KMG860 Swipe Card Access Control System Solution
[ad_1]
1. Overview of access control
Today with high technology, access control systems have become an extremely important part of security systems. In some developed countries, access control systems are developing rapidly at a much higher rate than other types of security products; the reason why access control systems can be used in many security systems The fundamental reason for the product to stand out is that it has changed the passive security methods of past security products such as closed-circuit monitoring and anti-theft alarms. It has replaced passive monitoring with active control and greatly prevented criminals from being normal by controlling the main channel. The intrusion of the passage, and the control of the passage door can be used to limit the scope of activities of the criminal to prevent the crime or reduce the loss when a crime occurs.
In recent years, access control systems have quietly emerged in China due to their own advantages. Various types of places including post and telecommunications systems, power supply systems, banking systems, residential communities, resorts and other places have already used access control systems. Through this system The use of has greatly improved the work efficiency of managers and the degree of safety in the management area.
Now the more commonly used access control systems mainly include biometrics (fingerprints, palms, iris, etc.) and systems represented by radio frequency card systems. Although traditional access control systems represented by radio frequency cards can achieve some effects, in essence, It is the “thing” held by the inspector, not the person himself. As long as the validity of the “thing” is confirmed, the person who holds the “thing” is considered a legal person. So the problem with this method of identifying people by “things” is obvious. One is that the loss of “things” will prevent legal persons from obtaining legal verification; the other is that the use of “things” will prevent illegal people from obtaining legal verification.
With the continuous development of biometric technology and the continuous decline in prices, people increasingly rely on their own characteristics that others cannot replace to prove their identity. Through this set of access control system, your company can realize the clear limitation of personnel authority. Whether it is internal or external personnel, you can clearly define the range of free entry and exit through the setting of authority, and record the entry and exit of personnel. To prepare for inquiries, it greatly relieves the pressure of personnel management, and can achieve the effect of saving manpower while improving safety.
2. Scheme design
Target point setting
It is mainly installed at various demand points, including the fortification of important doors, the management and control of departments that require confidentiality, and the control of company gates.
Management Mode
According to the actual needs of your company, the access control machine can work offline and can be managed online.
product model
In this solution, we mainly use optical independent fingerprint access control attendance machine
Independent fingerprint access control attendance machine: domestically produced, it can work completely offline. It can also be networked for management, using optical fingerprint technology, integrated TCP/IP protocol, simple networking and convenient management. Can be used for access control and attendance system at the same time.
The following specifically introduces the access control attendance program:
Independent fingerprint access control attendance machine
3. Product brief description:
The stand-alone fingerprint access control and attendance machine is an optical offline network fingerprint access control/attendance machine based on Internet technology. Its core covers the two most cutting-edge technologies, bringing people a new generation of safe, convenient, stable and cheap card access control and attendance. system.
The independent card-swiping access control attendance machine adopts a new generation of optical fingerprint sensor, which has more stable performance and can adapt to the operation of complex environments. The independent fingerprint access control attendance machine utilizes the networking mode of Ethernet, which can meet networked applications. Using advanced TCP/IP transmission protocol, the communication is more stable and the transmission rate is higher.
Swipe card + password to open the door, more secure;
Independent and continuous work, good stability
Support multi-user, multi-department combination to open the door;
Time management, making management more scientific;
Do not close the door reminder; power down reminder function.
With output alarm finger, if someone is forced to open the door, you can use it to make an alarm;
Support remote access, allowing you to manage at any time from thousands of miles away;
With SMS function, if you need to notify colleagues or publish some messages, you can directly enter them on the computer, and when colleagues use the machine to open the door, you can see your messages at a glance;
With the attendance software, fingerprint access control/attendance integration can be achieved.
Performance parameters:
KMG860 fingerprint swipe card access control machine is a newly launched fingerprint swipe card access control system launched by Lizhilong, which is convenient for customers who originally used a fingerprint system but now want to use a credit card system;
This machine can store 2000 card information
It has multiple identification methods such as fingerprints, radio frequency cards, passwords, etc., which can be identified in any combination to meet the individual needs of users.
It has communication methods such as TCP/IP and RS485, and has the function of downloading from a USB flash drive.
With offline function, it is suitable for long-distance and inconvenient networking applications.
Have smart learning methods and record query functions
1. Detailed parameters:
Liquid crystal display: 128×64
Recognition angle: full angle recognition
False acceptance rate/rejection rate: <0.0001 %/< 0.1%
Response speed: ≤0.1 second
Working mode: offline, online
Comparison method: 1:N and 1:1
Authentication method: any combination of fingerprint, proximity card, password
Card storage capacity: 2000 sheets
Management record capacity: 1000
Recording capacity: 50000 records
Communication method: TCPIP/RS485/U disk
Language display: Simplified Chinese, Traditional Chinese, English, Korean
Voice prompt: high-definition humanized voice
Ringing function: timing ringing
Alarm function: duress alarm, tamper alarm, forced door opening alarm, door opening overtime warning, input point alarm
Function keys: on duty, off duty, out, return function keys
Lock output: normally open/normally closed
Door open button: can be connected to a normal button or a wireless remote control button
Doorbell output: can be connected to any voltage doorbell
Access control interface: Wiegand 26/34 optional, input/output optional
Working voltage/current: 12V/1A
Lock combination function: optional
Anti-tailing and anti-passback function

Product view

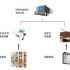
Network connection diagram
Installation process introduction
1. Two KMG860 machines are installed on the gate of each floor, one is installed at 1.5 meters on the right side wall of the room (4 eyes are needed to fix the machine), and the other KMG860 machine is installed on the right side of the outdoor door (make one outside) 1.1M—1.2M bracket to put the machine).
2. The power cord and the automatic door share the same line. The signal line comes from the automatic door motor to the outdoor KMG860 and the indoor KMG860 (see the construction CAD plan for details), and the network cable is pulled from the computer room or the company switch. Go to KMG860 outdoors and KMG860 indoors. If the wiring part is a solid wall, you need to go through the open wire sticking groove.
3. Attendance statistics management
Attendance management software application platform: Window 9X / NT / 2000 / XP (Chinese and English system).
The functions currently implemented are
Set the time of holidays and employee shifts, in view of the differences in the working conditions of employees of different companies, go beyond the 24-hour free scheduling, and the shifts are based on the regularity of the work of the employees, whether there are ordinary shifts and scheduled shifts (employees have certain regularities. Sex, such as a cycle of three days).
Provide employees with daily attendance management such as card signing, leave, overtime, business trip, shift change, etc.
Provides the function of not counting late and automatically working overtime within a certain period of time
According to the end of a certain time period, provide the attendance statistics of employees and departments in each time period.Including day, month, year late
Reports, early leave reports, absence reports, overtime reports, leave reports, business trip reports, and shift reports are used as the basis for assessing employees, department performance, wages, and implementing rewards and penalties.
Provides the login identity settings and passwords, module access rights, and data maintenance functions.
The above report can be saved and printed directly.
Provide data development interface, easy to combine with other management systems.
[ad_2]