Shenzhen Fei Ruisi Technology Internet of Things Security Series Application Solutions
[ad_1]
Internet of things security, as the name suggests, Internet of things security is to combine the functions and characteristics of Internet of things products and security products to achieve the role of security protection. That is, the application of Internet of Things technology to realize the application of security.
On the other hand, based on the needs of the development of the Internet of Things, the application of security products and technologies in the realization of the Internet of Things is an extension of the security application field. The essence and most important thing is the intelligentization of security products.
In the security industry, the application of video surveillance occupies the vast majority of the market. Therefore, the first solution to the intelligence of security products is the intelligence of video surveillance technology. Through intelligent video analysis technology, some key information worthy of attention can be separated from the video. In this way, a video capture device with intelligent video analysis technology becomes an intelligent sensor that collects key information and becomes the front-end core of IoT applications. As a result, the applications brought about are no longer just video surveillance applications, but a series of new applications centered on video surveillance applications.
1. “Face Capture Technology” for Internet of Things Security
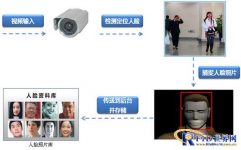
Face capture technology refers to a technology that uses intelligent video analysis technology to detect and locate a suitable face from a video source, and then capture a photo of an adult face. This technology does not require the cooperation of the monitored person, and obtains face photos conveniently and quickly, and can be deployed in a large number of applications.

Undoubtedly, human information is one of the key information that needs the most attention in the security field. Face photos have the characteristics of small storage space and large information capacity, and can establish relationships with personal identities. Therefore, capturing and storing face photos is of great significance. A large number of photo captures can bring the traces of human behavior activities to be preserved, leading to at least four types of excellent applications: face retrieval, blacklist defense, VIP recognition, and stranger recognition.
1. Realization of face capture:
To capture human faces, there are three main ways that can be achieved:
1.1 The front-end face capture instrument analyzes and captures the face in the video source;
By connecting the video to the face capture device at the front end, the face capture function is realized on the front-end embedded device, and the captured face photos are transmitted to the face database through the network and other interfaces. This method is generally used for new projects, small projects, and decentralized projects.
1.2 Intelligent video analysis platform, which separates and captures faces from the back-end centralized video source;
By introducing video sources at the back end of the centralized video surveillance platform, face capture is realized on the back-end intelligent video analysis platform. This method is most suitable for intelligent transformation of large-scale centralized video surveillance platforms such as Safe City and Safe Campus.
1.3 Use the handheld to capture the face on the move.
Use handheld video capture devices with intelligent processing capabilities to collect face photos on site, and transfer the captured faces to the back-end face database to complete relevant real-time applications. For occasions that require mobile collection and mobile law enforcement, this is the simplest and most effective way to collect faces.
2. Application of face capture:
After the front end completes the face capture and collection, it is generally necessary to cooperate with the front-end or back-end face photo recognition and comparison technology to complete the comprehensive application. There are four main types of applications.
2.1 Face retrieval
Face retrieval refers to searching for facial features in a large number of face photos and video sources by inputting photos or other face information, and searching for records where the face has appeared.
Generally, this application is used in conjunction with the intelligent transformation of a safe city. When a large number of face photos are collected at the front end, through face retrieval, you can quickly locate the behavior and activity traces that the photos have left in the system, and it is convenient to locate the past activities of the people concerned, the places where they appeared, etc. , It can effectively cooperate with the application of various technical investigation methods.
2.2 Blacklist Arming
In some key occasions, it is necessary to quickly arm and alarm the blacklisted personnel, such as various ports, airports, and petition offices. When the faces in the blacklist appear in the video scene, they can be quickly identified and alarmed, prompting manual intervention.
The face captured by the front-end is automatically compared with the blacklist library in real time. When the similarity reaches a certain threshold, the alarm linkage is automatically performed, thus realizing the process of arming the blacklist. For wanted criminals, smugglers, etc., it has a great deterrent and application effect. A similar system was deployed at Shenzhen Huanggang Port, supported by Shenzhen Fei Ruisi Technology.
2.3 VIP customer identification
Imagine a scenario: when a VIP customer enters the business premises, the system can automatically identify its identity without the customer’s proactive identification, provide personal data, consumption history, consumption preferences and other information to the service staff, and the service staff will go there immediately Provide corresponding personalized services before. This is VIP customer identification.
Main applications include luxury stores, high-end car service points, high-end clubs, bank account management centers, sales offices, etc.
2.4 Stranger recognition
Stranger recognition refers to a way of identifying and prompting strangers outside a certain range. The main applications are private gardens, private clubs, etc. The captured face is automatically compared with the faces of all owners/members, and strangers are automatically prompted for manual intervention by the staff.
3. Application analysis
Through the analysis of face capture and its industry applications, it is not difficult to find that its application scenarios are very wide, involving large-scale government applications such as safe cities, safe campuses, and city management, as well as enterprise applications such as commerce and banks. It can also be used It has very obvious application prospects in general application fields such as property management.
2. “Fatigue Testing” of Internet of Things Security
For a long time, car accidents and tragedies caused by fatigue driving have appeared endlessly and shockingly. At the same time, with the improvement of people’s safety awareness, the active safety of car driving and special operation posts has also been paid more and more attention by people, and it is expected to be reduced by various technical means. Various hidden dangers caused by fatigue driving and fatigue operation. The main occasions that need to use fatigue detection are:
Fatigue driving warning, mainly for drivers of dangerous goods transportation vehicles, long-distance passenger vehicles, school buses and other drivers in the industry;
The fatigue status detection and early warning of operators in special dangerous positions such as tower crane operation posts;
Detection and early warning of fatigue status of guards on guard posts, duty rooms, etc. who need to maintain a high degree of attention;
From the perspective of the application of the Internet of Things, fatigue detection is to continuously perceive the fatigue state of the human body through a non-contact method. Once the human body is fatigued, various linkages such as local sound and light alarms and remote alarms are performed to achieve the purpose of early warning.
Fei Ruisi Technology uses the technology accumulation in intelligent video analysis for many years, and analyzes the human body appearance and identity through intelligent video analysis, so as to realize the continuous analysis and perception of the fatigue state of the human body. Based on this, an intelligent video fatigue state warning device was introduced to detect and warn the fatigue state of the human body.
[ad_2]