RFID-based jewelry management solution
[ad_1]
1. System composition

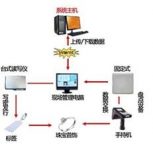
The system is composed of RFID electronic tags corresponding to individual jewelry individuals, electronic tag issuing equipment, on-site inventory reading and writing equipment, computers, management system software, and related network equipment and network data interfaces.
Fixed reader: Because the fixed reader adopts an RFID integrated reader, the antenna and the reader are integrated into one. On the one hand, it can identify the tags and realize remote data collection at the same time, so that the collected information can be real-time Accurately transmit to the background server.
Electronic tags: Jewelry tags are mainly made into hang tags and hung on the jewelry to store jewelry information, including the name, type, model, etc. of the jewelry. Encapsulated tags are recommended.
Card Issuer: Write data for the electronic tag, including the name, type, model of the jewelry, etc., and can lock the data area to prevent the data in the electronic tag from being rewritten. It is recommended to use a desktop UHF reader with superior performance.
Antenna: Mainly set up at the doorway for people to enter and exit, to effectively identify members, and mainly play a role of identification in the system.
2 application scheme
Jewelry label initialization
① Newly delivered jewelry, when the jewelry is delivered, the EXCEL form (including jewelry number, production certificate number, purity, etc.) attached to the jewelry and new jewelry information will be delivered together;
② Initialization of the homogenized jewelry label, the same type of jewelry of the same brand, first import the type of jewelry information into the UHF handheld terminal through the USB port, and then use the UHF handheld application to convert the number to the batch of UHF tags Binding, complete the initialization of the homogenized jewelry information label;
③ Non-homogeneous jewelry initialization, first import the jewelry information into the UHF handheld terminal in batches, and then bind the jewelry number and the UHF tag one by one through the UHF handheld application to complete the initialization of the non-qualified jewelry information label ;
④ Synchronize the initialization information of the jewelry label with the management system, and communicate the jewelry label distribution information with the webservice through the handheld terminal application to realize the synchronization of the jewelry label information and the management system information.
Jewelry inventory management
Automatic jewelry inventory, through fixed readers to regularly or real-time inventory information on the booth, the inventory information is transmitted to the supervisory server through the local area network.
Jewelry inventory check, according to the total number of data collected by the fixed reader and the jewelry data of the management system, the jewelry information is compared one by one (position movement, etc.), and the alarm is prompted when the information is inconsistent.
Application in jewelry display
According to the actual situation on site, RFID antennas are arranged in various display areas such as original showcases, display trays, and display racks in the store. For example, if employees need to put jewelry in a display tray for customers to watch, they can take the jewelry out of the RFID smart display cabinet and put it in the RFID smart display tray for a one-minute display. Before this piece of jewelry is put back into the smart display cabinet, the antenna installed in the center of the smart display tray will monitor the tray. Once the jewelry leaves the safe area, an alarm will be triggered to remind the central management personnel, showcase employees and security guards to pay attention to the problematic area immediately.
Abnormal alarm management
A special antenna is installed under the jewelry counter to record the time, number of times, and final sale time of each piece of jewelry in the box in real time. If there is any abnormal operation during the sales process, the system will issue an alarm. The real-time alarm function can greatly improve the security level of the store, so that the merchant can take measures in the first time. At the end of each day, before the jewelry is put back to the safe location, the goods are verified by the counter installed in front of the security door and the jewelry is transferred to the safe. The data is compared with the data of the previous day. If there is a deviation, the staff will be reported Alert.
3 system function
3.1 Jewelry purchase, sales and inventory management
Jewelry purchase, sales and inventory management, through the relationship between RFID jewelry tags and jewelry, automatically collect and record jewelry purchase, sales and booth information;
Jewelry daily report, according to conditions such as day, category, area, etc., reflect the in and out of jewelry jewelry;
The monthly report of jewelry reflects the entry and exit of jewelry and jewelry by month, category, area and other conditions;
Monthly statistics table of jewelry purchase, sales and inventory, according to time, category and jewelry statistics;
3.2 Jewelry real-time monitoring
Using the jewelry inventory installed on the counter can be used to monitor, control and track labeled jewelry, to achieve rapid inventory, real-time tracking and sales management intelligence, so as to track and record the entry and exit of jewelry products and the sales process in an all-round way.
3.3 Jewelry alarm management
① Alarm when the jewelry is not in place. When the jewelry leaves the booth without authorization (only a specific authorized employee opens the cabinet with RFID lock through the RFID electronic key) within a limited time, an alarm is triggered;
② Overtime alarm for jewelry retention time, overtime for jewelry display time (standard timeout can be configured), trigger the alarm;
③ Jewelry inventory alarm, the total number of real-time inventory of the fixed reader is inconsistent with the data registered in the management system, triggering an alarm.
3.4 System Management
Jewelry branch information management, add, delete, modify jewelry branch, record the name, code, address, level (organization structure), contact number, contact person, person in charge and other information of the branch.
User management, add, delete, modify system users, users can be divided into browsing users, operating users, administrators, and senior administrators.
Password management, add, delete and modify the user’s password.
3.5 Handheld terminal application
Jewelry tag reading and writing, realize the initialization of jewelry tag data and the correction of tag data.
Data synchronization management realizes data synchronization between the handheld terminal and the management system.
Inventory check (optional), to realize the comparison check between the actual jewelry in the store and the registered data of the management system.
Password management, add, delete and modify the user’s password.
[ad_2]