Intelligent solution for bank network monitoring and management system
[ad_1]
I. Overview
Today’s rapid development of science and technology has brought people into the era of digitization and information in advance. The use of high technology to prevent, deter, and combat crime has gradually occupied an increasingly important leading position in the three major prevention methods (namely, civil defense, control, and technical defense).
The bank is a key security guard unit of the country. It has the characteristics of diverse scales, numerous important facilities, complex entry and exit personnel, and a wide range of management fields. As the main circulation place of currency in today’s society and an important link in national economic operations, it serves the country with its unique functions and advanced technology. All walks of life, its business involves a large amount of cash, securities and valuables. Banks have also been the focus of various criminals. Since the birth of modern banks, theft and anti-theft, robbery and anti-robbery, fraud and anti-fraud, corruption and anti-corruption have also developed simultaneously with the development of the banking industry. At present, domestic criminal activities against banks are on the rise, and criminal methods and methods are gradually diversified, violent, and intelligent. It has become urgent to comprehensively strengthen and update the current bank security system to adapt to the transformation of banking mechanisms and business development.
This article will take the Bank of China Shenzhen branch network monitoring system project as an example to discuss the needs and solutions of the financial system intranet monitoring.
2. Demand analysis
After years of development, the Shenzhen branch of Bank of China Co., Ltd. has continuously expanded its business volume. Branches under jurisdiction at all levels, secondary branches, unmanned self-service banks, and ATM systems have reduced the work intensity of staff and improved work efficiency. With the deepening of the shareholding system reform of the Bank of China Limited, higher requirements have been placed on the internal control and management of various tasks of the various functional departments of the Shenzhen branch. At the same time, how to better ensure the safe operation of sub-branches and off-bank ATM systems is also critical to the bank. The security system puts forward more stringent requirements.
From strengthening internal management and meeting new security needs, promoting the implementation of the State Council’s “Three Preventions and One Protection” work, and realizing the specific requirements of the financial industry’s modernization and efficient management, Bank of China Shenzhen Branch puts forward a combination of the current level of security industry development and use Advanced technology, adopting safe and reliable design schemes, carry out digital transformation of the monitoring system of the whole branch, realize centralized control of security system and functional management, so as to improve the level of safety prevention and comprehensive guarantee management of the whole bank. Based on this, Tianyinglong Technology Co., Ltd. proposes to use branches as the network hub of the entire system, branch lines as secondary network nodes, and deposit points and branch offices as tertiary network nodes to establish a safe, efficient, and advanced ” TYL-NMS” intelligent security network management system remote network monitoring system.
In order to reduce the work load of grassroots personnel and improve the bank’s comprehensive safety management level, the following steps will be taken:
(1) The management authority of the digital video surveillance system is transferred from the branch to the branch center: the municipal secondary branch science and technology management department will take the lead to establish a networked monitoring center for the secondary branch of the city. Conduct centralized monitoring and management with the digital image monitoring system and alarm system of the local treasury.
(2) Integrate professional alarm reception and management functions of various access control systems: increase the integration of other security monitoring systems. In addition to the integration of the original 110 alarm system that has been built, special attention is paid to the construction and integration of various access control management systems , Including two-door interactive interlocking access control management system for business outlets, off-line ATM machine equipment room access control management system, self-service equipment room access control management system, important machine room access control access management system and vault multi-fingerprint access control management system.
(3) Expand the scope of monitoring to mobile targets and network with urban security monitoring: increase the monitoring and management of mobile cash transport vehicles and library bag escort vehicles, and increase the integration of GIS geographic information systems and GPS positioning systems to facilitate mobile transportation Monitoring of banknote vehicles.
Three, design ideas
With the completion or near completion of the digitization of the bank’s monitoring system, the bank’s need for an integrated monitoring system has become very urgent. However, according to the author’s research on security and technology departments of many banks, as well as the research on the existing systems of banks, many products and solutions on the market can no longer meet new business needs. The author believes that the core part of a system is its architecture design and values:
The system structure determines whether the system itself can adapt to changes in the bank’s monitoring scale and scale, and whether it can respond quickly and seamlessly integrate into the original system when user needs change. The architecture also determines whether a system will be eliminated in a short period of time, or it can continue to improve itself with the development of information, video, intelligence, and security technology.
Values determine whether the system can truly provide customers with what they need. And whether it can meet the ever-evolving business needs of customers. He also decides whether every function and every feature realized by the system is to realize more business value, or whether it is just for function and function, product and product.
In summary, the “TYL-NMS” intelligent security network management system developed by Shenzhen Tianyinglong Technology Co., Ltd. adopts the current advanced J2EE architecture in the IT industry. J2EE has the characteristics of cross-platform, high scalability, and easy scalability. , Known by the industry as the preferred architecture for large-scale enterprise-level applications and mission-critical applications in the world.
From the perspective of the bank, the ultimate goal of the integrated management system should be to provide a platform. Under the management of this platform, all organizational structures (branch, sub-branch, outlets, etc.), equipment (monitoring equipment, alarm equipment, storage All managed objects such as equipment, external equipment), mainframes, systems, etc. should be combined into one organism, coordinating and serving the bank’s monitoring and management objectives. In other words, to the bank, all the devices and systems in the platform are just like the same omnipotent and expandable device that provides the required services for various institutions and personnel of the bank. The addition of each function module and the use of functions follow this idea. Whether it is organizational structure management, permission setting, real-time monitoring, recording, storage, playback, retrieval, alarm, access control, equipment inspection, fault handling, and all other functions that may be added and expanded, they are centralized, unified, and hierarchical. They are designed and managed by the method, in accordance with the authority and requirements of the operator, in actual use, they can cover all, part, and specific related equipment of the system, thereby providing extremely high management value and individual needs to meet.
Four, system architecture design and principle
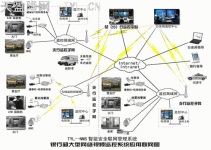
According to the analysis of the requirements of the computer room monitoring system by the above financial system, the “TYL-NMS” intelligent security network management system builds a financial monitoring system in the following way. And subdivide it into monitoring front-end, communication network, and monitoring center.
The overall structure of the bank network monitoring and management system is as follows:

As shown in the figure, let’s analyze how the system meets the above requirements.
(1) On-site monitoring
For the on-site monitoring of ATM machines and self-service banks, the original hardware equipment is used. Among them, the PC-based DVR built-in software is recommended to be replaced with the “TYL-NMS” intelligent security network management system. If the board does not support software replacement, you can refer to the planning and design The implementation steps are modified. For the treasury, it is necessary to add access control equipment, alarm equipment and a dedicated field device server software for bank network monitoring installed in the digital monitoring host: “TYL-NMS” intelligent security network management system, which allows the on-site monitoring host to collect images, voice, and alarm The data of the host and the access controller. The self-service DVR host supports external intercom devices and alarm boxes. The alarm box collects the button signals for help and intercom request, and then the alarm box outputs RS232 signals to connect to the DVR host to achieve intercom and alarm with the center. For embedded DVR, as long as the manufacturer provides a development kit, the software developer can write the corresponding driver to achieve direct access without modification.
For PC-based DVR, the image and voice signal is directly connected to the built-in image and voice compression card of the digital surveillance host. The alarm signal is collected through an external alarm interface box. The alarm interface box is connected to the host through an RS232 signal, and the data output by the alarm host is collected by obtaining its protocol and controlled for arming and disarming.
If there is an alarm host on site, and RS232 communication interface and interface protocol are provided, we can also directly use the RS232 interface of the monitoring host to connect to the original alarm host to realize its data collection.
On-site configuration of a single-door access controller, the access controller is connected to the fingerprint machine, electric lock, and exit button. The access controller transmits the data to the protocol converter through the RS485 bus, and the protocol converter converts the data to the RS232 signal and then The monitoring host is connected to realize the control and management of the access control system. In actual use, there must be two managers on the spot to perform fingerprint identification through the fingerprint machine. After the data downloaded and saved in the controller are compared with the data saved in the controller, the vault door can be opened. During fingerprint recognition, the system can set up linkage to take pictures. When an abnormal alarm occurs, the system can remotely automatically close the door and prohibit the on-site door opening. The on-site monitoring host can be connected with an external intercom device to realize intercom with the center.
(2) Central master control
The center must be equipped with a main control workstation and install the “TYL-NMS” intelligent security network management system main control software. This main control software can realize network monitoring, control, query, browsing, burning, electronic recording of all digital image equipment in the network Map alarm and other functions, support remote arming and disarming operations and real-time monitoring of the alarm system, support remote real-time access monitoring and remote switch control of the access control system, with the highest control and management authority, built-in short message alarm software module and external short message alarm The module realizes that when an alarm occurs, it automatically sends an alarm message to the designated mobile phone, and realizes the intercom command function with an on-site intercom by connecting an intercom headset. The main control software of the basic specifications can monitor, query and manage the maximum 64-channel image data of various digital image equipment, and the management of alarm defense zone data and fingerprint access control data are not limited. Support short message alarm. It can manage the host computer that is installed with the bank’s field device server management software remotely.
(3) Central sub-control
The center selects multiple sub-control workstations according to needs, and all install the “TYL-NMS” intelligent security network management system sub-control software license. This software is equivalent to the C/S sub-control terminal, and the basic functions are the same as the main control software.
(4) Central network digital matrix and TV wall control
The center can configure the network digital matrix host according to the needs, built-in “TYL-NMS” intelligent security network management system network digital matrix software, this software can receive the network audio and video compression data stream transmitted by the remote DVR/DVS, and manage the local decoding card Or the matrix card outputs single-picture and composite picture image data to the local display and external TV wall. The current single-machine supports up to 6 4-channel decoding cards or 16 2-channel matrix cards. Provides local display control, built-in video decoding card, matrix card output control, provides an operation interface for analog matrix mutual control (supports keyboard simulation control), provides electronic maps, grouping, patrol, linkage and other control methods, provides matrix Card output control in compound mode (single picture, multi picture, picture-in-picture).
The software also supports mutual control through serial communication and traditional analog matrix. It supports direct control of traditional matrix through PC keyboard and mouse and direct control of digital matrix output through traditional matrix keyboard.
(5) Central system management service
The center must be equipped with a system management server, and install the “TYL-NMS” intelligent security networked management system management server software. The software module can be used for the personnel of the entire system, remote digital image equipment, remote access control equipment, remote alarm equipment, and remote access server. Various sampling parameters, linkage strategy settings, and electronic maps are centrally configured and managed, while real-time access control and management of all clients (including C/S and B/S methods) are realized. When many monitoring sites do not have fixed IP addresses but only dynamic IP addresses, the central system management server (with fixed IP) can also provide domain name resolution services related functions to realize networked monitoring based on the public network.
(6) Central WEB client software download service
The center configures WEB client software according to needs, installs “TYL-NMS” intelligent security network management system, which supports remote client access to download WEB controls, and then implements basic client software functions, such as monitoring and pan-tilt control, locally by WEB , Video query, alarm query, access control query, etc., but cannot achieve local video downloading, burning and other functions.
(7) Central streaming media forwarding service
When the network bandwidth between the center and the site is limited (less than 2M), in order to satisfy the simultaneous access of the center or other remote customers to the equipment in the remote monitoring site, the center also needs to configure a streaming media forwarding server with a built-in “TYL-NMS” intelligent security network management system stream Media forwarding server software is used for streaming media forwarding. The purpose of setting up a streaming media forwarding server is to alleviate the area where the network bandwidth is tight. Access to the video server in this area is all forwarded through the streaming media forwarding server software module, so that the video service of the video server only occupies one channel. The multi-level setting of the streaming media management software module can improve the efficiency of response access, and the setting of the streaming media forwarding server software module can be planned reasonably, so as to obtain a higher bandwidth utilization rate for less time. According to the actual situation, the secondary streaming media forwarding server and software can also be installed at the monitoring site to realize the secondary streaming media data forwarding function in the WAN environment, supporting dual network cards and cross-network segment application environments, and bundled with the central streaming media forwarding server software.
(8) Central network storage management service
In order to ensure data security, the center can also be equipped with a network storage server, built-in “TYL-NMS” intelligent security network management system network storage management server software, realizing remote real-time recording of all images, alarm recording, central centralized backup and subsequent retrieval, query, storage The medium can be an ordinary hard disk, a disk array or a tape library.
V. Conclusion
The network monitoring system project of Bank of China Co., Ltd. Shenzhen Branch has successfully passed the acceptance by the Municipal Public Security Bureau’s acceptance expert group. And won the unanimous praise of the acceptance expert group. The members of the acceptance expert group stated that the smooth completion of the project and the acceptance of the project provided a good reference for the next step in the transformation and upgrading of the city’s financial system security networked monitoring project, and was of great significance to the improvement of Shenzhen’s financial security.
[ad_2]