Networked anti-theft system for valuables
[ad_1]
1 System introduction
With the continuous penetration of scientific and technological innovation concepts, the demand for asset anti-theft monitoring systems in the security industry has become increasingly diversified, and the requirements for the technological content of security systems have become higher and higher. Some conventional technical preventive measures can no longer meet the increasing demands of users.
The asset anti-theft monitoring system uses wireless radio frequency technology, wireless sensor technology, wireless communication technology, digital video technology and other current most advanced core technologies of the Internet of Things, and provides users with assets through real-time perception of the location, posture, and movement status of important assets. Multi-scene 360-degree real-time monitoring and multi-means timely alarm.
The system can provide security protection for hundreds of assets at the same time, and realize direct and active monitoring of assets through real-time perception, real-time response, and real-time alarm. The system fully considers customer needs and application environment, and is easy to install, easy to operate, and flexible to use. It is of great significance for the expansion of security technology and the improvement of the reliability and effectiveness of the security system, and it will also bring significant benefits to users who implement and use this system!
Compared with traditional anti-theft alarm methods such as infrared beam, door sensor, and video, this system has the following advantages:
Wireless transmission, simple wiring;
The label is small and easy to conceal;
Easy to install, just stick to the monitored asset;
Active monitoring, advanced and reliable technology, minimize the occurrence of false alarms;
Partition fortification, easy arming and disarming, and asset monitoring can be set arbitrarily;
Video linkage, when an alarm is triggered, the surveillance camera can be immediately mobilized to view the video in real time;
Automatic inventory, the monitored assets will automatically upload data to facilitate real-time data statistics;
With strong scalability, it can realize comprehensive management of personnel and assets.
2 System characteristics
Directly monitor assets, management is more timely, accurate and effective;
Real-time monitoring and active alarm, alarm, notice and record the first time an event occurs, which can effectively prevent the occurrence of illegal behavior;
No restrictions on personnel entry and exit, normal personnel activities are allowed, only assets are monitored, and personnel interference, false alarms and monitoring failures are reduced;
Advanced wireless radio frequency technology and wireless sensing technology to achieve wireless transmission of asset status signals;
Use frequency hopping communication to prevent interference from other external signals;
Advanced AES encryption technology to ensure the security of information and data;
Advanced posture, vibration, and position recognition algorithms to prevent false alarms;
The system proactively alarms, which can avoid searching through video retrospectively afterwards;
A single host can monitor 300 cards, realizing all-round monitoring of assets;
It can realize independent monitoring and management of a single asset, making asset monitoring and management more flexible and more widely used
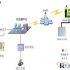
3 System principle
Composed of “electronic tags” and “signal transceivers”, it is equivalent to the human body’s nervous system, realizing the real-time perception and transmission and collection functions of various position and status information.
Assemble the corresponding asset electronic tags for the objects, such as close to the cultural relics, close to the wall of the box, hidden in the accessories of the cultural relics; install signal transceivers in specific areas for remote real-time reception of electronic tag signals, such as installation Installed on the eaves, on the wall or in the ceiling; information management and services are completed by a specially developed software system, which can be understood as the human brain, and can conduct comprehensive management and intelligent analysis of the collected information and data, and according to actual management needs Construct various intelligent management and service methods such as real-time monitoring, intelligent alarm and comprehensive management and control.
4 Engineering construction
Install signal receivers in important venues, which can be installed on the eaves, on the wall or in the ceiling, so that the signal covers important cultural relics that need to be monitored.

5 System function
5.1 Smart anti-theft
Intelligent anti-theft mainly refers to attaching electronic tags to the cultural relics in the museum, the boxes where the cultural relics are stored, doors and windows, etc., and direct and accurate anti-theft monitoring of the state and location of the objects. Once the following abnormalities occur in the object, the system will detect it as soon as possible and activate a smart alarm (see smart alarm function):
(1) Vibration;
(2) Leaving the designated area;
(3) The electronic label is detached.
5.2 Smart alert
The intelligent alarm function consists of two parts: alarm rule setting, intelligent matching and alarm:
(1) Alarm rule setting-management personnel preset various management rules in the system (including abnormal state of objects, partition defense rules, security work arrangements, personnel authorization rules, etc., see various specific management functions), various violations The alarm methods corresponding to the situation (including mobile phone text messages, monitoring system pop-up windows, on-site sound and light alarms, etc.), and alarm removal rules (including time-limited release, designated personnel on-site release, system operation release, etc.).
(2) Intelligent matching and alerting-the system will intelligently match the situation detected in real time with preset alert rules, filter out violations, and activate corresponding alert methods, such as:
The system pops up an alarm window, and the location and prompt of the alarm source are displayed on the electronic map. Click the alarm icon to view the details and the nearby surveillance video screen.
Acoustic and visual alarms are activated on site.
According to preset alarm rules, send alarm messages to relevant personnel.
5.3 Video linkage
In addition to traditional video surveillance functions, as described in Smart Alarm, when the system sends out an alarm message, it automatically pops up the corresponding video surveillance screen and automatically starts on-site video recording. Avoid the shortcomings that the monitoring personnel cannot perform comprehensive and effective video surveillance due to the small video images of each channel after the screen is split.
5.4 Smart authorization
Smart authorization includes work authorization and access authorization.
(1) Work authorization: Managers can authorize designated personnel in the system (more than one person can be at the same time) to have the authority to maintain the designated objects. Personnel only need to wear their own electronic tag card to perform maintenance operations on the designated object site. The system will recognize it as a legal operation and will not trigger an intelligent alarm. At the same time, it will automatically generate work records and save them in the system log.
(2) Access control authorization: similar to work authorization, it enables authorized personnel to enter and exit designated areas without triggering an intelligent alarm, and at the same time generate personnel entry and exit records.
In the above cases, the corresponding personnel can also be notified by SMS according to preset rules.
5.5 Smart Arming
The system provides intelligent arming setting function:
(1) Partition defense: The manager can separately deploy any designated area, which is convenient for management and maintenance work.
(2) Time-sharing deployment: Managers can pre-set the deployment time, which is convenient for forming an orderly management system.
(3) State-by-state defense: The manager can set the specific state of the designated object to achieve a flexible and practical monitoring and defense mode.For example, there is no need for vibration monitoring for A cultural relic, only tilt monitoring for B cultural relic, and only position monitoring for C cultural relic.
6 Operating model
Operation model 1: Cooperate with security companies to launch dual anti-theft operation products, install active anti-theft systems for owners of fixed locations, increase the cost of key monitoring objects, and collect monthly value-added rents based on the number of identification cards to achieve value-added benefits.
Operation mode 2: Cooperate with the system integrator to upgrade the existing single anti-theft solution project, and cooperate by collecting the initial installation fee in the early stage and paying the agreed equipment rent every month.
Operation mode 3: Direct sales mode, directly find similar museum units to cooperate, adopt active anti-theft management for valuables during the exhibition, and cooperate in the way of collecting deposits and calculating rents on a daily basis.
[ad_2]