The Status Quo and Security Strategies of Mobile Payment in the Era of Internet of Things
[ad_1]
With the determination of my country’s mobile payment standards in 2011, mobile payment in the Internet of Things era finally ushered in a period of rapid development. Like other electronic payment methods, the key to mobile payment is still security. This article starts from the nature of the Internet of Things. Combining the domestic status quo of mobile payment and advanced foreign experience, it analyzes the security problems existing in its industrial chain and proposes security strategies.
1. Mobile payment in the Internet of Things era
Following the “information revolution” triggered by Internet technology in the last century, now the Internet of Things will once again change our lives. As the name implies, the Internet of Things connects all items to the Internet through sensors to realize functions such as monitoring, tracking, and information interaction. Connecting bank cards and merchant POS machines through mobile phones and other digital personal items forms a new field: mobile payment. Users can use SMS, WAP} IVR, proximity sensing and other methods to conduct business activities such as transfer, shopping and payment.
In August 2009, Premier Wen proposed the concept of “perceive China”, which greatly promoted the research and development of the Internet of Things. The era of the Internet of Things has become an irreversible trend. On April 28, 2011, Hong Feng, executive vice president of China UnionPay, announced that the mobile near-field payment uses the 13.56MHz standard, and the last mile of mobile payment has been opened. As the vanguard of the Internet of Things, mobile payment will not only bring convenience to our lives, but also detonate the retail industry and greatly enhance the national economy.
2. The status quo of mobile payment at home and abroad
China Mobile, China Unicom, China Telecom, and UnionPay have also deployed their own mobile payments. In 2010, China Mobile invested 39.801 billion yuan in shares of Shanghai Pudong Development Bank, and then pushed forward its mobile payment business. In May 2009, China Telecom also officially launched the “mobile payment” business, including four sub-businesses of mobile phone ordering, mobile payment, mobile banking and mobile card swiping. China Unicom also launched a series of mobile payment services in December 2008. In April 2010, China Unicom cooperated with China UnionPay to promote UnionPay mobile payment services. China UnionPay launched the first-generation mobile payment service in 2002, realizing various value-added services such as empty ticket booking and electronic discount coupons. In July 2011, UnionPay Commerce launched the convenient payment brand “Pay for All” and formally entered the offline payment field. At the same time, UnionPay also launched home mini-terminals and mobile phones to enable users to pay utility bills, book tickets, and buy lottery tickets at home. According to Analysys International’s report, the transaction scale of China’s offline convenient payment market will reach 435 billion yuan in 2014.
However, my country UnionPay and the three major telecom operators have not unified the standards since the test experiment of near-field mobile payment services. Mobile chooses 2.4GZ RF-SIM technology. China Unicom chose 13.56MHz NFC and SIMPass technology. Telecom chose the 13.56MHz SIMPass technology, and also selected the 2.4GHz RFUIM technology in individual trials. UnionPay chose 13.56MHz NFC, SD card, SIMPass, etc. All giants want to seize the opportunity of mobile payment. In fact, Japan is the operator who controls the mobile payment industry chain, but South Korea is the bank, but all parties can make money together. This is originally a cooperative and dependent industry. Mobile payment can become a new business growth point for mobile operators and banks. From the experience of Japan and South Korea, sincere cooperation between operators and UnionPay is the ultimate way out. The introduction of national standards for mobile payment has allowed us to avoid more wars of attrition.
Even a profitable industry, as long as it can attract the whole people or enough people to participate, it can make a Big Mac cake. Back then, domestic portals such as Sohu, Sina and so on were cooperating with operators to turn losses into profits with a few cents of short message service. With the rapid development of e-commerce today, no one dares to underestimate mobile payment that combines remote and on-site transactions. According to a latest research report released by iResearch in July 2011, by 2015, the total global mobile payment transaction volume will reach 670 billion US dollars, far exceeding this year’s 240 billion US dollars. Mobile payment has shown a blowout trend worldwide, especially in our neighbors Japan and South Korea, where more than 85% of customers have used mobile payment. Japan began to promote mobile payment services in 2004. As of 2009, 65% of mobile users were mobile payment users. At present, 70% of electronic payments in South Korea are completed by mobile payments. The French government and companies announced in 2010 that Nice, France, became the first non-contact city in Europe. Correspondingly, these countries with highly developed mobile payment have formulated complete relevant laws and policy supervision.
3. The key issues of mobile payment
Although the technology and standards have been fully prepared, the promotion of mobile payment is still full of difficulties. The biggest problem is how to cultivate the user’s habits, safety, confidentiality, ease of operation and legal protection. Security is the most important and most difficult issue for payment. Chinese users generally lack a sense of security on mobile devices such as mobile phones. Almost everyone has received fraud and spam messages. The blooming copycats, including many domestic brand mobile phones, have preset fee traps. The entire social credit system is imperfect. People are insecure. These will hinder the rapid development of mobile payment.

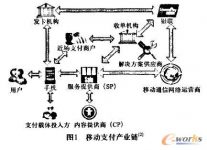
The industrial chain behind mobile payment is too long—financial institutions, mobile operators, network operators, terminal equipment providers, and retailers, as shown in Figure 1.
Compared with traditional payment methods, the security problem of mobile payment is particularly severe. All departments in the industry chain must work together from technology to credit. The Internet of Things is an extension of the Internet, which is naturally open, inclusive and anonymous. If you want the Internet of Things to better provide people with convenient and fast services, you must first ensure personal privacy and information security. If people have a bad or insecure experience when they first learn about mobile payment, then in the future It will be very difficult for mobile payment, including the entire Internet of Things, to reverse this “first impression”.
4. Security strategy of mobile payment
Security measures can be strengthened from all aspects of the industry chain: financial institutions can allow users to set transaction limits, so that accidental losses can be controlled within a certain range, and the side effect is that it will cause inconvenience to users. UnionPay can also send dynamic verification passwords or reminders of consumption amount to users’ mobile phones, which can greatly improve the safety factor, but requires users’ mobile phones to be turned on and must not be in arrears. From the mobile operator’s point of view, it is necessary to strictly prevent the user’s SIM card from being copied or forged. There have been many cases of using fake ID cards to report the loss of the SIM card and causing user losses across the country. In this regard, a combination of real-name authentication and fingerprint authentication can be used, and financial-grade security chips and encryption software can be installed on mobile terminals. In terms of terminal equipment, mobile operators or financial institutions can purchase uniformly, reduce procurement costs through scale, and shield counterfeit and counterfeit equipment from the mobile payment industry chain to ensure the safety of terminal equipment.
On the technical level, the security model can protect privacy well. For a centralized control network environment, you can use an enterprise-level security model, role-based access control (RBAC), and divide the RD1D system into RDID tags, readers, and information processing systems; put the data in the RDID tags and the information processing system separately In, the password can be decrypted only after the two are merged. When the label changes, the encryption and decryption password will also change. This method is expensive in calculation and storage, and has low real-time performance, and it is not suitable for distributed IoT environments.
At present, cryptography has been relatively perfect, homomorphic encryption technology, secure multi-party calculation methods, but these methods require a lot of calculations, and they cannot be directly applied to the special computing environment of the Internet of Things. Nowadays, many studies on the privacy and security issues of the Internet have also discussed in depth access control, data encryption, behavior monitoring, and proxy services. However, the Internet of Things environment has its particularities and needs to be further improved. The Internet of Things is an emerging industry, and various security privacy protection schemes and security structure models are based on a specific perspective. There is no universality and there is still a lot of room for development. Furthermore, any security measures are only temporary. Encryption and decryption technologies are always developed alternately. On the basis of continuous R&D and progress in security technologies, the social credit mechanism is further improved, and the Internet of Things and the entire Internet of Things are guaranteed through moral and legal constraints. The healthy development of society is the way to long-term stability.
[ad_2]