Personnel and asset management solutions (software)
[ad_1]
1. System overview
1. Project background
With the vigorous development of high technology, intelligent management has entered people’s social life. Intelligent buildings have emerged to meet the needs of the information age. As buildings and office environments used across the centuries, they must be functional. Meet current and future development needs and become a base for cultural and economic development.
The inductive IC card access management control system based on radio frequency automatic identification (RFID) technology (access control system for short) has multiple functions such as door access control, real-time monitoring, security and anti-theft alarm, etc. It mainly facilitates the access of internal employees and prevents outsiders The random entry and exit of personnel not only facilitates internal management, but also enhances internal security, thereby providing users with an efficient and economical working environment. It has realized communication automation (CA), office automation (OA) and management automation (BA) in terms of functions. It is based on the integrated wiring system and the computer network as a bridge to fully realize the integrated management of communication systems and office automation systems.
As an advanced high-tech technical prevention and management method, the access control system has been widely used in scientific research, industry, museums, hotels, shopping malls, medical surveillance, banks, prisons, etc. in some economically developed countries and regions, especially because of the system itself It has the characteristics of concealment and timeliness, and it is more and more widely used in many fields.
For many companies, resources exist in various forms, which can include production materials, equipment, vehicles, telephone poles, manned wells, cables, etc., with harsh environments, scattered locations, small size, high value, and easy flow. Characteristics, the management of these resources is really a headache. In order to find (or inventory) the location of these resources and understand their status, companies often waste a lot of precious time and resources.
The resource management and tracking system based on RFID technology uses RFID tags, readers and software to monitor corporate resources, so as to realize comprehensive visibility of corporate resources and transparency of information. Allow users to more refined asset management, maximize the utilization of resources, so as to ensure that those expensive resources can be obtained anytime and anywhere when they are needed. Implement resource management in every aspect of enterprise operations, help companies minimize operating costs and risks, increase profitability, and enhance comprehensive competitiveness.
2. Software requirements analysis
This system manages the main entrances and exits of the laboratory. The staff and visitors who enter and exit the laboratory must enter and exit the corresponding doors under the premise of the authorization of this system. The software management requirements are as follows:
l Make basic settings for the system;
l Manage and maintain laboratory employee information;
l Manage and maintain visitor information;
l Manage and maintain the status of each access control card reader;
l Issue ID cards to laboratory staff and visitors;
l Recycling and reporting the loss of ID cards;
l The access authority of each ID card can be set according to the time period;
l According to the information returned by the card reader, record the access status of the corresponding door of the ID card: including time, card number, door number, entry and exit, whether it is an employee or a visitor, the current card is valid or expired time and other information;
l Distinguish the trust level of visitors, whether their card is valid for one entry and exit, or for multiple entries and exits. This distinction can facilitate the needs of visitors who need to leave the building temporarily and come back;
l Record which internal personnel visited by the visitor;
l After the system recognizes the card user, it will display the user’s identity information and welcome message on the monitor next to it;
l Record accidental visits, including personnel entering an unauthorized area or entering the laboratory after the card expires;
l Record the flow of ID cards;
l You can query the history access records of all ID cards and give corresponding reports;
l It can count the visits of various personnel by time period;
l Public information such as announcements, notifications, news can be displayed on the entrance display, and PPT, movies, documents and other information provided by the user can be dynamically played;
l Functions required by other customers.
The requirements for asset management are as follows:
l Basic information of managed assets;
l Bind, change, and cancel the RFID number of each asset;
l Count assets, and give a report on the status of asset inventories;
l Monitor the flow of assets;
l Functions required by other customers.
3. System Architecture
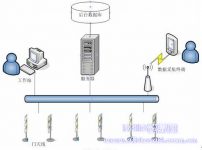
In the design of the system architecture, a three-tier system is used to divide the entire system. in:
1) Data collection layer: This layer is directly connected with each card reader to collect the data returned by the card reader. In the design, data proxy technology is adopted. All data interaction with the card reader is filtered by this layer and then passed to the database layer. This can reduce the redundant data of the database and reduce the burden on the management application layer.
2) Database layer: This layer uses Microsoft’s SQL SERVER2000 database system, which can accurately store large-capacity data in real time. At the same time, a data security and backup mechanism is set up to ensure that the data is accessed within the authorized scope, while also ensuring that the data can be restored in time in the event of an accident in the system.
3) Management application layer: This layer is the main application presentation layer of the system, and all functions that directly interact with management users are distributed in this layer. Including system management, ID card management, personnel management, card issuance, card recovery, card loss reporting, query statistics, etc.

System architecture diagram
2. The overall design of the system
1. Design principles
The principles for the design of this software system are:
1) Openness
In order for customers to connect to other modules or extend the ID card management scope in the future, this system should be an open system, and it should provide standard data interfaces, network interfaces, system and application software interfaces. Only in this way can the customer’s investment be fully protected, and the smooth upgrade and transformation of the customer in the future can be ensured. The characteristics of system openness are:
l Good scalability and flexibility;
l Strong compatibility and portability of application software;
l Good maintainability and long life cycle.
2) Modularity
The system must be developed in strict accordance with the modular structure to meet the versatility and interchangeability. Therefore, the system adopts a modular design and a distributed implementation strategy.
3) Advancement
The system should be in line with the trend of technological development, and an expandable platform should be established to protect the connection between the early stage project and the subsequent advanced technology, so that the system is advanced.
4) High efficiency
As an application system, we must provide customers with an efficient and practical software environment, so that customers feel that the application of such a management system can truly improve management efficiency and effectiveness.
5) Reliability
For any application system, the reliability of its stable operation is very important, and the customer’s work must not be delayed because of the system failure. This system adopts measures such as independent data agency and timely data backup to ensure the stability and reliability of the system.
2. System selection
Server: Windows Server 2003
Workstation: Windows XP
Development tools: Microsoft Visual Studio 2005
Development language: Visual C#
Database: Microsoft SQL Server 2005
3. Software standards
In order to ensure the integrity of the system and meet the above requirements, the system adopts a large number of information management standards, communication protocols, software integration modules, and so on. The third-party standards adopted by the system are listed as follows:
1) Windows 32—All servers and workstations in this system use Microsoft’s Windows 32-bit operating platform. Because of the use of Microsoft’s Windows interface, the network management and selected application software are all open.
2) ADO (ActiveX Data Object) compatible database, application software adopts standard database exchange and connection format.
3) API (Application Programming Interface). API is a number of software modules, compiled by various system supply companies, these software modules are used to exchange data with other subsystems. Through API, each system does not need to have a clear understanding of the format of other system databases and detailed instruction format. Because each system communicates with a set of public function calls in the API, and each system only needs to write software in accordance with these public function call formats, it can ignore the complex instructions in each system, and the API will translate it on its behalf.
4) OLE-Microsoft’s object link embedding OLE (the most advanced data exchange technology) has become the most common standard method in the software industry and Microsoft.
5) COM/DCOM-common control model/distributed common control model, Microsoft’s control definition standard-control is composed of standardized data and internal definitions. This feature makes it very easy to exchange data in applications through programming.
4. Network standards
1) Ethernet–IEEE802.3 (10/100Base-T): The most advanced and popular network solution in the world at present is an industry standard widely adopted and has been successfully verified many times. Support multiple transmission media, including UTP/STP, coaxial cable, optical fiber and wireless. The transmission rate of the network is 10MB or 100MB (adaptive) and supports 1G bit (Gigabit Ethernet). A large number of newly launched network products reduce network costs and ensure that the network system adapts to different situations under different installations.
2 TCP/IP: Transmission Control Protocol/INTERNET Protocol, this protocol standard on Ethernet is used to allow data transmission, tunneling and routing. It provides the most basic data information transmission standard on INTERNET/INTRANET.
The technologies and standards mentioned above will be applied to this system to ensure the completion of system operation data, access and other defined system functions.

System structure function diagram
3. Personnel Management Subsystem
The personnel management subsystem mainly manages the control of internal and external personnel’s access to each door, and achieves the effect of management and monitoring through the setting of cards and personnel identities. In addition to the real-time control effect display, there are also combinations of various conditions that are provided to the administrator to maximize the convenience of the administrator to understand the visits of personnel.
1. Basic settings
1) Personnel management
Management information, including internal staff and visitors. You can enter, modify, and delete personnel information. Visitors have a trust level and can be set to enter and exit once with their card or allow multiple entries and exits. However, the temporary card used by the visitors must be set with a valid time, so that the system prompts the visitors to return the card in time.
2) Card management
Register all RFID card information in the system.
3) Issuing cards
Bind the person with the corresponding ID card, and the card number is the person’s identity in the system.
4) Recycle card
When the employee resigns or the visitor returns the card, the binding between the employee and the card is released.
5) Report loss card
After a card is lost, the card is set to become invalid, and the card can no longer pass through any doors.
2. Access control management
1) Door controller
Set the basic information of the door controller, including location, code, etc.
2) Identify echo
When the card user passes through the card reader, after the card reader recognizes the user’s identity, the card user’s identity information and photos will be displayed on the display next to the card reader, and a welcome message will be sent out by voice.
3) Time period setting
Set several basic time periods, such as working hours, off working hours, and holidays for use when setting access permissions. In addition, you can also directly enter the specific time period when setting the specific settings.
4) Real-time view
Display all access control statuses managed in the system, as well as the records of recent access to each door.
5) Responding to illegal entry
After the door controller detects the illegal entry, it sends an illegal entry message to the system. The system records the information and sends out a sound warning to remind the security or the administrator to check the illegal entry.
3. Query statistics
1) Access query and report
You can query historical access records based on the combination of personnel’s name, time, door number, etc., and the query results can be printed out.
2) Abnormal situation query and report
Abnormal access records can be inquired based on the combination of personnel’s name, time, door number, etc., and the result of the inquiry can be printed out.
3) Access statistics report
According to needs, statistical reports or charts can be given according to different conditions such as time, department, and door number, and the statistical results can be printed out.
4) Inquiry about the flow of a single card
According to the visit records of a certain card in a period of time, it is possible to track the activity route of a certain card (that is, a person) in a period of time.
4. System Management
1) Coding table management
Manage various standard coding dictionaries used in this system, such as department table, holiday table, asset category, etc.
2) User management
Manage user accounts that log in to the system, and assign different user roles according to different user types.
3) User role
According to the different types of users who log in to the system, different user roles are set. It may be a system administrator, security guard, duty manager, etc. They can all log in to the system, but the available functions and the data viewed are different, so different roles need to be set for different function permissions and data viewing permissions.
4) Personnel role
Set up different personnel roles according to the types of personnel who may enter and exit the door, and set different access rights with these roles. When a person is bound to a role, the person has access to this role.
5) Public information display
Set up a monitor at the entrance, and the system controls and displays some public information, such as announcements, news, and welcome information to guests. In addition, according to needs, other introduction information such as PPT, movies, and documents made by the user can also be displayed.
5. Data Agency
1) Read the data returned by the reader
When a card passes through the range of the card reader and the card reader is triggered to read the card, the card reader will send the card information and the door serial number information to the data agent. The data agent records this event, and at the same time searches the corresponding card number and door controller number in the database, returns information on whether the card and door match according to the matching relationship set by the system, and sends the corresponding instruction (the authentication passes the green light, otherwise it is red Light) to the door controller.
4. Fixed asset management subsystem
Fixed asset management based on RFID technology can save time and human resource costs, reduce workload and reduce the probability of errors. It can provide immediate feedback on the inventory situation when inventorying assets, and automatically prompt for missing inventory when inventory is in deficit, so that inventory can be completed more quickly. Users can accurately query the location and status of each fixed asset. Maintain and maintain the corresponding assets in a timely manner, thereby reducing the maintenance costs of fixed assets. Therefore, the application of RFID technology for enterprise fixed asset management can ultimately improve the management level of the enterprise and the efficiency of its asset operation.
1. Asset Management
1) Asset information management
Manage asset information, including asset code, asset name, category, purchase time, value and other information. You can enter, modify, and delete asset information. Assets can have a containment relationship. For example, a cabinet is an asset, and several servers in the cabinet are also assets. However, the cabinet can contain servers. For assets such as servers, the parent asset is defined as the cabinet.
2) Card management
Register all RFID card information in the system.
3) Issuing cards
Bind the asset with the corresponding ID card, then the card number is the identity of the asset in the system.
4) Recycle card
When the asset is scrapped or sold, the binding between the asset and the card is released.
5) Report lost card
After the card on a certain asset is lost, the card is set to become invalid.
6) Inventory of assets
Count all or part of the assets in the system. The financial department shall formulate an inventory plan, listing the scope of assets to be inventoryed. The system automatically generates an inventory list according to inventory requirements and forwards it to the physical management department. Under its unified deployment, the asset use department will take a physical inventory of the fixed assets within the scope. In the inventory process, first check whether the information recorded in the electronic label is consistent with the actual situation (such as location, department of use, etc.).
The specific process is that the inventory personnel use the handheld to obtain RFID information and check the specific conditions of the equipment, and then the handheld returns the inventory information to the system, and the relevant data is automatically entered into the inventory list established in advance. Inconsistent data must first find out the reason, and then make corrections. The inventory information table is summarized by the system and sent to the finance department, which will check the information in the fixed asset database with the inventory information to verify the conformity of the accounts.
After the inventory is completed, the system automatically compares the inventory plan with the actual inventory, and lists the data that does not match the actual account for reference for correction.
7) Asset flow management
Set up a card reader at the entrance and exit of fixed assets to read the movement of fixed assets, such as moving out from door A or moving in from door B. List the change information to the asset manager for confirmation. After the administrator confirms, modify the location information of the corresponding asset.
5. Description of Microsoft .NET Development Tools
This system uses Microsoft’s VS.Net 2005 as the main development tool.
This version of Visual Studio 2005 and .NET Framework 2.0 has made significant progress in all aspects of application development. First of all, Visual Studio 2005 adjusts the software development experience according to the personal needs of the developers and sets new standards for the work efficiency of developers. This “personalized work efficiency” will provide corresponding functions in the development environment and the .NET Framework class library to help developers overcome their most pressing difficulties in the least amount of time. Second, Visual Studio 2005 enables developers to apply existing skills in a wider range of application development scenarios through better integration with Microsoft Office System and SQL Server 2005. Finally, Visual Studio 2005 will provide a set of new tools and features to meet the current large-scale enterprise application development needs.
The central content of Visual Studio 2005 includes:
1) “language” language and IDE work efficiency.
As part of the four languages of Visual Studio (Visual Basic, Visual C++, Visual C#, and Visual J#), Microsoft has built a unique feature for each of its voices. This language innovation will enrich the programming experience of each developer group without sacrificing existing language features and interoperability. The functions displayed through language innovation will be embodied by the IDE, and provide personalized work efficiency for all developer groups.
2) Microsoft .NET Framework.
NET Framework 2.0 will introduce enhancements in the .NET Framework class library. Through new controls and designer functions, Windows client application development will be simplified, and the introduction of “Click Once” technology will significantly simplify Windows client application deployment. Other enhancements include more effective ADO.NET data access, support for the latest Web Service standards, and extended functions for device-based development.
3) SQL Server 2005 solution development.
SQL Server 2005 integrates the development and debugging of database objects into the Visual Studio 2005 development environment, allowing developers to use the same tools they currently use to write managed components and applications to generate and deploy database objects.
4) Enterprise development and lifetime support.
Microsoft plans to provide improved support for architects and enterprise developers in the 2005 version. The new tools will provide enhanced project analysis and design, software configuration management and deployment, and a scalable, new build engine to ensure that Microsoft developer tools can span the application lifetime.
Six, SQL SERVER database description
The database of this system adopts SQL Server 2005 of Microsoft Corporation. As Microsoft’s next-generation data management and analysis software, SQL Server 2005 helps simplify the creation, deployment, and management of enterprise data and analysis applications, and achieve significant improvements in solution scalability, availability, and security.
SQL Server 2005, built on the technical advantages of SQL Server 2000, will provide an integrated information management solution that can help organizations of any size:
1) Create and deploy more scalable, reliable and secure enterprise-level applications.
2) Reduce the complexity of database application creation, deployment and management, thereby maximizing IT efficiency.
3) Rely on the rich, flexible and modern development environment that can be used to create more secure database applications to enhance the work efficiency of developers.
4) Achieve data sharing across multiple platforms, applications and devices, thereby simplifying the connection between internal systems and external systems.
5) Realize powerful and integrated business intelligence solutions, so as to promote scientific decision-making and improve work efficiency throughout the enterprise.
6) Control the level of costs without sacrificing performance, availability or scalability.
The major improvements achieved by SQL Server 2005 for enterprise data management are mainly reflected in the following aspects:
1) Availability.
Investments in high-availability technologies, complementary backup and recovery functions, and replication enhancements will help enterprises create and deploy highly reliable application solutions. Innovative and highly available features such as database mirroring, failover clustering, and improved online operations can keep downtime to a minimum and help ensure that critical enterprise systems are accessible at all times.
2) Scalability.
Scaling improvements such as table partitioning, snapshot isolation, and 64-bit support will allow you to use SQL Server 2005 to create and deploy the most demanding applications. The partitioning function for large data tables and indexes greatly improves the query operation of very large databases.
3) Security.
Enhanced features such as “default security assurance” settings, database encryption, and improved security models help provide a high level of security for enterprise data.
4) Ease of management.
The new management tool suite, self-adjusting capabilities and powerful new programming model will allow database administrators to flexibly control the daily operation of the database. Improvements to the SQL Profiler and other tools can also help database administrators adjust the server to optimal performance. These improved features will allow database administrators to free themselves from daily database operations and concentrate on more valuable tasks such as database architecture design.
5) Interoperability.
The technological advancement achieved by SQL Server 2005 allows you to integrate and connect relatively independent applications and databases within an expanding enterprise scope, thereby realizing the goal of maximizing the investment benefits of new and existing systems. SQL Server 2005 can provide high-level support for industry standards, Web services, and Microsoft .NET Framework, and on this basis, it can achieve interoperability with multiple platforms, applications, and devices. SQL Server is highly integrated with other Microsoft software products (from the Microsoft Windows Server® operating system to the Microsoft Visual Studio® development package and Microsoft Office applications), and can help your organization save time and money by using collaborative technology.
7. Description of system security measures
The security of this system is divided into four aspects:
1. Network Security
According to the system design requirements, the system can be connected to the local area network of the unit. But the local area network is based on TCP/IP Ethernet, and Ethernet is a broadcast network, so users in the same network segment can monitor the contents of all packets on the network, and can monitor the communication between other hosts. Therefore, if the user password and other information are transmitted in clear text on the network, the password can be easily intercepted by using network monitoring tools such as sniff. Therefore, the transmission of the password on the network must be encrypted. The scheme adopted by the system is user password encrypted transmission and encrypted storage.
Another suggestion is that the network is completely closed loop, not connected to LAN and WAN. This has the advantage of completely avoiding external intrusions, but it does not have convenient technologies such as remote control and SMS notification.
2. Operating system system and database security
Because the Windows 2003 Server operating system itself has strict security protection, and the SQL Server 2005 database itself has additional rights protection, it is basically possible to ignore the situation of illegal users directly tampering or destroying data on the server.
And because of the flaws in the bottom layer of the Windows 2003 Server operating system, it is vulnerable to network attacks that cause the operating system to crash. Therefore, it is required to patch the operating system every time the server is installed and with the existing patch software (patch). After patching the operating system and conducting actual attack experiments, it has been shown that most of the existing attack programs can be resisted.
3. The security authority setting of this system
The security permission setting of this system adopts a permission setting method based on role setting. It is mainly divided into user management, role management, and function authority management.
l User settings: Set all possible direct users of the system, give each person a fixed code and set the corresponding password.
l Role setting: Set up different roles according to users of different tasks. Different users can be set to belong to different roles according to actual needs, and the functions that the user can use are different. The functions between roles can overlap, that is, several roles can all have a certain function.
1 Role permissions: Set the functions that the role can operate and the data reports that can be viewed.
4. Backup and restore
The various basic data involved in this system are very important for this system, for the safety of the entire building and the management of assets. Therefore, it is necessary to establish an online backup system to regularly back up these critical information so that it can be quickly restored when the information is damaged. The system to be backed up includes all the data of the system. Most of these systems are in uninterrupted operation, and the system information needs to be backed up regularly according to the backup strategy without affecting the normal operation of the operating system.
In this system, we recommend using LAN backup technology to realize automatic backup of key data on the system. Use data backup software to manage and control the backup work, flexibly set up various backup strategies, and back up the data to the optical disc library. Use high-quality DVD to burn discs and save 3-5 years of historical data. When data on the integrated information platform is lost due to unexpected circumstances, data recovery can be carried out flexibly through the backup system to ensure data security.
If you have any questions, please contact
Document production: Ren Gong
Email: [email protected]
QQ: 479017087
Mobile: 13911533725
http://company.rfidworld.com.cn/rfidworld_company_27961.html
[ad_2]



