vehicle is lost, he can enjoy commercial insurance, and the insurance company will compensate the owner’s loss; traffic law enforcement officers have RFID handheld devices on the street to scan non-motor vehicles on the street at any time. Motor vehicles must go through the relevant procedures at the traffic police department of the public security at the specified place and time, otherwise the traffic police will detain the vehicle;
This is a happy ending. The car owners’ vehicle safety is guaranteed, the insurance company has played its role, the public security department has greatly improved the work efficiency, and the company has brought convenience to the society.
2. Scheme design
2.1 System design principles
Reliability: The bicycle anti-theft management system adopts electronic coding corresponding identification technology, which is safe and reliable, and eliminates the possibility of false alarms and non-reports.
Practicability: The system is simple and easy to implement, and has strong operability; the electronic label is small and easy to carry, which reduces the impact on the owner’s daily life; the flashing light and the alarm system are combined, and the visual management interface is convenient for managers to monitor in real time. The probability of theft is reduced to a minimum.
2.2 The basic process of the system

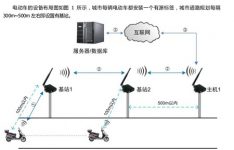
Figure 1 Application layout

Figure 2 System topology diagram
The main operation process of the entire bicycle anti-theft system is shown in the figure above: After the electronic tag enters the electromagnetic field of the antenna, it receives the radio frequency signal from the reader, analyzes and executes the instruction sent by the tag with the energy obtained by the induced current, and then backscatters Product information stored in the tag chip; after the reader reads and decodes the information, it is sent to the central information system (upper computer) for relevant data processing.
Tracking of lost vehicles:
Method 1: After the owner loses the vehicle, report to the Vehicle Security Office. After the security office reviews the information, register the lost vehicle information to the data center. The lost vehicle information in the data center (-—alarm storage) can be queried by the portable terminal and the terminal device of the card issuing outlet , When the patrolman with a portable terminal is patrolling the block, when it recognizes the information of the lost vehicle, it will prompt to find the lost vehicle.
Method 2: An abnormal vehicle is detected at a fixed monitoring station (when there is only a vehicle card but no personnel card, the data center will automatically count the lost vehicle module-judgment storage), and then the data center can query the subsequent identified location information of the lost vehicle .
Method 3: When a patrolman with a portable terminal is patrolling the block, and when an abnormal vehicle is identified (only a vehicle card but no personnel card), a prompt appears, so as to confirm on the spot whether the vehicle is a stolen vehicle.
Method 4: When the anti-theft office obtains the data center to collect and analyze the abnormal vehicle information (determination of storage, alarm storage) in real time, the anti-theft office personnel instruct the relevant area to hold the portable terminal police to go to the latest identification area, and guide the vehicle supervision by referring to the real-time video surveillance image check.
If tracking is required in the field, the location information can be obtained by sending a read command through the management center.
>See the next page for the flow chart of stolen vehicle tracking
For detailed function description, please refer to the next section.
2.3 Principles of System Management
By installing a management identification label in each vehicle (key controller), the smart chip in the label has a globally unique identification code and this code cannot be rewritten. Number, purchase time, card application time, battery information, car owner information, etc.) are entered in our software system and stored in the database. At the same time, each driver is also issued an identification label (the label has a different style but the function is the same as the vehicle identification label, and it also has corresponding identification codes and information), and the system binds the two sets of codes to each other.

Figure 3 Information binding diagram

Figure 4 Flow chart of looting vehicle tracking
When the system is working, the system station considers the vehicle to be a legitimate vehicle only when it reads two identification tags that are bound to each other at the same time. Capture photos for evidence.
2.4 System architecture

Figure 5 System structure diagram
This system is composed of several parts such as data acquisition system, software system, network system and alarm system.
The system is a modular design, which can be flexibly adjusted according to actual application requirements. It is adaptable, extensible and easy to use. Not only can the car be managed, but also personnel and vehicles can be managed after adding the corresponding software modules and hardware devices.
Three, function description
RFID system management for electric vehicles and bicycles is to install an active RFID electronic tag with vehicle information on each vehicle (vehicle card), and at the same time, the owner of the vehicle has a tag —– -Personnel card, and associate the two tags. Secondly, install RFID readers and antennas at the fixed monitoring station, and install the industrial control touch screen system with management software, which can input the relevant information of each vehicle, such as vehicle photos and owner information Wait.
The core issue of the management of electric vehicles, bicycles and other vehicles is the identification of identity. Attach RFID electronic tags to vehicles, they have the function of being identified, and the information recorded in the RFID electronic tags can be directly read through a dedicated reader, and the public security organs can use scientific and technological means to prevent theft of vehicles. Effective management is conducive to safeguarding the interests of car owners.
When the owner and the vehicle enter the reading range of the RFID antenna, the system automatically detects. When the tags of people and objects are detected at the same time, the green light on the control screen will be on, and the name of the person and object will be displayed at the same time;
When only the personnel card tag is detected, the yellow light is on and the name of the person is displayed on the screen; when only the vehicle card is detected, the red light is on and the buzzer is activated to alarm, and the owner’s name and vehicle photo are displayed on the screen (the owner’s photo can also be displayed). Contact information and photos);
When it is confirmed that it is a stolen vehicle, it can be captured in time, and the owner, 110 and other units can be notified according to different security levels. The specific function realization is shown in Figure 4:

Figure 6 Function diagram of RFID bicycle anti-theft management system

Figure 7 Installation of fixed monitoring stations at urban road junctions
[ad_2]



