Application scheme of non-contact IC card building and residential area access control system
[ad_1]
1 background
In order to implement the “Regulations on Commercial Encryption Management”, strengthen the importance of cities
Access control
System password application security management work, according to the National Password Administration “Notice on Printing and Distributing the Guidelines for the Application of Passwords for Important Access Control Systems” (State Secret Bureau[2009]No. 614) In the spirit of the document, the IC Card Center of the Ministry of Housing and Urban-Rural Development formulated this implementation plan.
2. area
This implementation plan specifies the cryptographic equipment, cryptographic algorithms, cryptographic protocols and related requirements for key management used in the system when using non-contact IC cards to adopt cryptographic security technology in large public buildings and residential area access control systems.
These rules apply to the following situations:
1) Design and implementation of newly built access control system
2) The transformation of the access control system implemented in accordance with the requirements of the national password management department
3 Overview of Access Control System
3.1 System composition
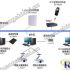
The cryptographic application of the access control system based on non-contact IC card involves application system, key management and card issuing system, as shown in Figure 1.
.jpg)
Figure 1 Structure diagram of password application in access control system
3.2 Application system
In the application system, it is generally composed of an access card, an access card reader and a background management system. The password module in each device provides password security protection for the system. in,
1) The password module in the access control card: used for the access control card reader or background management system to authenticate the access control card (identify whether the access control card is legal) to provide password services (such as calculating the authentication code);
2) The password module in the access control card reader/background management system: used to provide cryptographic services (such as key decentralization, verification authentication code, etc.) when the access control card is authenticated/secure message transmission. When designing the specific scheme of the access control system, a password module should be used in the access control card reader and background management system.
3.3 Key Management and Card Issuing System
The function of the key management and card issuance system is to generate keys for the password application of the access control system, and issue the device (initialize and inject the key) through the cryptographic module to issue the cryptographic module, and issue the access control card (initialize, inject the key and the key) through the issuing device. Write application information).
The cryptographic equipment in the key management and card issuance system provides cryptographic services such as key generation, key decentralization, and identity authentication when access control cards are issued.
4 Security technical requirements related to passwords
4.1 Password application security technical requirements
The password application scheme in the access control system based on non-contact IC card should meet the requirements of Chapter 7.
4.2 Security technical requirements for cryptographic equipment
The cryptographic equipment in the non-contact IC card-based access control system includes: application system cryptographic module, key management and card issuing system cryptographic module. The specific cryptographic equipment is shown in Figure 1.
All cryptographic devices used in the access control system must be approved by the National Cryptographic Administration and certified by the IC Center of the Ministry of Housing and Urban-Rural Development.
4.3 Cryptographic algorithm security technical requirements
The cryptographic algorithm used in the access control system must meet the relevant national requirements, and the cryptographic algorithm application plan should meet the requirements of Chapter 7.
4.4 Security technical requirements for cryptographic protocols
In the access control system, it is necessary to realize the identity authentication of the access control card by the access control card reader and the safe transmission of the authentication data. The authentication protocol used in the identity authentication process should meet the requirements of Chapter 7.
5 Key management security technical requirements
5.1 Key generation
The key generation must use the “City Card Key Management System”.
5.2 Key injection
Attention should be paid to the following two points in key injection when issuing access control cards and password modules:
1) No part of the plaintext key shall be disclosed during the key injection process;
2) Only when the cryptographic device, interface and transmission channel have not received any conditions that may lead to the leakage or tampering of the key or sensitive data, the key can be loaded into the cryptographic device.
5.3 Other requirements
During the entire process of key generation, injection, update, and storage, it should be ensured that the key is not leaked.
6 Other safety factors that should be considered
In addition to the security requirements for cryptographic applications, this solution must consider the following factors from the perspective of the overall security of the system:
1) Management requirements of the background management system;
2) Other management and technical measures that have nothing to do with the password security mechanism, such as password identification, biometric identification, personnel on duty, etc.
In the design and application of the system scheme, other appropriate management and technical measures shall be taken on the basis of password security for specific application conditions to increase the security of the access control system.
7 Non-contact CPU card scheme based on SM1 algorithm
7.1 System composition
This solution uses a non-contact CPU card based on the SM1 algorithm and a security module based on the SM1 algorithm. The schematic diagram of the system configuration is shown in Figure 2.
.jpg)
Figure 2 Schematic diagram of the access control card system
7.2 Principles of the scheme
In this scheme, the access card adopts the CPU card of SM1 algorithm approved by the National Cryptography Administration and approved by the IC Center of the Ministry of Housing and Urban-Rural Development. The card stores the security authentication code, issuance information and the card key, and has an on-chip operating system that meets the relevant standards; The SM1 algorithm is used for identity authentication and secure message transmission between the access control card and the contactless card reader; the card issuing system and the security module in the reader also use the SM1 algorithm to decentralize the key of the access control card, realizing one card for one dense.
The schematic diagram of the scheme is shown in Figure 3.
.jpg)
Figure 3 Schematic diagram of the scheme
In this scheme, the card reader is responsible for the legality authentication of the access control card, and at the same time, the obtained identification information of the access control card is fed back to the access control background management system in the form of security messages, and the security module of the SM1 algorithm of the background management system performs double Identify the legitimacy of the access control card, and control the access control actuator to complete the access control operation. At the same time, the access control server is also responsible for the management of the access control card reader.
In this solution, the SM1 algorithm security module integrates MCU and radio frequency interface functions, and all processing procedures are implemented in the security module. The radio frequency interface module is responsible for the radio frequency communication between the card reader and the access control card; the MCU controls the communication between the radio frequency interface module and the access control card, and is responsible for implementing the data encryption transmission inside the card reader and the communication function with the background management system.
7.3 Password security application process
7.3.1 Card Issuing System
It is divided into the issuance of access control card, the issuance of the security module of the access control reader, and the issuance of the security module of the background management system.
1) Issuance of access card
The back-end management system uses SM1 algorithm to decentralize the root key of the system to realize one card and one secret; the card issuance reader uses SM1 algorithm to authenticate the card in the card utilization process, and the data structure such as application directory and file system is initialized and completed. The download of the card key and the writing of cardholder information and issuing unit information to the card. This process uses the card issuance process of the CPU card to ensure the security of information writing and the confidentiality of data.
2) Security module issuance
The access control background management system uses the “city card key management system” to generate the access control system root key and safely import the security module.
7.3.2 Access card control
The access control card reader directly authenticates the access control card, and at the same time encrypts the authentication data and sends it to the background management system to control the execution of the access control function, which not only guarantees the authenticity of the identity authentication, but also guarantees the confidentiality of the information transmission process.
The specific method is as follows:
The access control card reader reads the security identification code of the access control, which serves as a card-to-card-to-secret dispersion factor;
The access control card reader sends an internal authentication command to the access control card (the access control security module generates a random number). The access control card uses the one-card-one-secret key KEYC in the existing cards to encrypt the random number with the SM1 algorithm to obtain RA ′=ENK(KEYC,RA) and send back to the access control card reader.
? The access control card reader first uses the root authentication key KEYR in the security module to scatter the security identification code with SM1 algorithm to obtain KEYC, and then encrypts the random number RA to obtain RA″, if RA′=RA″, then the card’s The identity authentication is correct, otherwise the authentication fails.
After the authentication is passed, the security module of the access control card reader uses the encryption key KEY to calculate the security message of the authentication information and then transmits it to the background management system. The background management system uses the corresponding decryption key KEY in the background security module to authenticate the security message . After the authentication is passed, the legitimacy of the access control card is compared with the back-end database to execute the door opening operation.
The identity authentication process is shown in Figure 4
.jpg)
Figure 4 Identity authentication process
7.4 Current Status of Cryptographic Products
The key products in this scheme are the non-contact CPU card supporting SM1 algorithm and the security module supporting SM1 algorithm.
The non-contact CPU card supporting the SM1 algorithm must pass the inspection of the IC Center of the Ministry of Housing and Urban-Rural Development.
The security modules supporting the SM1 algorithm are uniformly managed by the IC Center of the Ministry of Housing and Urban-Rural Development.
7.5 Modification content
For existing access control systems that do not meet the requirements of these rules, the following modifications must be made:
1) Adopt standard SM1 algorithm non-contact CPU card as the access control card.
2) Transform the access control card reader, using SM1 algorithm security module as the cryptographic calculation and data processing component.
7.6 Program features
This solution uses commercial cryptographic algorithm products approved by the National Cryptographic Administration and tested by the IC Center of the Ministry of Housing and Urban-Rural Development: non-contact CPU card supporting SM1 algorithm, SM1 security module, and reliable password security.
At the same time, because the SM1 security module integrates MCU and radio frequency interface functions, it is more reliable in terms of data security, and it is uniformly purchased by the IC Center of the Ministry of Housing and Urban-Rural Development and issued to each user unit. The price is cheaper and can greatly reduce the construction cost of the system. Modification costs.
8 CPU card solution that meets the national urban construction industry standards
The CPU card of the national urban construction industry standard can provide a unique card serial number, that is, a security identification code. This security identification code can be read out with only one standard command and can be used for identification in the access control system.
This program adopts SM1 security module approved by the National Cryptographic Administration, and the security of the password is reliable.
Because the SM1 security module integrates MCU and radio frequency interface functions, it can read the unique identification codes of the M1 card and CPU card issued by the current city pass card, and the price is cheaper, which can greatly reduce the construction and transformation costs of the system.
[ad_2]