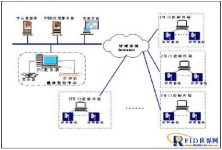
Based on RFID technical personnel asset tracking system solution
[ad_1]
Chapter 1 System Overview
1.1 Application overview
The real-time location and tracking system for classified assets (APS: Area Position System) is an area real-time location system that uses the most advanced ACTIVE RFID technology in the world. The APS positioning system can timely and accurately reflect the dynamics of personnel in various areas to the central monitoring computer system, so that managers can grasp the distribution of personnel in the control area and the movement trajectory of each controlled object at any time, so as to make more reasonable manage. When there is an emergency, managers can also quickly understand the location of relevant personnel and confidential assets based on the data and graphics provided by the APS regional positioning system, and take corresponding control measures in time to improve the efficiency of safety and emergency work .
The company’s main business is 2.4G long-distance readers and various active electronic tags in the field of radio frequency identification. The product adopts the most advanced 0.18uM microwave chip technology, which makes the performance of RFID substantially improved compared with the original microwave technology, and completely solves the long-distance, large-flow, ultra-low power consumption, and high-speed moving identifiers. The problem of identification and data transmission, and the cost is greatly reduced compared with the past. At the same time, it also solves the fatal weakness of the low-frequency electromagnetic wave technology with short induction distance and poor anti-collision ability. Its various technical indicators are superior among similar products, and are widely used in long-distance identification of various personnel, vehicles and assets, all-in-one card consumption, anti-counterfeiting and anti-theft, real-time monitoring, tracking and positioning, etc.
Chapter 2 Design Ideas and Principles
2.1 The idea of system design
The APS area real-time positioning system involves embedded technology, mobile computing technology, radio frequency identification, computer software, database, digital communications, etc. Therefore, in addition to its functions, the stability, reliability, anti-interference ability, fault tolerance and abnormal protection are also fully considered when designing the scheme. The system uses the existing mature industrial TCP/IP communication network as the main transmission platform, and the corresponding wireless identification base stations, RFID identification tags and other equipment are connected to the system, and the real-time positioning management software and the main system are used as a standard special database for the background Data exchange to achieve regional target tracking and positioning and safety management. The overall design of the system is mainly reflected in:
1) Realize the effective identification and monitoring of the entry and exit of targets in the deployment control area, so that the management system fully reflects “humanization, informationization and high automation”.
2) Provide managers with management information on personnel entry and exit restrictions, attendance operations, cross-zone alarms, safety monitoring, help alarms, and reasonable scheduling. Once there is an emergency, the system can immediately know and trace all controlled targets. The location and history of sports to ensure the efficient operation of safety management;
3) The safety, scalability, easy maintenance and easy operation of the system design;
4) Easy networking, BS structure, easy to realize a wider area networking monitoring.
2.2 System design features
1) Highly automated. The system can automatically detect the time and location information of the controlled target passing through the controlled area, and automatically realize the attendance, statistics and safety management of the controlled target.
2) Mature and reliable network communication system. The wireless identification base station installed in the deployment control area transmits the collected information to the central centralized control system through the TCP/IP communication network in real time, without human intervention in the whole process.
3) Complete data statistics and information query software. The system software has a dedicated database management system, including controlled target information collection and statistical analysis system, attendance statistics and management analysis system, display and print various statistical reports, and provide a full range of queries and management for senior managers Serve.
4) The safety, stability and reliability design of the system. The system products are designed to work continuously and reliably all day long in an outdoor environment.
5) Complete alarm call system configuration for abnormal conditions (including invalid card, invalid card, blacklist card entry, unauthorized area, etc.).
2.3 Main functions realized by the system
1) Real-time tracking and monitoring of the controlled target and emergency button for help, and the position is automatically displayed;
2) Real-time query and print the current and a certain period of time controlled target number, activity track and distribution;
3) Attendance, statistics, storage and printing of controlled targets;
4) The static and dynamic editing and drawing of the monitoring map page is open to users, supports multiple graphics formats, and can be operated by the mouse and keyboard
Work, fully support real-time multi-tasking. While the system is collecting real-time data, the system can record, display, query,
Editing, manual entry, network communication, etc.;
5) The system central station and network terminals can be operated in a local area network, so that all terminals on the network are within the scope of use authority
Monitoring information and system comprehensive analysis information can be shared inside, and various data reports can be inquired;
6) The monitoring software has a strong drawing ability, and provides a corresponding graphics library, the operator can continuously monitor
At the same time, it is easy to realize online and complete graphic editing, drawing and modification;
7) The RFID identification tag adopts nanowatt low power consumption design, is light in weight, does not need external power supply, and has a variety of carrying methods for
choose.
The entire system will try its best to maintain the user’s existing network system and application system, and reserve interfaces, which can be combined with the existing application system or the future application system to realize the unified management function of multiple parties and reduce or avoid the user’s repeated investment.
2.4 Principles of system construction
System construction includes both software and hardware. When developing, purchasing and integrating software and hardware, Shanghai Renwei Electronic Technology Co., Ltd. guarantees that the following principles are followed:
1) Advanced
The main construction idea of the APS system is to use radio frequency automatic identification technology, embedded mobile computing technology and software technology to construct a product intelligent tracking system covering a large area, with the advantages of advanced, mature, and cost-effective products.
2) Economical
On the premise of ensuring that the technical requirements are met, the system design uses products with the best performance-to-price ratio as much as possible. The construction of the system maximizes the role of some of the original equipment, such as computer networks, equipment, software, etc., saves investment for users to the greatest extent, and protects existing user investments.
3) Practicality
The construction of the system fully meets the application requirements and actual conditions of this project, highlighting strong practicability, friendly interface and simple operation.
4) Scalability
In the system plan, the system capacity and network development plan are designed according to the viewpoint of system analysis and overall planning, which not only considers the current ease of use, but also has appropriate advancement.
Chapter 3 System Overview
3.1 System principle
The APS real-time positioning and tracking system uses RFID (electronic tag) as the most advanced identification code at present. It has the characteristics of not easy to break, reliable data, long service life, and long effective communication distance. It is an alternative to barcode and infrared identification. The best choice. Install it on the controlled target to be the unique identification of the target for tracking and positioning.
At work, managers use networked wireless identification base stations to track and locate targets.
3.1.1 Electronic label
Simply put, electronic tag (RFID) technology is a non-contact automatic identification technology. Its basic principle is to use radio frequency signals and their spatial coupling and transmission characteristics to realize automatic machine identification of stationary or moving objects to be identified.
The radio frequency identification system generally consists of two parts, namely the electronic tag and the reader. In the application, the electronic tag is attached to the object, equipment, and person to be identified. The reader is used to automatically remove the electronic tag in the It is agreed that identification information is taken out or specific information is written, so as to realize the function of automatically identifying items or automatically collecting item identification information.
Because RFID does not require a light path between the tag and the reader, it avoids the shortcomings of other automatic identification systems (such as bar codes). This ensures that the RFID system can be used in harsh environments, such as dust, dirt, high humidity, and poor visibility environments. The biggest advantage of RFID is that it can still get a satisfactory read and write speed under the above-mentioned harsh environment. In most cases, it can respond within 100 milliseconds. In addition, the reading and writing of RFID is completely automatic and transparent. It does not require manual scanning of tracked objects, nor does it require activation of magnetic stripe readers, IC card readers, etc. like other contact tag technologies.
3.1.2 The working principle of RFID automatic identification
The system composed of RFID and short-range communication equipment mainly includes two parts: smart RFID, RFID read-write unit (Read-Write Units, RWU). The wireless communication between the read-write device RWU and RFID realizes the communication between the information management system and RFID. Information exchange.
The read-write device RWU is an RFID read-write controller, which is composed of a microprocessor, a security module, a microwave communication controller and communication interfaces such as RS232, 485, TCP/IP, etc. It uses short-range communication protocols and microwave wireless transmission methods to realize RWU For the purpose of safe and reliable information exchange with RFID, RWU connects to the host computer through RS232, 485, WIFI, GPRS, TCP/IP, etc., receives control commands and data from the host computer and returns data.
RFID is a mobile device with microwave communication function and information processing and storage functions. RFID built-in a small real-time task system to complete the internal memory, I/O, power supply, communication protocol, key, algorithm, command protocol processing and other functions of the RFID.
The core of the wireless communication protocol adopted by the short-range communication technology is the cell segmentation formed by the coverage of low-power microwave antennas, and the time division multiple access and synchronous communication mechanism based on the HDLC protocol are adopted to realize RWU- by designing corresponding processing and control software. Two-way data transmission and information exchange between RFID.
3.2 The overall structure of the system
According to the overall system functions and on-site investigations, the overall design plan of the secret-related asset management system consists of two parts. One is the external secret-related asset access control system on the floor, and the second: the secret-related asset management system within the floor. The two parts complement each other to form a complete Secret-related asset management system.
3.2.1 Access control management system for foreign secret-related assets on floors

Access control design for off-floor assets
3.2.2 Working principle of access control management system
The fixed asset access control management system is based on advanced radio frequency technology. Each mobile carrier is equipped with a wireless identification. On the first floor, two identification base stations (elevator entrance and exit installation cables) are installed at the elevator entrances and exits (unit gates). Test antennas and install directional readers at the entrance of the unit). When the wireless identification is within a certain range of the identification base station, the identification base station will automatically identify the entry and exit of the item, and automatically record the wireless identification ID number carried by the item that enters and exits; If confidential assets are not authorized, the system will automatically alarm to prevent the occurrence of confidential incidents. So as to realize the strict control of the access of each fixed asset carrier, and at the same time ensure the high efficiency and speed of actual operation.
3.2.3 Access control management system functions
1) Prevent the unauthorized removal of secret-related assets from unauthorized areas. For example, when a secret-related asset is authorized for use inside the building, and the borrower deliberately or unintentionally carries the asset outside the building (again Sub-authorization), the reader/writer collects relevant information and transmits it to the background for comparison, and activates the alarm device to give an alarm to prevent confidential leakage; only the fixed assets that have been authorized for the second time can be taken out of the building. Related information (such as: borrower, borrowing date, out-of-warehouse time, etc.) is automatically recorded in the database;
2) Unit leaders or unit employees only need to carry electronic tags and pass through the access control to complete the attendance function (employee’s name, position, working time and other related information are automatically entered into the database), and can print out the weekly and monthly time periods according to actual needs Attendance report;
3) Prevent strangers from breaking into the office building under various names to ensure the safety of various classified assets and administrative personnel;
4) Register and issue temporary passes to visitors, foreign businessmen, etc. approved by the leader.
3.2.4 Components of the access control management system
1) Long-distance fixed directional reader (all-in-one), long-distance fixed cable test antenna reader
2) Long-distance active (passive) electronic tags, as temporary cards
3) PC server
4) Alarm
5) Confidential asset management system software
6) The card issuer, authorizes the temporary card
3.2.5 Installation Topology Diagram of Access Control Management System

Elevator cable test antenna installation diagram

Installation location of the directional antenna at the entrance of the unit
3.3 Secret-related asset management system on the floor

Secret-related assets design drawing on the floor
3.3.1 Work flow of the secret-related asset management system on the floor
The secret-related asset management system on the floor uses RFID technology, and each mobile carrier is equipped with a wireless identification. Install one (or more) identification base stations that match the wireless identification in the computer room, so that all fixed assets are identified Within the identification range of the base station, the identifying base station will automatically identify all the ID information carried by all fixed assets and supervise the status of all fixed assets in real time. If confidential assets are brought out illegally without permission, the system will send information to the monitoring center and trigger an alarm at any time. Only authorized legal fixed assets can be safely brought out, thereby ensuring the safety of each fixed asset.
3.3.2 The working principle of the secret-related asset management system on the floor
1) The wireless identification is scanned by the identification base station equipment, and the signal is transmitted to the server;
2) The administrator logs into the management platform through the password-related asset management software administrator password on the server to enter the fixed license, temporary license or wireless identification number that is strictly prohibited to be carried out, and the system automatically recognizes and judges;
3) If the server receives a wireless identification that the system is set to allow to carry out, the system will automatically record the time of entry and exit and the card number;
4) If the server receives a wireless identification that the system is set to prohibit carrying out, the monitoring center or the door and its secret room alarm will beep for a long time until the danger is eliminated.
3.3.3 Functions of the secret-related asset management system on the floor:
1) Real-time inventory, the inventory staff click the page refresh option, the reader will complete all the fixed assets in place within a few seconds, and the uploaded system management software will inform the inventory staff of the number of inventory assets and display the loaned assets Physical information (lending time, lending period, borrower’s name, contact information, etc.), through the networking mechanism of each warehouse, you can know the loan and lending of the company’s computer room assets across the country at any time;
2) Regional positioning, regional non-precision positioning can be achieved through more than 3 readers.
Detailed area positioning: The main technical issues regarding RFID positioning are as follows:
◆ The complexity of the positioning environment, RFID is a technology that uses microwave transmission, and the emission of waves is irregular, and the transmission is easily affected by the environment, such as reflection, diffraction, shielding, etc.;
◆ The technical characteristics of RFID products and the recognition distance of the product. At present, the recognition distance is mainly through adjusting the signal receiving range (the gain of the reader antenna) and the direction (receiving range) of the reader. Because these two indicators are difficult to accurately control, they limit the development of RFID positioning technology to a certain extent;
Since the reception of the reader is difficult to control, do we consider changing the antenna gain of the RFID electronic tag to achieve positioning, thereby making fuzzy judgments. .
Regional positioning plan:
ABC is a reader, the receiving range is constant, tag1 tag2 tag3 is the same parameter and gain type tag. The gain can be cycled automatically (0db 1db 2db 3db respectively). When transmitting data, it can also send its own antenna gain data.
Schematic diagram:

Take the icon tag1 as an example,
When the maximum tag gain is 2db, the ABC reader can receive the signal
When the maximum tag gain is 1db. AB reader can receive the signal
When the maximum tag gain is 0db, the A reader can receive the signal
From this, it can be calculated through the software that tag1 is closest to A, that is, tag1 is positioned near A to achieve regional positioning
Take tag2 as an example:
When the maximum tag gain is 2db, the ABC reader can receive the signal
When the maximum tag gain is 1db, the ABC reader can receive the signal
When the maximum tag gain is 0db, the B reader can receive the signal
The software can also calculate that tag2 is closest to B, that is, tag2 is positioned near B.
This solution can avoid the influence of complex environment on RFID signal transmission to a certain extent. It can judge the realization of regional positioning by the number of recognition by multiple readers and its own gain when receiving. This technology can meet some of the needs of regional positioning to a certain extent, such as: monitoring the bank cash box area, monitoring the location of special equipment in hospitals, and the positioning of classified assets and personnel. . . . .
[ad_2]



