Design scheme of Oupin OPEN smart access control card system
[ad_1]
Chapter 1 Overview
With the rapid innovation of the information industry and the rapid development of the network, smart card technology has been accepted and applied by all walks of life in the society. Among them, the non-contact smart card “all-in-one card” is due to its advanced technology, convenient use, confidentiality and security. More and more widely used in various fields, government agencies, office buildings, smart communities, large enterprises, commercial consumption, highway tolls, campuses, hospitals, etc., identity recognition, parking lot management, access control, passage control, attendance, conference sign-in , Visitor management, personnel information, security patrol, resource management/elevator control, consumption/POS, library management, energy control, etc. are the most commonly used functions.
1.1 Non-contact smart card and multi-information carrier identification
Card identification carrier: The basic carrier for authentication and identification of the one-card system is a contactless smart card. Its full English name is Contactless Integrated Circuit Card, also known as a radio frequency card (proximity card). It is an OR card with storage, encryption and data processing capabilities. Multiple integrated circuit chips and induction coils are enclosed in a standard PVC card, through the data signal of radio waves to complete the access to information, modify reading and writing, etc., and return to the card reader.
Now the commonly used cards include ID cards, IC cards and CPU cards. ID cards have low security and cannot store data. They are suitable for ordinary occasions with low requirements; IC cards have encryption measures, can store data, are highly secure, and are widely used. A card system composed of multiple commonly used subsystems; CPU cards have higher security and are used in a small number of occasions with higher security requirements. Of course, the security of biometrics is even higher.
Multi-information identification carrier: However, with the expansion of the system scale and the requirements for higher-level security and convenience of the system, biometric identification (fingerprints, etc.) with inherent, specific and unique characteristics of the human body, as a more reliable More and more flexible and more convenient authentication and identification methods are used more and more in the card system in combination with card identification, thereby achieving the best combination of high security and return on investment of the entire system. On the other hand, other identification types of information carriers such as RFID electronic tags, vehicle number scanning, various active or passive cards, etc. can also be combined and used in the same system, so that managers and users are no longer limited to one type. Information identification carrier, which greatly realizes the flexibility and convenience of use and management.
1.2 Smart Access Control System
The OPEN smart access control system is an application subsystem under the OPEN one-card system. It refers to the installation of smart card electronic automatic identification systems at the entrances and exits of buildings based on modern electronics and information technology. ) The intelligent management system that implements release, rejection, recording and other operations, its purpose is to effectively control the entry and exit of personnel (items), and record all the details of the entry and exit, and realize the safety management of the entrance and exit.
No matter what kind of non-contact smart card or biometric (fingerprint, etc.) is used in the OPEN access control management system, automated management can be achieved, depending on the capital investment, functional requirements, and matching conditions with other systems.
The OPEN intelligent access control system monitors and manages each controller through a computer. It adopts 485 communication interface and supports TCP/IP protocol. In a system with multiple access control points, a dedicated communication line can be used to form a dedicated system network, and the communication with the computer can be realized by RS232/485 signal mode. It is also possible to use the Lan local area network lines established within the community or modern enterprises and groups to integrate the access control system into the local area network or close to the Internet. There is no need to set up another line network to control different access control in the same system at any place in the world. Point to achieve remote management and control.
Chapter 2 System Requirements Analysis
The current actual situation and your system requirements are summarized as follows:
(1) There is a total of access points.
(2) One one-way access control (swipe in, button out) points; two two-way access control (swipe in, swipe out) points.
(3) The number of authorized cards per door reaches up to one person.
(4) Does certain door swipe card require the machine to display the card number and time at the same time.
(5) Use Mifare1 IC card.
(6) Use dedicated RS485 communication or TCP/IP communication or a combination of TCP/IP and RS485 communication.
(7) Other analysis
Chapter 3 System Design Goals and Principles
3.1 System design goals
OPEN access control management system is based on advanced computer technology, communication technology and non-contact card technology to provide safe and convenient management for access control. The specific goals are:
Holders of a valid card can easily enter and exit the doorway.
People without a card or with an invalid card cannot enter and exit the doorway.
There are emergency measures for abnormal situations.
The detailed entry and exit records of someone at a certain time can be easily inquired through computer software.
Managers can control the access rights of each card at any time.
Economical and reasonable operating costs.
3.2 System design principles Advancement
The construction of the OPEN access control card system must be based on today’s internationally advanced and promising technology that represents the mainstream trend, and the system thus realized can be smoothly upgraded with the development of future information technology. For example, the network communication in the all-in-one card system adopts the internationally popular TCP/IP protocol, the server and workstation adopt the Microsoft Windows operating system, the database adopts Microsoft’s SQL Server large-scale database system, the front-end application program is developed using Delphi, and the system has C/S Combine the platform with B/S.
Practicability: The OPEN access control card system should fully understand and analyze the user’s various management modes and characteristics, and the development of each application system should be fully functional, convenient to use, technologically humanized, economical, reasonable, practical, and efficient. At the same time, targeted designs and flexible solutions can be made for specific needs and actual conditions of on-site engineering.
Security: The design of the OPEN system is highly reliable, and the product has mature and stable performance, ensuring long-term trouble-free operation of the system, ensuring the accuracy, integrity and consistency of the data even after an accident is interrupted, and it can be quickly restored normal. Security can only be ensured by ensuring reliable and stable system hardware. The OPEN software system has strict management and operator authority control. It has alarms and log records of various operations, which effectively prevents internal cheating. The software can cancel the authority of reporting lost cards and blacklisted cards in real time to prevent fraudulent use and abuse of cards, and ensure The security of the entire system is improved.
OPEN system uses encrypted card number (to prevent security vulnerabilities such as duplicate cards and imitation cards)
The OPEN system uses the encryption function of the IC card. The identification of the card is not the serial number of its own card chip but the card number that the user defines and writes in encryption when the system is issuing the card. Each system uses a unique password to encrypt and issue the card. This system reads and writes the card. The device only recognizes the cards issued by the system, completely eliminating the potential safety hazards caused by repeated card serial numbers or low-order repetitions of card serial numbers.
The communication between the OPEN system card reader and the access control host is a self-defined encrypted communication method to prevent unauthorized persons from using other card readers to replace the original card reader to transfer data to the host illegally opening the door.
The card amount encryption password in the OPEN one-card consumption system is set by the user when the system is activated, which effectively prevents illegal recharging and cheating, and effectively guarantees the user’s safety and interests.
Scalability: The OPEN access control card system can not only meet the needs of current users in terms of capacity and functions, but also easy to expand due to the standardization and open compatibility of the system to ensure future expansion and upgrades of users. The system can be added to existing systems at will The control equipment of the new system can also be added to form a larger all-in-one card system.
Chapter 4 System Solution and Technical Description
4.1 System overview
OPEN intelligent access control system refers to an intelligent management system based on modern electronics and information technology that installs automatic identification systems at the entrances and exits of buildings, and implements release, rejection, and recording of people (or objects) entering and exiting.
The purpose of the OPEN access control management system is to effectively control the entry and exit of personnel, and to record all the details of entry and exit to achieve convenient and safe management of entrances and exits, including card issuance, access authorization, real-time monitoring, access query and printing reports, etc.; control machine It can work online or offline; single-door control machine, TCP/IP access control machine, network multi-door machine can be selected for use; practical, standard, enhanced, international, large-capacity access control can be selected according to the use situation; access control The access records can be used as the basis for attendance; the access control machine can also be used as a patrol at the same time, the patrol staff will record the card information when swiping the card but will not open the door; for the community occasions, you can choose the intercom built-in access control machine (high integration design, volume The small is directly fixed and installed in the intercom host of the cell unit door to form a whole or the card reader is built into the intercom host of the cell unit door to form a whole).
4.2 System functions and features
Unique features of OPEN access control management system:
Smart card recognition and fingerprint recognition can be mixed in one system, and the same set of software is managed uniformly, and users can choose different recognition methods according to the security levels of different entrances and exits;
Eliminate crashes (multi-level watchdog circuit design);
The clock and storage adopt the DALLAS chip imported from the United States; to ensure the accuracy of the clock and the stability of the data, there will be no loss of access records (also important for attendance or high-security places), and the card will not be invalid without opening the door (on the motherboard of many other domestic manufacturers) With batteries, the low-cost storage method used is not reliable for data storage. Once the data of the authorized card is lost, it must be re-downloaded to restore to normal). DALLAS memory chips are recognized as reliable memory chips in the world and are widely used in electricity. , Control and military industry;
The host computer includes a back-up power supply design, no additional power supply is required for card readers, electric locks, etc., easy installation and reasonable structure;
The high-end access control system has multiple real-time monitoring functions. Multiple computers (multiple places or different departments) can monitor, manage, and authorize the access control at the same time. Persons with administrative rights can log in to the access control software on any computer in the TCP/IP network. It can monitor and manage the access control points without being fixed on a certain computer. It is suitable for large-scale use occasions such as high security or nested management of headquarters and branches. For detailed function descriptions, please refer to the access control software description section;
The monitoring interface is intuitive and clear at a glance, with personnel entry and exit records and photos displayed. Different colors of each channel represent different states (for example, green represents the door is normally closed, white represents the door is normally opened, yellow represents an alarm has occurred, and red represents communication interruption);
The new generation of community intercom has built-in access control, which is super stable and reliable; the opening authority is written in the card, as long as the card is not damaged, legal personnel can effectively open the door. You can choose to use it offline or online, and have credit card record query;
Practical, standard, enhanced, international, intercom built-in access control can be used comprehensively in one system to achieve the highest cost performance.
OPEN access control system function:
(1) Basic functions
It can control various electric locks.
Different access permissions can be set for different people.
Six time periods can be set in a day, which can strictly control the entry and exit of personnel in each period.
It is possible to set whether the permitted time period is valid on holidays and weekends.
Forcibly open the door, and automatically alarm if the door is not closed over time.
A variety of information records: each time the door is opened, the door card, number, alarm reason, and location.
The door opening delay is adjustable.
Can be used offline or online.
Multi-level watchdog circuit design prevents crashes.
Using American original built-in battery chip, data and clock will never be lost.
(2) Linkage function
Security linkage: When the door is opened (including illegal intrusion, the door lock is broken), the linkage monitoring system is activated to send out real-time alarm information.
Linkage of lights, etc.: When the card is valid, the lights of the corresponding area are automatically turned on
Fire linkage: When a fire alarm occurs, the corresponding area channel is automatically opened
There are three ways to implement this function:
1. The access control point adopts AC220V AC bus power supply, the main power switch controlled by the relay, the normal switch is in the closed state, and the system is normally powered. Once a fire alarm occurs, the alarm signal drives the relay to turn off the power switch, and the doors controlled by this switch are all off. The electricity is turned on automatically. This is the most commonly used, most effective, most reliable and easiest way. The electric lock adopts a normally open electric lock that is switched off when the power is turned off. The access control system can also be equipped with a power bus for full control or according to the partition of the fire signal. To achieve sub-regional control, the schematic diagram of linkage control is as follows:

2. The fire-fighting linkage signal is directly connected to the access control host in the area through wiring. When a fire alarm occurs, all relevant doors are automatically opened. This method requires additional wiring.
3. The fire-fighting linkage signal is input into the access control computer software, and the software controls all doors to be opened. This method requires the software to be running all the time, and the fire-fighting system must provide related interface protocols.
(3) Centralized management
The management center uniformly sets, changes, cancels, and restores personnel access rights.
The management center can remotely control the door to open.
The management center can monitor the status of each door and personnel access in real time.
Can centrally query, print, etc.
(4) Offline operation
The access control host itself has storage and calculation functions, which is equivalent to a small computer. The management center downloads the permission information of this door to the access control host through software, and the access control host can save this information, that is, the PC that does not rely on the management center can automatically To identify, judge, read and write, and record the information of personnel entering and exiting, the PC can send instructions to the access control machine at any time to change personnel permissions or read entry and exit records, etc.
Other features of OPEN access control management system are as follows:
Single door, network multi-door, intercom built-in function hybrid networking can be mixed with all access control machines such as TCP/IP access control machine, unified management
RS485 communication, pure TCP/IP communication, or backbone using TCP/IP, partial RS485 communication is optional, and can be used in combination
Lightning protection design (10KV500A response speed 1-10 nanoseconds)
Adapt to mains voltage fluctuations (switching power supply design, input range AC180V—250V)
Powerful additional functions (alarm, patrol, etc.)
The software is well designed and tempered to meet various needs
Support TCP/IP protocol, Internet management
There are 6 time slots in a single day, Sunday, Saturday, Saturday afternoon, 30 custom holidays, and free combination access control for channels; the universal super access control machine has unlimited access control periods and control numbers.
With door-closing in-position detection, the door-closing status will be automatically checked after unlocking, and a warning signal will be issued when the door-opening delay is exceeded
Possesses the function of dealing with emergencies such as fire, theft, etc.
Emergency button to open the door in special circumstances, computer remote open the door function
Open the door regularly (you can set two time periods to open the door/lock every day, during which there is no need to swipe the card to enter and exit)
Networking and online patrol function, after the patrol card is swiped, only records will be kept but the door/lock will not be opened
Personnel entry and exit records can be used for attendance
Inquiry, report statistics, output, etc. of personnel swiping card access records, alarm events, system management personnel login, etc.
CPU card/IC card/ID(EM) card/electronic label (Mifare, HID, Motorola, TI)/fingerprint recognition mode optional
Central software arming and disarming; on-site swiping card or password arming and disarming
Multiple door opening methods such as card opening, password opening, card plus password opening, etc. can be set and changed at any time through the software
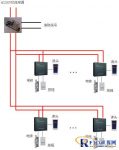
4.3 System structure
Stand-alone management mode: In this mode, a computer manages all doors. The database and management software are installed on the management computer. The management computer connects and manages all access control machines through the RS485 converter or the TCP/IP converter.
Local area network management mode: The local area network management mode is to set up a database server for large-scale access control systems or systems that require sub-regional management. There can be multiple management computer workstations. Each management computer can access the data on the database server together, and pass RS485 or TCP/IP communication method connects and manages access control machines in their respective areas.
Internet management mode: This mode is suitable for remote unified management of network connections such as Internet/GPRS/CDMA/GSM/private networks. There is no local management computer at the access control point, and it is managed by the remote center management workstation through the Internet or wireless communication.

4.4 System workflow
A. The flowchart is as follows:


B. Work flow:
1. The administrator sets basic information such as channels and personnel in the management software.
2. The administrator issues a card to each person and authorizes each person to enter and exit at which doorway and time period.
3. When entering the door, the cardholder uses a non-contact card to sway in front of the card reading area of the access control machine. After the access control machine confirms the identity, open the electric lock to open the door, and the door is closed after the person enters.
4. When going out, the cardholder swipes the card or presses the exit button, the door opens, and when the person goes out, the door closes.
Chapter 5 Equipment Introduction (omitted)
Chapter VI Introduction to Management Software
The OPEN access control system is an integral part of the all-in-one card management system. The program login account must be added by the administrator in the system management program. Operations such as reporting the loss and unhooking should be carried out in the system management program. The main window can monitor the status of each access control point and whether it has alarmed in real time. When an alarm signal occurs, the system automatically pops up an alarm interface.
The main interface of the high-end access control subsystem software is as follows. The main interface of the system is the real-time monitoring interface, which can monitor the status of each door, personnel entry and exit conditions and photos (the photos of personnel can be displayed in an enlarged size). In some special doors or special time periods, it can be realized that after the cardholder swipes the card, the system will display the cardholder’s information and photos and will not open the door temporarily. The duty officer will give the door open signal to allow entry after confirmation.
Multiple real-time monitoring of high-end access control software: Choose OPEN high-end access control software, which has multiple real-time monitoring functions. Multiple terminal computers can monitor the status of each door and real-time personnel access in real time according to levels, regions and nesting. Local real-time monitoring and management of access control points in area A, computer B monitors and manages access control points in area B locally, and multiple simultaneous real-time monitoring and management of access control points in areas A and B can be performed on the computer in headquarters or general control center C at the same time. In addition An administrator with a valid account and password can log in to the OPEN access control software on any D computer in the TCP/IP network, and then they can simultaneously monitor and manage part of the access control points that are authorized in real time (it is possible to authorize the monitoring and management of a part of the access control points in Zone A). Part of the access points in Zone B) or all access points. If someone enters or exits a door in area A, the related multiple monitoring computers A, C, and D can simultaneously display the name, time, photo and other information of the person entering and leaving; if an alarm occurs at a door in A, the relevant Multiple monitoring computers A, C and D computers can simultaneously pop up an alarm processing box, accompanied by voice prompts. The diagram of the multiple real-time monitoring system is as follows:

This high-end function has three major use cases: 1. Nested management of headquarters and branches, each branch independently manages local access control points, and the headquarters performs unified management and control on this; 2. Managers can use their own office computers or other Real-time monitoring, control and management of access points can be completed by using a legal account and password to log in to the access control system on any computer, without having to go to a server or a fixed management computer that communicates with access control hardware; 3. High security such as prisons or banks Locally, in order to prevent omissions, multiple monitoring centers have been established to monitor and manage the access control system simultaneously. Once an intrusion or other alarm occurs, multiple monitoring centers can simultaneously receive the alarm signal in real time to ensure that the alarm is handled in a timely manner.
Access control period: A period of time refers to a passable interval. A day can be divided into six periods, and each period is independent of each other. When authorizing access rights, you can select the time range of authorized personnel in these six periods.
Holiday setting: 30 days of holidays can be preset. And according to the unit system to set whether Sunday, Saturday, and Saturday afternoon are holidays. When authorizing access rights, you can choose whether to allow normal passage during holidays. If a five-day work system is used, Saturday and Sunday are both holidays.
Entry and Exit Authorization: Entry and exit authorization is mainly to set when each person can enter and exit those passages or at which passages to perform patrols (can swipe the card but cannot open the door). You can choose to authorize by personnel or by channel. If authorized by personnel, the personnel will be displayed on the left, the door passage and authorized time allowed for this person are displayed on the right side, and the door passage forbidden by this person is displayed on the right side. Perform the same operation to change the authority of this person. Click the time period to set the specific time period and holidays that the selected person is allowed to pass on the selected channel. Before the specific time is set, the default is to pass at any time.
Electronic map: This interface is for map input and picture replacement or deletion operations. The map supports various picture formats (jpg, bmp, etc.), and the system supports multiple maps.
Access control distribution: The access control distribution is to mark each access control point correspondingly on the corresponding map.
Real-time monitoring: The real-time monitoring of the electronic map mode directly shows the status of each door on the map. The background color of the access control point is red to indicate abnormal communication, green to indicate normal communication, and yellow to indicate that there is an alarm at this point. You can perform operations such as zooming out, zooming in, dragging, slow screen, and original image size for each map.
Channel status: The channel status can be used to query whether the channel is normally open, normally closed or normal, as well as the arming status of the channel and whether it is alarmed or not.
User information: The user’s files can also be briefly searched in the access control subsystem, which is convenient for personnel to check and manage at certain times.
Entry and exit query: The entry and exit query mainly queries the entry and exit records of personnel, and the top is the query condition, which can conveniently query the entry and exit status by number, name, card number and entry and exit time range, and can export the entry and exit records of any day to which day to Excel File.
Alarm query: Alarm query can query all alarm record information by channel, event and time.
System event query: You can query the operation, control and corresponding time of the operator on the access control machine.
For more information, please contact: Shenzhen Oupin Technology Development Co., Ltd.
Shenzhen: 3rd Floor, Building 205, Tairan Science and Technology Park, Chegongmiao, Futian District, Shenzhen
Phone: (0755) 82049788
E-mail: [email protected], [email protected]
[ad_2]



