RFID fixed asset information management solution
[ad_1]
Chapter 1 RFID Fixed Assets Information Management Solution
1.1 Project overview
At present, fixed assets in all walks of life rely more on traditional manual management methods and means. Data collection and entry have always been manual operations, with low efficiency and high error rates. The book cannot reflect the existence of assets, the asset management is difficult, the assets are lost, the inventory is laborious and time-consuming, the effect is not good, the clearing before and after the chaos, and the cost of assets cannot be accurately and timely verified. Through the construction of an RFID asset management system, the above problems have been fully solved.
1.2 Market demand
According to the needs of various industries in the current market, our company independently develops a fixed asset management system to meet the asset information management needs of various industries. The system uses radio frequency identification technology (ie RFID technology), uses RFID tags to identify fixed assets, and uses data collection terminals to complete the daily management and inventory of fixed assets, thereby efficiently realizing the physical life cycle and use status of fixed assets Tracking throughout the entire process, to the greatest extent possible technically to ensure that the assets are consistent with the actual accounts, thereby avoiding the loss of fixed assets, and at the same time improving the efficiency of asset maintenance, so as to realize the information management of fixed assets.

1.3 Asset Management System
1.3.1 System Overview
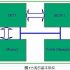
The asset management system adopts the most effective non-contact automatic identification technology recognized in modern times—RFID (Radio Frequency Identification) technology to comprehensively and effectively manage the storage, application, and inventory life cycles of assets, assets, etc., and detailed records through the purchase of assets, The entire process of acquisition, maintenance, and scrapping is managed to achieve efficient and reliable fixed asset management. The system composition mainly includes a central data server, inventory handhelds, RFID asset tags, and asset management systems.
1.3.2 Business Process
The RFID asset management system uses computers, all-in-ones, mobile hard drives, printers, fax machines, desks and chairs and other asset information to enter the system and allocate RFID tags, register the department and the applicant of the assets, and write the data to the corresponding tags Inside. Quick asset management and inventory work can be achieved through a handheld reader, which greatly saves manpower and material resources, improves asset management efficiency, and provides fast asset query and search tools for relevant management departments. The figure below is a schematic diagram of asset inventory and monitoring.

1.3.3 Function planning

functional module
? Electronic label management
On the basis of the centralized display terminal program, the module is added, no additional client program is added, and user operations are reduced.
? Asset Information Management
Information management of assets (new addition, modification, scrapping, etc.) can be performed, and asset information, user information, etc. can be inquired.
? Asset claim management
All asset claims need to make corresponding business applications in the system. After the approval is approved, the system automatically writes the claimant, claim time, return time, etc. through the reader.
? Asset archives (asset life cycle)
After the assets enter the system, an asset file is formed. You can query purchase information, user information, claim and return records, maintenance records, violation records, scrap records, etc.
? property assessment
The user conducts mobile inspection and inventory operations through the handheld device. The handheld can identify assets and display related information, statistical quantities, etc.
? Asset Ledger Management
? Assets can be divided into office assets, computers, electronic products, and other asset management, and can also be classified according to user-defined standards;
? Each asset has all-life logs related to purchase, use, inspection, maintenance, Internet access, transfer, take-out, firmware changes, and scrap;
? Equipped to specify multiple types and multiple condition combinations of search queries, export EXCEL reports, classified statistics (reports and graphics in two ways).
1.3.5 Function description
1.3.5.1 System background management
System back-end management is the foundation of the secret-related asset management system, which is mainly responsible for the establishment of initial data, system configuration, creation of users, adding unit departments, position (role) management, resource registration, authority distribution, etc. System background management includes organization management, system resource management, system integration authority management, log management, and system configuration management.
1.3.5.2 Asset Management
The addition of assets, the initialization of tags, the modification and query of asset information, etc. UHF tags are used for warehouse entry and exit records, patrol inventory, illegal alarms, etc. (desktop computers, portable computers, mobile hard drives, digital cameras, digital video cameras and other fixed assets).
1.3.5.3 Asset inventory
By installing the inventory program on the handheld, the automatic identification of the tags can be realized in batches, and the quantity of various tags can be calculated, and the inventory function (the difference between the quantity of various assets in the system and the actual collected quantity, and detailed information).
The user conducts mobile inspection and inventory operations through the handheld device. The handheld can identify assets and display related information, statistical quantities, etc.
1.3.5.4 Asset file records
The asset file can view the entire life cycle of the asset from asset purchase to scrap, such as the person applying for purchase, approving person, purchase time, approval time, all violation records (violator, violation time, and reason for violation, processing result, etc.), all Outgoing records (exit time, person carrying, reason for outgoing, return time, etc.), scrap application, approval status, scrap verification result, etc.
1.3.5.5 Asset Information Query
Query the basic information, current status, access records, violation alarm records, and asset file information of assets.
Violation records can view all violation records of a certain asset, the person who violated the law, the time of the violation, the reason for the violation, the processing result, etc.
Access records can view the access records of a certain asset, the time of each entry and exit, the person to bring, the reason for going out, the return time, the approver, approval opinions, etc.
Asset archives can view the entire life cycle of assets. Such as the person applying for purchase, the person who approves, the time of purchase, the time of approval, the record of violations (the person who violated the regulations, the time of the violation, the reason for the violation, the processing result, etc.), the entry and exit records (the time of each entry and exit, the person carrying, the reason for going out, etc.), Retirement application, and approval status, etc.
1.3.5.6 Ledger Management
Assets can be divided into office assets, computers, electronic products, and other asset management, and can also be classified according to user-defined standards.
Each asset has a life log related to purchase, use, inspection, maintenance, Internet access, handover, take-out, firmware change, and scrap.
Equipped to specify multiple types and multiple condition combinations for search queries, export EXCEL reports, and classified statistics (reports and graphics in two ways).
1.4 System equipment configuration
1.4.1 Desktop Card Issuer

It supports three communication interface types: USB interface, serial port, TCP/IP network port, and optional high-frequency single/multi-protocol or ultra-high frequency ISO18000-6C protocol.
1.4.2 Handheld RFID reader
Reader selection is selected and matched according to customer needs

Asset management RFID tags
Readers are selected according to customer needs.

[ad_2]