The application scheme of Tianjin Mobile RFID technology in secret carrier and personnel access control management
[ad_1]
1. System overview
At present, more and more attention is paid to the management and monitoring of secret-related carriers and important confidential documents, such as office portable computers, USB flash drives, mobile hard drives, digital cameras, video cameras, voice recorders, and confidential documents. The secret carrier and important secret document management system adopts the traditional bar code scanning and personnel access control combined method, which has various drawbacks, which brings great inconvenience to the management of secret carrier of enterprises and institutions. Because the traditional bar code asset management method cannot realize the real-time monitoring of the location changes of important assets, and the traditional access control system can only understand the entry and exit of the personnel, and the personnel must actively show the access control card, and cannot grasp the current location of the personnel in real time. Illegal persons carry secret-related carriers out to create opportunities, causing the leakage of secret-related carriers and important documents.
RFID technology is used to realize the authority management and monitoring of staff and visiting customers who enter and exit the scope of secret-related carrier placement, and realize secret-related carrier monitoring, loss prevention management and inventory. This solution uses active RFID readers and active radio frequency cards to realize the remote identification and monitoring function. The staff can realize access control and attendance without actively swiping their cards. At the same time, the staff can be set permissions (including regional permissions, time restrictions, etc.). Sound and light alarms are used for the entry and exit of illegal personnel, so as to avoid the loss of secret-related carriers.
Two, system goals
2.1, system requirements
Every enterprise and unit has movable assets such as confidential and important documents, which can include office portable computers, U disks, mobile hard drives, digital cameras, video cameras, voice recorders, confidential documents, and important paper documents. Information etc. In order to ensure that the above-mentioned secret-related carriers and important documents are effectively protected, the requirements are as follows:
Need to protect the important information stored in the laptop;
Need to authenticate the identity of the person who uses the laptop;
It is necessary to effectively monitor the entry and exit of important paper documents and materials into and out of the confidential office area;
It is necessary to effectively monitor removable electronic devices that store important information;
Other secret-related carriers need to be effectively monitored.
2.2, system goals
The security objectives of movable assets such as confidential and important documents are as follows:
The system automatically recognizes secret carriers and displays detailed information;
The system automatically recognizes the identification card of the person carrying the secret carrier and records the detailed information;
The system sets permissions for personnel entering and exiting the scope of secret-related carrier placement;
When the secret-related carrier is brought out without approval, the system will automatically activate the sound and light alarm and record the detailed information;
3. System composition and characteristics
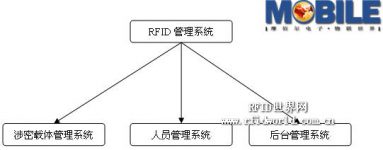
The secret carrier and personnel access control management system mainly manages and supervises the secret carrier and important documents. At the same time, it manages the personnel carrying the secret carrier. The system consists of three parts: the secret carrier management system, Personnel management system and background management system.

Figure 1 System composition diagram
3.1. Secret carrier management system
3.1.1 Secret carrier management function
This solution uses RFID technology to realize the intelligent management function of secret-related carriers, so RFID tags need to be deployed on key movable assets (including secret-related documents, laptops, and others). According to the user’s actual situation and different types of movable assets, electronic tags suitable for different media are used to mark the individuals that need to be identified.Its functional working steps
Attach active electronic labels to secret-related carriers and important documents;
Write information about the secret carrier and important documents on the active electronic label, and the active electronic label card number corresponds to the secret carrier one-to-one;
Upload the active electronic label and secret carrier information to the central database of the management system:
Only those with certificates recognized by the system can enter the scope of control of secret-related carriers:
Hold a certificate recognized by the system and go through the procedures for borrowing, returning, and using after entering;
Find, consult, carry, and inventory secret-related carriers and important documents.
3.1.2 Procedures for preventing the loss of secret-related carriers

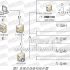
Figure 2. The flow of preventing the loss of secret-related carriers
The use of RFID technology for secret carrier monitoring and loss prevention management can not only monitor the location and flow of each secret carrier in real time, but also remotely monitor the number, name, outflow time, inflow time, and carry of each secret carrier. Personnel information and other materials flowing in secret carriers.
The anti-leakage management of confidential carriers has the timeliness of alarming when the loss occurs, so that the asset management department and security personnel can handle the loss event in the shortest time after the loss occurs, and arrive at the loss site, thereby preventing the loss;
When a person carries a supervised secret-related carrier through the exit, the active reader reader can read the ID numbers of both the person and the secret-related carrier, and the server finds that this secret-related carrier belongs to the scope of supervision. If the person is not authorized to leave, the system will activate an audible and visual alarm, and the server will send the personnel and asset information represented by the two ID numbers to the asset management department and the security control room, and display the room from which it flows out, making relevant Supervisors arrive at the place where the secret-related carrier has been alarmed as soon as possible, and proceed with further processing.
3.1.3 Secret carrier inventory
The use of RFID technology for secret carrier inventory can save time and human resource costs, reduce workload, reduce error probability, instant feedback of inventory status, and automatically prompt missing inventory when inventory is lost; complete inventory work more quickly, and accurately query each involved The location and status of the secret carrier, and the status of each secret carrier can be inquired at any time, and timely maintenance and maintenance can be carried out to reduce the maintenance cost of the secret carrier and improve the operation efficiency and management level of the enterprise.
3.2 Personnel Management System
3.2.1 Internal staff management
The staff corresponds to the radio frequency identification card, which has the staff’s photo, department, position, employee number, etc.;
The staff and the radio frequency identification card adopt corresponding technology for authority management. Each radio frequency identification card has a unique ID number, which cannot be changed or copied; this ID number is the same as the name and department of the employee in the database Corresponding, and set the corresponding permissions;
The staff shall be allowed to enter when they enter the authorized area;
When the staff enters an unauthorized area, the system activates an audible and visual alarm to prohibit entry, and the server reports the accident to the management department, and can directly send it to the security control room to notify the corresponding department to deal with the accident;
When a staff member’s RFID information card is lost or damaged, the server will list this information card as a waste card. When someone else holds the card and enters the storage area of the secret carrier, the system will activate the sound and light alarm to prohibit entry, and the server will report to the management department and security control The room sends an accident alarm for further processing;
The background database records the daily flow information of the staff and automatically organizes and archives them.
3.2.2 Visitor management
Visitors need to show their credentials at the front desk. The front desk compares their credentials with the appointment information and enters the customer’s name, company and other information into the computer after confirmation, and sets the customer’s activity area permissions and valid time, and then issues this temporary card To customers, complete the card issuance process for visiting customers;
Visitors are allowed to enter when they enter the authorized area;
When a visitor enters an unauthorized area, the system activates an audible and visual alarm to prohibit entry. At the same time, the server reports the accident to the management department, and can directly send it to the security control room to notify the corresponding department to deal with the accident;
When the visitor leaves the storage area of the secret-related carrier, the temporary card will be returned by voice or screen prompts, and the visitor will return the temporary card to the front desk. The front desk swipes the card to cancel the correspondence between the temporary card ID number and the customer, and complete the customer visit management process;
When the visitor’s temporary card is lost or damaged, the server will list this information card as a useless card. When someone else enters the storage area of secret-related carriers with this card, the system will activate a sound and light alarm to prohibit entry, and the server will report to the management department and the security control room. Send alarms of unexpected events for further processing;
The back-end database records the flow information of visitors and automatically organizes and archives them;
When visitors need to shuttle between different authorized floors, the inter-floor readers will sense the entry and exit of customers and write records on the server side.
3.2.3 Early warning of entry of unknown persons
Give voice prompts or other reminders to all customers who have not returned their temporary cards when entering or exiting the carrier storage area without authorization.
3.3. Backstage management system
The background management system process is shown in Figure 3:

Figure 3 Backstage management system process
Figure 3 The background management system process is described as follows:
All departments will report the confidential and secret-related carriers that need to be entered and exited to the Secrecy Office;
The Security Office will enter the secret-related carrier into the management system, and the system will begin to monitor the secret-related carrier;
When an outgoing person carries a secret-related carrier out of the gate, the system determines whether the secret-related carrier is allowed to “enter and exit.” If allowed, only record without alarm; otherwise, alarm and record.
Entry and exit records are stored in the system and handed over to the Confidentiality Office;
Fourth, the principle and function of the system
4.1, the working principle of the system
The system schematic diagram is as follows:

Figure 2 System schematic diagram
First, place active card readers in the building’s passages and the area to be monitored. The specific number and location need to be determined according to the actual working conditions on site and the functional requirements to be realized, and they are connected to the computer in the monitoring center through network wiring. At the same time, an active radio frequency identification card is provided for each cadre of the agency and professional institute.
When entering and exiting personnel carrying a secret-related carrier containing radio frequency electronic tags through the channel, the system will automatically identify and display the carrier’s category, serial number, responsible person, placement location and authorized carrying scope and other relevant records. If the secret carrier is carried out without approval, an audible and visual alarm will be activated to remind the guards to pay attention. At the same time, the entry and exit time, processing results and other data will be recorded, and the data will be sent to the background management center. When passing through the channel with the personnel identification card, the photo and personnel information will be displayed, the relevant data will be recorded, and the data will be sent to the back-end management center for attendance registration. Administrative functional units check violation information through the back-end management center every day, notify each unit every week, and put forward rectification requirements; report serious violations to the chief, and put forward suggestions for handling in accordance with relevant regulations.
4.2, system function
The secret-related carrier and personnel access control management system can perform intelligent management and attendance registration on the entry and exit of secret-related carriers and personnel carrying secret-related carriers
Alarm function: When illegal persons or unauthorized persons pass by carrying secret-related carriers, the system will start audible and visual alarms, and record current detailed information (such as: time, location, secret-related carrier information, illegal personnel photos, etc.);
Inventory function: use active RFID handsets to inventory secret-related carriers;
Authority function: the authority (scope and time authority, etc.) can be set for the person carrying the secret carrier;
Attendance function: real-time statistics of the names, time, position, quantity, etc. of personnel entering and exiting secret carriers; statistics, query, summary, report generation, printing, etc. of attendance data;
Tracking function: real-time dynamic tracking, position display, and running track playback of secret-related carriers and personnel carrying secret-related carriers, and real-time positioning and tracking of special personnel;
Query function: all secret-related carriers and personnel carrying secret-related carriers can be inquired (such as: the current location of the secret-related carrier, the name and current location of the carrier, etc.);
Modification function: the relevant personnel information can be modified to reflect the latest personnel situation;
Delete function: delete the destroyed or transferred secret carrier information.
Networking function: The system has a powerful networking function. According to user needs, the control center and each system can be networked in a local area network, so that all networked systems can share attendance tracking data within the scope of use authority, which is convenient for remote query and management ;
Five, system settings
Active card readers are scattered and installed in different areas according to site location and needs, so TIC/IP network structure or optical fiber access is adopted, and a set of monitoring equipment is set up in the gate and the building to share the server. On the management platform, the equipment of each system can be managed, and the control center can manage and control all positioning, alarm, monitoring, access control and other subsystems.
Solution company: Mobile (Tianjin) Electronic Technology Co., Ltd.
Contact: Wang Yao
Fixed phone: 022-58268876
QQ: 1090204646
URL:http://www.myiot.org
[ad_2]