Solution of security alarm system for bank vault door remote guard
[ad_1]
Chapter One System Introduction
1. System function introduction
The bank vault security management system integrates security alarm function, wireless vault door control function, identification function (fingerprint), digital monitoring function, real-time monitoring, timing switch and centralized management of the vault’s entry and exit dynamics and security status, and the vault password The lock cooperation can realize the multi-lock linkage switch of the vault door (two locks, three locks or four locks).
620)this.style.width=620;” border=0>
During normal working hours, the system implements real-time monitoring of the vault entry and exit, and records the entry and exit of the vault; during non-working hours, the vault is armed with anti-theft, and the vault door is closed through the motor lock (the door must be authorized by the center to open the door), and the front-end equipment of the system is both It can work independently on a single machine (its advantages are simple and convenient to use, and relatively low cost), and it can also work with a host computer located in the management center of the county or city bureau (its advantage is that the system has high security, can remotely alarm, and the management department can Centralized management and monitoring of the treasury under its jurisdiction).
Once someone commits criminal acts of robbery, illegally enters the control area or steals the vault door, the alarm control host will automatically send the relevant personnel’s mobile phone (four mobile phone numbers can be sent) through the wireless network (GSM) and the county bureau (or city bureau) ) The treasury security management center alarms (networking status), the alarm information includes the name of the treasury where the alarm occurred, the contact person, the contact’s phone number, the phone number of the nearby police station, and the category of the alarm situation, etc. The personnel on duty in the center can quickly and accurately learn the name and contact number of the person responsible for the alarm location and the unit responsible for the alarm on the display, and the duty officer can promptly notify the relevant personnel to check the situation of the vault based on the information on the alarm situation. When an alarm occurs, the management center can also monitor the sound of the scene, and grasp the dynamics of the scene in time, so that the staff on duty can make correct judgments. This effectively solves many hidden safety hazards in traditional vaults that are easy to copy, lose, difficult to manage, and commit crimes at get off work, and improve the security level and scientific management level of the vault.
At the same time, image monitoring equipment linked to the alarm equipment can be installed in the vault. Every time the vault is opened and an alarm occurs, the system can automatically transmit the image of the person who opened the vault to the management center through the telephone line in the form of a photo. , In order to facilitate the management of the center to understand the situation of the treasury in time and correctly handle the police situation.
In addition to identification and timed opening and closing of the vault door, the bank vault security management system can also be connected to a variety of alarm detection devices to perform alarm detection and realize security alarms, thereby adding multiple layers of security to the vault:
First, install infrared probes outside the vault door to detect the criminals’ intrusion as soon as the criminals have not yet approached the vault, so as to make an on-site alarm and report to the management center.
Second, a motor lock, a fingerprint sensor and a door sensor sensor are installed on the vault door to control the opening and closing of the door. Only users with correct identification can enter the vault during normal working hours, and there is no management during non-working hours. No one authorized by the center can open the vault door controlled by the motor lock. If it is opened forcibly, an alarm will be generated by the door sensor.
Third, we can also install infrared probes and cameras in the vault, so that criminals can enter the vault illegally after breaking through the first two lines of defense. There is also an alarm device in the vault that senses the situation and makes an on-site call to the center.
The features of the system are as follows:
Access to the vault adopts an identity recognition system: the system uses a fingerprint recognition system that cannot be copied and cannot be deciphered to identify the personnel entering the vault. The fingerprints are mapped to the information of the vault opening personnel to realize the identity recognition of the personnel entering and exiting (only legitimate users and within the specified time) Can enter the vault). The fingerprint registration, modification or deletion adopts multi-level password protection, and the security is fully guaranteed;
Timed opening and closing of the vault door: The vault door can only open the motor lock installed on the vault door to enter the vault after the fingerprints of two people are authenticated within the specified time (six time periods can be set), and the system will automatically enter the disarmed state at the same time. At this time, the door opening system will not alarm;
With the functions of input, logout, and deletion of fingerprints: the system is set to 15 working groups, one group per person, each group can take 4 fingerprints, one of which can be set as a duress alarm fingerprint (that is, the fingerprint can open the door, but it will Send alarm and distress information to the management center and related personnel), any combination of fingerprints in any two groups can open the door.
After fingerprint authentication opens the motor lock, if the vault door is not opened within 10 banknotes, the system will automatically lock the motor lock to reduce potential safety hazards.
With the function of automatic arming and manual arming after closing the door: leaving the vault, after the vault door is closed, you can manually enter any fingerprint to make the system enter the arming monitoring state, and you can also set the system in the alarm control host within seconds after the vault door is closed Automatically return to the arming monitoring state;
The system equipment can work independently on a single machine, or run on a network. The front-end equipment of the system can work independently (it has the advantages of simple and convenient use and relatively low cost), and it can also work with the host computer of the management center located in the county or city bureau (its advantage is that the system has high security and can remotely alarm. The management department can conduct centralized management and monitoring of the treasury under its jurisdiction).
The door opening and closing information can be uploaded to the management center: the normal door opening and closing information is uploaded to the management center, the information includes: the name of the vault, the name of the certifier 1, the name of the certifier 2, the authentication time, and the status of the vault door (whether it is open or closed);
Illegal fingerprints (or IC cards) cannot open the door, and force an alarm. The motor lock installed on the vault door cannot be opened without entering a legal fingerprint. If the vault door is forcibly opened, an alarm will be issued immediately. At the same time, the on-site warning lights and siren will be driven, and the alarm information will be sent to the monitoring center. The alarm information includes: the name of the vault, the alarm time, and the occurrence of the alarm. Types of emotions, etc.;
The door is opened illegally during non-working hours or outside the set time period, and an alarm will be generated regardless of whether the fingerprint (or IC card) is input or not;
Adopt a variety of alarm methods to ensure that there are no omissions in the alarm. Alarm methods include: on-site warning lights and siren alarms, wireless upload of alarm information, wireless SMS notification to relevant personnel; as long as there is an alarm, the system will automatically send alarm information at regular intervals (the number of times and time intervals can be set) until the alarm is lifted by the designated personnel.
The alarm can be cleared by a legal fingerprint or a dedicated remote control;
Multi-lock linkage (three-lock, four-lock linkage) can be realized together with the vault code lock
The fingerprint-controlled motor lock has a delayed self-locking function (the motor lock will automatically lock if the vault door is not opened after ten seconds after opening.)
The management center can remotely authorize door opening during non-working hours and remotely cancel alarms;
The alarm control host equipment installed in the treasury has the function of anti-dismantling protection;
An alarm will be issued after the external power supply is cut off, and the backup power supply will be activated at the same time, so that the equipment can continue to work for more than 24 hours after the power is cut off;
Fingerprint information can be added or deleted only with a dedicated password;
A centralized monitoring center can manage more than thousands of vaults, with low cost and high efficiency;
Support historical data, alarm data query, output, print reports, etc.;
After obtaining the authority of the advanced user, the staff on duty can remotely arm and disarm the alarm control equipment of the branch vault and set various data through the center.
2. Operation process of entering and exiting the vault
During the set open time period of the vault management system, the indicator light of the fingerprint identification device next to the vault door lights up in the[red]state, indicating that it is time to swipe the fingerprint to open the vault motor lock. If the indicator light of the fingerprint identification device is off, it means that it is the time to enter the prohibition of swiping fingerprints.
1) The vault door opening procedure: the two persons first open their respective code locks-then the two persons press the fingerprint on the fingerprint identification device to open the motor locks-turn the vault door turntable to open the door-after the business processing in the warehouse- -Close the door and turn the turntable, the motor lock will be automatically locked, and then the password will be disrupted-and then one person uses one fingerprint to press once on the fingerprint identification device for defense.
2) Instructions for the specific operation steps of the vault door:
a) First, the two persons turn on their code locks.
b) Then when the first person presses the fingerprint and hears a short beep, it means that the fingerprint has been recognized as a legal fingerprint. Then another person presses the fingerprint and hears a short beep. After the sound, you can hear the unlocking action of the motor lock “click”, indicating that the motor lock has been opened, and then turn the vault door turntable to open the door.
c) Turn the vault door turntable to open the door within ten seconds of opening the motor lock, otherwise the motor lock will be automatically locked after ten seconds (you need to press the double fingerprint again and repeat the second step).
d) After the vault door is opened, the staff can enter to conduct various business processing. At the same time, the host computer starts to count down (the initial storage time limit is 20 minutes, if the time limit is exceeded, the host computer will sound an alarm). If the staff closes the vault door in the warehouse for business processing, they can press the exit button in the warehouse to open the door when going out.
e) After finishing the business processing in the warehouse, first close the vault door, turn the dial to lock the door, the motor lock will be automatically locked, and then the password will be disrupted, and then one person will use one fingerprint to press the fingerprint on the fingerprint identification device for defense (This step can also be omitted, the host will automatically arm the defense within the specified time).
f) If you hear a long beep when pressing a fingerprint, it means that the fingerprint cannot be identified, such as an incorrect pressing position or an illegal fingerprint.
g) Special circumstances (non-working hours) need to enter the treasury, which must be approved by the management center and authorized by the center before opening the treasury in the normal way of opening the door.
Chapter 2 System Structure
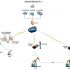
This system takes the city or county bureau as the unit for system construction, and the management center of the treasury under the jurisdiction of the city or county is located in the city or county bureau.
620)this.style.width=620;” border=0>
The central system of this system is composed of a central data receiving device, central monitoring software, and PC. It remotely monitors the real-time entry and exit status of each vault and security alarm status through wireless mobile network and fixed telephone network (for image data transmission) .
Branch equipment: a treasury alarm control device, a pair of door sensors, fingerprint recognition equipment, police siren, motor lock, infrared probe, etc. (digital camera and image transmission equipment can be installed); used to detect the opening/closing of the treasury door, Timely control the treasury door, illegal warehousing, damage to the host, power failure, and many other preventive control information.
The treasury alarm control equipment is installed at each treasury site to detect the entry and exit of the treasury door, the power supply of the system and the security alarm status of the treasury, and transmit the detected information to the bank treasury security management center by wireless short message transmission.
When the system is in the monitoring state, within the set working hours and within the specified fingerprint authentication time interval, input two legal fingerprints of different persons continuously, and the treasury alarm control host will enter the shielding alarm state (disarm) and open the motor lock Open the outer door of the vault. The vault door can be opened normally in the disarmed state. At this time, the monitor host will shield various input alarm signals. Even if the door is opened or there is an alarm signal for disassembly and destruction, the system will not alarm. If the treasury door is opened in the disarmed state, the treasury alarm control host will upload the center opening time, location and name of the door opener through the wireless transmission module. In the disarmed state, if you want to leave the disarmed state and return to the monitoring state (armed), there are automatic and manual options: automatic means that the vault alarm control host automatically returns to monitoring after a set time in the disarmed state; manual refers to In the shielding state, enter a legal fingerprint arbitrarily, and the monitor will return to the monitoring state.
In the monitoring state, if the door is not opened correctly through fingerprint authentication or the machine is illegally disassembled, the treasury alarm control host will generate an alarm and enter the alarm state. The treasury alarm control host will record the alarm information and transmit the alarm time and location through wireless short messages. Upload to the mobile phone of the monitoring center and related personnel. After the center receives the alarm sent below, it saves the alarm to the database on the one hand and triggers the center alarm output. In the alarm state, in order to improve the reliability and timeliness of the alarm, the alarm information will be displayed and the alarm sound will be displayed until the treasury alarm control host leaves the alarm state.The alarm release of the treasury alarm control host must be through the following two methods
Input two legal fingerprints at the treasury site at the same time to cancel the alarm, and the system will automatically enter the armed state after the alarm is removed;
The management center will disarm the alarm, and the system will automatically enter the armed state after disarming the alarm;
If the system is not in the alarm or shielding state outside the set normal working hours, it will not accept fingerprint (or card reader) data input, and the motor lock will be closed. At this time, as long as you break the lock and open the door and enter, the monitor host will enter the alarm state. Regardless of the state of the system, as long as there is a mains power failure, the treasury alarm control host will send the power failure alarm to the center.
For occasions with special security requirements, this system also supports remote authorization. If you want to enter the vault during abnormal door opening hours, you must obtain the designated remote dialing (or SMS sent by designated mobile phone) authorization before entering legal fingerprints. , Otherwise, the system does not accept fingerprint input (this function requires the dialing function of the SIM card).
Chapter III System Equipment
1. Equipment installed in the vault
Treasury alarm control host
Nine defense zones microcomputer control, keyboard programming, LCD display, easy programming operation, small size, flexible configuration
Support 2 alarm centers, and 4 security department phone numbers can be set.
Two authorized door opening numbers can be set to prevent occasional needs, such as: opening the door during abnormal working hours or losing the access control card. In the event of damage, the vault door can be opened through the authorized number.
You can set the on-site monitoring number to monitor or actively monitor the sound of the location of the alarm.
The keyboard sets the working time limit for opening the vault door, it will automatically alarm when overtime, the fingerprint authentication time limit, and the time limit for repeated alarms if the alarm is not confirmed.
Built-in four-wire four-wireless universal defense zone input that can be independently armed and disarmed.
It has on-site code matching learning with the wireless remote control to realize the on-site arming and disarming of the remote control.
Alarm field siren output, linkage control switch output (can set siren, linkage output time).
You can set the dedicated working hours and working days of the treasury.
With linkage image function: linkage image output when alarming (the linkage output time can be set) or the center actively dials to view live images.
When an alarm occurs, it is linked to the on-site siren output.
Chinese name can be set for SMS defense zone alarm information.
The built-in electronic clock can set the automatic arming and disarming time of the defense zone.
You can set the interval for reporting the current status of the host regularly.
With fingerprint entry, assignment, and cancellation of fingerprints, the system is set to 15 working groups, one group per person, each group can take 4 fingerprints, one of which can be set as a duress alarm fingerprint (that is, the fingerprint can open the door, but will send The management center and related personnel send alarm and distress messages), and any combination of fingerprints in any two groups can open the door.
Automatically detect the working status of the machine, and report fault/recovery information, such as power failure/low battery voltage/card reader abnormality, etc.
With rechargeable battery inside, it can work normally for more than 24 hours after power failure.
Fingerprint reader
The fingerprint module is made of cast steel integrated material by die-casting at one time, and there is no artificial rivet inside, which is safe and reliable;
The fingerprint module adopts the most advanced optical module in the world and has passed the certification of the Ministry of Public Security;
[ad_2]