Asset management rifd solution
[ad_1]
RIFD Asset Management Solution
Introduction to RFID
RFID (Radio Frequency Identification: Radio Frequency Identification), commonly known as “electronic tag”, is a non-contact automatic identification technology that automatically recognizes the target object and obtains related data through radio frequency signals. The identification work does not require human intervention. It is used as a wireless version of the barcode. RFID technology has the advantages of waterproof, anti-magnetic, high temperature resistance, long service life, long reading distance, data on the label can be encrypted, storage data capacity, and storage information can be changed freely. Its application will be used in retail, Industries such as logistics have brought revolutionary changes.

RFID basic composition
? Radio frequency tags are physically composed of three parts: tags, antennas, and readers;
?Tag (Tag): Composed of coupling components and chips, each tag has a unique electronic code, high-capacity electronic tags have a user write area, attached to the object to identify the target object;
?Reader (Reader): a device that reads (and sometimes writes) tag information, which can be designed as a handheld or fixed type;
? Antenna (Antenna): transmit radio frequency signals between the tag and the reader;
RFID features
?Data storage: Compared with traditional forms of tags, the capacity is larger (1bit—1024bit), and the data can be updated at any time and can be read and written;
? Reading and writing speed: Compared with bar codes, there is no need to align and scan in a straight line, and the reading and writing speed is faster, multi-target recognition and motion recognition are possible;
? Easy to use: small size, easy to package, can be embedded in the product;
? Security: dedicated chip, unique serial number, difficult to copy;
? Durable: no mechanical failure, long life, resistance to harsh environments;

RFID working principle
The basic working principle of RFID technology is not complicated: the reader sends a radio frequency signal of a specific frequency through the transmitting antenna, and when the electronic tag enters the effective working area, an induced current is generated to obtain energy, the electronic tag is activated, and the electronic tag encodes itself The information is sent out through the built-in radio frequency antenna; the receiving antenna of the reader receives the modulated signal sent from the tag, and it is transmitted to the reader signal processing module through the antenna regulator, and the effective information is sent to the background host system for processing after demodulation and decoding. Related processing: The host system recognizes the identity of the tag according to logical operations, makes corresponding processing and control for different settings, and finally sends out instruction signals to control the reader to complete the corresponding read and write operations.
RFID classification
1. According to the power supply, it can be divided into Passive and Active:
?? Passive Tag (Passive): The Passive sensor itself has no power source. The power source is from the Reader. The reader emits a frequency to make the sensor generate energy and transmit the data back to the Reader. The volume is relatively light, thin and short, and has a long use. Years, the sensing distance is shorter.
?? Active Tag (active): The price is higher, because of the built-in battery, so the volume is larger than the Passive tag, there are years of use, longer sensing distance.
2. According to the frequency, it can be roughly divided into three categories: LF, HF, and UF:
?? Low Frequency (Low Frequency): 100~500KHz The sensing distance of low frequency is shorter and the reading speed is slower, mainly 125KHz, with good penetrating ability;
?? High Frequency (High Frequency): 10~15MHz high-frequency sensing distance is slightly longer, and the reading speed is also lower and the frequency comes quickly, mainly 13.56MHz;
??Ultra High Frequency/Microwave: between 850~950MHz (UHF) and 2.45GHz, the sensing distance is the longest, the speed is the fastest, and the penetration is poor;
Rfid application
As a data carrier, electronic tags can play the role of identification, item tracking, and information collection. In foreign countries, electronic tags have been applied in a wide range of fields. The RFID system composed of electronic tags, readers, antennas and application software is directly connected to the corresponding management information system. Every item can be accurately tracked. This comprehensive information management system can bring many benefits to customers, including real-time data collection, secure data access channels, and all product information can be obtained offline, etc. Wait. In foreign countries, RFID technology has been widely used in many fields such as industrial automation and commercial automation.

RFID data center asset management
In addition to the selection of highly reliable IT infrastructure equipment for successful data center management, an efficient asset management system is also the key, which is directly related to maintaining the reliable operation of the system, reducing the operating cost of the system, and increasing the profit of the enterprise. Survey reports on the United States, the United Kingdom and other developed European countries show that:
Downtime incidents have huge losses, and the losses caused are directly related to the management of the computer room
Large organizations experience 20 serious downtime incidents of “a certain system” each year, and it takes an average of 13 hours and US$140,000 to resolve an incident. Operational losses and legal liabilities caused by downtime are sometimes quite huge. The survey found that 70% of outages were related to line connections, and 85% of them were caused by human error. 80% of the time spent dealing with downtime is to find the wrong device or connection. 42% of companies said it can take at least a day to find a down server.

Serious waste of assets and equipment
The survey found that for companies with thousands of server rooms, the average utilization rate of each server is only 10%-20%. 28% of company information center managers do not know how many servers there are in their computer rooms, let alone know the warranty period and maintenance of idle machines and equipment. The investigation also found that 20%-40% of the infrastructure is idle because the engineer did not remove the wiring from the patch panel in time when the line was reconnected. Approximately 60% of the cost of software licensing is redundant. Low equipment utilization is not only a direct waste of asset investment, but also consumes power and takes up valuable rack space.
Energy and space crisis
The survey found that 11% of data centers will have insufficient space in the computer room that year; 14% have reached the power supply limit.
Based on previous work experience and successful experience from many parties, our company has designed and deployed a set of RF-EAM (RFID-Asset Management System) data center asset real-time monitoring platform that meets the characteristics of the data center. It is one of the basic components of the next-generation data center. The system uses RFID automatic identification technology and network and software platforms to provide faster, more careful, and more accurate daily management for the monitoring of important business assets such as cabinets.
Optimization of data center and migration of new and old computer rooms
According to data from the world’s advanced IT data centers, data centers are not static. About 24-40% of data center assets are moved and updated every year. The main reasons come from: optimizing power supply and introducing new ones (machine updates); implementing virtual technologies (for example: cloud computing, etc.); and relocating old and new computer rooms.

In response to the above problems, with its current advanced technology and rich implementation experience, it has developed an asset monitoring system that meets the characteristics of the data center. Using RFID automatic identification technology and network and software platforms, it provides faster, more careful and more accurate daily management for the monitoring of important business assets such as cabinets, and realizes the functions of real-time monitoring, automatic recording and asset inventory, and further reduces the occurrence of security risks Possible.
solution
The basic environment of the data center is very conducive to the application of RFID technology, because the usual data center is concentrated in a limited area with high density of expensive equipment, and the basic environment such as temperature and humidity is very good, this environment can be reduced The cost of deploying RFID and improving its efficiency. RFID radio frequency identification technology is mainly composed of reading and writing equipment and electronic tags. The target object is automatically identified through radio frequency signals between the reading and writing device and the electronic tag, and its related data is obtained, thereby realizing the identification of the object and transmitting the collected data Go to the application system platform for summary, analysis, and processing. This technology has the characteristics of long reading distance, strong penetrating ability, anti-pollution, high efficiency (multiple tags can be processed at the same time), and large amount of information.
Using the above principles and characteristics of RFID, install RFID electronic tags on fixed assets such as the cabinet and its internal equipment, install RFID identification equipment at the entrance and exit of the computer room and inside the cabinet, and combine with the asset management monitoring platform to achieve full visibility of assets and real-time update of information. It can monitor the use and flow of assets in real time, which is embodied in real-time query of equipment location, equipment movement tracking records, alarms, equipment management statistical reports and other management objectives, and establish a set of advanced, standardized and optimized management mechanisms.
System composition and architecture
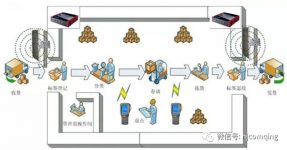
The RFID cabinet asset monitoring system is composed of electronic tags (RFID tags), readers (RFID readers), servers and system software (Tracking Server). This system is in B/S mode. The following figure shows the system architecture of an RFID cabinet asset monitoring system, in which:
Each device in the cabinet is equipped with RFID electronic tags (Tags);
RFID reading system is installed in each cabinet;
An RFID reading system is installed at the entrance and exit of the computer room;
The staff uses a handheld RFID reader.

Main function
The RFID data center management solution can achieve the following functions:
Equipment monitoring inside the cabinet: Install the RFID reading system inside the cabinet to cover the RFID tags of the equipment inside the cabinet. The system can read the RFID tags on the equipment in real time. When the equipment is operated and moved, it will automatically form a work record. Alarm value to realize asset monitoring and alarm;
Computer room entrance and exit monitoring: The RFID reading system installed at the entrance and exit of the computer room covers the passage area. Any equipment with RFID tags will be recognized by the system when passing through the area, and the data will be uploaded to the monitoring platform in real time for corresponding data recording and processing;
3D display platform (Horizon View)
?? Establish a database of equipment and facilities, and add all the equipment and facilities in the computer room to the database to clearly manage each equipment and facility and provide the necessary basic data for monitoring;
?? Carry out 3D graphical management of the location of the device; realize the location query of the device;
?? Record the changes of equipment location in real time and automatically;
?? In order to dynamically display the equipment at each location on the monitoring interface, when adding equipment, you can choose the original equipment model, or the new equipment model, if the equipment model is added, you need to submit a proportional photo of the front of the equipment;
?? The alarm function is implemented by the alarm engine deployed on the monitoring node; first, establish an alarm strategy library, and set the alarm threshold for each collected state data;
?? Whenever the device data is collected, the alarm engine is called to check the threshold to determine whether an alarm is triggered; if the threshold is exceeded (ie, illegal operation and movement of the device), an alarm is triggered;
After triggering an alarm, add a record to the alarm record and submit it to the main control center; at the same time, call the alarm notification module to send alarm information to other systems.
[ad_2]