Software product solutions for the whole life monitoring and management system of secret-related carriers
[ad_1]
Object Oriented
“Secret-related Carrier Lifetime Monitoring Management System” is mainly for the secret-related carrier management offices of scientific research institutions and enterprises, involving the management personnel of the file storage management room and the direct leadership of the secret-related carrier management.
Introduction to the overall plan
The current practice of all enterprises and institutions is to restrict the scope of use of secret-related carriers and prohibit the export of secret-related equipment. However, secret carriers such as U disk notebooks are often overwhelming due to their portability. This negligent leak has brought immeasurable losses to enterprises and personnel.
Secret carrier life-span monitoring and management system adopted2.4GMicrowave technology, network communication technology, all-weather monitoring of the use of all secret-related equipment within the signal coverage. When using secret-related equipment in violation of regulations, timely notification of management personnel and direct leaders to intercept, to the greatest possible reduction in negligent leaks.
value of customer
Strengthen the management of secret-related equipment
The “Secret Carrier Lifetime Monitoring Management System” starts management from the receipt of the equipment to the scrapping and destruction of the equipment, and records every link in the use of the equipment, so that it is well-documented to ensure that each equipment is protected. Whole life management.
Reduce accidental confidentiality
The system monitors the use of all controlled equipment in real time to prevent the equipment from being brought out of the controlled area, which greatly reduces the risk of using confidential media externally to leak secrets and the economic losses caused by this.
Strengthen the code of conduct for confidential personnel
The whole-life monitoring and management system of secret-related carriers makes up for the lack of safety management of secret-related personnel, and the system strengthens the behavior development of secret-related personnel, and they develop good working habits in normal work.
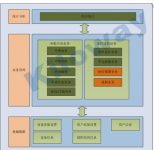
Overall scheme architecture diagram

The core function of the whole product
Equipment Approval Module
If the owner of the equipment needs to take the equipment out of the monitoring scope, he must initiate the “application business process”. After the owner initiates the process, the system initiates an approval process based on the set organization and the confidentiality level of the equipment brought out. Leaders at all levels of approval authority conduct layer-by-layer approval based on confidentiality and direct relationships, and the system automatically forwards the business. If the final approval is not completed, the equipment owner can suspend the approval business at any time.
Real-time monitoring of business
The real-time monitoring system monitors the equipment within the monitoring range around the clock, and records the monitoring and alarm conditions of all equipment in real time. When an unauthorized device is brought out of the monitoring area, the system activates an audible and visual alarm to remind the management personnel to intercept it. At the same time, when equipped with a short message transceiver, it sends an alarm short message to the owner and the direct leader of the device as a reminder. In the case of video surveillance, start video recording for evidence collection, authorize users to bring out the surveillance area, and the system records historical traces.
Main hardware equipment

[ad_2]


