Long-distance personnel vehicle management system solution
[ad_1]
Chapter One Design General Description
In order to strengthen the management of its personnel and vehicles, a large enterprise requires strict management and control of the internal and visiting personnel of the unit. It adopts advanced RFID radio frequency identification technology to realize automatic tracking and control of incoming and outgoing personnel. The employees of this unit are talented with their cards. When entering and exiting, foreign people without a card enter the detection and alarm; at the same time, it is also required to reflect the humanization and intelligence of technology. The smart card for employees can be carried arbitrarily, which does not give employees a sense of control, and is convenient for employees to use. It is adopted for management of external visitors. The second-generation ID card reader registers and issues the card and authorizes the access control channel corresponding to the defended person. The unit vehicle is automatically identified and released at a long distance, and the system is required to not visually damage or obstruct the original building to maintain the overall delicacy and beauty of the building. An advanced management method, and to achieve it at a lower cost.
Chapter 2 Demand Analysis
1. Access control system: Due to the large number of personnel in the unit, the access control system should work in a fully automatic card reading method. For the personnel passage at the unit gate, employees can enter and exit normally as long as they have a card. Places such as computer rooms should be entered in the form of active card swiping. As the key point of the whole system, long-distance card reading requires the following points:
The induction card carried by the employee should be carried arbitrarily, and the card can be put in the employee’s pocket, bag or hung in front of the employee as an identification card.
The sensing distance of the card should not be too far or too close. If the distance is too far, the employee will produce wrong records when passing by the channel, and if the channel is too close, the channel will not be sensed.
In order to reflect human care, the card cannot be directional and can be placed arbitrarily, and employees must not be required to place the card in order to identify it.
The system must have multiple identification and anti-conflict capabilities. There are a lot of people entering and leaving at the same time during the peak hours of employees’ commuting, and the system must ensure that all cards can be accurately identified at a high speed.
The system must accurately determine the direction of entry and exit of personnel, and can not simply record incidents to prevent false entry and exit.
The radio frequency signals generated by the card readers and proximity cards must be harmless to the human body, because employees spend most of their time within the signal range, and the safety of everyone cannot be abandoned for the convenience of management.
2. Attendance system: employees have specific entry and exit time and records when entering and exiting the access control channel. The system does not need to set up other attendance equipment, and directly uses the entry and exit data of the access control point in line with the work time as the attendance record.
3. Consumer system: The consumer system uses the employee’s access card to directly consume, all data is transmitted under the network, and the data between the consumer machines must be automatically synchronized.
4. Visitor system: For foreign visitors, register by directly reading the information of the second-generation ID card of the visitor. For the first-generation license or driver’s license, automatic scanning and text recognition scanners should be used, and the visitors should be photographed. Those who need to enter and exit the entrance control point Places issuing visitor access cards.
5. Vehicle management system: All vehicles of this unit are assigned a long-distance sensor card. When the vehicle arrives near the gate, the gate will be opened automatically, and the foreign vehicle will be released after manual registration. For the vehicles that the cooperative unit enters and exits for a long time, you can also consider installing a long-distance card to facilitate its entry and exit.
Chapter III Implementation Plan
The first section system description
1. System principle
This system is designed using the latest CypherTag™ series TV6 proximity card and RV1 card reader from IDENTEC in the United Kingdom. CypherTag™ is the fourth-generation low-frequency radio frequency automatic identification brand developed by the company in the United Kingdom. CypherTag™ series proximity cards and readers are truly fast and long-distance induction radio frequency identification products, with a card reading distance of up to 3 meters, covering a channel width of up to 3 to 32 meters, and can identify up to 320 proximity cards at the same time , The card reading speed can reach 80km/h, so it can accurately identify and track the direction of fast-moving objects or people from a long distance. In the field of low-frequency radio frequency identification, CypherTag? induction technology is at the world’s leading level.
The working mechanism of the CypherTag? series of remote sensing products is: each proximity card has a 64-bit number. When the proximity card appears within the reading range of the reader, the proximity card is continuously emitted by the reader. The signal wakes up, so as to feed back to the reader a response signal carrying the proximity card number. Through the inquiries and responses between the proximity card and the reader, the reader can accurately and quickly identify the card carried in the proximity card. And output the read proximity card number to an external controller or other terminal equipment in a certain output format, so as to realize the identification of the proximity card.
The management center issues a card to each employee. When the employee passes the card reader antenna (with a reading distance of 3 meters), the card reader can sense the card and transmit the card number in the card to the local controller. The controller judges the access authority of the card, controls the opening of the corresponding door control equipment, and transmits the received card number to the management software. The management personnel can monitor and manage the entry and exit of each door in real time. The software directly adopts the personnel to meet the working hours The incoming and outgoing data is used as attendance data.
For important entry and exit areas, the system is equipped with a photoelectric column with anti-tailing function. The column can emit multiple pairs of infrared beams with a diameter of only 2.5 mm. The system can promptly identify unauthorized persons who are trailing behind legal persons trying to enter the passage. The center sends out audible and visual alarms, and can also capture photos of illegally passing people through the camera for future verification. At the same time, it can send in and out information to the manager’s mobile phone or mailbox. The personnel with the card will be authorized by the controller and no alarm will be generated. record. The system has no physical barriers, which is convenient for people to pass through quickly, and at the same time, it can prevent unauthorized persons from illegally passing through without swiping cards, realizing real fast passing.
For foreign visitors, use the visitor registration machine to directly read the second-generation ID card, the first-generation ID card and other documents to automatically scan and recognize, use a high-precision camera, and automatically take pictures when visitors register. Management software, to authorize the visitor’s office access control permissions, the software automatically displays the visitor information when the visitor passes the access control point at the entrance of the building, and the visitor without a card will generate an alarm when he passes by, and he can swipe his card to sign out when he leaves. Barcode scanner can be selected. Barcodes are printed on the visitor list. After the interviewee signs, the visitor will automatically scan and sign out in the guard room, which is more efficient and faster.
For vehicles entering and exiting, a transparent plexiglass fixed box is placed behind the windshield of the car. Insiders only need to put the card in this box. When entering and exiting the vehicle channel, the card will be read by the antenna on the ground or next to it, and the barrier will automatically Turn on, and the camera will capture the vehicle at the same time.
The TV-type long-distance card used in the system can be used for long-distance recognition or short-distance recognition. Combined with the REV1 card reader with a reading distance of 15 cm, it can realize access control, attendance, consumption, visitors, elevators, vehicles, and patrols. More management and other all-in-one card functions. In addition, the remote proximity card also has the characteristics of non-copying, safe and reliable, and long life. The non-contact card reading method reduces the mechanical wear of the card to zero.
2. System implementation instructions
The system is equipped with a management server and placed in the computer room of the monitoring center; multiple clients are set up, and a monitoring client computer is placed in the lobby on the first floor for security personnel to view the personnel entry and exit photos and alarm information in real time, and install it on the computer room management server The one-card management software is responsible for the maintenance and management of the entire system; the access controller is the core component of the system, responsible for the processing, storage, and control of the input and output information of the entire system. In order to facilitate on-site construction and daily maintenance, the access controller is installed nearby Near the door point, all access controllers are connected via TCP/IP.
Install remote card readers and microwave human body detection probes on the corridor doors; the induction antenna is buried under the floor or placed on the ceiling, and an automatic door-type microwave human body detection probe is installed at the top of the door. Each employee is issued a remote sensor card. The person walks to the first few 3 meters to read the card, and then the door opens automatically after being detected by the probe. The door does not close unless all the personnel pass through, and all the personnel pass through the back door. The angle of the microwave probe is adjustable. The indoor walkway overlaps with the antenna sensing area. Area, set the microwave probe detection area to be about 60 cm, the door will not open when people do not enter the area when passing through the aisle to prevent accidental opening; for stair doors and fire passages, manual swipe card opening methods are used for entry and exit, and close reading is installed inside and outside. Card reader, employees enter and exit by swiping their cards; for visitors and outsiders contacting business, temporary cards are issued for management. Outsiders visiting need to register on the visitor machine at the designated location of the management department, and the registration staff will ask the visitor to go. After contacting and confirming by phone, issue a card with the corresponding authority and print the visitor form. The visitor can enter and exit the designated floor or department with the authorization card in his hand, and cannot enter or leave other unauthorized floors or departments. Hierarchical authority management realizes effective management of the security of the entire unit.
In order to achieve the regional anti-tailing function, in accordance with the strict requirements of the building’s safety management, this scheme uses two doors at the entrance of the first floor of the design unit building as anti-tailing passages. In order to meet the fire protection requirements, the fire alarm button is connected to the alarm input of the controller. When a fire alarm occurs, all doors connected to the control will be automatically opened. The network cable from each access control controller to the switch adopts Category 5e shielded twisted pair to ensure stable communication. Where 485 transmission is used, 485 line must also use RVSP shielded twisted pair. Shielded wires are used to connect the access control controller and other equipment at the door.
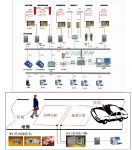
3. System working topology diagram

Section Two, Equipment Selection
1. British CypherTag? Low-frequency long-distance card reader

◆ Transmit frequency 125KHz, receive frequency 4MHz
◆ Underground antenna card reader, no obstacles on the ground
◆ 3m sensing area on the ground
◆ Ultra-wide coverage, single antenna width up to 14 meters
◆ More economical, 16 antennas can be connected externally, with 16 outputs
◆ Accurately judge the direction of personnel entry and exit (anti-fake entry and leave)
◆ The card is always read in a fixed position, and accurately controls the door, gate and channel
◆ The card can be put on a person or in the pocket of a car, and the person and the car can be identified together
◆ The card can be read at any angle, and the signal can penetrate water and some metals
◆ High-speed reading, 320 frames/sec, 120 km/h
◆ High-precision reading, with a misreading rate of less than 1/100 million
◆ One card, the card can be recognized at close range, 15 cm swiping distance
◆ US Federal Communications Commission FCC certification, CE certification
2. SK100-NT Chinese network controller

◆ Adopt 32-bit ARM9 chip and embedded LINUX operating system, clocked at 200MHZ
◆ It can be directly connected to the computer via TCP/IP, without a TCP/IP converter, the communication speed can reach 100M
◆ The card capacity is 10,000, and the event record is 100,000.
◆ Using Flash data backup, the data can be stored for 10 years after power failure
◆ In case of system failure, the latest 100,000 records can be restored
◆ It can be upgraded online through TCP/IP, 232 interface
◆ Smart lock.When the system detects that the door is opened and then closed, it can automatically lock the door
◆ Whether password control and time zone control are required for entry/exit can be set separately
◆ After the card is legal, the name and job number of the person who swiped the card will be displayed
◆ Passed CE and Ministry of Public Security certification
3. Proximity card
Using CypherTag low-frequency and long-distance proximity card, there are two models to recommend, TV1 and TV6. The sensing distance of the two cards is exactly the same. TV1 proximity card is a sealed card, TV6 is a battery-replaceable type, and can be inserted into other types of cards, such as the original unit’s access control card. The features of the product are as follows:
CypherTag TV6 document type long-distance proximity card (replaceable battery)

Product Features:
Long-distance recognition: card reading distance 3 to 4 meters
Anti-collision: 320 proximity cards can be recognized simultaneously on the RV1 card reader
High accuracy: misreading rate is less than 1 in 100 million
High security: private encryption protocol, random communication data
Self-test: automatic output of battery status
Beautiful and practical: can be used as ID card, can print name, photo and other information
Self-sleep: automatically sleep after leaving the sensing area
Anti-liquid: the signal passes through the liquid without any change in the sensing distance
technical parameter:
Card number: 64-bit encoding, optional output digits
Dimensions: 95 x 64 x 5 mm
Weight: 30 grams
Working life: with battery, the battery life is more than 3 years, the battery can be replaced, it can still be used normally for 1 to 2 months after the low battery voltage, and output prompt information.
Material: bright gray ABS shell, can insert a PVC material ISO standard label, can print name, photo, unit and other information, used as a certificate
Working temperature: -20~+60℃
Working humidity: 0-80% non-condensing, slightly waterproof
Working frequency: transmitting frequency 4MHz, receiving frequency 125KHz;
CE, DTI & American FCC certification
Applications:
It is suitable for applications requiring long card reading distance, fast recognition speed, and simultaneous recognition of multiple electronic cards, such as personnel tracking management system, item tracking management system, parking lot management, and vehicle automatic charging management, etc., especially suitable for items Or personnel tracking, control or positioning.
CypherTag TV1 remote proximity card (sealed personnel card)

Product Features:
Long-distance recognition: card reading distance 3 to 4 meters
Anti-collision: 320 proximity cards can be recognized simultaneously on the RV1 card reader
High accuracy: misreading rate is less than 1 in 100 million
High security: private encryption protocol, random communication data
Long life: 7 years of service life
Self-test: automatic output of battery status
Beautiful and practical: can be used as ID card, can print name and other information
Self-sleep: automatically sleep after leaving the sensing area
Anti-liquid: No change in sensing distance when working in water
technical parameter:
Card number: 64-bit encoding, optional output digits
Dimensions: 86 x 54 x 4.5 mm
Weight: 28 grams
Working life: with battery, life is more than 7 years, it can still be used normally for 2 to 3 months after low battery voltage, and output prompt information.
Material: Bright gray ABS shell with polycarbonate label (73 x 50 x 0.2 mm)
PVC white signature panel, can be signed or printed
Working temperature: -20~+60℃
Working humidity: 100% waterproof, normal work in water, no change in sensing distance in water
Working frequency: transmitting frequency 4MHz, receiving frequency 125KHz;
CE, DTI & American FCC certification
Applications:
It is suitable for applications requiring long card reading distance, fast recognition speed, and simultaneous recognition of multiple electronic cards, such as personnel tracking management system, item tracking management system, parking lot management, and vehicle automatic charging management, etc., especially suitable for items Or personnel tracking, control or positioning.
CypherTag TV1 remote proximity card (sealed personnel card)
Product Features:
Long-distance recognition: card reading distance 3 to 4 meters
Anti-collision: 320 proximity cards can be recognized simultaneously on the RV1 card reader
High accuracy: misreading rate is less than 1 in 100 million
High security: private encryption protocol, random communication data
Long life: 7 years of life
Self-test: automatic output of battery status
Beautiful and practical: can be used as ID card, can print name and other information
Self-sleep: automatically sleep after leaving the sensing area
Anti-liquid: No change in sensing distance when working in water
technical parameter:
Card number: 64-bit encoding, optional output digits
Dimensions: 86 x 54 x 4.5 mm
Weight: 28 grams
Working life: with battery, life is more than 7 years, it can still be used normally for 2 to 3 months after low battery voltage, and output prompt information.
Material: Bright gray ABS shell with polycarbonate label (73 x 50 x 0.2 mm)
PVC white signature panel, can be signed or printed
Working temperature: -20~+60℃
Working humidity: 100% waterproof, normal work in water, no change in sensing distance in water
Working frequency: transmitting frequency 4MHz, receiving frequency 125KHz;
CE, DTI & American FCC certification
TP5 card holder (for vehicles)

Pasted on the windshield of the vehicle, a long-distance card can be placed. When the personnel drive, the card is placed in the fixed box, and the card reader can read the card when entering and exiting the vehicle channel. At the same time, the vehicle access control and personnel attendance can be realized.
Applications:

4. SKEPS all-in-one card system

The one-card system mainly includes: access control system, attendance system, personnel tracking system, visitor management system, parking lot management system, patrol system, consumption system, elevator management system, conference registration system, peripheral guarding alarm and other subsystems; in addition, it can also According to user requirements, expand the functions of other application subsystems on the existing basis, such as automatic vending subsystems. The key is to fully develop the one-card multi-purpose function of the proximity card. This is more suitable for the characteristics of the various application subsystems of the internal management of the enterprise unit belonging to different functional departments. Each application subsystem can form its own management system, which can communicate with each other through non-contact proximity cards, which not only meets the independence of management of each function, but also ensures the consistency of the overall management of the enterprise unit. The installation and use of each application subsystem does not require consistency in time. The multi-purpose function of one card is a continuous realization process, which is very flexible and easy to operate.
[ad_2]



