Haohai Yitong personnel and asset management solutions (hardware)
[ad_1]
System Overview:
This system uses RFID technology to realize the authority management and monitoring of the laboratory’s internal staff and visiting customers, as well as the inventory of internal fixed assets and the management of the prevention of loss.
The system will use the same hardware environment to manage personnel and assets in a unified manner.
System composition description:
The system is divided into three subsystems: personnel management system, asset management system, and back-end management system.
Realize functional requirements:
○ Personnel management function:
Realize the correspondence between personnel and card numbers; divide the regional access authority of the internal laboratory staff: the staff of each independent laboratory can only work in the designated laboratory, and prevent other laboratory staff from entering without permission;
Regional authority and time authority of visiting customers: visiting customers are active in authorized areas and time periods to prevent customers from entering non-authorized areas and entering after the authorized time limit;
Give voice prompts or other reminders to all customers who have not returned their temporary cards when they are not authorized to enter and leave.
○ Asset management function:
Card numbers correspond to fixed assets one-to-one, realizing quick inventory; monitoring the flow of fixed assets and alarms of flow and loss under unauthorized conditions.
○ Backstage management system:
Process the information collected by the front-end and feed back information on current events.
Function realization description:
○ Hardware facilities:
An RFID reader is installed at the entrance and exit of each laboratory to monitor the personnel and objects entering and leaving the laboratory.
Each staff member is equipped with a personalized printed work card containing RFID tags, and visiting customers are equipped with temporary cards to realize the correspondence between the entry and exit personnel and the tag ID number.
An RFID tag with absorbing material is fixed on each fixed asset to realize the correspondence between the tag ID number and each asset.
(1) Personnel management:
○ Staff management:
The staff are often in and out of the laboratory, and adopt corresponding card issuing management. That is, the photo, department, job title, and employee number of each employee are printed on the surface of the work permit on the RFID work permit; more detailed personal information of the employee can also be written in the work permit. Make each work permit have both visual image and text information, as well as internal information that can be read from a distance.
The staff and RFID work permit adopt corresponding technology for authority management. Each RFID work card has a unique ID number, this number cannot be changed or copied; this ID number corresponds to the employee’s name, department, etc. in the database, and the corresponding authority settings are performed.
When an employee enters the authorized area, the door antenna indicator will show a green light; entry is allowed.
When an employee enters an unauthorized area, the door antenna indicator will show a red light and give a sound prompt; entry is prohibited. The server reports this unexpected situation to the management department, and can send it directly to the security control room. Notify the corresponding department to deal with accidents.
When an employee’s RFID information card is lost or damaged, the server will list this information card as a waste card. When someone else enters the laboratory with this card, the door antenna indicator will show a red light and give a sound prompt; entry is prohibited. The server sends unexpected event alerts to the management department and the security control room for further processing.
The background database records the daily flow information of the staff and automatically organizes and archives them.
○ Visiting customer management
Visiting customers need to show their credentials at the front desk. The front desk compares their credentials with the appointment information, enters the customer’s name, company and other information into the computer after confirmation, and sets the customer’s activity area permissions and valid time, and then this temporary card Issued to customers. Complete the card issuance process for visiting customers.
When the customer enters the authorized area, the door antenna indicator shows a green light; entry is allowed.
When a customer enters an unauthorized area or enters the laboratory after the expiration date, the door antenna indicator will show a red light and a sound prompt will be issued; entry is prohibited. The server reports this unexpected situation to the management department, and can send it directly to the security control room. Notify the corresponding department to deal with accidents.
When the customer leaves the laboratory, the temporary card will be returned by voice or screen prompts, and the customer will return the temporary card to the front desk. The front desk swipes the card to cancel the correspondence between the temporary card ID number and the customer, and complete the customer visit management process.
When the customer’s temporary card is lost or damaged, the server will list the temporary card as a waste card. When someone else enters the laboratory with this card, the door antenna indicator will show a red light and give a sound prompt; entry is prohibited. The server sends unexpected event alerts to the management department and the security control room for further processing.
The back-end database records the customer’s flow information and automatically organizes and archives it.
When visiting customers need to shuttle between different authorized floors, the door antennas between floors will sense the customer’s entry and exit, and write records on the server side.
For example, when a visiting customer enters an unauthorized floor, the door antenna will give an alarm to prohibit entry. At this time, the door antenna should read the customer ID number twice. When the record leaves after the alarm, when the interval between the two records exceeds the specified time, it shall be regarded as the customer staying illegally in the unauthorized area.
In special circumstances, if the customer is allowed to move between the two floors of AB, the door antenna will not send an alarm when leaving the A floor, but when the customer leaves the A floor and walks out of the institute building, the door antenna at the entrance of the institute will An alarm is issued to remind the customer to return the temporary card to the original card-collecting office. Reduce the loss of temporary cards and reduce operating costs.
○ VIP visits
○ Unidentified people enter the early warning mechanism
When an unknown person enters the laboratory floor, the door antenna detects the entry of a person without a card, the door antenna indicator shows a red light, and a sound prompt is issued; entry is prohibited. The server sends unexpected event alerts to the management department and the security control room for further processing.
(2) Asset management:
○ Inventory of fixed assets
Fixed asset inventory based on RFID technology can save time and human resource costs, reduce workload, reduce the probability of error, instant feedback inventory status, and automatically prompt missing inventory when inventory is lost; complete inventory work more quickly, and accurately query each fixed asset The location and status of the asset. The status of each fixed asset can be inquired at any time, and maintenance and maintenance can be carried out in time to reduce the maintenance cost of fixed assets and improve the operation efficiency and management level of the enterprise.
In the preliminary work, each fixed asset is affixed with RFID tags to form a corresponding relationship, and then the corresponding relationship is entered into the server database and output to the handheld RFID reader.
During the inventory, the staff only need to place the handheld RFID reader close to the label area (3-10cm) of the fixed asset to read out the name, property unit, installation date, maintenance date and other information of the fixed asset. The reader will automatically write the reading information into the database to complete the inventory operation.
As shown in (Figure-5), the asset management in the laboratory computer room can be regarded as a collective relationship in the software. A represents the entire laboratory computer room, which includes all asset information in the computer room; B represents a cabinet, which is not only an independent fixed asset, but also includes information about all subordinate items in the cabinet C; D represents an independent asset without subordination information.
The advantage of setting the collection relationship in the database: it can refine the affiliation of each asset in the cabinet to facilitate asset maintenance and management; it is especially convenient to remind the missing inventory from the entire computer room after the inventory is completed to each cabinet in advance when there is a missing inventory. When the internal asset inventory is completed, early reminders will help deal with the missing inventory earlier and reduce the effort of repeated inventory.
For example, there are eight switches C0, C1, C2, C3, C4, C5, C6, and C7 in cabinet B. After the assets in cabinet B are counted, only seven switches can be read. When starting to count the next cabinet, the handheld RFID reader will automatically send out a voice prompt that the asset inventory in cabinet B has not been completed, display the information of the switch that has not been counted, and prompt to repeat the inventory of cabinet B or report the loss of assets. If the cabinet-switch set is not set up, the missing inventory or asset loss can only be known after the inventory of each laboratory computer room is completed; this will increase the time and human resource loss of repeated inventory.
Using RFID technology for fixed asset inventory, the average inventory time for each fixed asset is only 1 to 2 seconds, and all the staff has to do is to move the handheld RFID reader close to the fixed asset, and there is no need to fill in the fixed asset inventory table. , It also saves the trouble of re-listing when the market loses. Based on this calculation, a laboratory with 500 fixed assets can complete the inventory work in just 17 minutes. save time and energy.
Missing inventory reminder: When the staff completes the inventory of a single computer room area, the handheld RFID reader will automatically compare the inventory assets with internal data; if a missing inventory is found, the handheld reader will display the list of uninvented assets and send it out Voice prompt. The staff can make a replenishment or report to the asset management department through prompts.
○ Anti-loss management of fixed assets
In the use of RFID technology for fixed asset monitoring and loss prevention management, RFID technology has shown that it is faster and more efficient than any previous technology; it can not only monitor the location and flow of each fixed asset, but also remotely monitor each fixed asset. The number, name, outflow time, inflow time, information of personnel carrying fixed assets and other information.
In the anti-loss management of fixed assets, the most important thing is the timeliness of the alarm when the loss occurs, so that the asset management department can deal with the loss in the shortest time after the loss occurs and arrive at the loss site, thereby preventing the loss;
The fixed assets here include not only hardware assets such as servers, but also paper, CD-ROMs, USB flash drives and other carriers that record technical data, experimental reports, and other confidential information.
Fixed assets will not move by themselves, so when fixed assets flow out of the laboratory, someone must carry them out of the laboratory. When a person carries a supervised fixed asset through the laboratory exit, the exported RFID reader will read the ID number of both the person and the fixed asset, and query the server through the server that this fixed asset belongs to the scope of supervision and has not yet been obtained Authorization to leave the laboratory. The door antenna will automatically send out sound and light alarms; the server sends the personnel and asset information represented by the two ID numbers to the asset management department and the security control room, and shows which laboratory it comes from. Make the relevant supervisory personnel arrive at the laboratory where the alarm occurs as soon as possible, and carry out further processing.
○ Normal flow of fixed assets
When fixed assets are put into storage for maintenance or dispatched to other laboratories for operation, etc., it is regarded as the normal flow of fixed assets.
For the normal flow of fixed assets under authorization, the fixed asset flow authority is set through the background management input terminal, and then the designated fixed assets are moved to the designated location by the staff within the specified time. Finally update the server database information.
The structure diagram of the accident handling process:
The accident here refers to:
●Enter the laboratory area without a card:
●Access to unauthorized areas with a card;
●Customer’s temporary card is overdue for entry;
●Invalid card enters the laboratory area;
●Unauthorized movement of fixed assets;
Annex I:
Occupied frequency resource description
Which frequency to use to transmit the signal is a question to be carefully considered when applying RFID.
●Low frequency (125 kHz) is usually used on livestock tags. It has a good transmission effect in a short distance (<10cm), but the data transmission speed is relatively low and the cost is relatively high.
●High frequency (13.56 MHz) has relatively fast data propagation speed and low cost, and is the only frequency that can be used all over the world.
●Ultra-high frequency (860-960 MHz, microwave 2.5-5.9 GHz) can be transmitted quickly and cost is low, but the signal of the tag is easily shielded or interfered, especially on metal and liquid (human body), the signal attenuation is large, We have solved these problems well.

Application environment requirements of this program:
1 Personnel management requires no electromagnetic radiation damage to the human body, and can reach an identification distance of about 1.2 meters (the width of the laboratory entrance and exit); the RFID tags worn by the personnel can be completely and reliably read when the personnel pass quickly;
2 Asset management requires that RFID technology can be used to achieve rapid inventory without missing or misreading; it can be read well on the metal surface of the equipment in the computer room; the door antenna can completely and reliably identify the RFID tag on the fixed asset.
3 In the use environment, RFID tags and readers are required to have no interference with the electronic equipment in the computer room. In the mobile communication technology experiment and development in the computer room, they will not interfere with the communication frequency band of the mobile phone and other communication frequency bands to ensure the electromagnetic radiation in the test space Purity.
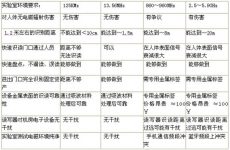
According to this environmental requirement, the four frequency bands of 125KMz, 13.56MHz, 860~960MHz, 2.5~5.9GHz are screened as follows: (see table)
Comprehensive comparison of barcodes, RFID tags in various frequency bands, and readers:

Taking the above factors into consideration, this solution uses 13.56MHz frequency band RFID products for personnel and asset management.
Attachment 2: This program is different from other RFID manufacturers’ advantages
In this solution, the specific needs of the customer and the special application environment are the final starting point, and various frequency conflicts and frequency interference risks that may be encountered in the implementation are predicted for the customer, and the customer’s implementation cost and maintenance cost are reduced.
Attachment 3: Similar successful cases
Xiamen Jimei University Library
Book inventory and library automatic lending and return management can reduce waiting time in line and reduce theft rate. RFID technology can also speed up the classification of various books in the library, and can quickly put all kinds of books back on the shelf, simply scan through the RFID card reader next to the shelf to quickly understand the detailed catalog; verify the borrower’s History of identity and borrowing.
Personnel Management of Jiangsu Mining Bureau
Personnel attendance and equipment inspection, through the readers installed in fixed positions, automatically record the flow of personnel, and accurately understand the number of personnel entering and exiting each well in real time, improving the overall management level and efficiency of the enterprise. Predict possible risks and prevent various accidents.
Annex 4:
Main hardware technical parameters and basic quotation:
slightly
Annex 5: Project Implementation Plan
Hardware installation: the installation and wiring of the antennas of each door, the erection and overall connection of the server, the printing of internal employee cards and visiting customer cards. Complete within 10 working days
Software development and debugging are completed: project preliminary investigation, analysis and design, database and various module development, man-machine interface design, system debugging. Complete within 30 working days
Total implementation time: 30 working days.
If you have any questions, please contact
Document production: Ren Gong
Email: [email protected]
QQ: 479017087
Mobile: 13911533725
http://company.rfidworld.com.cn/rfidworld_company_27961.html
[ad_2]



