RFID museum solution
[ad_1]
1 System goals
1.1 Overview
The RFID smart museum system is an organic combination of RFID radio frequency identification technology, computer technology, and multimedia technology to realize the intelligence and informatization of the museum, which can greatly meet the needs of museum management, improve management efficiency, circulation speed, and retrieval speed. Efficiency is conducive to organizing collections, greatly reducing the workload of administrators, and providing more user-friendly services.
1.2 Platform composition

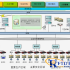
Figure 1 System networking
The intelligent museum system is mainly composed of edge layer data acquisition system, label management subsystem and management center subsystem.
Data collection system: including fixed, handheld readers, middleware, client components, responsible for reading electronic tags, and transmitting information to the management center;
Label management subsystem: Responsible for issuing and printing electronic labels;
Management center subsystem: It is the core of the entire system, including anti-counterfeiting application software, network management system and other system interfaces, etc.
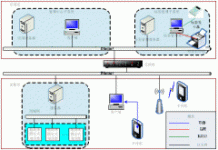
2 RFID smart museum system solution
The RFID smart museum system integrates the latest achievements of modern mathematics and cryptography, automatic identification technology, microelectronics application technology, material science and the most cutting-edge technology in the field of anti-counterfeiting, and can support museum collection management and collection anti-theft applications.
2.1 Collection management system
2.1.1 Collection registration and storage management
The application server issues tags for the new collections, establishes collection information and associates them with the tags, records the storage time of the collections, uses the handheld to collect the location of the collection tags in the warehouse and reports them to the application server for recording.

2.1.2 Collection management
The administrator holds the handheld to pick up the goods, and reads and records the tag information of the collection every time a collection is taken. After the outbound operation is completed, the handheld data is transmitted to the application server, and the application server records the data and records the actual outbound Collection;

2.1.3 Collection inventory management
The operator prepares the inventory list through the application server and transmits the inventory list to the handheld. The operator holds the handheld to perform inventory in the museum. Each time a tag in the inventory list is read, the data will be transmitted after the inventory is completed. To the application server, the application server will give an inventory report, listing the collections that have not been inventoryed.

2.1.4 Collection positioning
Through the RFID asset positioning function, the current location of an asset can be known at any time.
Through the handheld, the collection that the manager needs can be quickly found from the numerous collections.The operator downloads the EPC number of the asset that he wants to find to the handheld, and then uses the handheld to search for the asset in the warehouse. After the handheld scans the asset, a prompt sound will be emitted. The operator will follow the direction scanned by the handheld antenna. Find the corresponding asset
The monitoring software of the application system displays the current position information of the tag in real time. Once it finds that the information of a certain tag is not received at a certain time, the monitoring software should immediately give an alarm prompt
When the application system finds an error in the location of the asset, the monitoring software must immediately give an alarm.
2.1.5 Background management
Responsible for the registration of all warehousing collection files, the production and registration of staff certificates, and the backup and restoration of the database. The backstage management realizes three functions: database management, personnel file management and cultural relic file management. The back-end can also inquire about the archives of cultural relics and various data such as storage and exit according to needs, and make statistical reports.
2.2 Collection anti-theft system
2.2.1 Application scenarios
The collections in the museum are often threatened by man-made theft, so a very reliable anti-theft system is needed to realize the intelligent anti-theft and protection of the collections in the museum. RFID technology is used to realize the tracking and monitoring of the collection items, in order to automatically trigger the alarm system when the collection items move outside a certain range.

2.2.2 System solution
label design
The RFID electronic tag is attached to the collection items and adopts an anti-disassembly design, that is, once the tag is forcibly removed from the target item, the tag will automatically send an alarm signal to the reader and trigger the background alarm system.
Reader antenna coverage
The reader antenna adopts a special design, and the signal sent by it can stably cover a specific area set in advance. If an item in a coverage area leaves this area, unless prior approval is obtained, the back-end system will know that the tag has left this area. , Immediately trigger the alarm system.
Entrance and exit reader settings
Install readers at the entrances and exits of the museum and the main passages. The entrance readers are used to issue wireless tags and tag registration and item registration. The exit reader is used to identify and alert the protected items, and the items that are normally taken out of the museum are marked off and returned at the exit.
A reader is installed at the entrance and exit of the museum. The entrance reader is used to identify the items entering the museum and automatically arm the defense. The exit reader is used to identify the items taken out of the museum and disarm after confirmation by the personnel.
Background monitoring
The reader and antenna send the identification code of the tag on the protected item in the protected area to the monitoring center monitoring host through the signal concentrator, and dynamically display the area location of each tag on the screen, and give an alarm when the tag moves abnormally.
[ad_2]