Zhongying Kexun RFID Asset Management System
[ad_1]
1. Application background
RFID technology has been widely used in bill anti-counterfeiting. For example, in airports, railway stations, subways, and tourist attractions, where there are many people, use RFID electronic tickets instead of traditional manual tickets to improve efficiency, or in competitions and performances. When the ticket volume is relatively large, use RFID technology to prevent counterfeiting of tickets. Not only does it no longer need manual identification to realize the rapid passage of people, but it can also identify the number of times the ticket is used to prevent the ticket from being stolen and used again, so as to achieve “time anti-counterfeiting”.
2. System design
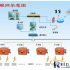
The system consists of three parts: a back-end database, a ticket terminal, and a ticket reader, and each part is connected through a network system.
The back-end database is responsible for storing anti-counterfeiting information such as ticket holder information sent by the ticketing terminal. The ticketing terminal writes the relevant information of the ticket buyer into the electronic label attached to the ticket through the label printing machine, and uploads the information recorded in the label to the system database at the same time
The reader installed at the entrance of the venue is responsible for collecting the electronic label information in the bill, and completing the verification process by comparing it with the information recorded in the background database
3. System workflow
1. Information binding: RFID anti-counterfeiting bills can be made by RFID label printers. Each ticket has a unique and unchangeable ID number.
2. Ticket sales: When the ticket is sold, the name of the ticket holder, the certificate number, the validity period and the number of validity of the ticket can be written in the RFID anti-counterfeiting ticket, which can be determined according to specific needs. The ID number of the sold bill will be added to the list of legal bills in the system database as a basis for verification.
3. Ticket verification: When it is necessary to verify the identity of the ticket holder (such as an airport), the authenticity check of the ticket is similar to the authenticity check of the certificate, that is, the information in the ticket is read through the reader, and the Relevant information is retrieved from the back-end database and compared with the certificate and bill of the bill holder.
4. Introduction to RFID tags with SM7 algorithm of Zhongying Guomi
Zhongying’s RFID tags based on the National Secret SM7 algorithm are independently developed under the premise of obtaining the National Secret qualification.
The chip’s wireless communication interface complies with ISO/IEC 15693. The security protocol uses a dedicated encryption algorithm SM7 to protect the security of data exchange. There is a high-speed CMOS EEPROM inside. The tag’s high-speed RF communication interface can reach a data transmission rate of up to 106kbit/s. The tag has an anti-collision function: it can process multiple tags within the effective working distance of the tag reader antenna at the same time. The anti-collision algorithm ensures that only one tag is selected and that it is not affected by other tags entering or leaving the radio frequency area during data exchange with the selected tag.
Features of the chip:
◆ Using SM7 national secret algorithm encryption to protect the security of data interaction
◆ Triple mutual authentication system
◆ Encrypt all data during communication to prevent signal interception
◆ With 8 mutually independent keys, support one card for multiple purposes
◆ The 4-byte serial number of each card is unique
◆ Meet 100,000 erasing and writing, ten years of data storage
◆ Can withstand the maximum working field strength of 8A/m
◆ Working temperature: -20℃ to 70℃
◆ High data security:
◆ Each Block has 16-bit CRC check
◆ Each byte has a parity bit
◆ Use coding method to distinguish 0, 1 or no information
◆ Conform to “ISO/IEC15693”
◆ Conform to “ISO/IEC DIS9798-2”
Five, summary
By writing the identification code information when the label is issued, and verifying the identification code information when using the label, the purpose of label anti-counterfeiting can be achieved. The above scheme shows that the contactless logic chip based on the National Secret SM7 algorithm can be completely suitable for low-cost anti-counterfeiting applications. This solution has been extended to a variety of anti-counterfeiting systems, such as door and window label anti-counterfeiting, stamp anti-counterfeiting, and ticket anti-counterfeiting. The program has been used on a small scale in these project markets and has been well received by users.
[ad_2]