Base station wireless access control system plan book
[ad_1]
Chapter 1 Proposal of Base Station Wireless Access Control Scheme
Due to the particularity of the construction of communication base stations such as China Mobile and China Unicom, the location of the base stations is relatively complex. In our country, the topography and landforms are ever-changing. If necessary, urban and rural areas, mountains and plains may become base stations, and they are generally unattended. , The theft phenomenon is becoming more and more rampant, making the outdoor and indoor equipment of the base station face the danger of theft, easily causing the base station to fail to work normally and causing immeasurable losses. Therefore, the demand for intelligent access control management is becoming increasingly urgent, and because of the limitations of network wiring, traditional access control solutions are no longer applicable, and wireless access control solutions have emerged as the times require.
When it comes to wireless access control, people may have a cognitive misunderstanding, thinking that wireless means that there is no need to connect the card reader, controller, electric lock, exit button, and door sensor. In fact, this is incorrect. As far as the power supply of the electric control lock is concerned, a wired power supply must be connected. In addition, all the above-mentioned devices are installed near the door, and the interconnection is very simple, without the need for wireless. The wireless access control technology described in this solution refers to the networking mode of the access control controller and the upper management computer. Generally, the networking of the access control system is the wired RS-485/422 bus, and newer products use the TCP/IP network for networking. These two methods obviously have limitations in the base station access control management application. The RS-485 bus The communication distance is not far enough, and the investment in TCP/IP network wiring is huge; the wireless access control system we propose now connects each access control controller with the upper-level management computer in a wireless manner to form a wireless access control network, and this wireless method uses ready-made The GSM communication network realizes the transmission of data through short messages, and can communicate with the network where there is a mobile phone signal.
Chapter 2 System Overview, Design Principles and Functional Features
1. System overview
Kingkang series of access control management products adopt today’s most advanced digital electronic technology, identification technology, wireless communication technology and network technology to integrate intelligent identification, computer network management, and digital monitoring into one intelligent access control, pushing access control management to a new world . In this program system, we will use radio frequency card access control machines to centrally manage and decentralize the access management of each channel (mainly the base station door here). We can use proximity cards as base station maintenance personnel and inspectors to enter and exit the mobile communication base station. The certificate can be used to generate the entry and exit record report of the mobile base station access control channel security through the computer, and can be connected to the linkage equipment through the access environment detection equipment to transmit alarm information in real time to ensure the stable operation of the base station.
2. Design principles
Due to the need for security and high-efficiency management, the design of the base station access control system should follow the following principles:
Practicality of the system
The content of the base station access control system should meet actual needs. It is convenient and simple to build or modify the system, and is convenient to use; the software is simple to operate and easy to use, and it is convenient to save and transplant data.
System stability
Since the base station access control system is an uninterrupted and long-term working system, the safe and stable operation of the base station is closely related to people’s lives, so the stability of the system is particularly important. The system is required to have more than one year of successful application experience in the market, with a corresponding customer base and customer service system. In terms of communication, the wireless networking method adopted by the system is based on the GSM mobile communication network, where there is a mobile phone signal to ensure stable communication.
System security
While all the equipment and accessories in the base station access control system are in safe and reliable operation, they should also comply with relevant Chinese or international safety standards, and can work effectively in non-ideal environments. The powerful real-time monitoring function and linkage function fully guarantee the safety of the use environment.
System scalability
As the technology of the access control system continues to advance, user needs are also changing. Therefore, the design and implementation of the base station access control system also takes into account the actual needs of future expansion, and can flexibly increase, decrease or update various subsystems to meet different requirements. The needs of the time, to maintain a leading position for a long time, become a model of practical application. When the system is designed, a reasonable configuration is made for the functions that need to be realized, and this configuration can be changed. Even after the project is completed, the configuration change is also possible and convenient. The system software will be upgraded and perfected according to the market demand of the developers in different historical periods, and the software will be upgraded free of charge for the corresponding application customers. At the same time, it can be extended to all-in-one card projects such as the attendance system and patrol management system.
Easy maintenance of the system
The maintenance of the base station access control system during operation should be as simple and easy as possible. The operation of the system is truly to the extent that it can work when the power is turned on, and it can be operated when it is plugged in. And there is no need to use too many dedicated maintenance tools during the maintenance process. From the configuration of the computer to the configuration of the system, the configuration of the front-end equipment has fully considered the reliability of the system and implemented the corresponding certification. While achieving the lowest system failure rate, we also consider that even for unexpected reasons When a problem occurs, ensure the convenient storage and rapid recovery of data, and ensure that the channel can be opened quickly in an emergency. The maintenance of the entire system is online, and the normal operation of all equipment will not be stopped due to the maintenance of some equipment.
All in all, the system can be more convenient, safer and more reliable for the management and monitoring of base stations.
Three, the main design basis specifications
1. International integrated wiring standard ISO/IEC11801
2. “Code for Electrical Design of Civil Buildings” JGJ/T 16-92
3. “The People’s Republic of China Security Industry Standard” GA/T74-94
4. “People’s Republic of China Public Safety Industry Standard” GA/T70-94
5. “Engineering Technical Code for Monitoring System” GB/50198-94
Chapter 3 Wireless Base Station Access Control System Structure and Configuration
1. The functions and features of the system
In addition to the channel control and management functions, the wireless base station access control system also adds environmental monitoring and equipment linkage functions. It is the best choice for unattended base stations and computer rooms:
1. It can improve the efficiency of base station maintenance, make management more standardized and effective, monitor events in real time, and reduce the burden on maintenance and management personnel.
2. One proximity card can replace all base station door keys, eliminating the confusion of key management; and one card can have different access rights, and the authorized card can enter the base station within the scope of its duties. All incoming and outgoing situations are recorded in the computer, which is convenient for inquiring about the time of specific events and fulfilling responsibilities.
3. If the employee’s proximity card is lost, you can report the loss and delete the authorization immediately in the system, so that even if someone else finds the proximity card, they cannot enter the base station for damage. This is much more convenient than ordinary mechanical locks, and you don’t have to do it for safety. For the sake of changing the lock again, re-key for everyone. For those who resigned, fired or left, the proximity card can be recycled for reuse, and authorization can also be deleted. Because the proximity card cannot be copied, there is no need to worry about reentering the base station after resignation.
4. Using advanced international internal encryption protocols, outsiders cannot open your electric locks to enter your premises by mechanical or other high-tech methods.
5. In special circumstances, the software can be forced to operate, and the door can be forced to close through the function of the software, so that even authorized card holders cannot enter. After that, the system can be restored to normal through the software.
6. All Chinese operating system based on Windows, friendly interface, convenient and simple operation. Ordinary clerks can be competent to operate the corresponding management software, not to mention the professional technical personnel of the operator.
7. The system has good scalability and has wireless and wired networking functions. You can upgrade and add new control doors at any time at low cost.
8. It is recommended to use the original all-weather card reader, which is waterproof and anti-static to ensure the stable operation of the system. When the system is running, there is no need to connect to a dedicated computer, and the system information will not be lost when the power is off, and it can be equipped with UPS backup power to maintain the normal operation of the system. High-quality products and perfect after-sales service system relieve you of worries.
9. The environmental monitoring and equipment linkage function can monitor the environment of the base station at any time, and can respond instantly through the access of linkage equipment, and upload alarm information to the management center computer and alarm management mobile phone to ensure the safe and stable operation of the base station.
2. Functional management structure model
The basic function of base station wireless access control is not much different from that of ordinary access control, and it has a variety of composition modes, as follows:
Mode 1: One-way induction type (access card reader + controller + exit button + electric lock)
The user shows the authorized proximity card outside the door. After the card reader recognizes and confirms the legal identity, the controller drives the electric lock to release, and records the time of entry. Press the door button to open the electric lock and go out directly. All operations are uploaded to the management center computer in real time via SMS.
The security level of this mode is low, and the record of going out cannot correspond to people.
Mode 2: Two-way induction type (access card reader + controller + exit card reader + electric lock)
The user shows the authorized proximity card outside the door, and after the card reader recognizes and confirms the identity, the controller drives the electric lock to release, and records the time of entry. When the user leaves the controlled room, he must also show the authorized proximity card inside the door. After the card reader recognizes and confirms his identity, the controller drives the electric lock to release, and records the time of going out.
The security level is high, not only can effectively prevent the illegal entry of outsiders, but also can inquire the last person and time to leave, facilitating the implementation of responsibilities and providing evidence.
Mode 3: Card + password type (card reader with keyboard + controller + card reader + electric lock when entering the door)
After the user has swiped the authorization card, he must enter the correct password to open the door. The password is a personalized password, that is, one password per person. The advantage of this is that it has higher security. Even if the card is lost, it cannot be accessed even if it is picked up by someone. It is also necessary to enter the correct password.
This method requires not only card verification, but also password verification. Only when both verifications are valid can the verification be passed.
Mode 4: Multi-card door opening method (access card reader + controller + exit card reader + electric lock)
To enter the base station, you need to use multiple authorization cards (2-6 optional), and you can enter after the inductive swiping identification is valid;
Multiple card openings can be combined with different permissions. For important base stations with central equipment, this method has the highest security, but it requires at least two people to work together to implement it.
Mode 5: Open the door remotely
Open the door remotely through the management center software or send an instruction to open the door remotely through the management mobile phone. This method mainly plays the role of assisting the door opening.
Three, the basic components of base station wireless access control
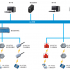
1. Wireless access controller:
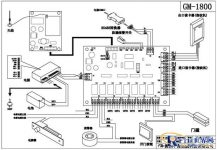
The wireless access controller GM-1800 is composed of a stable switching power supply, a control panel, and a short message transceiver module; the control panel can be connected to 2 card readers, 8 switching inputs, 8 relay outputs, and 4 AD input interfaces; The SMS transceiver module is responsible for communicating with the wireless integrated management software installed on the computer of the management center.
2. Integrated wireless access control management software:
Centrally manage and monitor all units through a computer, and perform corresponding management tasks such as clocks, authorization, environmental monitoring, and information statistics.
3.Management center computer short message transceiver module
Responsible for the communication with each wireless access control, it is the SMS sending and receiving terminal. In theory, each SMS transceiver module can communicate with N wireless access controller mobile phone numbers, but considering the actual application operation and system stability, it is recommended that each SMS transceiver module manage within 50 wireless access controllers; One management computer can receive multiple SMS transceiver modules.
4.Mobile SIM card
Each wireless access controller needs to be equipped with a mobile phone SIM card, and the SMS transceiver module of the management center also needs a mobile phone SIM card.
5.Manage mobile phones
The system can set up 4 mobile phone numbers for each wireless access control controller except all the management mobile phone card numbers of the SMS transceiver module of the management center as the management mobile phone. As an important person in charge, you can instantly receive the alarm information sent by the wireless access control controller, and You can send related instructions to directly operate the wireless access controller.
6. Proximity card:
The proximity card has a variety of shapes and can be selected at will. The chip in the card is written with a 32-bit code that will never be repeated.
7. Card reader:
The card reader is the control part that reads the proximity card. A built-in radio transmitting antenna can receive information such as the code sent by the card when the proximity card is approaching. After the card reader analyzes and confirms that it is a valid card, the code is transmitted to the control part.
Note: The important channel can use a fingerprint collector for higher security.
8. Power locks:
Electric locks are used to replace mechanical locks. After the controller sends the door open signal, the electric locks can be opened automatically.
9. Door sensor:
The contact detector is used to detect the opening and closing state of the door to determine whether the door opening is valid or approved, and then the controller triggers an alarm signal.
10. Door button:
Go out can be set to go out by pressing a button.
11. power supply:
Provides the power supply for system operation power and the execution structure of the electric lock. At the same time, the power can be connected to a backup battery to ensure that the system can operate normally during a power outage; the controller can provide the main power 12V power supply interruption alarm.
12. Other
The wireless access controller has the function of connecting to the environmental monitoring equipment, and the linkage alarm parameters can be arbitrarily set through the software, arming and disarming, and real-time transmission of relevant information.
Four, system connection diagram

[ad_2]