Suzhou Luhe RFID is applied to the monitoring system of personnel and vehicles entering and exiting the factory
[ad_1]
1. Company profile
Suzhou LOHO Electronic Technology Co., Ltd. is a high-tech enterprise with active radio frequency identification technology (RFID), wireless sensing technology, wireless transmission technology, etc. as its core, providing professional 2.45G Active RFID products and IoT transmission solutions. The company integrates scientific research and development, engineering design, product manufacturing, system integration and engineering services to provide customers with professional solutions.
As a provider of active RFID products, the company has built and implemented a number of successful projects in the fields of mine tunnels, smart parking lots, power temperature measurement, and video surveillance. From a people-oriented perspective, the company adheres to the starting point of changing lives with technology, creating a series of intelligent management systems that combine software and hardware to make people’s work and life more convenient, comfortable and efficient.
The company has a senior and excellent RFID industry elite team with rich practical experience in product development, operation management, marketing and other fields. At present, Luhe Technology has hundreds of industry users at home and abroad, and its products have entered key RFID application markets such as monitoring, anti-counterfeiting, power, logistics and transportation.
The company has participated in the research and implementation of a number of major Internet of Things and RFID application projects, and the technology has been widely used in personnel management, vehicle and ship management, logistics management, asset management and other fields.
With the rapid development of the Internet of Things industry today, Luhe Technology has a broad space for development, and the technology-centric development method enables Luhe Technology to have the potential for sustainable development.
Luhe Technology is a dark horse in the era of the Internet of Things. Based on the domestic and global perspective, Luhe Technology is committed to opening your smart life.
Company philosophy:
Our creed is: customer-oriented, quality first; technology-based, talent-oriented. Serving customers is the only reason for Mulan’s existence, and customer needs are the driving force behind Mulan’s development.
With good quality, good service and low operating costs, we give priority to satisfying customer needs and enhancing customer competitiveness and profitability. Continuously manage changes, achieve efficient process-based operations, and ensure end-to-end high-quality delivery. To develop together with friends and businessmen is not only a competitor but also a partner, to jointly create a good living space and share the benefits of the value chain.
2. System background and overview
2.1 System background
In recent years, some flammable and explosive plant areas are prone to safety accidents such as fires and explosions. Although there are obvious warning signs in the factory, people often ignore these warnings and still go their own way and ignore them. Some places in the factory are not allowed to enter and stay at will, but people have time to be curious and sneak in when people are away. There are also some management and responsible personnel who cannot go to work and make inspections on time. Bring hidden dangers to safety accidents. How to strengthen the preventive measures for safe production, how to correctly handle the relationship between safety and production, safety and benefit, how to accurately and real-time perform the safety inspection function of the flammable and explosive industry, and ensure the efficient operation of emergency rescue and safety rescue, is placed in the country In front of the competent departments and leaders at all levels. At the same time, how to change the current flammable and explosive enterprise’s backward management mode of on-site workers, and how to realize management modernization and informatization have also become the concerns of all flammable and explosive enterprises. We believe that it is imperative to establish informatization and intelligentization with the main objectives of disaster prevention, accident rescue, and electronic information management. To this end, we have introduced a location system for factory personnel and vehicles.
2.2 System overview
In terms of factory and vehicle attendance, the company previously used ordinary IC/ID cards for attendance, and to a certain extent, it also realized the attendance system. However, when the company has a large number of people, employees line up to swipe their cards every day to and from get off work, and they have to go to the card. Swiping the card in front of the machine wasted a lot of time. And our long-distance recognition system is to solve this problem; in terms of positioning, this system is a continuation of the factory’s traditional management methods, and it is very convenient to find out the movement trajectory and stay time of someone within the recognition range of the factory’s card reader .
Three, system design principles
3.1 Reasonable system layout
In the program design, the rationality of the system architecture and equipment selection is particularly important. For example, there are many and scattered monitoring base stations for plant personnel and vehicle positioning systems. If the transmission system is all wired, not only the construction is difficult, the structure is inflexible, but also the later maintenance is troublesome. If all are wireless, the cost of testing is higher. If the wired + wireless method is adopted, that is, the wired method is adopted for the main line that is convenient for construction, and the branch line that is not suitable for construction is adopted for wireless transmission, which is a more reasonable choice.
3.2 Meet the relevant industry standards of the country and all levels of management
The safety monitoring system complies with relevant technical standards, and the equipment has been uniformly planned to meet the national safety requirements for flammable and explosive areas, and can meet the needs of comprehensive management of large factories.
3.3 Use existing communication facilities
The construction of security monitoring fully considers the use of existing communication facilities and the policy of not repeating construction. For the existing communication networks in the factory, such as local area networks, wireless networks are fully utilized, and part of the management and maintenance work is handed over to professional network administrators, which saves costs.
3.4 Interface issues with other information systems
The plant personnel, vehicle entry and exit location management system platform retains the data interface with other information systems: such as the enterprise’s ERP information management system, etc., which can ensure that other systems are successfully connected to the system platform, open the corresponding application system, and retrieve the monitoring interface and corresponding data .
3.5 The principle of ease of maintenance
This is for the actual needs of the system in use. After the implementation of the system project is completed and delivered to use, it should be convenient for all kinds of daily maintenance work, and can easily carry out software reconfiguration, system self-check and recovery, hardware spare parts replacement and software system upgrade.
Fourth, the system design plan
This system is divided into two parts: attendance and positioning, we will introduce attendance and positioning separately
4.1 Time Attendance System
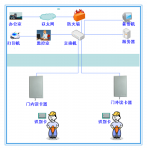
(1) Schematic diagram:

(2) Working principle:
Workers and vehicles carry long-distance identification cards, which can be identified about 10 meters away from the card reader, and the card reader sends the received identification card information to the server through the network. The software records when the workers enter the factory and when they leave the factory. So as to facilitate the effective realization of the attendance function.
4.2 Positioning management system
A schematic diagram

Schematic diagram of plant B

4.2 System working principle
(1) The principle of positioning in a small area in a workshop or room
First, install a wake-up card reader at the entrance of each room or workshop, and install one or two wake-up card readers at the entrance of the stairs. The wake-up source card reader does not need to be connected to the monitoring center computer. The fixed card reader is fixed at the stairway or away from the door within the range that the card reader can sense to wake up. The dual-frequency label card is fixed on the worker’s helmet. In order not to hinder the work, the label is fixed on the top of the helmet.
When the staff enters the room or arrives at the stairs, they are activated by the nearest wake-up card reader, and immediately send 2.4G active signal (the signal includes the card number and the address of the activated card reader). This signal is received by a card reader installed within 50 meters, and the card reader uploads the received signal and its own number to the monitoring center through the network. The computer can immediately determine the current status of a specific person (location, stay time in the area, etc.) based on specific information (corresponding to the installation location of the card reader, on-site conditions, historical status and time of the tag). The administrator can also select a time period (a certain day or a certain day) and a report type (attendance report, entry and exit record report of a specific area, personnel history track tracking report, warning report for violation of predetermined security policies) to obtain The required report. In addition, once an accident occurs in the factory, the personnel at the accident site can be found immediately based on the personnel distribution information in the computer, and then special detectors can be used to further determine the location of the personnel at the accident site to help rescuers rescue the trapped people accurately and quickly . The handling of temporary visitors is basically the same as that of fixed personnel, except that additional information is added to facilitate the cancellation and re-authorization of the electronic tag.
(2) Large-scale positioning method in a wide area
Place several card readers at various intersections, main passages and key monitoring large-scale areas in the factory. The specific number and installation location are determined according to the actual working conditions on site and the functional requirements to be realized, and they are controlled through the wired network The computers in the center are connected.
When a worker enters and passes through the factory area, as long as he passes through or approaches any card reader placed in the factory area, the card reader will immediately sense the corresponding electronic tag number (dual-frequency tag is transmitted in two state signals, when When the card reader is not awakened, it can also send a signal, but it is not the same as the signal state after being awakened), the reader’s own number and time are uploaded to the computer in the monitoring center, and the computer can immediately follow the specific information (corresponding The installation location of the card reader, the site situation, the historical status of the tag and the time) determine the current status of a specific person (location, staying time in the area). The administrator can also select a time period (a certain day or a certain day) and a report type (attendance report, entry and exit record report of a specific area, personnel history track tracking report, warning report for violation of predetermined security policies) to obtain The required report. In addition, once an accident occurs in the factory, the personnel at the accident site can be found immediately based on the personnel distribution information in the computer, and then special detectors can be used to further determine the location of the personnel at the accident site to help rescuers rescue the trapped people accurately and quickly . The handling of temporary visitors is basically the same as that of fixed personnel, except that additional information is added to facilitate the cancellation and re-authorization of the electronic tag.
Features and advantages of five systems
5.1 System features
Contactless
The electronic tag and the card reader are used for wireless communication, and the maximum identification distance can reach 80m (adjustable distance). Therefore, personnel only need to carry the electronic tag and pass near the card reader without getting off the car and approaching the reader. Card reader swipe.
Penetrability
The wireless signal can penetrate obstacles such as paper, clothes, plastic, etc., so even if the electronic tag is not in the visible range of the card reader (such as in a clothes pocket, in a car), it can work normally.
safety
The data of the electronic tag is sent to the card reader in the form of an electronic signal, so only a specific device can receive the data, and only the authorized administrator can view the data, ensuring the security of the data.
High-speed recognition
The card reader recognizes electronic tags at a very fast speed (200 can be recognized at the same time), so the recognition efficiency is very high for the situation where the moving speed is very fast or there are many people passing by at the same time.
High accuracy
Basically, a 100% recognition rate can be guaranteed.
Low power consumption
The electronic tag adopts ultra-low power consumption design, and only its built-in battery can maintain normal operation for 3 or 5 years without frequent battery replacement. The card reader is also designed with low power consumption, and the peak power does not exceed 1W.
Small size and light weight
The electronic label adopts microchip and patch technology, which is small in size, light in weight, easy to carry, does not affect normal work and is easy to keep.
Anti-pollution, suitable for various environmental conditions
The electronic label adopts a plastic shell, which is insensitive to common corrosives such as water, paint, stickers, chemicals, and electromagnetic interference. It is resistant to low and high temperatures, adapts to various working environments, and does not cause any pollution to the environment.
5.2 System advantages
Highly automated
The system can automatically monitor the time, location and other information of personnel or vehicles passing through the monitoring point in the factory, analyze and upload it to the network server and make corresponding actions. The entire process is fully automated without human intervention.
Easy to operate
The administrator only needs to enter the information of the personnel or the vehicle and the number of the electronic tag into the system to start using it without other operations. The personnel holding the electronic tag only need to carry the electronic tag without the need to swipe the card or register, which is completely unnecessary. It affects normal work and is very convenient to use.
Without any client software, the administrator only needs to log in to the website with a browser to remotely query information and perform management operations.
efficient
With the help of computer information processing technology, the system can register a large number of people, vehicles, and other information in a short period of time. The administrator can also specify conditions to obtain a variety of complete report materials, display and print them, for the top management Provide a basis for managers’ inquiries and decisions. Compared with the previous manual registration and statistical methods, the accuracy, reliability and efficiency have been greatly improved.
Information is timely and accurate
The information of the system is updated in real time and can be guaranteed to be accurate. Users can get the latest information as long as they log on to the website.
The system is stable, safe and reliable
The design of the system fully considers the stability and reliability. The card reader adopts a waterproof and explosion-proof housing, and the internal circuit is stable and reliable, and can work continuously in harsh environments. The equipment adopts wall-mounted installation, so there is no need to carry out tunnel construction on site. The entire system also uses power backup to ensure 7×24 hours of normal operation in an unstable power grid environment.
Intelligent fault detection
Including failure equipment monitoring, communication link failure monitoring and other intelligent monitoring functions, for failed equipment, only simple replacement of equipment can be restored to normal.Can query the attendance location information of employees, departments and cadres, and can output various information reports as required
Introduction of six system hardware equipment
The location management system for plant personnel and vehicles is mainly composed of electronic tags, card readers, communication facilities, computers and software.
6.1 2.4G long-distance identification card
(1) Product photos

(2) Technical parameters
Quiescent current is less than 2μA
Working current is less than 15mA
Battery life 3-5 years (lifetime 20 years)
Signal modulation method GFSK
Communication rate two-way 1024Kbit/s
Working frequency 2.45GHz
Maximum output power 0dbm
Signal modulation method GFSK
Communication rate two-way 1024Kbit/s
Working frequency 2.45GHz
Maximum output power 0dbm
Bit error rate 10-9
Shell material high temperature modified ABS plastic
Label type read-only
Appearance 90×55×6mm
Weight 25 grams
Multiple colors
Protection grade IP34
Hanging and wearing
6.22.4G long-distance card reader
(1) Product photos

(2) Technical parameters
Specifications
Interface network communication
Power supply +9V to +12VDC (MAX500mA)
Operating temperature 40℃~+80℃
Storage temperature -60℃~+80℃
Communication interface RS485 baud rate: 1200-19200, communication error detection CRC16 cyclic redundancy check
Recognition speed 200 km/h
Recognition distance 2-80M can be adjusted
Working life of 15 years
6.3 Wake up the card reader
(1) Product photos

(2) Technical parameters
Specifications
Power supply +9V to +12VDC (MAX500mA)
Operating temperature 40℃~+80℃
Storage temperature -60℃~+80℃
Recognition speed 200 km/h
Wake-up distance can be adjusted from 0.5-10 meters
Working life of 15 years
6.4 Communication facilities
Communication facilities are used to connect card readers and computers so that they can communicate with each other, and generally include various conversion devices.

Various communication equipment
6.5 Computer and software

computer
The computer is generally placed in the monitoring center to send control instructions to the card reader, accept the data uploaded by the card reader, connect to the network as a server to provide remote access services and provide an operating environment for the software.
The software adopts the B/S three-tier architecture design, the presentation layer: the interactive interface between the user and the software, the middle layer: the application server, which contains various business logic components and services, is responsible for the system business logic processing, provides interfaces for the presentation layer, and the data layer: Hardware interface components and databases. The hardware interface components communicate directly with the card reader, receive the data uploaded by the card reader for preprocessing and then send it to the business logic processing layer, receive messages from the business logic processing layer and send instructions to the card reader, The hardware interface component hides the specific implementation details and eliminates the difference between different hardware.
Seven system software function introduction
7.1 Personnel and vehicle information management
Management personnel and vehicle information, including the employee’s job number, name, department, position, shift, employee’s photo, telephone number and other information.
Corresponding vehicles have information such as vehicle internal number, license plate number, model, purpose, corresponding driver, and vehicle photo.
For temporary visitors and foreign vehicles, in addition to all the information of internal personnel and vehicles, information such as the unit, visiting time, reason, internal contact’s name, department, and departure time must also be added.
7.2 Automatic registration of personnel and vehicles entering and exiting the plant
Internal personnel and vehicles distribute long-held electronic tags, and temporary visitors and foreign vehicles distribute temporary electronic tags after registering with the administrator. When personnel and vehicles carry electronic tags into the factory area, the system will automatically record the corresponding entry and exit time.
7.3 Employee attendance
Employees can check attendance according to the entry and exit records of the factory, including work on time, off work, late, leave early, leave, absent, etc.
If necessary, similar time attendance can also be performed on vehicles or other equipment.
7.4 Real-time positioning and tracking of personnel and vehicles
Real-time positioning and tracking of people and vehicles can be performed to determine the area where the person or vehicle is currently located and the time when the person or vehicle enters the area.
7.5 Query and comparison of historical trajectories of personnel and vehicles
You can query the historical trajectory of people or vehicles in a certain period of time, and compare historical trajectories with each other or with pre-designated historical trajectories. It can be used to view a person’s activity records in the factory area, and can also be used to conduct patrol assessment of security patrol personnel.
7.6 Statistics of plant personnel and vehicles
It can count the personnel and vehicle information in the entire plant or a specific area, including the number of people, the specific name, license plate number, time and other information of the number of vehicles.
7.7 Area access control
You can query the access records of a specific area, and you can also specify the access authority of a specific person or vehicle to a specific area. For example, foreign visitors can only enter the office area and living area, but not the warehouse area and production area. Large foreign trucks can only enter the warehouse area but not the office area and living area. The hazardous chemical warehouse can only be entered by the custodian of dangerous goods. Wait. If there is a violation of the regional access control security policy, the system will issue a warning and notify the relevant personnel to stop it.
7.8 Detention time control
You can designate specific personnel or vehicles to control the access time of the entire plant and specific areas. For example, working hours are from 8 in the morning to 6 in the evening, and no one except the relevant personnel is allowed to enter the factory area at other times. Outside visitors shall not stay in the factory area for more than 2 hours without approval. The gate guard cannot leave during duty hours. Job position, etc. For violations of the detention time control security policy, the system will alarm, and the administrator can notify relevant personnel to take measures.
7.9 Specify the path
It is possible to pre-designate the path of persons or vehicles, including the sequence of waypoints, the arrival time, departure time, stay time of a certain waypoint on the way, the time interval between any two waypoints, etc. It is possible to plan the walking route of foreign vehicles after entering the factory area, or to stipulate the patrol path of safety patrol personnel.
7.10 System user management
Login to the system requires a user name and password (or the user who has not logged in is a guest by default and has the lowest authority). Different users have different permissions, including system super administrators, ordinary administrators and ordinary users. Different permissions can view different Page and perform different operations to prevent misuse or unauthorized operation.
8. System specification requirements
8.1 Applicable occasions
The plant personnel and vehicle positioning management system is widely applicable to various large-scale storage areas, power plants, petroleum, chemical, mining and other accident-prone flammable and explosive industrial plant areas and security agencies that need to control the entry and exit of personnel and vehicles.
8.2 Principles of Implementation
According to site conditions, the placement of the card reader should be based on the main paths, passages, entrances and exits, and sensitive areas to be monitored. The specific installation density should be able to cover all the critical path points (if the distance between the path points is Too far, you need to install a card reader in the middle).
8.3 Operating specifications
One person, one certificate, one vehicle, one certificate, person ID binding, vehicle ID binding, unified management
It must be ensured that each person and each vehicle entering the factory area is assigned a unique electronic tag, and the electronic tag must be authorized before distribution (including the information entry of the corresponding personnel and vehicles, the designation and activation of security policies).
Person wearing it correctly
Personnel electronic tags are generally worn on the chest or fixed on the helmet.
Correct vehicle placement

Authorization and cancellation of temporary documents
Personnel and vehicles temporarily entering the factory area will be given special electronic tags to inform them of the correct method of wearing and placement. Temporary visitors should return the electronic tags and log off in the system when they leave the factory area.
Caring for equipment
Please take care of the electronic label when using it, and it is anti-drop and high temperature. Please do not change the card readers and other communication facilities installed in the factory without the guidance of professionals, and do not deliberately destroy them.
Access control
Please keep the administrator’s account, if there is no professional guidance, please don’t make any changes to the configuration related to the bottom of the hardware in the system.
Nine case introduction
Comprehensive Management System for Personnel and Vehicle Entry and Exit Location of Shanshan Material Storage Area of Xinjiang Tuha Oilfield Material Supply Department



[ad_2]



