RFID entity car and driving file information management construction solution
[ad_1]
1.1 Project background
With the development of computer technology and radio frequency identification technology (RFID), as well as successive successful applications in the fields of book management, warehousing and logistics, food traceability, intelligent transportation, etc., it is possible to solve file management problems.
After the introduction of RFID technology in archive management, the circulation of archives can be dynamically managed. The system uses RFID tags as the information carrier to collect and supervise key links such as archive circulation, so as to realize the automation of archives business management and the full life cycle management of archives.
1.2 Project demand analysis
In recent years, the archival business has made considerable progress, the scale of the archival business has expanded, the number has also increased day by day, the types of archives have become more diversified, and the amount of information has expanded rapidly. However, the problems caused by traditional archive management methods and technologies have become increasingly prominent, which are mainly reflected in the following aspects:
1.2.1 Status Quo and Problems
(1) Manual operation of files in and out of storage, high work intensity and low efficiency. Although strict management regulations have been formulated, manual operations are time-consuming, laborious, and costly, making the whole process cumbersome and inefficient, especially for files that need to be completed through the collaboration of multiple positions, which are more likely to cause file loss, wrong files, and missing files. , Delays, etc., embarrassing the management department and serious consequences. Due to the time-consuming and labor-intensive manual operation, errors are unavoidable for the inventory and cleanup of archives and the registration of invalid archives before destruction.
(2) File retrieval is difficult and difficult to accurately locate. The inability to retrieve the files when adjusting the papers will put the management agency in an embarrassing situation where it will not be clear if it jumps into the Yellow River; the inspection work of the higher-level departments cannot quickly transfer the designated physical files, and it will also make the management agency feel uncomfortable.
(3) The number of files has increased dramatically, and it takes time and effort to retrieve files. Due to the inevitable errors of manual operation, the order of file storage is inevitably disordered, making it very difficult to find files, like finding a needle in a haystack. It often takes time and effort to search through the inventory without finding the designated file, which makes the staff miserable, especially for the need The transferred files have disastrous consequences, and some even face high price claims;
(4) Lack of modern scientific and technological means and low degree of informatization. Archival business needs to frequently retrieve files for comparison and confirmation. In the case of low informatization, it not only increases the workload, but also easily leads to misfiles. At the same time, the efficiency of work is extremely low, which often leads to the dissatisfaction of the masses who wait for a long time.
1.2.2 Project construction goals
The application of radio frequency identification technology (RFID) to the field of archives management makes full use of the many advantages of radio frequency technology to realize automation of warehouse information management and automation of file entry and exit operations, which plays an important role in improving the efficiency of file circulation.
Realize the informatization of intelligent management of archives. According to the daily storage, query, file adjustment, anti-theft and other specific business processes of file data, the file circulation is dynamically managed. Data collection and monitoring are carried out on the key links of archives circulation to realize the automation of archives business processing, thereby replacing the traditional paper work process.
Improve the comprehensive capabilities of file management and improve service levels. Realize data sharing, improve the efficiency of file management, simplify the management process, reduce the labor intensity of personnel, reduce errors, and provide a more convenient and effective management mode for file management.
1.3 Application advantages of RFID technology in file management
1.3.1 Data collection in non-contact mode
RFID technology has greatly enhanced the manager’s ability to collect, exchange, and track information about items stored in the warehouse. The manager does not need to open the file box, just pass the file box with the RFID tag past the reader to read the data stored in the chip. It is not afraid of harsh environments such as oil stains and dust pollution, and can work in harsh environments. Unlike bar codes, magnetic cards and other media, if the surface is not clean, it cannot be read accurately.
1.3.2 Large label information capacity and long service life
Compared with traditional data storage media such as barcodes and magnetic cards, the amount of data that RFID tags can store has greatly increased. With a capacity of 1K or even 8K, more information can be stored. For archive management applications, the basic information and borrowing of archives can be fully used. Records are written into the chip for storage.
1.3.3 High security
The data access of the label is protected by a password, and the identification code is unique and cannot be forged. This high-security protection measure makes the data on the label not easy to be forged and tampered with.
1.3.4 Strong anti-pollution performance and durability
The carrier of traditional bar codes is paper, so it is susceptible to contamination, but RFID is highly resistant to substances such as water, oil, and chemicals. In addition, because the barcode is attached to the plastic bag or the outer packaging carton, it is particularly vulnerable to breakage; the RFID tag stores the data in the chip, so it can be protected from contamination.
1.3.5 Small size and diversified shapes
RFID is not limited by size and shape in reading, and does not need to match the fixed size and printing quality of the paper for reading accuracy. In addition, RFID tags can be miniaturized and developed in various forms to be applied to different files.
1.3.6 Strong penetrating and unbarred reading
When covered, RFID can penetrate non-metallic or non-transparent materials such as paper, wood, and plastic, and can perform penetrating communication. The barcode scanner must be at a close distance and there is no object blocking the situation before it can read the barcode.
1.3.7 Anti-theft
The tag can cooperate with the door-shaped channel antenna to effectively realize the anti-theft function, prevent the loss of files, and realize the alarm function of illegal removal.
1.3.8 It can be adapted to disinfection, pest control, etc.
RFID tags can be adapted to the routine disinfection, high and low temperature insecticidal environments of file management, and will not cause the data stored in the tags to be lost.
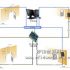
1.4 RFID file management system
1.4.1 System hierarchy planning

This system is designed with modular components and adopts a three-tier structure system. It can be used in combination according to actual needs. The three-tier structure is:
Device layer: It is mainly composed of hardware devices (RFID readers, counting cars, workstations, handhelds, LED displays, etc.), which are mainly used for data collection and display.
Middleware layer: It is composed of middleware, application services, database. Through the middleware to realize the communication with the hardware equipment, and write the corresponding database at the same time. Application services are used for data access and business logic processing.
Management application layer: It mainly realizes interaction with users, data display, query, etc. Provide business function modules according to user needs. .
1.4.2 System Data Architecture Planning

Data collection (file creation): The operator passes the file information (full case number, catalog number, file number, part number, file number, storage period, confidentiality level, location, etc.) in the system when handling the file creation for the customer The system automatically writes relevant information into the RFID chip to realize the binding of RFID and archives.
File circulation record: The post name, date, time and other information that the file passes through are automatically written into the RFID chip through the RFID reader; at the same time, the relevant information is fed back to the computer, and the computer transmits the information to the database server through the communication network Save it for users to retrieve and consult.
File storage verification: The processed files are entered into the list of files to be stored. When the storage verification is processed, the RFID reader and the borrower information management system are used. The file management personnel will compare the information, and the system will automatically allocate the location after confirming that it is correct.
File storage: LED display screens are installed in each area of the file room to display the file information to be stored. At the same time, an RFID reader can be installed to identify the files and display the storage location of the files.
File query: When querying files in the file room, you can find the storage location of the files through the ID number, file number and other information. When files are adjusted, batch operations such as files processed in a certain period of time or files in a certain place can be performed in batches. At the same time, enter the warehouse list of files to be taken out.
Inventory: File inventory can be channeled through a dedicated file inventory vehicle to support online and offline modes.
Inverted shelf: If the file storage location error is found, the file location information can be updated by counting the car.
Warehouse search: If you can’t find a file, you can search the whole warehouse by counting the car. After finding it, the system will automatically prompt (voice prompt and software interface).
1.4.3 RFID technology implementation design plan
(1) Binding of physical files and RFID
When the RFID entity file passes the range of the reader, the reader writes designated information such as file number, secret level, location, etc. into the RFID chip through wireless signals for storage, and at the same time stores related information and post flow information such as the name of the operating user and the name of the post , Date, time, etc. are fed back to the computer, and the computer transmits the information to the database server through the communication network for storage for users to retrieve and consult.
(2) Find files
When searching for files, you only need to set the required conditions on the corresponding computer or reader, and use the reader to scan the preliminarily identified file storage area. The information stored in the RFID file is continuously transmitted to the reader through wireless signals. The computer or reader will automatically compare the received information with the set conditions. After the comparison is successful, a prompt will be issued, and the staff can immediately confirm the location of the required file, so that the required file can be extracted quickly and accurately file.
(3) File storage and retrieval
The reader reads the relevant information stored in the non-contact IC card through wireless signals, the file management post computer automatically fills in the post and other information, and the fingerprint device collects the fingerprints of both parties in the file transfer to confirm the transfer of the file. The receiving party must be the fingerprint of the staff authorized to file in the system. At the same time, the computer of the file management post will automatically determine the legality of key fields such as file number and number plate number, otherwise the system will give a warning and not pass it. All information is automatically transferred to the database server for storage.
(4) File inventory
When clearing, registering before invalidation and destruction, set its current working status on the computer of the file management post to inventory cleaning or invalid file registration, scan the reader through the file, and the information in the RFID is transmitted to the reader through wireless signals Writer, the reader transmits the information to the file management post computer, the file management post computer automatically compares with the corresponding information in the database server, and automatically generates an inventory cleanup or invalid file register.
(5) Automatic comparison of physical files and electronic information
The physical file information confirmed by the system can be automatically compared with other application platforms on a regular basis to ensure one-to-one correspondence between physical files and electronic information, ensuring the safety and integrity of physical files.
1.4.4 Business link design and planning
1.4.4.1 File admission
1. After receiving the files, the staff of the Receiving and Sorting Office enters the file information into the system. The entered data includes: file category, file name, file number, file secret level, storage time, storage period, summary of file content, etc. An electronic label is printed out through the RFID electronic label printer, and the file information is written into the electronic label chip at the same time. The electronic label is pasted on the surface of the file box, and the basic information such as file name, serial number, category, and secret level is printed on the outside of the label.
2. The file with the electronic label pasted is sent to the safekeeping place for storage. Before storage, the storage staff scan the electronic tags of the files through RFID card readers, register the storage time and set specific storage locations, so as to establish the storage records of the files in the system.

File storage and storage: LED screens are installed in each area of the file warehouse, and the inquiry machine is installed in the central location. Realize warehouse take-out and store files to guide warehouse administrators. When warehousing, the warehouse management staff will put the files in the designated place according to the LED display prompt information. After completion, confirm the file has been placed through the inquiry machine or the handheld machine. The system automatically updates the file information status to be in the library.

1.4.4.2 File borrowing
1. Borrowing application
Install a self-service file information query machine in the utilization hall. The borrower can query the information of the required borrowing file, and print out the borrowing ticket through the query machine. The required borrowing file information (name and code) is printed on the ticket. At the same time, small The order number of the business transaction is also printed on the ticket, that is, the inquiry machine also has the function of automatic numbering of the business transaction.
2. Borrowing registration
The borrower presents the relevant certificates and the borrowing ticket, uses the hall operator to register the files that need to be borrowed and the borrower’s information, and submits the borrowing application record after confirmation; for some files that must be approved by the leader, the archives leader can do it through the software Online approval, after approval, the borrowing of audit records becomes effective.
3. File search
The file circulation management subsystem is installed on the computer of the staff in the storage area of each floor. Once there is a new borrowing application, the system will automatically display the record on the computer screen. The displayed information includes: file name, file number, storage location, etc. The staff searches the file according to the application record.
After the search is completed, the staff must scan the electronic label through the card reader to complete the file out-of-warehouse registration, and the system records the file out-of-warehouse time and the out-of-warehouse file number.

4. File lending
The staff of the depository transfer the files to the staff of the utilization hall. Before the files are handed over to the users, they must scan and register the electronic tags in the system to record the loan time and file number.

1.4.4.3 File return
1. After the user completes the file review, the file is returned, and the staff scans the file electronic tag, registers the return time and file number, and completes the return registration. If the user exceeds the designated review time, the system will automatically remind;
2. Before the storage staff put the files back to the designated storage place, they must scan and register the electronic tags and register the storage time. After the registration is completed, the files will become the storage status.

1.4.4.4 Induction, query and application of archives warehouse
Install LED screens in each area of the archives warehouse, and install the inquiry machine in the central location. Realize warehouse take-out and store files to guide warehouse administrators.
The LED display in each area displays the specific location information of the files to be taken out and stored in their own area.
In the warehouse, the specific storage location of a certain file needs to be inquired through the inquiry machine. At the same time, after storing the files, the query machine can be used to confirm that the files have been stored in and out of the library.

1.4.4.5 File adjustment

File adjustment: Obtain file information through the reader, ID card collector completes the collection of the identity information of the file adjuster, and the fingerprint device replaces the existing signature confirmation action. When handling the file adjustment service, the staff can inquire files according to the information (file number, whole case number, catalog number, case title, etc.) or check the file information through the ID card collector. After the file adjustment service registration is completed, the system will automatically Send the file information to be out of the warehouse to the LED display in each area of the warehouse. The warehouse manager takes out the files through the LED screen.
When searching for files, you only need to set the required conditions on the corresponding computer or reader, and use the reader to scan the preliminarily identified file storage area. The information stored in the RFID file is continuously transmitted to the reader through wireless signals. The computer or reader will automatically compare the received information with the set conditions. After the comparison is successful, a prompt will be issued, and the staff can immediately confirm the location of the required file, so that the required file can be extracted quickly and accurately file.
1.4.4.6 File inventory
The use of RFID technology for file inventory makes the original heavy and cumbersome file inventory work a simple and fast task.The file management system sends out an inventory instruction, and the warehouse management terminal sends an inventory instruction to the mobile terminal. The warehouse manager reads the label information of the file grid and the stored files according to the prompts on the mobile terminal, completes the inventory operation of a file grid, and proceeds in sequence Until the inventory operation of all files is completed
1.4.4.7 File anti-theft
All collection files are in the reading range of the reader. When the file is taken out, the RFID reader at the exit port captures the file information and checks it with the outgoing instruction information. If the file leaves the warehouse abnormally without the outgoing instruction issued by the archive management information system, the monitoring module will be activated The alarm module sends out abnormal situation alarms to prevent files from being destroyed and stolen.

It is used to manage the entry and exit of warehouse personnel and the visit management of valuables warehouse. Install access card readers and exit card readers inside and outside the warehouse’s entrance and exit doors to realize two-way swipe card authentication and personnel information registration. For confidential warehouses, multi-card mode or N+1 access mode can be used to provide a higher level of access control. Two pairs of RFID fixed reading and writing equipment and two pairs of infrared radio equipment are installed at the gate of the archives library. For the aesthetics of the archive, the equipment is installed in the door frame.
1.5 Features of Project Construction
1.5.1 Advanced RFID technology
The system is constructed using the most advanced RFID technology. RFID has many advantages such as convenient and fast reading, high-speed identification, batch identification, strong penetration, large data capacity, long service life, and high security. It is the core technology of the Internet of Things industry and the future development direction and trend.
1.5.2 Component software system
The software system architecture is built with a modular component structure to improve the scalability and tailorability of the system. Can provide highly flexible business expansion needs and streamlined business needs. Improve the application range of the software system, while meeting the different application needs of large and small customers.
1.5.3 System cascading deployment
The system uses an independent directory server. According to the server’s data, the independent file systems can be combined and cascaded to form a national-level file system. Realize the integrated query of data and archives in the entire system.
1.5.4 High security file management
This system provides high security file management. Comprehensive use of advanced access control systems (multi-card door opening mode, N+1 card mode, etc.), video surveillance linkage, environmental monitoring, infrared zone protection technology, and advanced RFID technology are used in the system to achieve multiple protections for file storage and access. Ensure the storage and access security of archives. Confidential warehouses can be set up for files with higher security levels to achieve higher access security control.
1.5.5 Precise location retrieval
On the basis of advanced RFID technology, combined with advanced software system algorithms and hardware deployment, it can support multiple retrievals of archives and achieve rapid and accurate positioning. So as to realize efficient file retrieval and access, improve the manageability of files, and improve work efficiency.
1.5.6 Efficient file access
On the basis of accurate file positioning, based on the technical advantages of RFID (high recognition speed, penetrating recognition, etc.), batch file access can be realized. When entering and leaving the archives, stack scanning is realized, which greatly improves the efficiency of file access.
1.5.7 Archive life cycle management
Many archives have a certain retention period (such as escrow business archives). This system supports the management of the archives’ life cycle, can record the start and end time of archives, and promptly remind expired archives to release archive storage space.
1.5.8 Reduce staff costs
After the establishment of the archives management system, the archives management system saves the cost of human resources, realizes high work efficiency, information accuracy, strengthens the archive confidentiality mechanism, extends the archives preservation period, and bids farewell to the cumbersome and inefficient archive work process. Long time. The file storage order is disordered, the file verification and reference time-consuming, the file security protection ability is weak, and the file inventory efficiency is low. The problems have also been effectively solved.
1.5.9 Improve the security level of archive preservation
Traditional file management cannot effectively guarantee the security of files. In order to prevent files from being maliciously stolen, the system can track files after using the RFID entity file management system. If the transfer is not authorized in the system, the files cannot be taken out of the file room and are forced to be taken out. The file room system will automatically alarm.
1.5.10 Improve the efficiency of file inventory
Due to the large number of files, it will be a very huge project to take inventory of all files, and the relevant classification data cannot be provided after the inventory. Using the RFID entity file management system, a medium and large file library, all files can be counted in 30 minutes. The relevant data is displayed in graphics and lists according to different categories, which is convenient for leaders to view and analyze the relevant data.
[ad_2]