Solution of refined management system for supervision places based on RFID technology
[ad_1]
I. Overview
Supervision places such as detention centers and prisons are an important part of the country’s powerful institutions, and they are responsible for the important mission of law enforcement and education reform. At present, China is in a period of social transformation. Due to the increasing number of detainees suspected of economic, violence, gang and drug involvement, there are also many repeat offenders, and the methods of criminal resistance are constantly being renovated.
In contrast, prison police are generally inadequate. For ordinary policemen, in order to prevent accidents, they need to spend a lot of time talking and communicating with detainees, and grasp the psychological conditions of detainees in a timely and complete manner. The work intensity is also very high. As far as the leaders of the prison are concerned, they are also faced with the fact that individual policemen do not strictly follow the relevant regulations and procedures of the Ministry of Justice and the Ministry of Public Security, and they are still relatively arbitrary and bring certain risks. If these risks do not happen, it is difficult for leaders to discover. From a management perspective, prevention is far more important than emergency relief.
At present, large prisons have thousands to tens of thousands of people, and the current prison management technology methods are mainly concentrated in security (mainly video surveillance, infrared curtain walls, access control, power grids) and OA. The refined management lacks technical support. .
Hangzhou SMIC Microelectronics Co., Ltd. has cooperated with Lin’an Detention Center in 2008. After more than two years, through RFID-related products and solutions, it can help to grasp the dynamics of detainees in real time and ensure that existing regulations and systems are strictly implemented. Improve the level of refined management of prison business safety.
2. Specific challenges faced by the delicacy management of prisons
1. Unable to accurately grasp the number and location of detainees in real time
At present, the method of naming the prisons is very primitive, mainly relying on the number of detainees reporting and the manual counting of the number of police officers. It mainly relies on the sense of responsibility of the police, which is particularly prone to errors. In the unlikely event that the disciplined police have a slightly less sense of responsibility and a little inattention, detainees will easily be fished in troubled waters. At night, due to safety reasons, there is no way to make an overall roll call. At night, the police cannot enter the prison room, only by visual inspection. In addition, the total number of people in the entire prison is summarized one by one by the police, which is very slow and not time-sensitive.
At present, the regional positioning of a detainee mainly depends on the manual judgment of the police officers, or the manual search through the video surveillance system. Not to mention the inefficiency, and there is no way to avoid concealing and shielding detainees by individual supervisors. Detainees move between different areas, such as from the prison to the factory, to the event venue, etc. There is currently no way to track when and where each detainee was, and how the historical activity trajectory is.
Currently, infrared curtain walls are commonly used for alarms on the perimeter of walls, but they cannot distinguish between animals, objects, and people, and cannot accurately identify who has crossed the boundary briefly. As far as the leaders of the prison are concerned, there is no way to understand the situation of the whole and each individual detainee in real time and accurately, which brings more serious hidden dangers.
2. Unable to strictly uniquely identify the identity of detainees without making mistakes
At present, the identification of prisons is still relatively primitive, mainly relying on the personnel number and name, and mainly relying on the responsibility and memory ability of the police officers (distinguishing names, personnel numbers, appearance characteristics), but each prison guards dozens or even hundreds of detainees. It is difficult for personnel to guarantee that there will be no mistakes, because it is impossible for people to concentrate for a long time. This is an objective physiological law.
After a long period of time in custody, detainees are all bald, wearing the same clothes and easy to be mistaken. It is difficult to distinguish between twins, and there are also many people with the same name and surname. In some prisons, there have been mistakes in the release of detainees with the same name and the same surname, and mistakes such as miscalculations of people with the same name and surname during consumption.
3. The alarm method is not concealed and inconvenient
At present, the alarm is mainly by shouting or pressing the alarm on the wall of the prison room. However, under special circumstances, detainees dare not call the police publicly; when a detainee is attacked, there may be no way to press the alarm.
At night, detainees have a heart attack, etc., it may be impossible or too late to press the alarm on the wall.
4. Consumption manual accounting is inefficient and error-prone
In the process of consumption, it is often easy to make mistakes with the same name and surname, and manual reconciliation search is very slow and labor-intensive; although the matter is small, the impact is very bad.
5. There is no precise monitoring of the entry and exit of temporary staff
Most prisons have labor production sites. In order to train detainees, some teachers are often hired from outside, and most of these teachers are migrant workers. They go in and out of the prison more frequently, and at present, the scope of their activities is mainly monitored by the police. Have they been approved by the leaders when they come in? Are there activities within the prescribed scope for certain? Is there a timeout? And so on, there is no precise information.
6. It is difficult to monitor the temporary outings of detainees
Temporary going out, such as seeking medical treatment, is the link with the highest probability of escape for detainees. At present, it is mainly based on the attention of the police. Apart from handcuffs and fetters, there is no other technical means to assist.
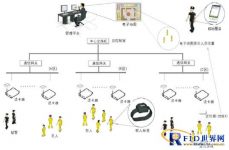
Three, the system plan
The system consists of two parts: hardware and software. The hardware includes:
Electronic tags (wristbands, badges), RFID readers, RFID locators, RFID handsets, RFID communication gateways, etc.
The wristband RFID active tag is a new type of tag specially designed for personnel location management. It is applied to the location management of special supervised groups. The unique ergonomic design makes the carrier more comfortable. The tag has reliable anti-vandalism characteristics. From the moment the tag is put on, the tag will continuously and automatically emit signals so that the system can monitor it at any time. If unauthorized, any attempt to remove or destroy the tag will trigger an alarm.
RFID readers are installed in specific locations such as doorways, passages, and internal area division points to receive information sent by all electronic tags in the functional area. The reader adopts innovative modular design ideas to provide customers with real-time label reading automation Management, location-oriented label data management, and application-oriented standardized data interface.
The RFID locator uses advanced low-frequency positioning technology to achieve precise positioning within the area. According to actual needs, the locator can be installed in key locations that require precise positioning, such as fences, cells, doorways, passages, etc. The positioning distance is adjustable within 12 meters.

The RFID communication gateway adopts RFID middleware technology, which shields the diversity and complexity of RFID devices (readers, locators, etc.), and can provide strong support for back-end business systems, thereby driving a wider and richer RFID application. All readers and locators are connected to the upper application system through the RFID communication gateway, and at the same time realize the functions of terminal equipment monitoring and management, data filtering, protocol conversion, and data encryption.
The system software adopts a three-tier structure, with SQL/Oracle as the back-end database, adopts the company’s self-developed, independent intellectual property rights RFID middleware technology, real-time positioning technology, and integrates messaging middleware, Web Service and other technologies to build an excellent performance, scalable upgrade Real-time positioning application. The system has reliable stability, extremely high real-time performance, sound management functions, and is easy to install, simple to integrate, and easy to develop and expand.
4. System function:
1. It is easy to master whoever, when and where
1.1 The zone boundary automatically records the entry and exit information, and judges whether to alarm according to the system’s pre-settings
According to different functions, the entire prison is divided into different areas, and the importance and sensitivity of the areas are different.
For example, the detention center as a whole can be divided into a decided area (that has passed a court decision) and a pending area (no court decision). There is a very big difference between the decided area and the pending area; in the pending area, the accomplices are absolute Those who cannot be together, otherwise there is the possibility of collusion.
The area can be a large area, such as labor site, teaching area, labor site, teaching area, activity area (including infirmary, basketball court, playground, sports field, meeting room, etc.), conference venue, ventilation area, etc.; it can also be accurate to Every room.
Control at the regional boundary. The system automatically records relevant information when a person passes the regional boundary. The system will automatically determine whether the crossing is legal. If it is not, it will automatically alarm.
1.2 Real-time area roll call
The general duty room or any policeman can initiate a roll call for any specific area through the computer or handheld at any time, as long as he has the corresponding authorization, the specific area can be the prison, teaching area, assembly, labor scene, eating, activities (such as playing Basketball) and so on. The general duty room regularly conducts an overall roll call of the prison, such as every 30 minutes.
When detainees pass through different regional boundaries, such as from the living area to the production area, the system will automatically make a roll call.
The system will generate the corresponding roll call report and send it to the corresponding personnel; if there is an abnormal situation such as lack of personnel or detainees who are not suitable for the same place, it will automatically alarm. And provide its last place information, for the staff on duty to notify the nearest police, and at the same time call out the video surveillance of the corresponding place.
1.3 Historical trajectory tracking
The system can record the historical activity trajectory of each detainee between the boundaries of different regions, and can fully grasp who, when, where, where they came from, and where they went.
2. Accurate, real-time and unique identification of identity
We bring a wristband-type electronic tag to each detainee, and issue a card-type electronic tag to the police. Since RFID (Radio Frequency Identification) itself is the biggest use for identification, it solves the problem of detainees. The identification problem.


The wristband needs to be able to resist damage, and strong collisions and beatings cannot affect its work. It can be installed by the detainees in a short time, but there is no way to dismantle it by themselves; at the same time, in case of damage, they can immediately call the police. Since it has been worn on the hands of detainees for a long time, and they have been worn on their hands for sleeping, eating, bathing, etc., our wristbands also have functions such as mildew resistance and anti-allergic functions.
3. Alarm safely and conveniently
Detainees, civilian police, and temporary staff in special circumstances, such as being attacked, threatened, or sudden illness, can safely and covertly call the police or ask for help by pressing the alarm button on the wristband or card. At present, vital signs have been integrated on the wristbands of some special personnel, and the passive alarm function has been added.
4. It is more effective to monitor the temporary going out of detainees
When detainees go out, they need to wear a special wristband and the police carry a special card. The system binds the two. When the detainee is more than 5m away from the police or the wristband is damaged, the wristband and card will sound an alarm; the police can immediately cancel their own voice by pressing the button, and the detainee’s wristband will always make a sound , Prompts the police to track the direction, unless the distance between the two is within 5m again.
5. Temporary personnel entering the prison are more standardized
Temporary personnel such as factory masters, family members of detainees, lawyers, and police officers must be approved by the supervisor on duty to enter the prison, and they must wear a wristband. The system automatically sets the permitted time and range. If the permitted time and range are exceeded, the system will automatically alarm.
6. Consume clearly
The 13.56M frequency band is integrated in the wristband tag to realize all the functions of all-in-one card consumption. Every link from depositing money, transfers, consumption, etc. is accurately recorded, and the system will automatically complete the reconciliation.
7. Combine the refined management of the existing system prison
Real-time monitoring of inquiries, escorts, meetings and other services is implemented, and business processing is faster and more accurate. For example, when a lawyer meets or the procuratorate interrogates, the system can accurately confirm the identity of the police and the detainees, and record the entire route trajectory and related time node information that the police will take the detainees back and forth from the cell to the corresponding room. Be able to accurately know the time, place and other information of the meeting between detainees, lawyers, prosecutors, etc. Those who continue to meet and arraigned after get off work will promptly send reminders to the patrol control, general shift, and on-duty leaders.
When the guards talked with the detainees, the identities of both parties were confirmed, and the time of the detainees entering and leaving the guarding conversation room was accurately recorded, so that face-to-face management was implemented.
Since the entire process is done automatically, it allows the police to spend more time on business instead of dealing with systems and systems. As a prison leader, he can not only control the overall situation at any time, but also track the real-time and historical details of each individual; it truly effectively solves the contradiction between the huge business volume of the prison and the refined management.
5. System value and advantages:
The system is an effective supplement to the original security system and management system. The combination of the two fully improves the management and security level of the entire prison; it solves the deficiencies of the existing security system and transforms from passive defense to active defense. It can also reduce the work intensity of the police, improve the management efficiency of the police, and achieve the goal of demanding police power from science and technology and improving the delicacy of the prison business safety management.
At the same time, the system also has the following advantages:
1. Stable and reliable
Stability is the biggest challenge, and false negatives and false positives are absolutely not allowed. At present, it has been tried out in Lin’an Detention Center for nearly a year, and it is now operating relatively stably and effectively.
2. Easy to operate
Try not to change the current working habits of the police, and do not increase the workload of the police; do not require complex training, simple and easy to use.
3. Easy to deploy
Since it has been running for a relatively long time, the product has become a stable and mature product. At the same time, our various products have been serialized and modularized, and there are mature implementation schemes, and the system is easy to maintain.
4. Highly scalable
System openness: It can be integrated with existing systems such as security system, prison office system, prison application business system, etc. to form a joint force; when new systems are installed in the future, interfaces will also be reserved.
Scalability of RFID applications: The system platform has been built. In the future, it will be very simple to expand many applications such as asset management, vehicle management, and tool management.
[ad_2]



