Ruili Yingfang Technology RFID personnel asset management system solution
[ad_1]
The integrated management system for personnel and assets is a set of intelligent building management systems developed and designed using today’s most cutting-edge RFID technology. It integrates advanced products and technologies such as domestic identification technology, transmission technology, and software technology, which can realize personnel management and asset management. Comprehensive management system for management, daily management and other functions.
1. Project overview
(1), project requirements
Through communication with the customer, our preliminary understanding of the project is as follows: In order to strengthen safety management and improve efficiency in a military compound, the customer proposed to build a set of RFID personnel and asset management system. The system is required to be able to achieve dual management of personnel and assets, and to monitor the entry and exit of personnel and assets.
(2), RFID technology
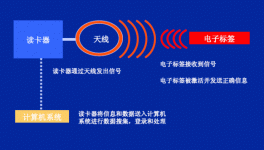
RFID is the abbreviation of Radio Frequency Identification in English (Radio Frequency Identification). Radio frequency identification technology is an automatic identification technology that began to rise in the 1990s and gradually matures. Magnetic field or electromagnetic field) to achieve non-contact information transmission and to achieve the purpose of identification through the transmitted information technology. A complete RFID system is composed of three parts: a reader, an electronic tag (usually called a radio frequency card), a so-called sensor (Transponder), and an application software system. Its working principle is Reader Transmit a specific frequency of radio wave energy to the Transponder to drive the Transponder circuit to send the internal data. At this time, the Reader will receive and interpret the data in sequence and send it to the application for corresponding processing (the working principle of RFID is shown in the figure below).

Radio frequency technology has the following characteristics:
It is highly adaptable and has a wide range of uses, which can be applied to the identification and anti-counterfeiting of various items;
Good physical performance, waterproof, anti-magnetic, temperature resistance, long service life;
Read and write information by radio frequency induction method, without manual contact during the identification process;
Multiple encryption processing, globally unique identification code, difficult to imitate;
The whole process is intelligent, easy to operate, safe and reliable;
Long recognition distance;
Data can be encrypted, stored information can be changed, identification is fast and accurate;
With anti-collision mechanism, multiple tags can be identified at the same time.
2. Scheme design
After analyzing the current technical characteristics of relevant mainstream products and the application of the open personnel asset system, we recommend that the latest RFID technology be adopted in the management system design to establish a safe, reliable, and equipment-stable safety management system.
(1) Open access control channel

Using passive high-frequency RFID equipment, the electronic tag does not need to be installed with a battery, and has a long service life, generally about 10 years. The maximum identification distance can reach 1.5 meters. The operating frequency of the equipment is 13.56MHz.
Through the unique correspondence between the RFID tag code and the person, the person’s number, basic information, etc. can be stored in the RFID tag, and the tag capacity is up to 10K. Due to the short recognition distance of passive devices, it is not possible to monitor staff in various areas of the office in real time. The only way to install recognition equipment is to install identification equipment at the entrances and exits of the areas. When employees enter and exit a certain area, the software system automatically registers personnel in and out.

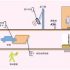
It can be seen from the above schematic diagram that a normal passing process will enter the radio frequency identification area twice and cut infrared rays twice, which can avoid blind reading to the greatest extent. Cutting infrared rays twice will also determine whether personnel enter or The meaning of leaving. Of course, the primary significance of setting up infrared recognition is to provide a warning when the radio frequency recognition does not indicate. For the above-mentioned passages, if two persons enter personally, misjudgment is likely to occur, and there will be situations where one person enters with multiple cards or without cards. In order to prevent the occurrence of this phenomenon, it is recommended that employees must maintain a certain distance when entering the passage. For example, a method similar to the 1-meter line can be adopted to ensure the correct judgment of the personnel entering and exiting the passage. Of course, the result of this is to delay the time to enter and exit the channel and reduce the efficiency.
In order to reduce the probability of misjudgment and improve the efficiency of traffic, other methods can also be adopted. For this reason, it is recommended to install two channels at the entrance and exit of the building, each channel only installs a single-sided infrared device, and implements segmented management. In the morning peak hours, the two channels can be opened at the same time for entry; during the off-peak hours, both channels are open for leaving at the same time; at other off-peak hours, one channel is for entry and the other channel is for exit. Of course, doing so increases the complexity of management. Therefore, if conditions permit, four channels or more can be installed, some of which are entry channels, and the other channels are set as exit channels, eliminating the need for time-sharing management and reducing management complexity.
The following figure is an application example:

System Features:
Intelligent identification-the system uses radio frequency identification technology and infrared sensing technology to accurately and automatically identify internal and external employees;
Humanized management-internal personnel only need to carry work cards with them to freely pass through the detection channel, and the system can quickly identify;
Information-based supervision and management-management personnel can remotely view the entrance and exit of the gate in real time through the client software, supervise the working status of security personnel, and improve the security level of the entire management system;
The personnel card (ie, electronic tag) has 100,000 repeated erasing and writing functions, which can be reused many times;
(2) Asset management
According to the form of the article, various types of labels, such as paper labels, embedded labels, tag-type labels, and anti-metal labels, can be affixed to the articles to record the information of the articles. For such common assets, mobile identification devices can be used to implement asset management functions such as inventory and query.
The mobile identification system is composed of a notebook computer and a handheld device terminal. The powerful ability of the EzBee-20 reader to read electronic tags can quickly and accurately complete the identification task.

The working diagram of the system is as follows:

When important assets pass through the identification monitoring point of the channel, they are immediately recognized by the system, and exchange information through the system network, and transmit the passed area, time and other information to the monitoring center for recording, and prompts can be displayed on the large geographic information screen at the same time Information, showing the name of the carrier. If the information of important assets is not related to the carrier, the system will automatically alarm, and the security monitoring center staff on duty receives the alarm signal and immediately executes the relevant safety work management procedures.
Schematic diagram of asset monitoring

For equipment in important areas, real-time monitoring can also be adopted. When the equipment leaves the designated area, an alarm will be given on the information screen of the monitoring center. For such a situation, you can further connect with the surveillance video equipment to check the abnormal situation at any time.

[ad_2]