RFID-based asset management solution system
[ad_1]
1. System background
There are a large number of fixed assets, such as important equipment, instruments, installations, articles, etc., in banks, jewellery shops, military and other institutions. The traditional management methods of these devices usually rely on a non-automated paper document-based system to record and track incoming and outgoing assets. The internal management of the enterprise is completely implemented manually. Therefore, the management efficiency is extremely low, which not only causes a lot of waste of human resources, but also Moreover, due to human factors, asset data entry speed is slow and accuracy is low. As a result, equipment managers cannot fully grasp the accurate quantity, status, and real-time location of equipment in a timely manner, and even the discovery and tracking of missing equipment often lags behind for a long time. As the scale of the enterprise continues to grow, the types and quantities of fixed assets that need to be managed are gradually increasing, the frequency of receiving and returning is gradually increasing, and the management work is more complex and diversified. The traditional manual management operation mode and data collection method have been difficult to meet the fixed requirements. High-speed and accurate asset management requirements. Therefore, how to realize the comprehensive management of valuable assets by introducing existing high-tech security measures has become one of the important tasks of today’s valuable and confidential organizations.
In the old-style management system, the usual asset management methods are prone to many shortcomings, which are difficult to meet the needs of modern asset management. The problems are as follows:
1) Asset introduction: Asset management personnel must manually fill in the equipment data and check the number and status of the equipment. The actions are complicated, cumbersome, time-consuming, and error-prone; fixed assets are not easy to identify, the identification is easy to deface, lose, and it is not easy to save;
2) During the inventory and inventory of assets, managers manually confirm assets one by one. The workload is huge and wastes human resources, and due to artificial irregular operations, it is easy to cause confusion in inspection results and loss of assets;
3) Lack of real-time statistical analysis of assets and timely and accurate preventive maintenance data;
4) It is impossible to accurately determine whether to repair, repair, or replace equipment;
5) Asset status information includes inventory, recorded, damaged, pending report, unrecorded, etc. Assets in different states are stored in different databases, which not only easily causes confusion in data management, but also brings statistics and inquiries A lot of trouble.
6) Data management records are kept separately, making it difficult to realize data sharing.

2. System overview
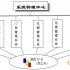
My companyRFIDValuable assets real-time positioning and tracking management system for the security management of valuable assets, combined with advanced radio frequency RFID technology, wireless sensor technology, mobile computing technology, digital communication technology, digital video technology, etc., on the basis of the traditional valuable asset management system, adding valuable Asset regional security monitoring, regional security fortification, loss alarm, unauthorized movement alarm, disassembly alarm and other functions, and can import electronic maps to realize asset visualization and real-time supervision, which overcomes the lack of asset security management in the traditional valuable asset management system and the single method Disadvantages, the realization of informatization and networking of asset management is of great significance to the rational allocation and utilization of assets, reducing input costs, increasing input-output benefits, and improving management level and efficiency.
The platform construction mainly includes the following contents: realize the positioning management of valuable assets, including real-time monitoring of location and movement trajectory by time and area; realize the routine task management of valuable assets, such as: asset introduction, requisition, loan and return, Inventory, scrap and other related management work; combine sensor technology, image acquisition technology, wireless transmission technology and other means to connect with asset management systems to realize real-time monitoring of asset environmental safety and data collection records; realize professional management of asset access and automatic formation Accurate and reliable historical behavior reports to trace asset history; form and establish a professional security alarm system (alarm for illegal removal, alarm for illegal disassembly, alarm for illegal movement, environmental security, etc.), and link with the system to achieve long-term management of valuable assets Alarm mechanism.
Three, system function
3.1 Asset positioning system
Install RFID positioning tags on the corresponding assets, and perform real-time position and status management of the assets in the supervision area through the read-write equipment in different areas, and realize the management of fortification and disarming of the supervision area, the authorized movement of assets, and the division of supervision areas , Map import and other operations, enable valuable assets in the supervision area to realize real-time asset tracking according to their type, department, and area to ensure asset safety; asset positioning tags have anti-disassembly alarm function, if illegal disassembly occurs, the system will automatically link to alarm management Part of the security alarm is carried out to ensure the safety of assets.
3.1.1, asset positioning
Assets in the management area can be positioned and managed in real time through various paths, gates, and indoor positioning devices. Assets (types, information) can be displayed on the electronic map through the system, and the corresponding asset historical movement can be queried in the system Tracks, current status, etc.
3.1.2. Fortification and disarming of the supervision area
For the system management area, managers can freely set up fortified areas, and can divide different areas on the corresponding electronic map for the fortification and disarming operations of asset management in the area. The fortified area is marked in red on the system electronic map.
3.1.3, asset authorization movement and anti-disassembly alarm
Managers can freely set asset management authority at any time, such as: asset movement authority, asset movement area authority, asset removal authority, etc. After authorization, assets can be used and managed in the management area according to their corresponding authority; asset positioning tags have anti-disassembly alarms Function, in case of illegal disassembly of electronic tags, the system will promptly alarm for illegal disassembly through the system, effectively guaranteeing asset safety.
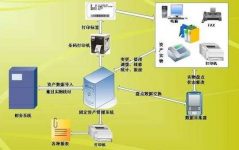
3.2 Fixed asset management system
3.2.1. Asset file management
After the asset purchase inspection file, the operator uses the RFID card issuing machine to issue an RFID asset management label for the new equipment. The label includes the asset number, asset name, purchase date, custodian, asset status, and other information such as the phone number of related personnel. The label is pasted or hung on the surface of the asset, and the system records the completion of the asset storage. RFID asset management tags will be used together with the asset life cycle to facilitate the operator’s future use of assets, return, inventory and report damage.
3.2.2, asset acquisition management
When using the assets in the library, the system registration or the operator uses the handheld RFID terminal to read the tag information on the assets. After confirming the assets to be taken, the system automatically modifies the asset out of the library, asset acquirer, asset status and other related information, and the asset is out of the library The operation is completed in one step, reducing the work intensity of the operator and reducing the error rate.
3.2.3, asset retirement management
When the asset is scrapped or damaged, the operator needs to read the RFID asset management tag information attached to the asset. After confirming the information, the system automatically modifies the relevant information, reducing the work intensity of the operator and reducing the error rate.
3.2.4. Asset inventory management
The purpose of the fixed assets inventory is to check the difference between the fixed asset account and the physical object, so that the corresponding treatment can be made to achieve the actual balance of the account. Put RFID tags with asset numbers on all fixed assets. When counting, the fixed asset accounts are downloaded to the handheld terminal according to the location of the assets on the account. According to the work plan, the inventory staff took the handheld terminal to the corresponding location to scan the RFID tags on all fixed assets in the location one by one, and the terminal automatically completed the comparison between the actual inventory situation and the book situation. After the inventory is completed, an asset difference table is formed, and the difference data is unified and manually processed in accordance with the corporate asset management method.
3.3. Environmental Management System
Combine with video capture technology and sensor technology to monitor the environment and asset conditions in the system management area in real time. The environmental management system has the functions of monitoring temperature, humidity and smoke detection. Managers can freely set the temperature and humidity safety range and alarm system as required Linkage realizes environmental hazard alarm; the environmental management system combines with video capture equipment to record real-time video of asset conditions and on-site environment, effectively guaranteeing asset safety, and ensuring that safety issues are well documented and based on evidence.
3.4. Asset Access Management System
RFIDelectronic labelThe fixed assets are embedded in the system for binding and then entered into the system. Read-write devices are installed at the entrances and exits of each area to monitor the entry and exit of the assets. The requesting personnel shall enter the information of the requested equipment, use, and use department into the system as required, and the management department will pass the approval , Requisitioning personnel requisition items; asset access management area gate, read-write equipment will upload relevant asset information, access time, location, etc. to the management platform, and enter the system database for record. For assets that have been approved for legal entry and exit, the asset entry and exit management system will promptly transmit the corresponding asset access information to the monitoring management center for archiving; if the asset information does not match or is maliciously and illegally brought out, the asset entry and exit management system will immediately send the information On the system platform, the alarm system is connected in parallel to perform sound and light alarms in order to detect abnormalities in time and take safety measures to ensure asset safety.
3.5. Asset alarm management system
Linked with various systems to realize a full range of security alarm management for assets, such as: illegal disassembly of asset electronic tags, unauthorized removal of assets and movement of illegal areas, security alarms for fortified areas, regional environmental security alarms, etc., asset alarm management systems and systems Platform linkage, with a complete alarm system, promptly notify the relevant management personnel and departments of the corresponding alarm information, and record the alarm records into the system database for future query and traceability; this system has a voice alarm function that can provide corresponding voice prompts and according to user needs Alarm management.
Four, system characteristics
1) The system automatically collects asset information, greatly improving work efficiency and information transparency in the entire process.
2) The accuracy of the information collected by the system greatly improves the future maintenance and safety of assets, and minimizes the error rate of manual recording and statistics.
3) Realize the safe positioning of valuable assets, that is, realize the positioning and tracking of valuable assets within a certain range, and systematically alarm when important assets leave the specified range;
4) The system has efficient, fast and accurate statistical functions (such as rapid statistics of total assets, equipment usage, current status of equipment assets, etc.) and can provide management with various data to make quick decisions.
5) Conditional early warning function can be provided for the asset return time and equipment maintenance time, which is convenient for the management department to further understand the asset usage.
6) The use of high and new technology can greatly improve management and establish a new image of the unit.
7) The system automatically, quickly, and remotely recognizes the entry and exit of valuable assets, automatically registers the person in charge of the asset, whether it has been used for application and approval, and the time of entry and exit, and promptly alarms the illegal state, which greatly improves the security of the asset.
[ad_2]