Financial escort IC card fingerprint verification management system
[ad_1]
System Overview
The logistics of many industries in my country is developing rapidly, and the logistics of the financial industry has gradually received attention from the society. Judging from the current development situation of the domestic escort industry, professional escorts are increasingly showing strong advantages and vitality. Successful experience at home and abroad has shown that separating banknote transport from the main business of the bank and handing it over to a third party, a professional escort company, is an inevitable choice for the banking industry to reduce risks and reduce operating costs.
The financial escort fingerprint verification management system is a high-tech product developed for the cash and cash box escort business in the financial industry. This system uses mature fingerprint automatic identification technology and traditional smart IC card technology to form a set of systems specially used to verify the identity of escort transfer personnel. It can fundamentally replace the traditional banknote transfer book and transfer IC card, reliably record all transfer time, outlets and transfer content, and ensure the accuracy of identity authentication during the transfer and the safety of the transfer data. At the same time, the system can automatically record important log information such as handover time, outlets, operators, etc., which facilitates the operation of banknote depositors, enhances the security of the banknote deposit process, and reduces the possibility of accidents during the banknote deposit process. Following the traditional banknote deposit method, the most advanced and safest banknote transport security management system has been launched. Provide security guarantee for the identification of the personnel of both parties in the transfer of financial escort business. It is very convenient and feasible to use fingerprints to realize identity authentication in links such as the handover of the tail box of the financial system.
demand analysis
1. Current situation
At present, the handover of cashier business generally adopts manual handover. The identification is mainly based on whether the bank’s money car and the person knows or not. However, the handover register and even the transfer vouchers are not included in the important voucher management in some banks. This method has serious problems. Security vulnerabilities are mainly reflected in the following aspects:
The identity authentication method is simple and extremely unreliable. The identity of the handover person is only used as the certificate of the handover person by the face of the handover person or a simple certificate. This is extremely dangerous and provides a convenient door for criminals.
The handover information is recorded on paper, which is easy to tamper with and difficult to enter information management.
Daily statistical information is obtained by manual calculation, which is prone to errors and heavy workload. Moreover, due to the lag of manual entry, it is impossible to monitor the payment status of subordinate branches in real time, and the abnormal payment cannot be detected and investigated in real time. .
If the registration book and transfer voucher information is not strictly supervised, other personnel can easily obtain and imitate it, and it is also difficult to manage this aspect.
Temporary transfer of payment by telephone has potential safety hazards that are difficult to identify and counterfeit transfers.
It is difficult to count and manage the workload and working conditions of the staff.
The division of labor can be changed at will. For example, security personnel and handover personnel can change roles during the handover process, which is prone to hidden dangers.
2. Business requirements
Based on the above situation, the bank cash teller project team put forward the requirements for the wireless terminal application of the cashier integrated business management system, aiming to solve the identification and control problems in the treasury management, cash box handover, and door-to-door collection and delivery. The specific measures are as follows to ensure Security of cashier business:
Safety production of personnel and box identification and identity tag card
Security control and line query security mechanism for hand-held terminal acquisition and return
Security identification and transfer control of cash box transfer in the banking system
Handover control of door-to-door collection
Handover control of home delivery
3. The system achieves its goals
The goal of the system is mainly to use advanced RFID electronic label technology and handheld terminal wireless network technology to achieve the security control of the cash box transfer in the banking system, as well as the security control of the merchant’s door-to-door collection/remittance transfer, specifically:
Use electronic label card to realize safe and efficient handover
Give full play to the characteristics of large storage capacity and good security of electronic label cards, so that staff use IC cards as the main identification method for the transfer of cash boxes, and electronic tags are also used as unique identification and identification methods for the transfer of various tags. The card and a wireless handheld terminal with a security module with a unique number are used for personal identification, which overcomes the security loopholes in the past that only rely on face or simple documents to hand over, and realize safe and fast handover.The escort tag card strictly authorizes working hours and working lines every day, and can store work records
Use the authorized operation and password protection of the work line during the working hours of the escort to record the personal work information in the tag card at the time of the handover, which can also be used as the basis for the workload or assessment of the bank staff
Electronic vouchers replace paper vouchers and register books. The handover data cannot be tampered with and is transmitted to the central database in real time to avoid manual input lag and tampering. All handover work shall be subject to electronic data. The register or payment voucher is only used as a necessary supplementary means , Even if tampering or imitating is meaningless
Handover records are stored in encrypted electronic data, which cannot be tampered with, and avoids the cumbersome manual entry, and can be easily uploaded to the branch or the financial management center database in real time.
The data of the transfer and payment transfer of the cash box can be monitored in real time, so that the bank can further achieve early warning and realize the intervention of abnormal payment transfer.Put an end to crimes that are happening
Temporary transfers can be initiated using wireless handsets for identity authentication
A dedicated wireless POS device can be used to initiate a payment transfer request. The uniqueness of the hardware code of each bank’s equipment and secure authority management can eliminate insecure factors in telephone transfers
The wireless handover equipment is durable, reliable and easy to carry
The handover environment is more complicated, and the equipment is required to be durable and reliable; it can be used outdoors, but also needs to be easy to carry, and the information can be reliably saved and uploaded
Using database encryption technology to realize data security management
The collected data enters the database through the system, and cooperates with the data of warehouse management to realize the information management of the business data of the treasury center.The database is encrypted with a special algorithm, which can only be accessed through the management system, so that the data entering the database is prevented from illegal tampering
Output customized reports to achieve management purposes
Data management is based on the database, and various reports can be customized and output according to business needs, making data statistics a simple task, making management targeted and evidence-based
Provide real-time query of various information, stable and friendly docking with banking system
system design
This system is a set of systems designed to address the security loopholes in the transfer of cash boxes in the treasury and the bank’s door-to-door collection and delivery business in recent years. The system uses electronic means to control and record the entire transfer. process.
Every bankkeeper, escort, cash box administrator, merchant financial staff, etc. receive and send money with the electronic tag ID card as the identity authentication certificate for the transfer of money and tickets, as the transfer of money box, package transfer, and certificate transfer , Foreign currency handover, on-site collection and delivery of money handover certification and many other tasks. Business outlets (or paying customers) recognize the card and not recognize the person, thereby verifying the identity and preventing fraudulent collection; at the same time, use this label card to forcibly track and record the collection business data, thereby preventing “collection” The occurrence of criminal acts such as “detainees, escorts, and embezzlement of deposits”.
An electronic label is installed on each box or bag as the unique identification of the box. Not only does the transfer person need to be authenticated during the handover, but the box must be confirmed to ensure that “the person is in the right box and the correct circulation”.
Whether it’s the transfer of money box or door-to-door receipt and delivery, the wireless handheld terminal is used for handover certification. The handheld terminal not only has a unique hardware number, but also has a safety certification module. The handover, query, background data upload and download all need to pass the safety certification module The certification ensures the safety of the system. The RFID wireless handheld terminal can store the original electronic information of the transfer register in the terminal, and can send it to the database of the branch or financial management center at any time as the data of the bank’s cashier business system. The data can be grasped by the branch or the financial management center at the first time, and the improvement of the timeliness of the data can create conditions for real-time monitoring of the transfer of cash boxes. Through the analysis of the handover data, abnormal alarms were detected, and fraudulent collection and embezzlement in the process of cash box handover and door-to-door collection were found in time. This creates conditions for timely action to prevent crime.
The RFID wireless handheld terminal can also be used as the initiating terminal for temporary payment transfers, instead of telephone transfers or paper bill transfers. Because of its uniqueness, passwords and operating permissions can be set, it can completely prevent savings houses from unauthorized transfers or counterfeiting. The occurrence of transfers. In addition, the data of temporary transfers can also be uploaded to the servers of branches or financial management centers in real time to strengthen data acquisition and monitoring.
The system is based on RFID radio frequency technology and wireless technology to supplement the existing bank teller business integrated management system. It will realize the real-time collection and reading of the handover business chain information, provide safe identity authentication, dynamic monitoring of the currency transport process, Audit and supervise management, realize the modernization and automation of management, ensure the safe and scientific conduct of business, and prevent unauthorized operations.
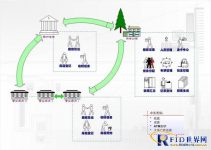
The function structure of the system is shown in the figure below:

The hardware structure of the system is shown in the figure below:

Equipment composition
Handheld fingerprint POS machine
The handheld fingerprint POS machine is a high-tech product developed by Shanghai Fuen Electronic Technology Co., Ltd. It is a perfect combination of fingerprint identification technology, RFID radio frequency identification technology, GPRS wireless communication technology, and POS technology. This product can be widely used. Used for social security cards, medical insurance cards, driving school student cards, fingerprint ID cards, fingerprint test admission tickets, fingerprint financial cards, electronic wallets and other systems that require online or offline identity verification that use IC cards as storage media.
The handheld fingerprint POS machine is small in size, easy to carry, powerful in function, reasonable in price, and flexible in use. The POS machine is embedded with a DSP module, which can independently complete the offline comparison of fingerprints. It has communication ports such as GPRS and RS-232, which can complete the real-time communication function with the host computer. The POS machine can realize the comparison between the fingerprints collected on the spot and the fingerprints stored in the IC card. The POS machine itself has a larger capacity (compared to the IC card) and can retain a large amount of data. Fingerprints are compared.
IC card issuer
The card issuer of this system adopts the FN HFD1108 desktop reader of Fuen Company. It is a high-frequency short-range reader that meets the ISO/IEC 14443 standard independently developed by Fuen Company. It has a sophisticated, stable, reliable, and rich interface. Features.
It can read and write a variety of non-contact IC cards and electronic tags, and supports ISO14443TypeA and Mifare protocols.
The interface between the reader and the computer can communicate with RS232, USB, TCP, etc.
Extensive software support. Support multiple operating platforms: DOS, WINDOWS UNIX, LINUX, etc.; support multiple development language interfaces: VC, VB, PB, Delphi, etc.
Classic design, simple and generous appearance, simple installation.
[ad_2]



